Remove This document protected by CloudFlare Virus
Tips To Delete This document protected by CloudFlare Trojan
This document protected by CloudFlare is a deceiving message shown by several precarious documents. Cloudflare is a legitimate web-infrastructure and website-security company that has absolutely no relation with this bogus message. This scam is triggered by potent cyber hackers in order to convince people that the infectious MS Office document is locked and in order to be able to access to it, they need to enable macro commands. However, these documents are malevolent and their motive is to infect PCs with malware. Such types of spiteful files are commonly spread via spam email campaigns.
More About This document protected by CloudFlare:
This document protected by CloudFlare scam message may also claim the Online preview of the file in not available. In general, users are encouraged to enable editing content. Moreover, you can also see the actual logo of CloudFlare inscribed on vicious documents. These kinds of files are used to propagate a wide range of malware like ransomware, trojans, cryptominers etc. As soon as users enable content on MS Office documents- they enable macro commands. Malicious documents infect PCs by executing pernicious macros which starts the infection process. Soon after the intrusion, this hazardous threat conducts a series of malicious activities in the background and causes multiple pernicious issues in the device.
This document protected by CloudFlare virus can monitor your Online actions, steal your personal data relating to banking and other financial details and expose them to hackers for bad intentions. Crooks can misuse your sensitive data for generating illicit profits and cause you to be a victim of cyber crime. This hazardous trojan can also share your crucial data with third-parties for advertising purposes. It displays fake security alerts, error messages, update notifications etc. and tries to scam you into installing rogue software. It alters the default registry settings by making vicious entries in it which allows the virus to get automatically activated with each Window reboot. This perilous malware messes with important system files that are crucial for smooth computer functioning and prevents many installed apps as well as drivers from working in a proper manner. And therefore, looking at all these hazards, the instant removal of This document protected by CloudFlare trojan is highly required.
How Does This Trojan Intrude Your System?
This nasty application can be bought Online however, it is distributed mostly via several precarious methods. Most often, crooks spread this trojan via spam email campaigns, illegal activation tools, backdoor trojans, unreliable download sources and fake updates. Spam campaigns are used to send bogus emails that contain malicious files attached to them. Such files are in multiple formats such as executable and archive files, JavaScript, Microsoft Office and PDF documents etc. As soon as these files are opened, run or executed, it initiates the infection process. Fake updaters infect the devices by abusing fault of outdated products and by simple installing malware rather than the promised updates. Apart from this, clicking on malicious ads and links, sharing peer-to-peer network, visiting infectious websites etc. are also prime reasons behind the infiltration of such dangerous parasites in the work-station. And so, you avoid interacting with these sources to keep the machine harmless and secured.
Threat Summary
Name– This document protected by CloudFlare
Category– Trojan, password-stealing virus, spyware, banking malware
Description– Steal users’ sensitive data for adverting purpose and also to generate illicit revenues by misusing those details, Disables all the running security measures of the infected PC and drop more infections in the machine as well as help the criminals to get access to system.
Symptoms– Slowness of system’s performance, fake error messages, security alerts, intrusive ads and pop-ups, unwanted redirects to questioning sites and so on.
Distribution– Spam email campaigns, malicious file downloads, P2P file sharing, and many more.
Removal– Manual and automatic guidelines as provided under this article
Other Harmful Properties of This Trojan:
This document protected by CloudFlare is able to deactivate of all the running security services and Windows Firewalls and make the machine vulnerable for more Online infections. It may easily bring other hazardous parasites such as rootkits, adware, worms, spyware etc. in your PC and turn the device into a malware-hub. This nasty virus might also bring dangerous ransomware in your computer which has tendency to encrypt users’ crucial files and data and put them hostage until the victims pay the attackers a sum of ransom to unlock it. If such types of destructive crypto-viruses could manage to infiltrate your machine, nothing can be worse than that.
This document protected by CloudFlare virus can ruin your important files kept inside the system and make them totally useless. It also creates tons of junk files in the hard drive of your PC which consumes huge amount of memory resources and drags down the overall computer performance severely. It causes the machine to respond slower than ever before and take more than usual time to complete any task. So, don’t waste any time. Just take an immediate action and remove This document protected by CloudFlare virus from the PC by following the effective removal steps given below.
