RobbinHood Ransomware Exploits Gigabyte Driver Bug To Block Security Products
New technique used by cybercriminal group behind RobbinHood Ransomware
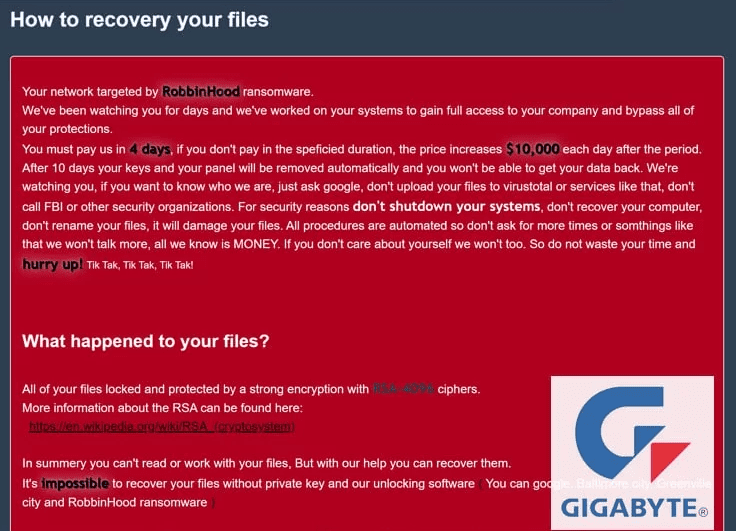
According to report, Cyber security researchers have discovered new threats in ransomware category i.e., RobbinHood Ransomware that is designed with new and unique method to encrypts files of targeted computer with interrupt. This Ransowmare virus is capable to bypass antivirus detection so that it can locks/encrypts all files stored in computer hard drives. Interestingly, security experts have discovered two attacks. Let’s take have a look at both attacks in detail.
RobbinHood Ransomware installs vulnerable Gigabyte Driver: Vulnerability allow the hacker to disable security products
Security researchers & experts have explained that cybercriminals group behind this attack perform to separate attacks including it installs vulnerable Gigabyte Driver on targeted computer along with main ransomware payload. The main purpose of installing the drivers is to allow the cybercriminals to blocks security products running in computer so that RobbinHood Ransomware can encrypt files without any interruption. Both the attacks blocking antivirus software and encrypting files are performed by RobbinHood Ransomware’s developers on targeted originations or its computers.
It is similar to Sodinokibi or Ryuk Ransomware as it primarily targets large organizations is they corporate or government companies which are often seen as high-value targets. When we talk about the new technique used by RobbinHood Ransomware, it is carried out over several steps starting with hackers gaining the initial foothold onto targeted network and follows the techniques to execute encryption tools.
Initially, cybercriminal group behind RobbinHood Ransomware attack installs legitimate Gigabyte driver with the name GDRV.SYS on targeted machine and then exploits the privilege escalation bug or vulnerability as CVE-2018-19320 Vulnerability found on the driver to gain kernel access. Once done, it uses Kernel access to temporally block the Windows operating System driver signature enforcement. Malware programmer installs malicious Kernel driver with name of RBNL.SYS that helps the attacker to disable or stop “antivirus software” or other security products running on Windows OS. Finally, RobbinHood Ransomware is executed and file encryption begins.
When we talk about updated report in September 2019, it involves the inclusion of code designed to kill processes so that encryption can occur unhindered. As per our research, the malicious codes itself targeted the processes associated with Microsoft Office application including MS Word, MS Excel, WordPad, Outlook, SQL and VirtualBox which is software that allows for the running virtual machines. It become clear to cyber security researchers by targeting SQL and VirtualBox that the malware programmers ware targeting business and potentially looking to join ranks of “big game” ransomware strains.
Clop Ransowmare is another strain that has adopted the similar tactics as of RobbinHood Ransomware. It was story of November 2019 when developers of Clop Ranosmware were attempting to block Windows defender as well as remove the Microsoft security Essential that allowed the hacker to encrypt all types of files stored in targeted computer.
Prevention & precaution methods against RobbinHood Ransomware, Clop Ransomware or other similar infection
- Limit access rights; give user accounts and admins only the access rights they need
- Make regular backups, and keep them offsite and offline where attackers can’t find them
- Lockdown your RDP; turn it off if you don’t need it, use rate-limiting, 2FA or a VPN if you do
- Ensure tamper protection is enabled – other ransomware strains attempt to disable your endpoint protection, and tamper protection is designed to prevent this from happening
- Use multi-factor authentication (MFA)
- Use complex passwords, managed through a password manager
Let’s Chat: Talk to us: Write comments
If you have queries or suggestions regarding “RobbinHood Ransomware uses new technique of encryption: Targeting business and individual users both”, please write on comment box given below.
You may also read: New Mexico AG is asking $5000 to Google for violating UPA






