Remove Restore19 ransomware and recover encrypted files
Complete tips to delete Restore19 ransomware and restore files
Restore19 ransomware is a huge risk ransomware infection designed to encrypt stored files and then demand ransom payment for the decryption, i.e., decryption software. The files encrypted by this ransomware will receive a string of random character and [email protected] as extension. For example, a file 1.jpg would appear something similar to “[email protected]”, “2.jpg” to “[email protected]”, and so on.

The ransom demanding message appears in a text file named “HOW TO RECOVER ENCRYPTED FILES.TXT”). It provides users the instruction how they can contact the crooks behind Restore19 ransomware, pay them the ransom and get the decryption tool and use them. [email protected] email address and a website address link are provided in it for the contacting purpose. Additionally, the message states the users have to contact to the crooks within 24 hours. If not, the attackers will start removing the files one by one on every 24 hours. Moreover, the victims are informed that they have only 72 hours to pay the ransom. After this, the price of the decryption tool will be double (4 times in another 72 hours and so on).
Here is the full text presented in the ransom note displayed/ created by Restore19 ransomware (in Russian and English language):
Добрый день.
Ваши файлы, документы, фото, базы данных и все остальное НЕ УДАЛЕНЫ.
Они зашифрованы WannaCry самым надежным шифрованием.
Восстановить файлы НЕВОЗМОЖНО без нашей помощи.
Будете пытаться восстановить файлы самостоятельно- потеряете файлы
НАВСЕГДА.
———————————————————-
Востановить файлы Вы сможете так:
- связаться с нами по e-mail: [email protected]
* сообщите Ваш ID и мы выключим произвольное удаление файлов
(если не сообщите Ваш ID идентификатор, то каждые 24 часа будет
удаляться по 24 файла. Если сообщите ID- мы выключим это)
* высылаете Ваш идентификатор ID и 2 файла, размером до 1 мб каждый.
Мы их расшифровываем, в доказательство возможности расшифровки.
также получаете инструкцию куда и сколько нужно заплатить.
- оплачиваете и подтверждаете оплату.
- после оплаты получаете программу ДЕШИФРАТОР. которой восстанавливаете ВСЕ ВАШИ ФАЙЛЫ.
———————————————————-
У Вас есть 72 часа на оплату.
Если не успеете за 72 часа оплатить, то цена расшифровки увеличивается в 2 раза.
Цена увеличивается в 2 раза каждые 72 часа.
Если не оплатите в течении 7 суток- Ваши файлы будут удалены навсегда.
Чтобы восстановить файлы, без потерь, и по минимальному тарифу, Вы должны оплатить в течении 72 часов.
За подробными инструкциями обращайтесь e-mail: [email protected]
* Если не будете терять время на попытки расшифровать, то сможете восстановить все файлы за час.
* Если будете пытаться сами расшифровать- можете потерять Ваши файлы НАВСЕГДА.
* Дешифраторы других пользователей несовместимы с Вашими данными, так как у каждого пользователя
уникальный ключ шифрования
—————— P.S. ———————————
Если связаться через почту не получается
* Зарегистрируйтесь на сайте hxxp://bitmsg.me (сервис онлайн отправки Bitmessage)
* Напишите письмо на адрес BM-2cVChsbUqL5H1nw98qrwbQkzdE1UqCs8nH с указанием Вашей почты и
личного идентификатора и мы с Вами сами свяжемся.
Если у Вас нет биткойнов
* Создайте кошелек Bitcoin: hxxps://blockchain.info/ru/wallet/new
* Приобретите криптовалюту Bitcoin удобным способом:
hxxps://localbitcoins.com/ru/buy_bitcoins (Visa/MasterCard, QIWI Visa Wallet и др.)
hxxps://ru.bitcoin.it/wiki/Приобретение_биткойнов (инструкция для новичков)
– Не имеет смысла жаловаться на нас и устраивать истерику.
– Жалобами заблокировав e-mail, Вы лишаете возможность остальных, расшифровать свои компьютеры.
Остальных, у кого также зашифрованы компьютеры Вы лишаете ЕДИНСТВЕННОЙ НАДЕЖДЫ расшифровать. НАВСЕГДА.
– Просто войдите с нами в контакт, оговорим условия расшифровки файлов и доступной оплаты,
в дружественной обстановке.