Special Offer (For Windows)
This document protected by CloudFlare can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and This document protected by CloudFlare has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
Google Chrome (PC)
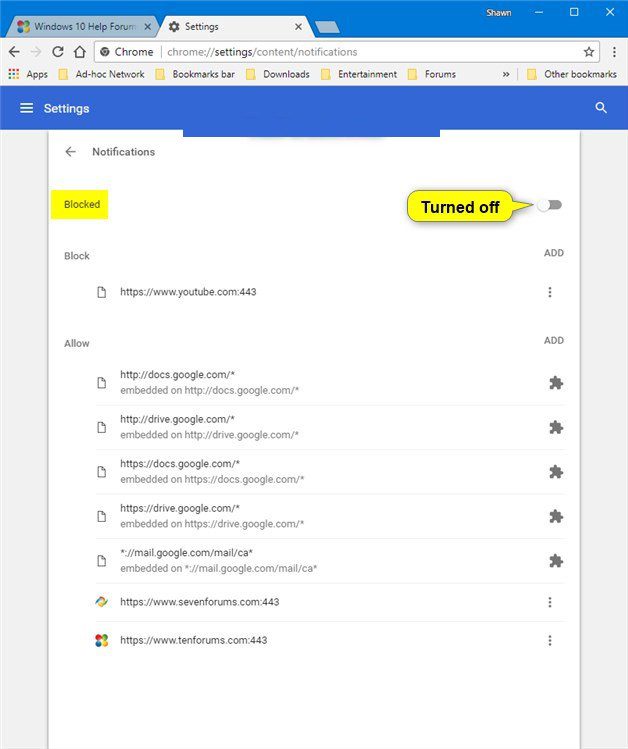
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
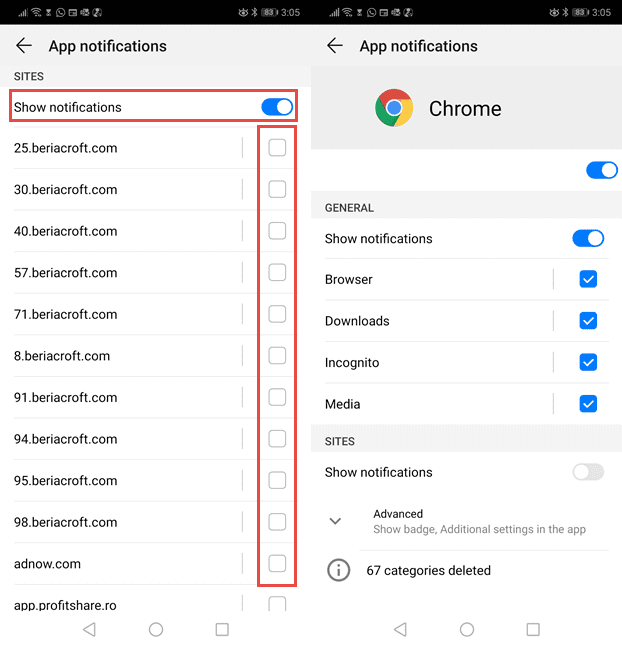
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
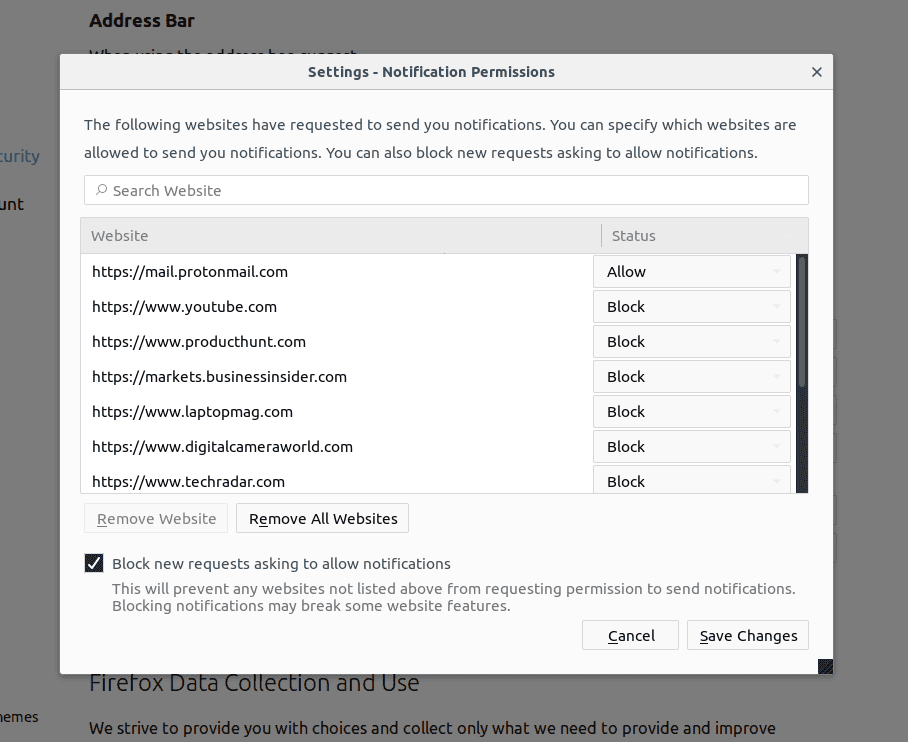
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
Internet Explorer
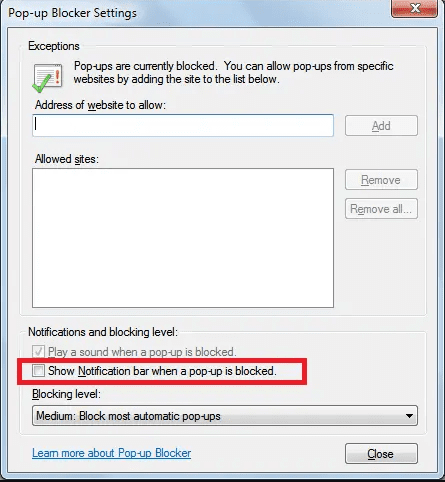
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
