What is Computer Virus? Malware Prevention on Windows, Mac
What is Computer Virus?
Computer Virus is program or code designed & developed by hackers. This program is designed to gain and corrupt computers, mobile phones, tablets or network. Once computer virus executed, it replicates itself by modifying other computer programs and inserting its certain code. If this replication is succeeds, the affected areas on computer then said to be ‘infected’ with computer virus.
Computer Virus requires a computer program to run. Generally, viruses writes its own code into computer program and when such computer program runs, the virus written or included in computer/host program is executed first, and causing infection and damages.
On other hand, computer worm doesn’t need a computer program as it is run impendent program or code chunk. So, this computer virus can run independently and actively carry out attacks. If you are not aware, computer viruses cause billions of dollars’ worth of economic damage each year.
However, the solution as protection against computer viruses are also exists in world. Much security company in response of computer viruses attacks, they have designed & developed some security tool against computer viruses.
These security tools offer computer users to find threats or malware in their System’s locations and provide results in user-readable format so that users could easily delete all detected threats. In simple word, if computer virus is problem, then antivirus or security tool is solution.

Computer virus example (Types of computer virus)
Resident Virus: It is computer virus stores itself within memory like RAM, offers it to infect other files even when the originally infected program is no longer running. For example, memory-resident virus could be in memory when writable drive is connected, or Diskette is inserted into computer. Once installed, this computer virus could infect the driver or diskette and delivers itself to any other computer that uses that drive or diskette.
Multipartite Virus: This computer virus is designed to infect entire System. This virus is spread by performing unauthorized actions on your Operating System, folders and programs. These computer viruses are capable of attacking both boot sector and executable files simultaneously.
Direction Action: This computer virus targets a specific file type, and most commonly executable files (.exe) file by replacing and infecting them. However, it is easy to find and remove this type of virus in computer because of its targeting specific file nature.
Browser Hijackers: It is computer viruses designed to infect your browser like Google Chrome, Internet Explorer, Mozilla Firefox, Safari and/or other browsers. Browser Hijackers are designed to redirects you to malicious websites. However, this virus can easily be detected and deletion is also possible with some necessary steps.
Overwrite virus: This computer virus overwrite files content to infect entire folders, files and programs. The aim of attackers behind this virus is to destroy the original program code with this malicious code. This deadly virus can exploit DOS platforms like Windows, Linux, and Macintosh.
Web Scripting Virus: This type of computer virus can come from suspicious links, ads, images, videos and website that are designed to run certain codes to install computer viruses in computer. Attackers behind this virus attempt to gain and infect computers when users download malicious files or visit malicious websites.
File Infector: This computer virus targets executable file and slowdown the program, and then damage the System files when users run them. Some file infector virus overwrites computer files and other can damage your hard drive’s formatting.
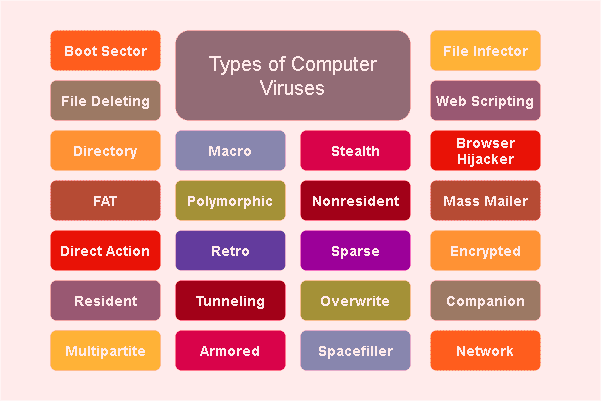
Macro Virus: Macro virus is also computer virus that can be found in Microsoft office documents (word, or excel). These viruses are usually stored as part of documents and can deliver when the files are transmitted to other computers or through email attachments.
Polymorphic Virus: This computer virus is designed to make malicious changes in System’s settings and makes antivirus difficult to detect this virus in computer. The evaluation of suspicious codes can occur in variety of ways including filename changes, compression and encryption with variable keys. Some examples of polymorphic virus are Storm Worm, Virlock Ransomware.
Boot Sector Virus: This computer virus infects the boot sector of floppy disks or the MBR (Master Boot Record) of hard disks. This virus executed when the System is booted from an infected disk, but once loaded, it will infect other floppy disks when accessed in infected computer. Some common boot sector viruses includes ‘Monkey’, ‘NYB or B1’, ‘Stoned’ and ‘Form’.

