Nworm TrickBot Trojan for silent Malware Spreading Module
The trickbot banking Trojan has come up with a new malware module that secretly attacks the Windows domain controllers without any detection. In the past, we have seen so many new modules being added in the Trickbot malware and tis constantly getting new additional modules and hence it can secretly perform several types of malicious activities. The Trickbot Trojan can steal cookies, active directory services databases, Open SSHKeys, PuTTY credentials and many more. The cyber-criminals partners with TrickBot for getting secret access on the targeted network for ransomware attack.
What is Nworm
As per the report by Palo Alto Unit 42, the trickbot has released a new version of network spreading module namely “nworm” and can avoid detection because it attacks the Windows domain controller. After successfully getting installed, this trickbot does a quick analysis of the running environment and secretly downloads multiple modules in the backdoor for executing predefined malicious activities. It infects the PC as well as the network.
In the past, we have seen that how trickbot successfully downloaded modules such as “mworm” and “mshare” in the “Windows Active Directory” environment and infected vulnerable domain controllers. The module exploits the SMB vulnerabilities to attack the domain controller.
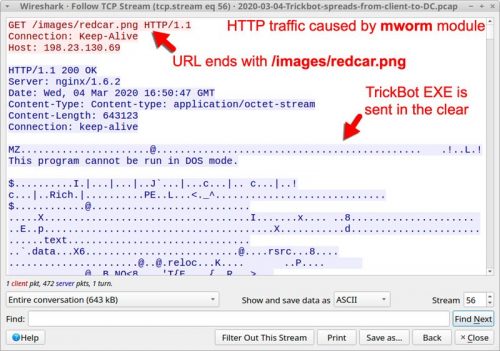
Mworm is being used by Trickbot from September, 2019 and it transfer Trickbot executable in an unencrypted form to the targeted vulnerable domain controller.
Attack Flow Until March, 2020
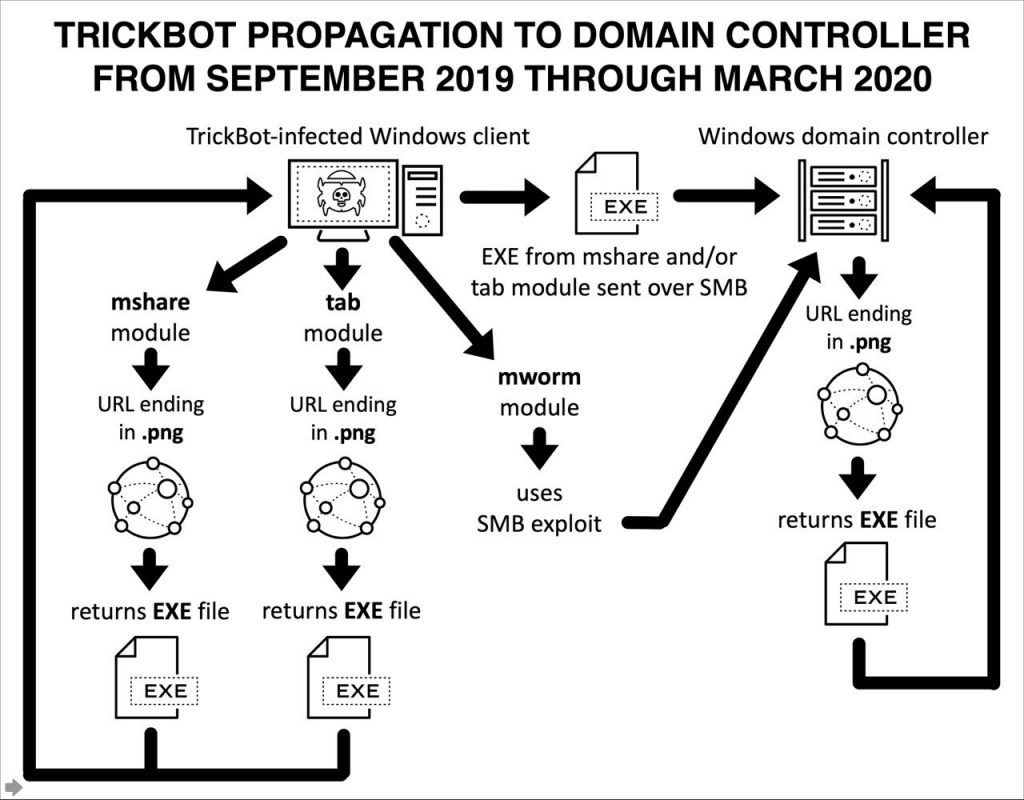
Since the malware executable is unencrypted, the security application present in the DC could detect it and remove after being copied.
Thus, the developer introduced a new updated module in April, 2020 namely “Nworm” which is very hard to get detected.