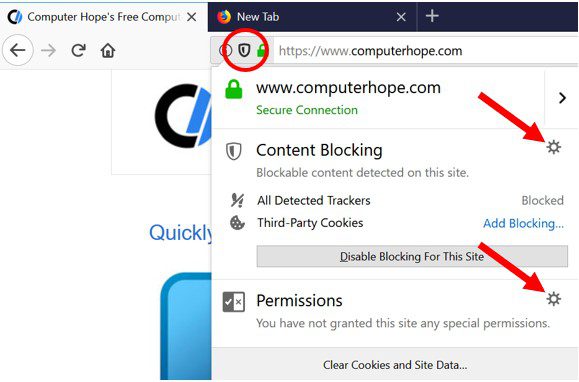
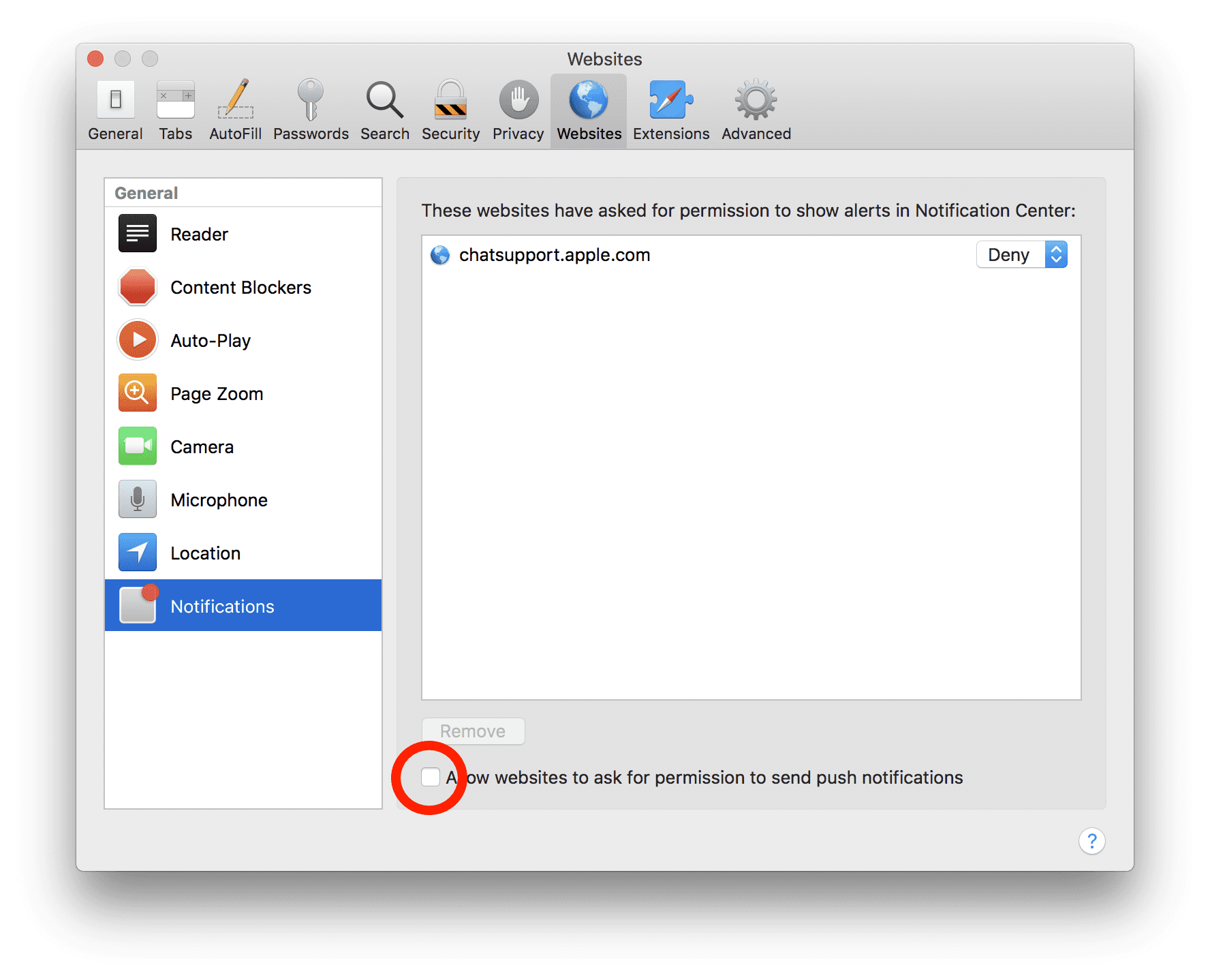
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove This document protected by CloudFlare:
Remove the related items of This document protected by CloudFlare using Control-Panel
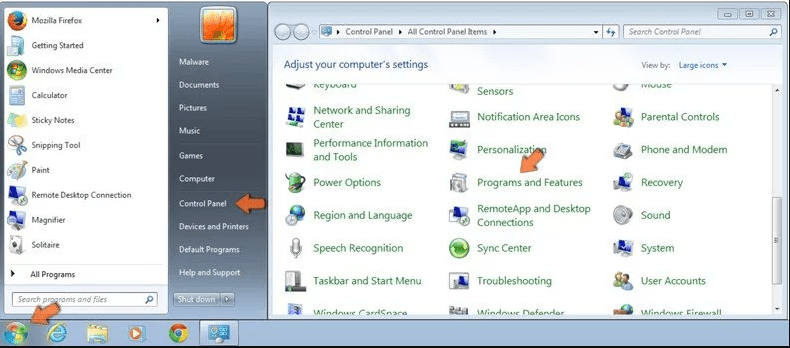
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
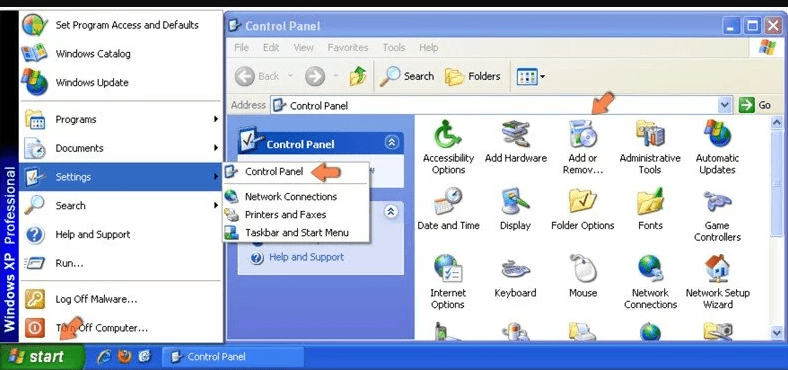
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
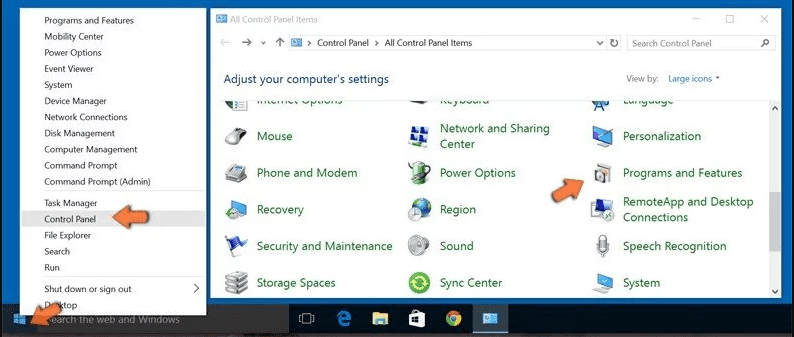
Mac OSX Users
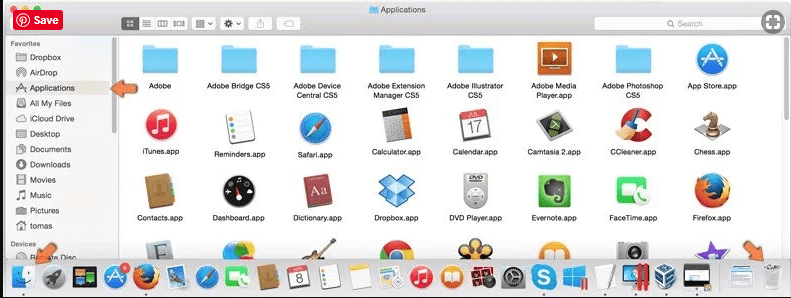
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
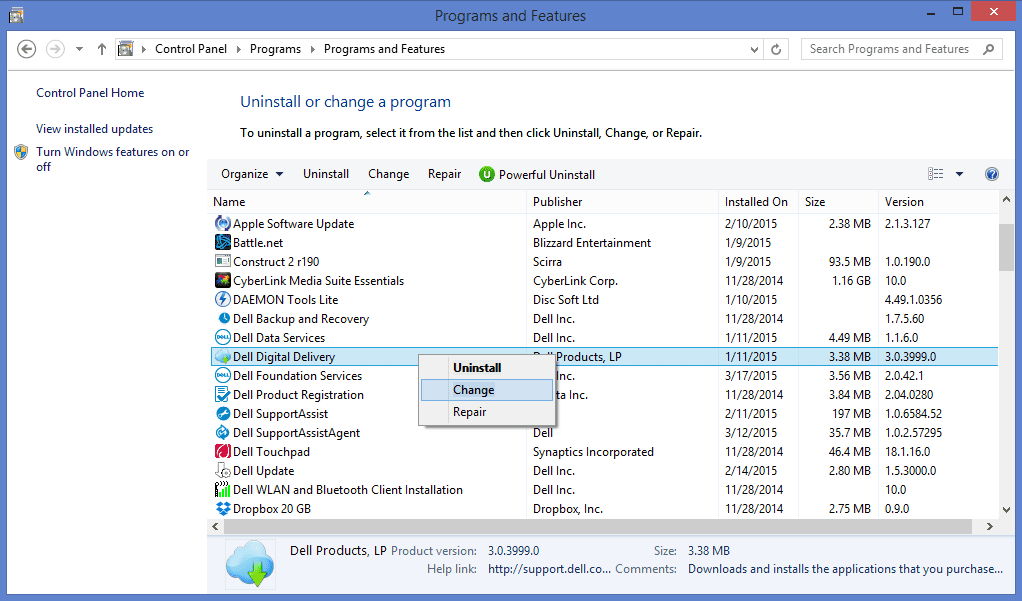