History of computer virus
In 1940s, John von Neumann – the mathematician first time discussed about ‘computer virus’ in his series of lectures and the paper ‘Theory of Self-Reproducing Automata’ published in 1966 explained about the mechanism of computer virus. The great mathematician ‘John von Neumann’ explained that computer virus is computer program to damage machines, copy itself and infect new hosts just like biological virus.
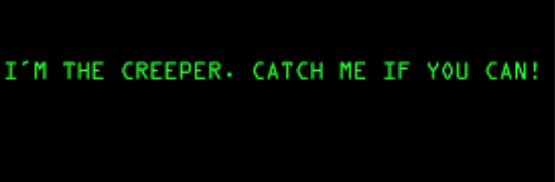
In 1971, the computer virus as ‘Creeper Program’ was designed & developed by Bob Thomas at BBN as the security test to see if self-replicating program was possible – which was the theory of John von Neumann.
‘Creeper Program’ virus infected DEC PDP – 10 computers running TENEX operating System. This computer virus gained access via the ARPANET and copied itself to the remote System where the message ‘I’m the creeper, catch me if you can!’ was displayed. However, this program was deleted by ‘Reaper Program’ – the first antivirus created by ‘Ray Tomlinson’ to move across ARPANET and delete transmitting Creeper Program.
In 1974, ‘Rabbit Virus’ or Wabbit Virus was designed & developed with duplicate itself capability. Once this computer virus installed, it made multiple copies of itself, severally reducing System performances and eventually crashing the machine.
‘ANIMAL’ – the first Trojan virus: This computer virus as first Trojan horse virus designed & developed by computer programmer John Walker in 1975. This virus was attempted to guess which animal the user is thinking of with the game of 20 questions, were extremely popular.
ANIMAL computer virus asked several questions of the users in an attempt to guess the type of animal they were thinking. However, the developers created PERVADE to replicate itself and ANIMAL virus in every folder to which the current users had access.
However, this program was carefully written to avoid damaging existing files or folders structures, and to avoid copying itself if permission did not exist, and its spread was blocked by an OS upgrade that changed the formats of file Status tables PERVADE used.
‘Brian – the first computer virus for PC’: In 1986, the first computer virus for IBM personal computers dubbed as ‘Brain Boot Virus’ was released. This computer virus is considered the first IBM PC compatible virus responsible for the first IBM PC compatible virus epidemic.
This virus was designed & developed by two brothers, Basit and Amjad Farooq Alvi – who ran a computer store in Pakistan. They developed ‘Brain Boot Virus’ which replaced the boot sector of floppy disk with virus. This computer virus was also first stealth virus contained a hidden copyright message, but did not actually corrupt any data.

How to Prevent Computer virus?
Cybercriminals or hackers never notify you actually when they will start infecting your machine with viruses like Adware, Trojan, worms, ransomware or other malware. So, it is your responsibility to be alert from any attacks and must follow some necessary precautionary measures to prevent System from computer viruses attacks.
Once viruses on computer, it made several unwanted modifications in System’s settings and collect sensitive data stored in computer. However, it is possible to avoid installation of any types of infections or computer viruses if you follow some necessary prevention tips. These methods can help you to block malware or viruses forever. Let’s take a look at some necessary prevention tips against computer virus.
Computer virus Prevention Tips:
Keep Operating System up-to-date: Cybercriminals can take advantages of weaknesses in computer like outdated Operating System, bugs in System files and/or other problems offers them to infect your computer. So, you should keep your Operating System up-to-date. Updating Operating System can fix any bugs or problems in computer and improve System performances as well.