———————————————————
Ваш Идентификатор:
–
=========================================================
Hello.
Your files, documents, photo, databases and all the rest aren’t REMOVED.
They are ciphered by WannaCry the most reliable enciphering.
It is impossible to restore files without our help.
You will try to restore files independent you will lose files
FOREVER.
———————————————————-
You will be able to restore files so:
- to contact us by e-mail: [email protected]
* report your ID and we will switch off any removal of files
(if don’t report your ID identifier, then each 24 hours will be
to be removed on 24 files. If report to ID-we will switch off it)
* you send your ID identifier and 2 files, up to 1 MB in size everyone.
We decipher them, as proof of a possibility of interpretation.
also you receive the instruction where and how many it is necessary to pay.
- you pay and confirm payment.
- after payment you receive the DECODER program. which you restore ALL YOUR FILES.
———————————————————-
You have 72 hours on payment.
If you don’t manage to pay in 72 hours, then the price of interpretation increases twice.
The price increases twice each 72 hours.
To restore files, without loss, and on the minimum tariff, you have to pay within 72 hours.
Address for detailed instructions e-mail: [email protected]
* If you don’t waste time for attempts to decipher, then you will be able to restore all files in 1 hour.
* If you try to decipher – you can FOREVER lose your files.
* Decoders of other users are incompatible with your data as at each user
unique key of enciphering
—————— P.S. ———————————-
If it is impossible to communicate through mail
* Be registered on the website hxxp://bitmsg.me (service online of sending Bitmessage)
* Write the letter to the address BM-2cVChsbUqL5H1nw98qrwbQkzdE1UqCs8nH with the indication of your mail and
the personal identifier and we will communicate.
If you have no bitcoins
* Create Bitcoin purse: hxxps://blockchain.info/ru/wallet/new
* Buy Bitcoin in the convenient way:
hxxps://localbitcoins.com/ru/buy_bitcoins (Visa/MasterCard, QIWI Visa Wallet, etc.)
hxxps://ru.bitcoin.it/wiki/Priobreteniye_bitkoynov (the instruction for beginners)
– It doesn’t make sense to complain of us and to arrange a hysterics.
– Complaints having blocked e-mail, you deprive a possibility of the others, to decipher the computers.
Other people at whom computers are also ciphered you deprive of the ONLY hope to decipher. FOREVER.
– Just contact with us, we will stipulate conditions of interpretation of files and available payment,
in a friendly situation.
———————————————————
Your Identifier
Unfortunately, without the involvement of crooks behind it, the files decryption is not possible – these people have the unique decryption key/ tool that they store on some remote server. Cyber security researchers are trying to crack the code used and develop free decryption software – however, they haven’t succeed in it yet. In such a case, you need to think of some other alternatives such as existing backups, Shadow Copies or data recovery tools. Paying/contacting the crooks is highly not recommended – these people are not reliable. They often disappear, leaving the victims without their files, once the payment is received.
Backups – best option to recover encrypted files
Backups you have are the best option to recover the files that got infected. Simply remove Restore19 ransomware and use the back to restore the files in earlier accessible condition. The problem is that not all users have such a backup option available. They still have at least two alternatives – use shadow copies or download any third party recovery tool. Shadow Copies are automatically created backup from OS. In some cases, ransomware left this option untouched during the system attack and files recovery process – you will complete guide on how to recover the files using this option just below the post in the data recovery section.
How did Restore19 ransomware infiltrate my computer?
It is common that ransomware viruses are distributed through spam email campaigns, Trojans, untrustworthy downloading channels, fake software updaters and unofficial activation tools. Mal-spam is used to send spam emails by thousands. These letters contain infectious files or links for such files as attachments, if clicked- the malicious malware download/ installation process is triggered. Trojans are malicious applications especially designed to cause chain infection on already infected computers. Untrustworthy downloading channels spread malware by presenting it as legit software. Some examples of untrustworthy sources are p2p networks, free file hosting sites and third party downloaders/ installers. Fake software updaters/ unofficial software activation tool exploit bugs/ flaws of outdated software or directly download malware instead of providing updates.
How to prevent ransomware intrusion?