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing This document protected by CloudFlare issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
This document protected by CloudFlare can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and This document protected by CloudFlare has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (This document protected by CloudFlare) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
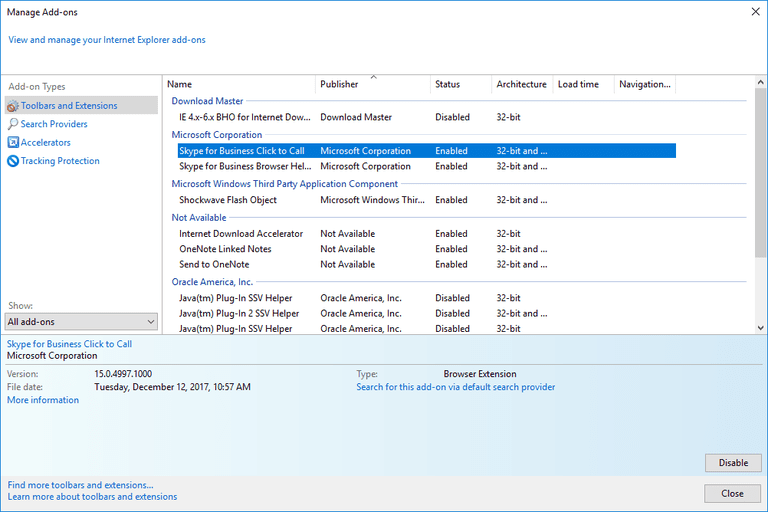
Additional Option
If you still face issues related to This document protected by CloudFlare removal, you can reset the Internet Explorer to its default setting.
