Parallax RAT becomes hackers’ choice to steal stored PC credentials
Parallax is a RAT or Remote Access Trojan which is being widely distributed via using scam email campaigns. It allows crooks to take complete control over the victims’ computer remotely from their services.
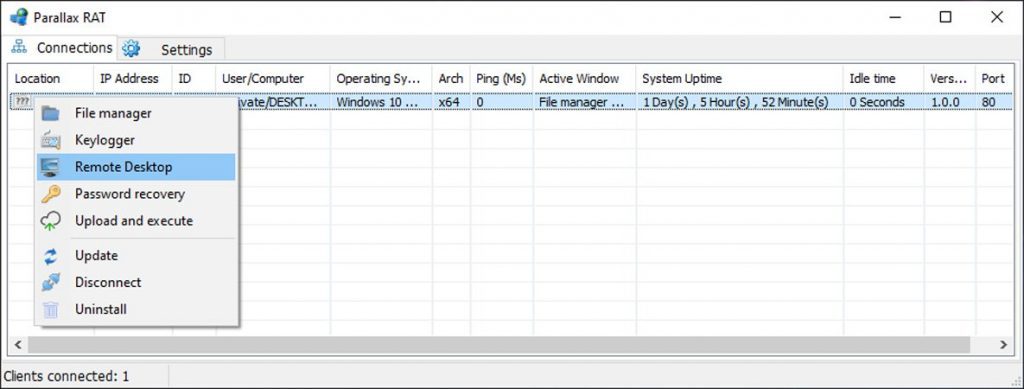
This sample of the Parallax had been tracking since December 2019 by MalwareHunterTeam. Being offered with minium $65 month, attackers started using this Trojan to gain complete access to a targeted host machine and steal the saved login credentials and files or to execute commands on it. The gathered information is used in performing identity theft, gaining access to the banking accounts and spreading the malware to other victims.
Parallax RAT sold on hackers’ forum since December
Parallax team had been promoting and offering the support of the Parallax RAT since December 2019. This product is promoted as having 99% reliability and being suitable for both professional and beginners.
“Parallax RAT had been developed by a professional team and its fully coded in MASM.
Its created to be best in remote administration. Parallax RAT will provide you all you need.
Suitable for professionals and as well for beginners.
First and most important we offer 99% reliability when it comes to stability.
Parallax was designed to give the user a real multithreaded performance, blazing fast speed and lightweight deployment to your computers with very little resource consumption.
We are a group of developers and we are here to offer quality service.
-Parallax Team, join now!”
Attackers can purchase the Parallax RAT in a little price of $65 or $175 for three months, with the features that include:
- Execute remote commands on the infected computer
- Remote Desktop capabilities
- Upload and download files
- Login credential theft
- Encrypted connections
- Standard support
- Supports Windows XP through Windows 10
The developers also claim that this program has the potential to bypass Windows Defender, Avast, AVG, Avira, Eset and Bitdefender.
Scam email campaigns are used for the distribution
Researchers are seeing that Parallax RAT is most commonly distributed via using scam email campaigns. As per James, a security researcher, it is very common to find a new campaign containing infectious attachment that installs Parallax. The infection occurs when users click on the provided attachment.
Both James and head SentineLabs Vitali kremez have seen that attackers firstly inject a loader with an image from imgur image sharing site containing an embedded parallax executable. This executable is launched to computer after extracting from the image. In a sample Parallax was injected into svchost.exe and in another sample it is injected to cmd.exe.
After the install, the parallax crates a shortcut to the launcher to the Window startup folder in order to launch automatically with each OS reboot. In some cases, schedule tasks are added to launch in various time intervals. This means, the virus gains the complete system persistence and access it when it wishes to.
After installing the RAT, the attackers use their command and control the host machine to steal the stored passwords, files and run command of their choice. In many samples, the Command and Control servers are hosted on duckdns.org.
In order to prevent the Parallax RAT intrusion, you should be careful when receiving any emails that contain attachment. You must firstly assure that the senders’ addresses are trustworthy and the letter not has any grammatical errors and spelling mistakes – these are general ways to distinguish emails as spam or not.