Install Antimalware- antivirus software: As mentioned, if computer viruses are problems in computer, then antivirus is solution. It means antivirus software offers you to find malware or viruses in computer, shows scan results in user-readable format, and then you can delete detected viruses. So, you should make sure that you have some strong antivirus software installed in your machine.
Keep your antivirus software up-to-date: You should keep your antivirus software up-to-date that could helps to find latest viruses in computer. Also, you should always try to use powerful antivirus software designed to detect all types of infections and avoid free antivirus software if possible.
Run System scans regularly with antivirus software: You can setup your antivirus software to run the scan at regular intervals either weekly or monthly. System scans with antivirus software offers you to find malware or malicious files in each computer’s location, and then it shows the scan results detailed about detected viruses.
Also, you should not to shutdown/restart your computer during System scanning process. Wait to finish scanning process. Once done, please check if infections are removed, and if not, then you can re-scan your computer with antivirus software.
Secure your network: You should be careful while sharing or accessing your personal data on network and check if this is secure network. Also, you should avoid accessing your personal or financial data using public WiFi.
Never broadcast an Open WiFi connection. Use WPA2 or WPA encryption. Also, it is not a great idea to broadcast your SSID – the name of your WIFI network. You can still access it with your device, you will just have to manually type in SSID and the password.
Avoid visiting untrustworthy websites, stop clicking any hyperlinks presented on it: Some websites on the web provide pirated material, contained suspicious links/button, and delivers some false-positive advertisements. You should be alert while browsing internet and avoid clicking any hyperlinks/ads presented on untrustworthy websites.
Hover your mouse cursor over the hyperlinks before click to see where the links really taking you. Also, you should be alert while downloading any files or applications from unknown sources, unknown file sharing sites and open from email attachments. If you have downloaded files from unknown sources, then you should scan it first with some powerful antivirus software, and then you can open it in computer. Also, you should avoid downloading files from unknown sources.
Keep your personal files or data safe: Cybercriminals can take advantages of your careless internet browsing or activities on system and can collect your personal or sensitive information stored on your computer or on the web.
They can attempt to collect your personal data by delivering bogus gift offers, security alert, and other types of scam popups on browser by malicious websites. They use malicious tricks you to gain access to your personal data like your online accounts. For example, they can show bogus Microsoft Login Form looks like legitimate login form associated with Microsoft, and ask you to enter your email ID and password details. This way, they can collect your email login credentials. So, we recommended you to stop sharing your personal or sensitive data to any users who are unknown to you and avoid sharing data to untrustworthy sources.
Use multiple strong passwords: Never use the same password for every account you have. You should make sure that your password for an account at least 8 characters long and includes upper and lower case, number and/or special characters. This way, you can make your password strong that can’t be guessed by hackers.
If you use same password for everything or on many things like email ID, Facebook, Twitter having same password, and it is discovered, then it takes only seconds to hack your account. So, you use multiple strong password and never share your password to anyone.
Backup your files: In case of System damages especially files lost, backup is one of the core solutions to recover your files or data back. For example, if System is infected with malware or viruses, and these infections attempted to corrupt/lock your personal files, and if you have already strong backup your personal files on some safe storage media, then you can easily restore them from a backup. So, you should keep backup of your personal files or data.

How to remove computer virus?
With antivirus or antimalware software, computer virus removal is possible. Computer viruses are hidden program and can easily be detected by some powerful antivirus software. As mentioned above, computer viruses can be included in software package you downloaded from unknown/unofficial sources, installed browser software, System registry, control panel, hard drives, boot sectors, and in your personal files or data.
Run System scan with some powerful antivirus software and wait to finish scanning process, and delete the detected threats is the ways of malware or viruses removal. So, you should try this. Let’s take a look at steps on how to remove computer viruses.
How to download and install ‘Antivirus Software’ in Windows/Mac?
Step 1: Open browser and ‘visit official website’ of antivirus company which offer powerful tool to remove all types of infections in computer. Or, you can download the antivirus software through link below.
Step 2: Double-click on ‘Software setup file’ and follow on-screen instructions to finish installation
Step 3: Launch the ‘Antivirus software’
Step 4: For the first time, you should go with ‘Full System Scan’. And if you are regular user of this antivirus software, then you can choose ‘Custom Scan’ or other available options to scan computer for malware.
Step 5: Wait to finish the scanning process. After scan, this will show the scan results in user-readable formats, with the option to delete all detected threats. Click on ‘Delete’ or other available buttons to delete them.
Important Notes:
Antivirus software installed in computer must be always turn ON means PC protection is turn ON that could helps to detect malware or viruses in real-time. Some malware blocks System scan with antivirus in ‘Normal Mode’. So, you need to enter into ‘Safe Mode’ or ‘Safe Mode with networking’, and then run System scan for malware or viruses. Also, you should keep your antivirus software up-to-date that could helps to detect and delete latest malware.
Conclusion
I am sure this post helped you to known about ‘Computer Virus’, its capabilities, types of computer viruses, timeline & history of computer viruses, and how to prevent System from malware or viruses. Also, you can read about how to remove malware or viruses in computer. That’s all. For any suggestions or queries, please write on comment box below.