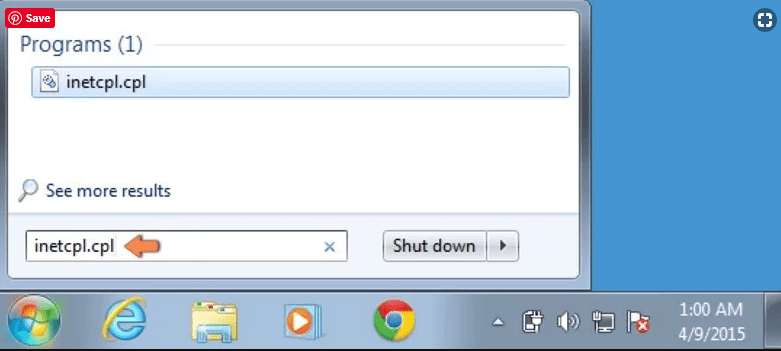
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
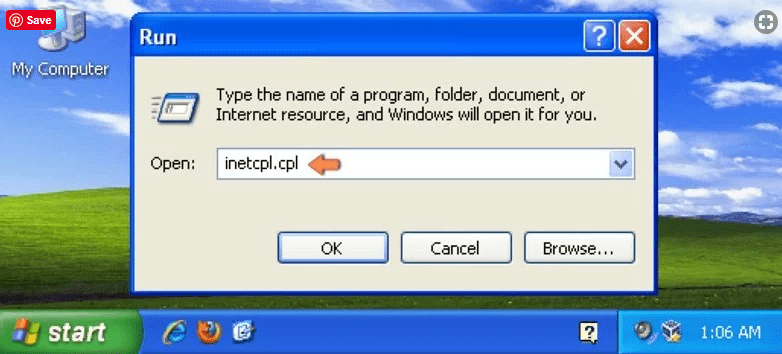
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
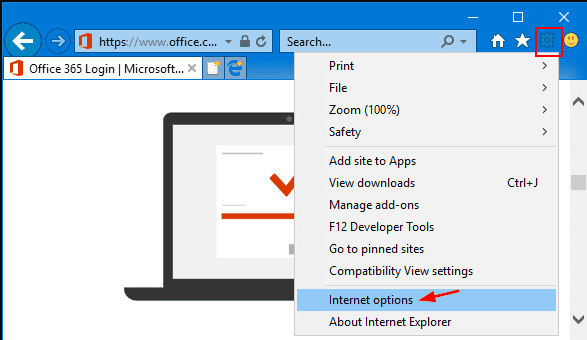
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
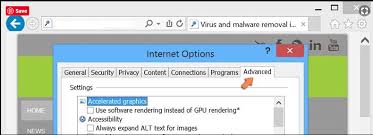
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
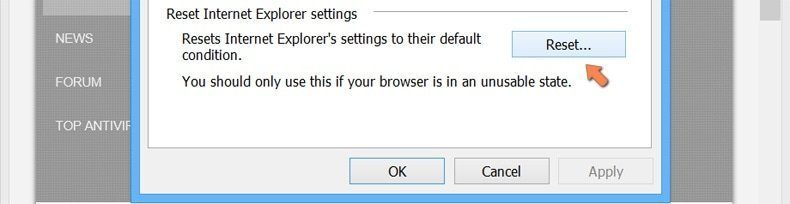
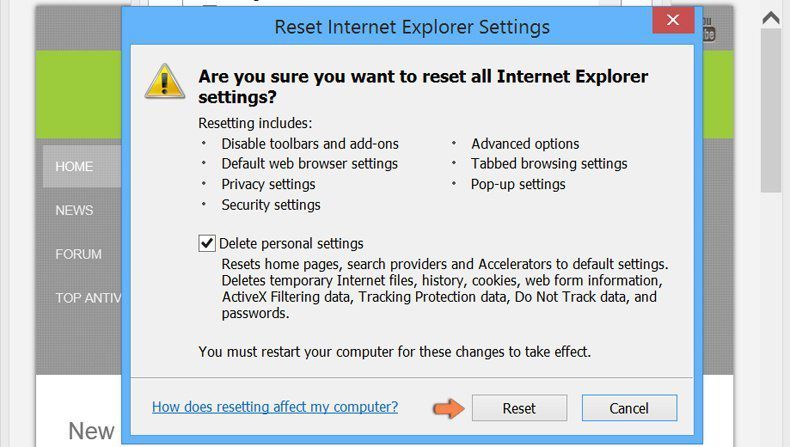
You have to press on the “Reset” button again to confirm that you really want to reset the IE
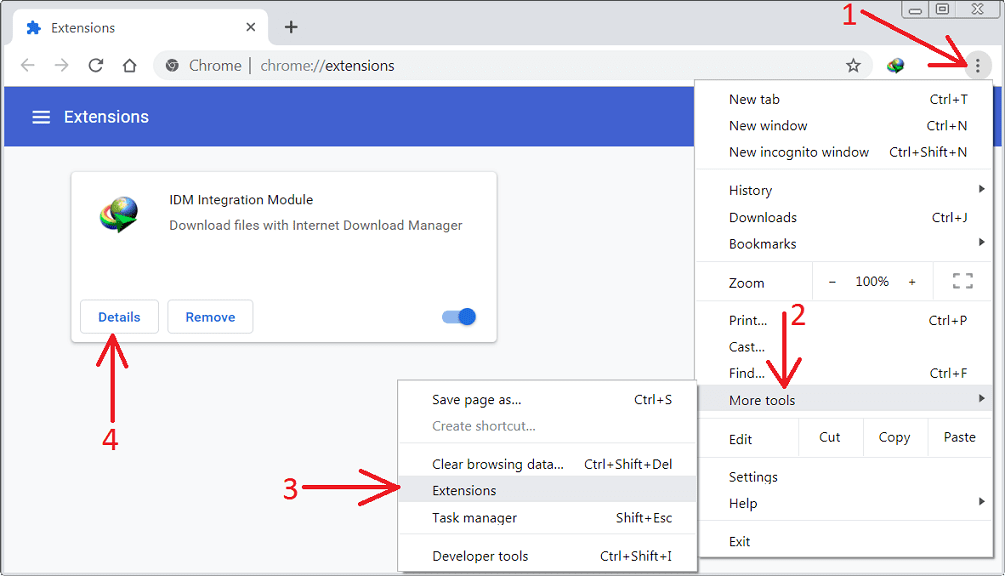
