Windows error log was altered by hackers to hide malicious payloads
Cyber criminals behind this use fake error logs in order to store ASCII characters which is disguised as hexadecimal values that decode malicious payload that are mainly designed to prepare ground for script based attacks. It is used as a trick which is described as a part of longer chain with intermediary PowerShell Commands that ultimately delivers scripts for investigation purposes.
Reading between the lines
MSP threat detection provider named Huntress Labs discovered an attack scenario where a threat actor will mainly target system that are used to run an unusual trick to carry along with their attack routine. The attacker behind this already gained access to targeted computer and achieve persistence. At this moment, they use a file called “a.chk” that identifies Windows error log for an application. The last column shows hexadecimal values.
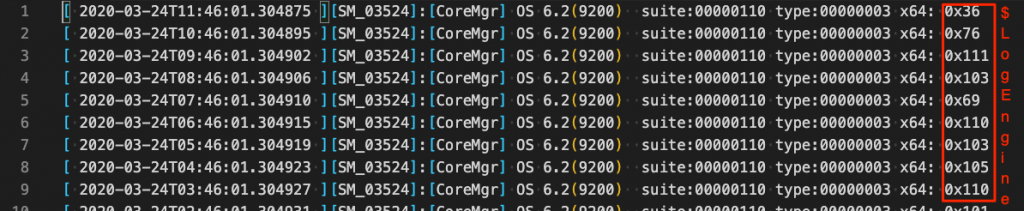
These are the decimals representations of ASCII characters. Once decoded, they make a script that contact the command and control server for the next step. A cursory look at the mock log file likely not raise any flags as the data includes timestamps and reference for Windows internal version number.
According to John Ferrell, “At first glance, it looks like a log for some application. It has timestamps and includes references to OS 6.2, the internal version number for Windows 8 and Window Server 2012”
Further, a closer application reveals that the trick used by actor to extract the relevant chunk of data and build the encoded payload are shown below how the numbers convert to text to form the script. According to Ferrell, the payload is obtained using a scheduled task impersonating a genuine one on the host and sharing its description. Two executables are involves, both being renamed copies of legitimate files to appear inoffensive.
Using legitimate filenames
One named is “BfeOnService.exe” and is a copy of “mshta.exe”, a utility that executes Microsoft HTML applications that has been used for deploying malevolent HTA files. In such case, it executes VBScript to start PowerShell and run command on it. The other has the name “engine.exe” and is a copy of “powershell.exe”. Its main purpose it to extract the ASCII numbers in the bogus log and convert them to obtain the payload.
Ferrell states that script decoded this way applies an in –memory patch to the Antimalware Scan Interface to bypass it. It also helps antivirus programs to detect and delete scripts based attack.
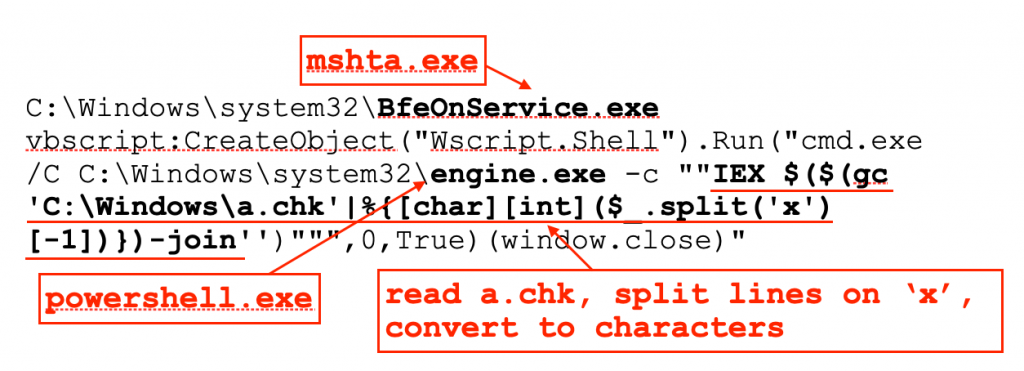
A second command act as a downloader that is executed to retrieve another PowerShell Command with the same functions. At the end of the chain is the payload that collects information about the compromised PC.
It is unseen that what the attacker is after, but the last script collects details about installed browsers, security products, point of sale software and general and specific tax preparation. It is far from being sophisticated attack, it shows that cyber criminals explore all revenues to gain foothold on the target network and developer their attack in various creative ways.