Installed programs should always be downloaded from official websites and direct links. No third party, unofficial tools should be used for software update/ activation. It is common that these tools are malicious. Moreover, it is not legal to use unofficial tools to activate licensed programs or use pirated, hacked programs. Further, website links and any attachment files presented on any emails whose senders’ addresses seem suspicious should never be clicked. A computer should always have a reputable antivirus tool installed and kept updated. Also, this software should be used in regular basic for virus detection and their removal.
Special Offer (For Windows)
Restore19 ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove Restore19 ransomware through “Safe Mode with Networking”
Step 2: Delete Restore19 ransomware using “System Restore”
Step 1: Remove Restore19 ransomware through “Safe Mode with Networking”
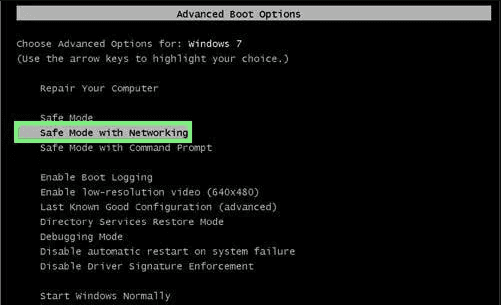
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
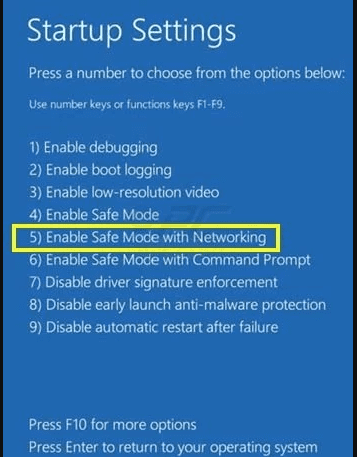
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
Step 2: Delete Restore19 ransomware using “System Restore”
Log-in to the account infected with Restore19 ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
Restore19 ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
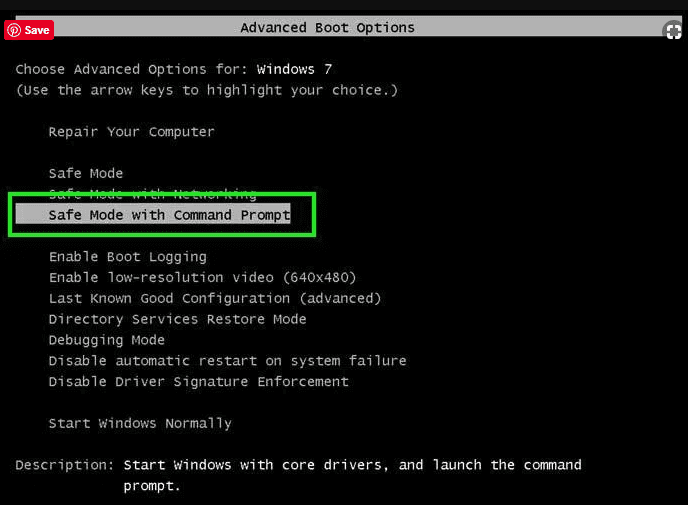
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
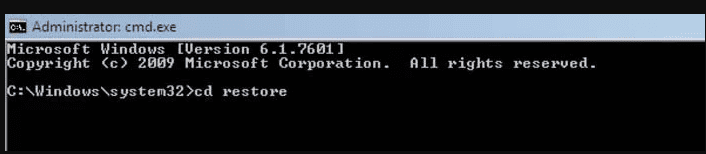
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
- Type: rstrui.exe and Press “ENTER”
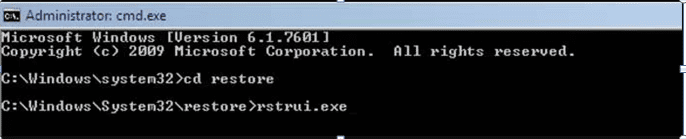
- Click “Next” on the new windows
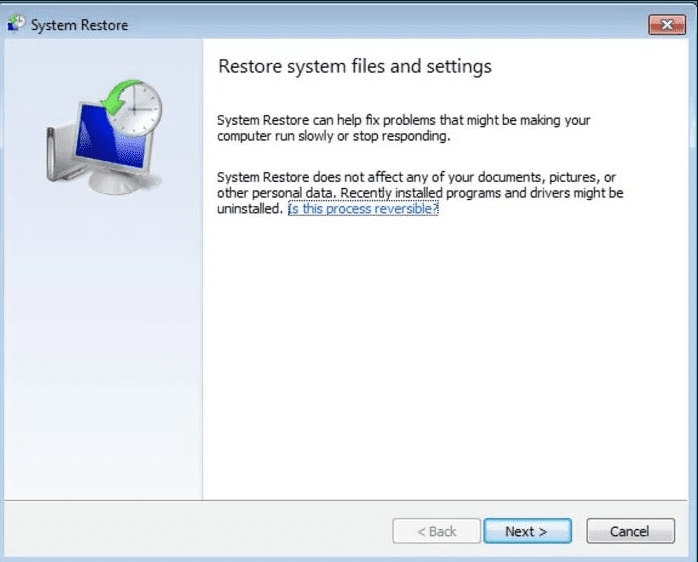
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to Restore19 ransomware infiltration in the PC.