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
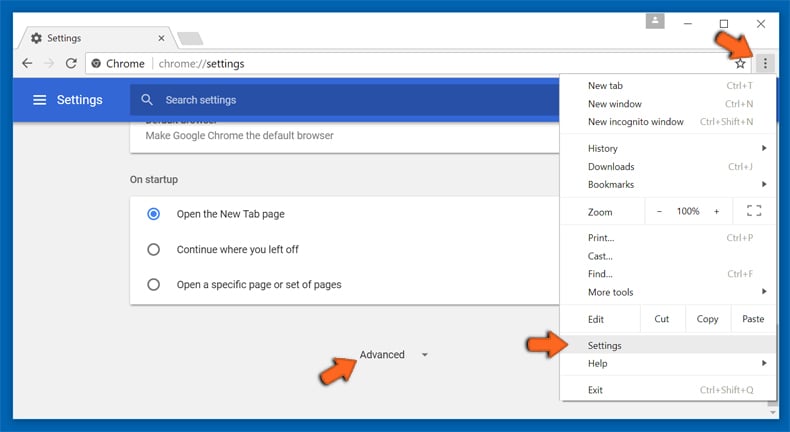
Optional Method
If the problems related to This document protected by CloudFlare still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
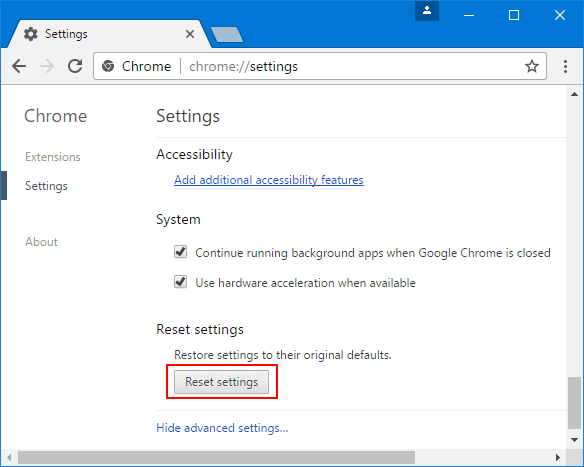
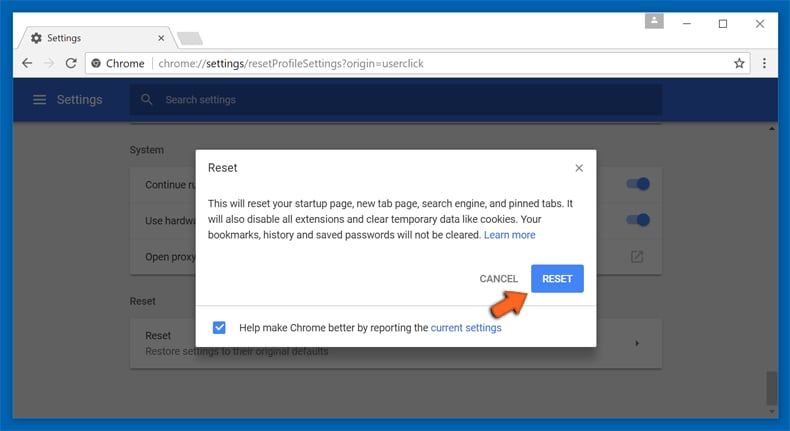
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove This document protected by CloudFlare plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in This document protected by CloudFlare removal then you have the option to rese the settings of Mozilla Firefox.
