Linkedin spear phishing campaigns distributing “more_eggs” backdoor to targets
A new spear-phishing campaign is detected targeting Linkedin job seekers with fake job offer to infect their systems with sophisticated “more_eggs” – a backdoor Trojan.
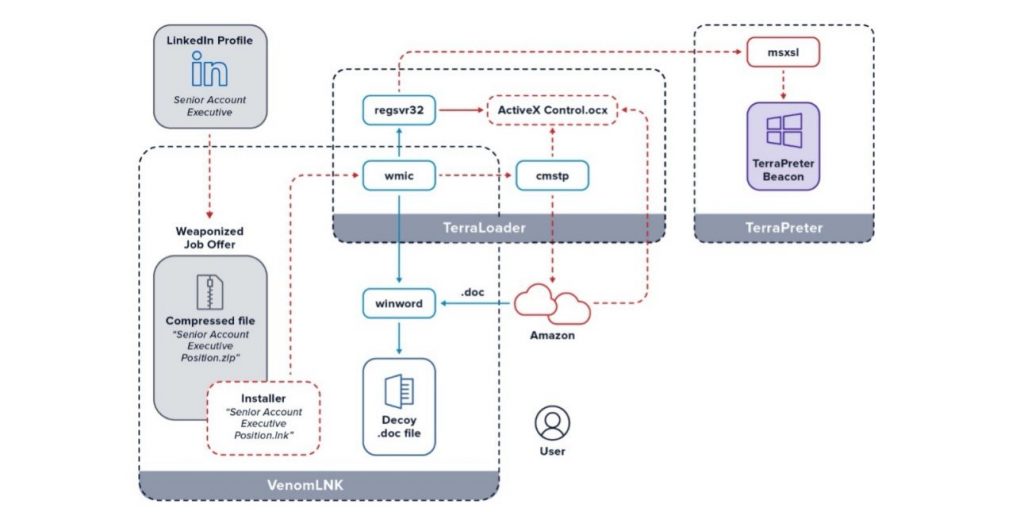
The phishing message lures the professionals into opening a .ZIP file, which is named as victims’ job title form the profile of their Linkedin profiles.
As for example, if the Linkedin’s member’s job listed as Senior Account Executive—International Freight, the malicious .zip file would probably have the name Senior Account Executive—International Freight position (note the “position” added to the end).”
As per eSentire security researchers, the campaign to deliver “more_eggs” uses the same module operandi as that spotted since 2018 with backdoor attributed to Maas or Malware-as-a-Service provider, Golden Chickens.
Once installed, more_eggs utilizes the Windows processes to run that makes difficult for the antivirus security solutions to detect it on the system. Because the malicious file has professional job title, plus the position, the chance is more of its execution.
The attackers exploited a number of unemployed people raised during the pandemic. The researchers noted, “A customized job lure is even more enticing during these troubled times.”
The very first phishing operating was taking place during the COVID-19 pandemic. During the year, 2020, more than 300 phishing campaigns were created to harvest personal and banking related credentials from potential victims.
The researchers are not sure about of the aim of the phishing operation. However, being a backdoor, it is said to likely be the one that acts as a conduit to retrieve additional payloads from remote attackers’ server, such as banking Trojan, Ransomware, and info stealer.
It may even act as a foothold for the victims’ network to ex-filtrate data. Fortunately, this phishing operating to distribute the backdoor virus has now been disrupted.





