Use this PowerShell command to check Exchange Servers for ProxyLogon hacks
Microsoft has released a PowerShell script to automatically check if a server was hacked with the recently disclosed ProxyLogon vulnerabilities.

The four zero-day vulnerabilities CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065 are together called ProxyLogon vulnerabilities. The exploit to this vulnerabilities allow attackers to perform remote code execution on Microsoft Exchange servers utilizing Outlook on the web (OWA).
As a part of the attack, certain web shells are installed that allow the attackers to control the server and access to the internet connection.
Microsoft fixed these vulnerabilities on 2nd of March. During the disclosed, a list of commands was provided that Exchange administrators use to check if the server was hacked.
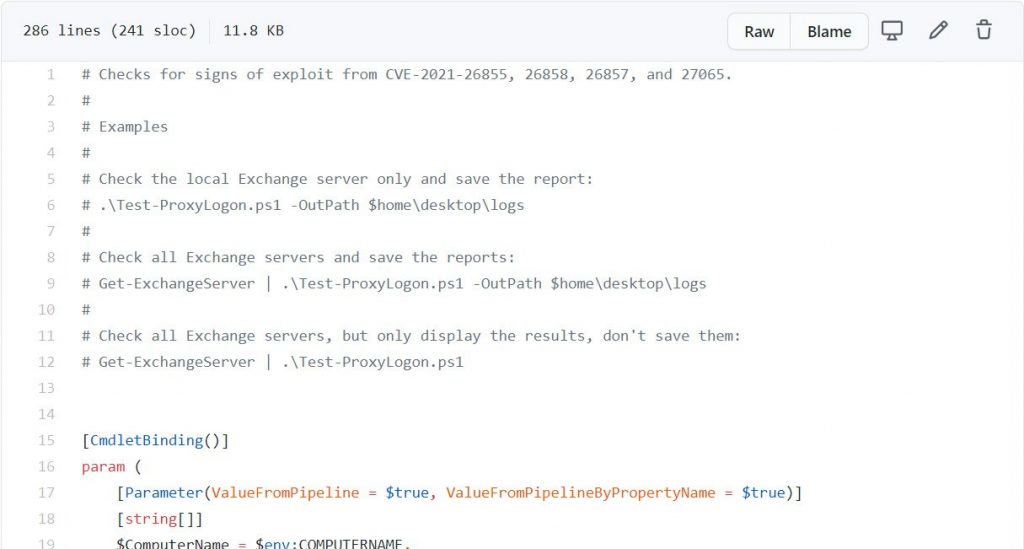
Earlier, commands would need to be executed manually. With the released the PowerSheel script [Test-ProxyLogon.ps1] yesterday, these tasks of the administrator will now automatic.
Microsoft provides instruction on how to use the PowerShell script. To check all the exchange servers in your organization and save the logs to the desktop, enter the following command under Exchange Manager Shell:
Get-ExchangeServer | .\Test-ProxyLogon.ps1 -OutPath $home\desktop\logs
Use the below command if you just want to check the local server and save logs:
.\Test-ProxyLogon.ps1 -OutPath $home\desktop\logs
To just test the local server and don’t want to save the result, enter the following command:
.\Test-ProxyLogon.ps1
CISA said in a new advisory, “CISA is aware of widespread domestic and international exploitation of these vulnerabilities and strongly recommends organizations run the Test-ProxyLogon.ps1 script—as soon as possible—to help determine whether their systems are compromised.”