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
Choose “Troubleshooting Information”
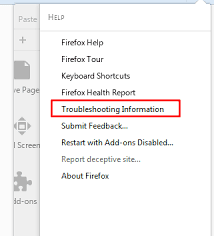
In the newly opened pop-up window, click “Refresh Firefox” button
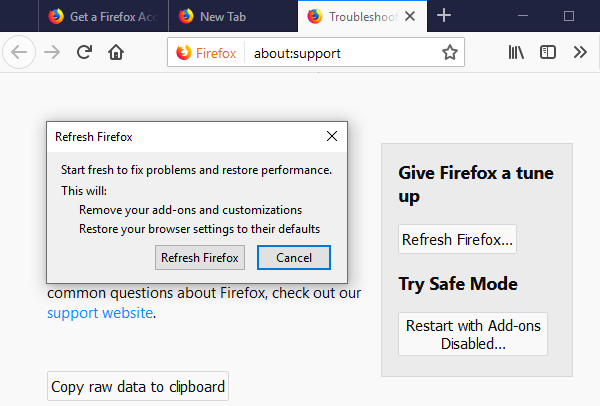
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
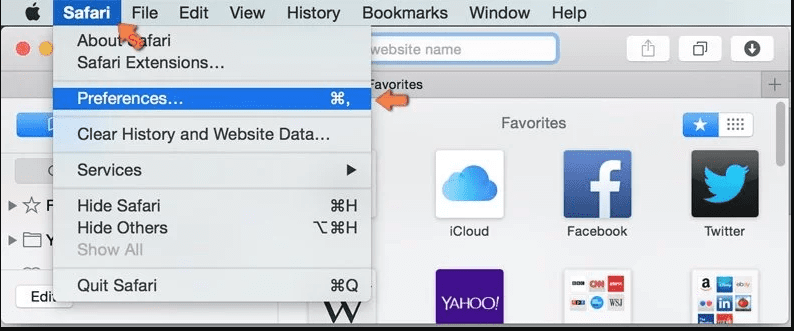
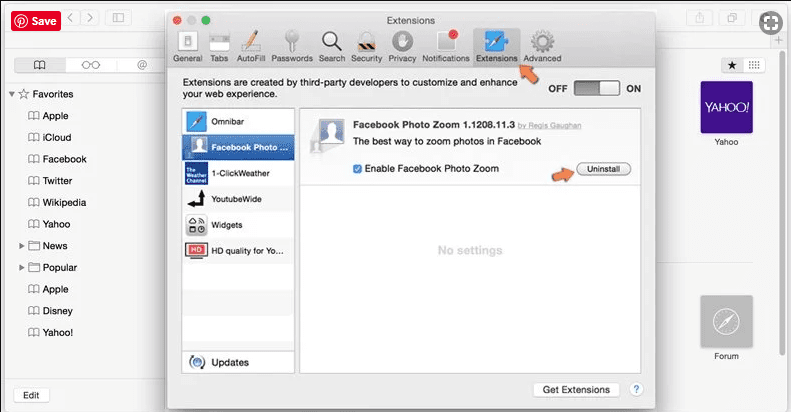
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
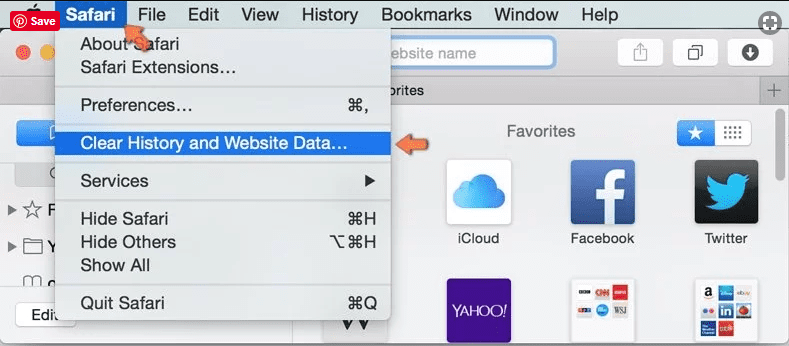
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
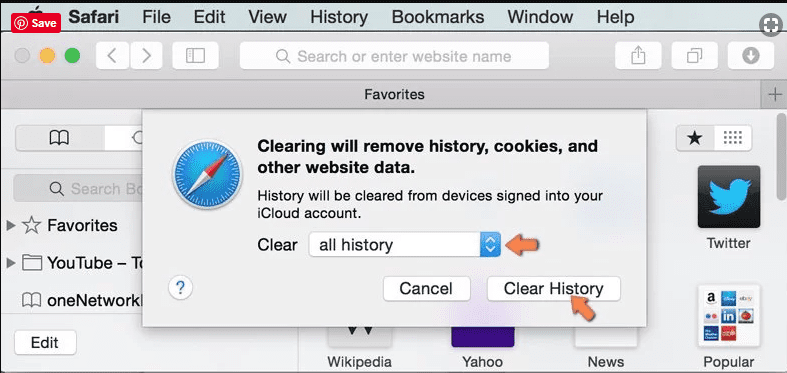
In the newly opened window, select “All History” and then press on “Clear History” option.