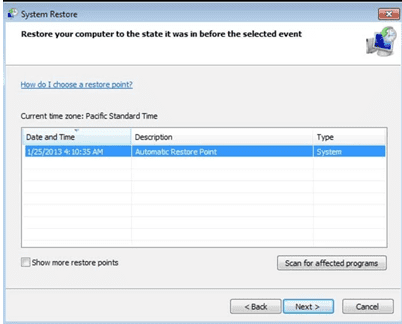
- In the newly opened windows, press on “Yes”.
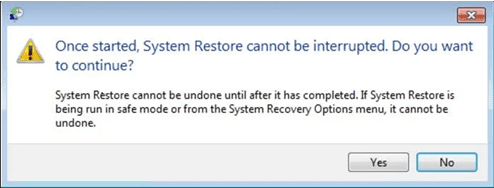
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove Restore19 ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of Restore19 ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
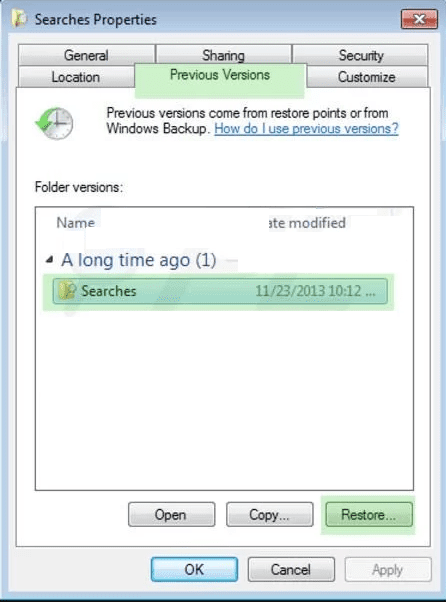
How to Restore Individual Encrypted File:
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
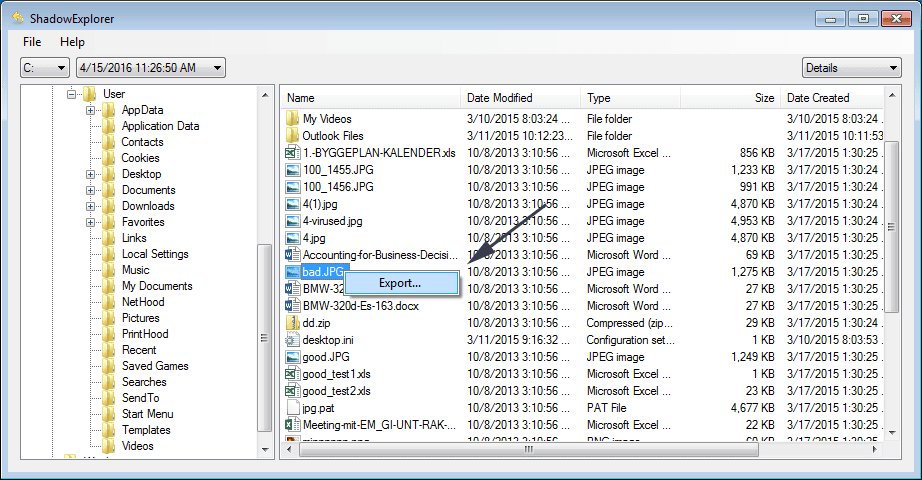
In order to access the files encrypted by Restore19 ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like Restore19 ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
