Ryuk ransomware uses Wake-on-Lan to infect the computer in network
A Malware analyst discovered that Ryuk Ransomware uses the Wake-on-Lan feature that allows powered off devices on a compromised network and encrypting the files on them.
Wake-on-Lan is a hardware that allows administrators to turn on powered off devices by sending special network packet to it. This feature is helpful for those have needed to perform scheduled tasks and updates to computer when it is powered off.
According to a recent analysis of Ryuk Ransomware by Vitali Kremez, a head of SentinelLabs, the malware will spawn subprocesses with the argument “8 LAN” when it is executed.
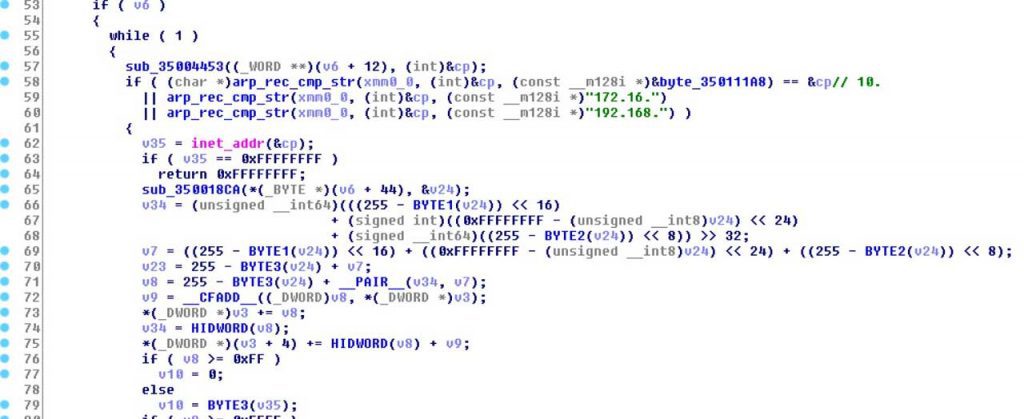
On using this argument, the ransomware will scan the device’s ARP table containing a list of known IP addresses on the network and their associated Mac addresses. It will check if the entries are part of the private IP address subnets of “10.”, “172.16.”, and “192.168, if so then the malware will send a Wake-on-Lan (WoL) packet to the Mac addresses of the devices to turn it on.
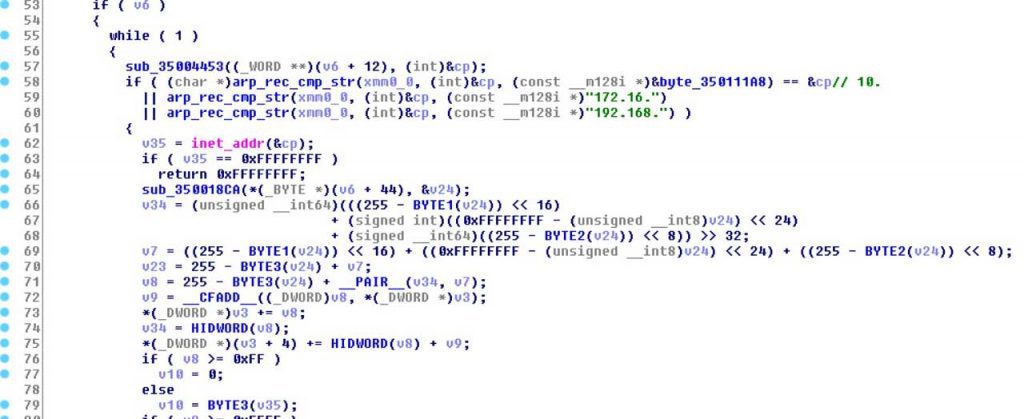
The request comes in a magic packet containg “FF FF FF FF FF FF FF FF”.
If this request is successful, the Ryuk ransomware will attempt to mount the remote device’s C$ administrative share.
![]()
If the share can be mounted, then Ryuk will encrypt that remote computer’s drive even.
Kremez states, “This is how the group adapted the network-wide ransomware model to affect more machines via the single infection and by reaching the machines via WOL & ARP. It allows for more reach and less isolation and demonstrates their experience dealing with large corporate environments.”
To mitigate this new feature, all that administrators required is to allow Wake-on-Lan packets from administrative devices and workstations.