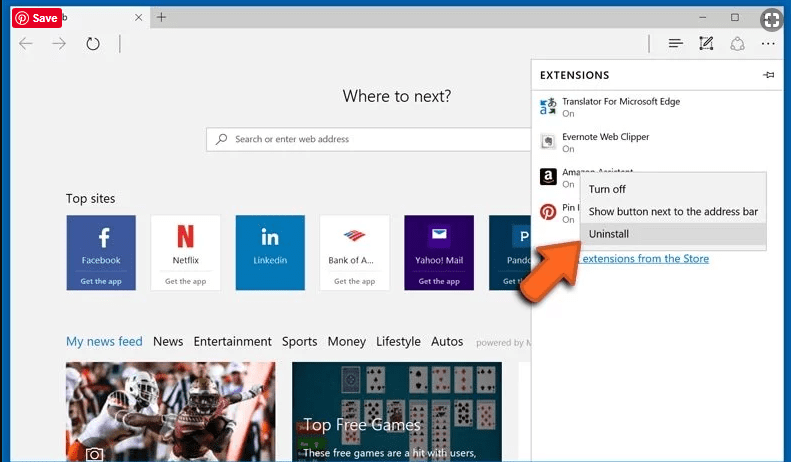
Delete This document protected by CloudFlare (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
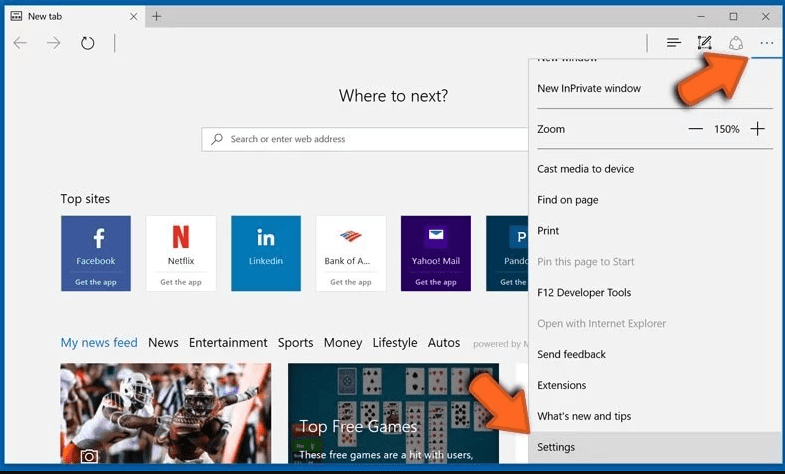
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
Next steps is to click on “Choose what to clear” button
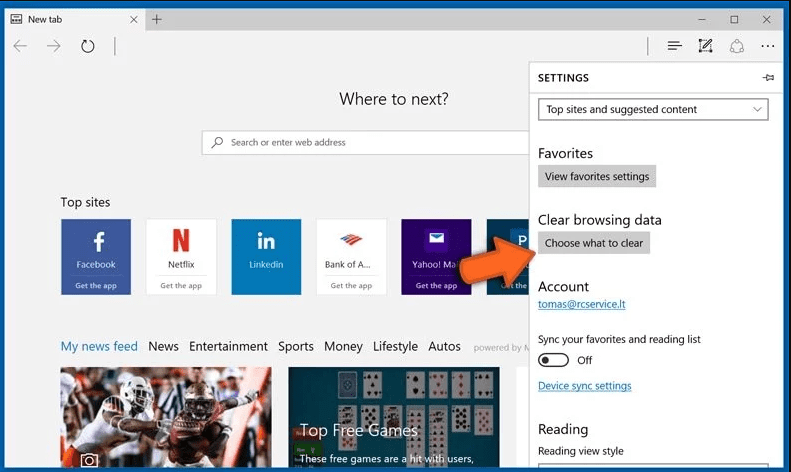
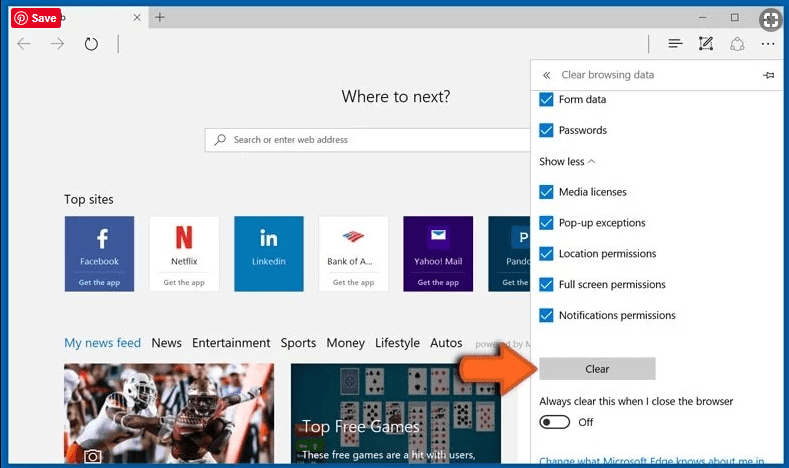
Click on “show more” and then select everything and then press on “Clear” button.
Conclusion
In most cases, the PUPs and adware gets inside the marked PC through unsafe freeware downloads. It is advised that you should only choose developers website only while downloading any kind of free applications. Choose custom or advanced installation process so that you can trace the additional PUPs listed for installation along with the main program.
Special Offer (For Windows)
This document protected by CloudFlare can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and This document protected by CloudFlare has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.