Attack Flow since April, 2020
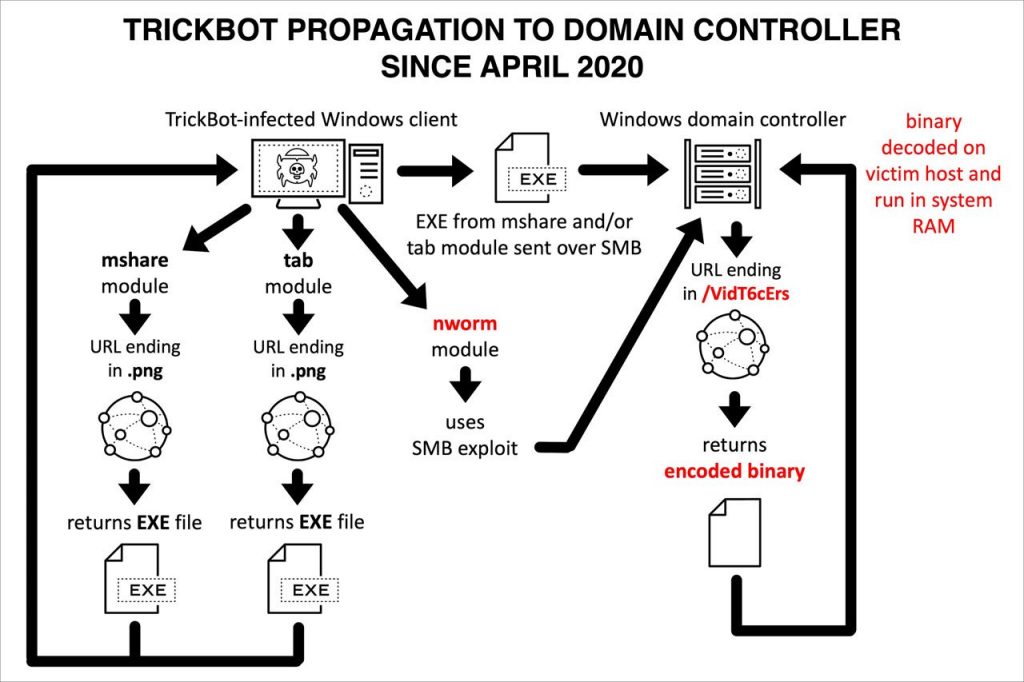
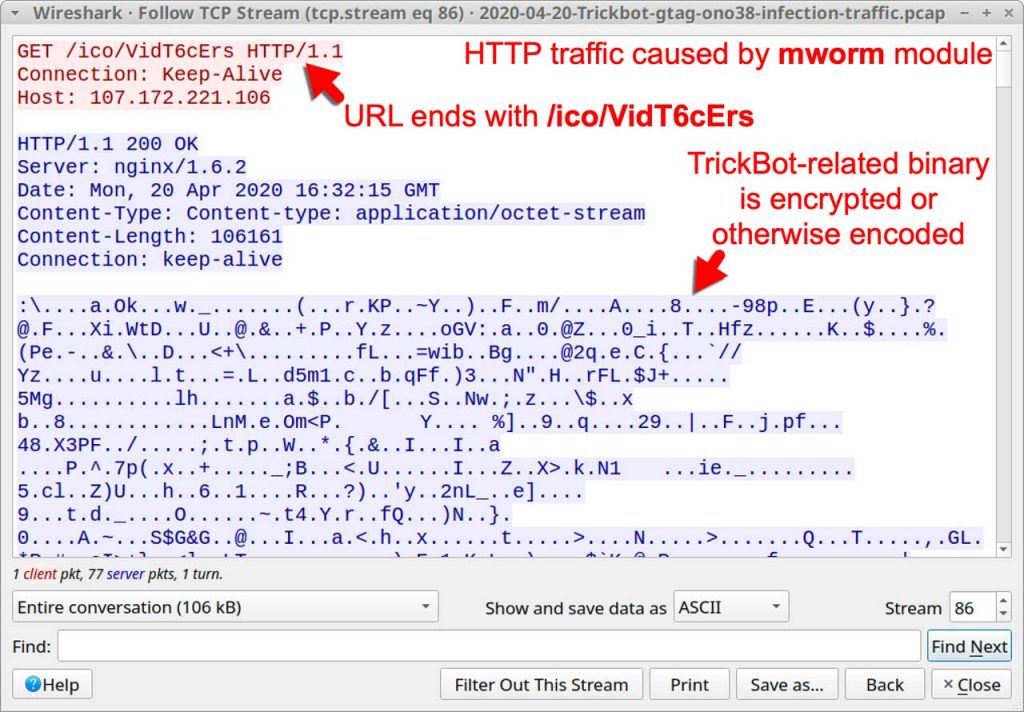
The newly “nworm” encrypts the Trickbot executable hence it is very difficult for security applications to detect it. Further, the infection gets launched on the domain controller in memory. This is a very effective method to intrude the TrickBot in the domain controller without getting detected.
On step ahead to improve the stealthiness, the Trickbot do not start again if the PC is rebooted. However, it very rare that a domain controllers are restarted. Usually, the malware gets enough time to execute and complete the harmful tasks.