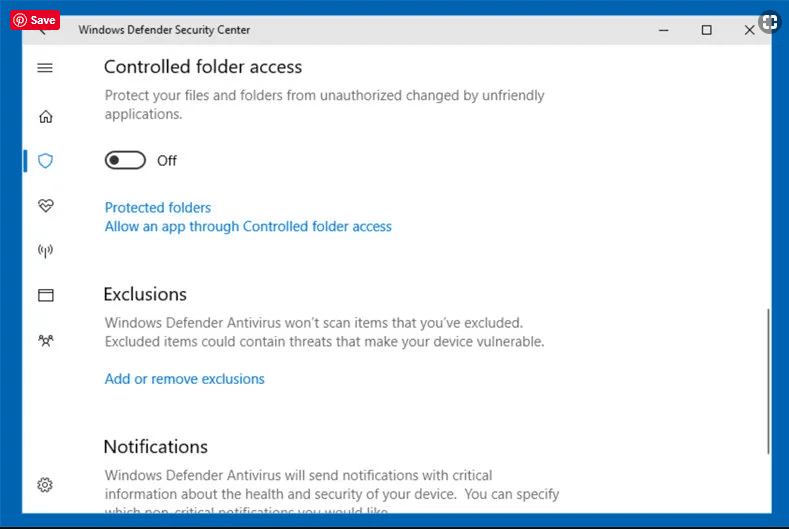
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by Restore19 ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with Restore19 ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove Restore19 ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

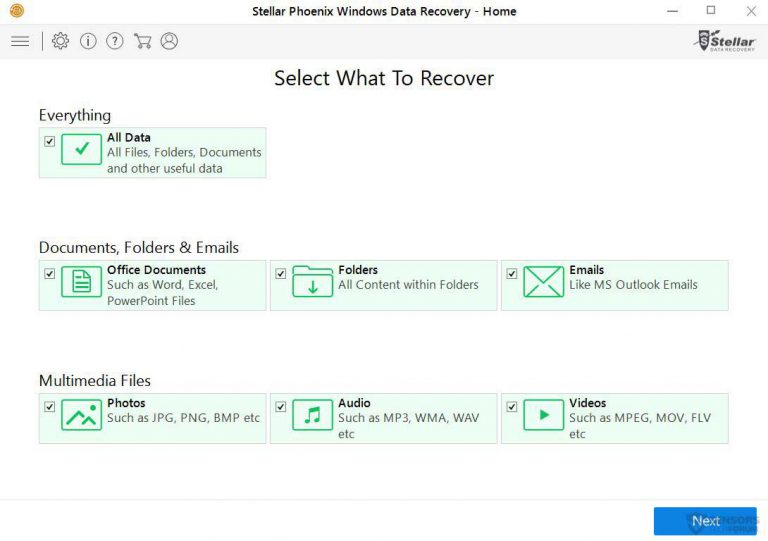
Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
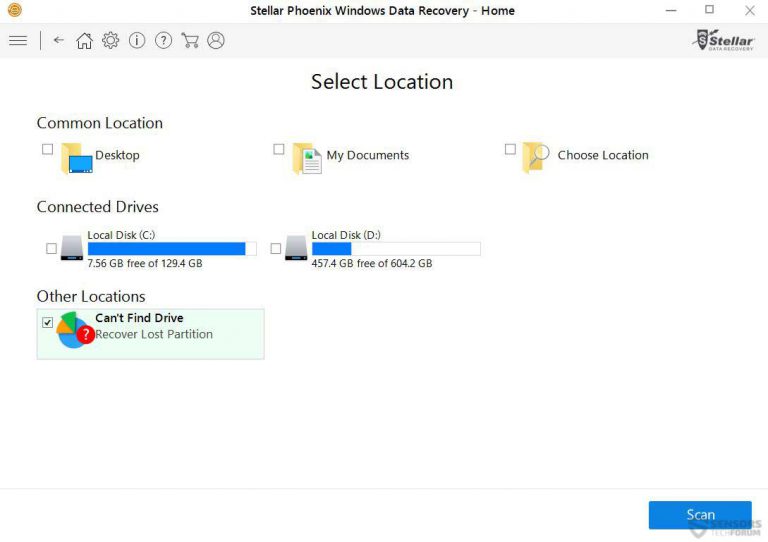
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
Restore19 ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.