Remove Im in possession of all of your private data Email Scam
Im in possession of all of your private data Email Scam Virus: Simple Uninstall Guide
Im in possession of all of your private data Email Scam is the sextortion note which states about a sexually explicit video of the recipients that can become public if they don’t pay the demanded amount. Emails that utilize this scam model have three known variants of the phishing messages used by them, and all of them make the same claim. The mail’s claim is false; no any video of the user has been obtained by scammers. These are common scamming campaigns which target rookie users aiming to make a profit from them.

More About Im in possession of all of your private data Email Scam:
Im in possession of all of your private data Email Scam involves money demands, that usually revolves around cryptocurrency. Analyzed samples show that 660/680 EUR or 800 USD is the amount asked from victims in Bitcoin cryptocurrency within 21 to 26 hours. The three versions of this scam letters differ little. The general through-line contains: claims of a system infection originated from an adult-themed site, explanations for poor grammar, use of the hijacked webcam to record a compromising video of the recipient, and the ransom demands.
In addition, the “Im in possession of all of your private data Email Scam” letters also mention that the recipients’ contact data has been exfiltrated. In case they don’t make the ransom payment, the recorded video will be sent to their contacts. We expressly advise to ignore the notification and delete mail from the inbox completely, so criminals cannot access any information on the device or your email box when you click on something without noticing. These letters are not real messages from scammers or the person which has any private data of you.
Im in possession of all of your private data Email Scam aims to get your cryptocurrency exchange platforms or deceive you into tapping on some vicious online links and content where you can get exposed to serious hazardous material. Avoid any interaction to keep the work-station safe. Such emails should not be considered authentic or real because there are only a few chances that criminals managed to hack your PC or webcam, other functions. Such campaigns spread around and make a profit from rookie users who decide to pay instead of having their video leaked or made public. Im in possession of all of your private data Email Scam or similar dodges can also be utilized to propagate notorious computer viruses that may steal data, infect personal files, increase usage of system resources, and so forth.
How Does The Threat Spread?
Malware spread through malspam campaign enter the PC systems when recipients download and open the malicious files attached to those mails. These deceptive mails are presented as ‘important’, ‘crucial’, or ‘official’, or pretend to be from some legitimate companies or other entities. However, this is just a trick used by threat actors to deceive recipients into infecting their systems with dangerous viruses. Virulent files attached to these letters could be in multiple formats, e.g., PDF and Microsoft Office documents, archives, executables, JavaScript, etc.
To avoid such intrusions, it is strongly advised against opening files attached to suspicious or irrelevant emails coming from unknown senders. Moreover, be very careful when downloading/installing freeware. Choose only official and verified download sources and stay away from Peer-to-peer networks, untrustworthy channels, and other third-party downloaders. But at the moment, you must remove Im in possession of all of your private data Email Scam virus from the PC without wasting any time.
Message Presented In All Variants Of Scam Letters:
Subject: If you want us to be silent, read
Hi,
Hope u will not really mind my english language sentence structure, since
im from Philippines. I infected your device with a virus and im in
possession of all of your private data from your os.
It was set up on an adult webpage and after that you have selected the
video clip, clicked on it, my application instantly gain access to your
system.
Next, your webcam documented you hand fucking, in addition i captured a
video that you’ve looked at.
Immediately after a short while in addition, it pulled out all of your
social contact info. If you ever wish me to remove your all that i currently
have – transfer me 660 eu in btc it is a crypto. This is my btc wallet
number – bc1qk06ykg8v97r6pylak0vae9azvnzrkgm9mt97z5
At this moment you will have 21 hours. to make a decision When i will
receive the transaction i will wipe out this video and every thing
completely. If not, you should be sure that the footage is going to be
submitted to your contacts.
Do Not Reply to This Email
Im in possession of all of your private data Email Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Im in possession of all of your private data Email Scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
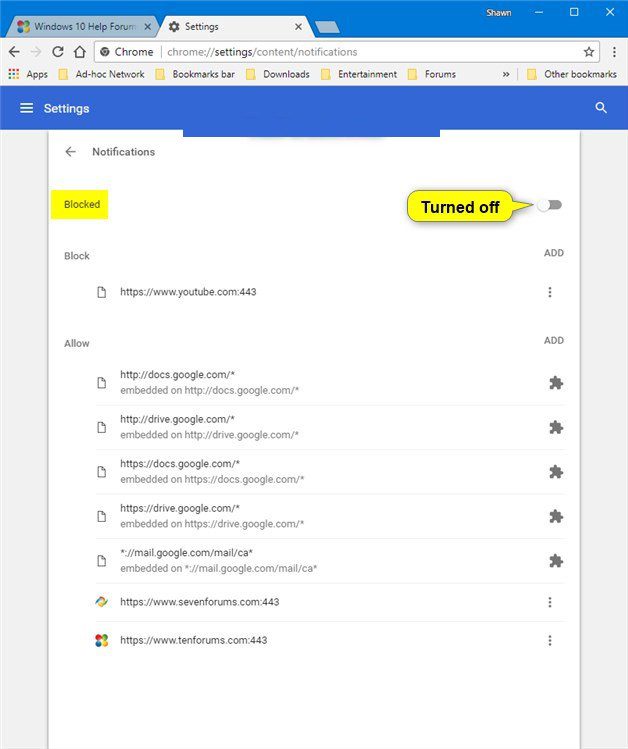
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
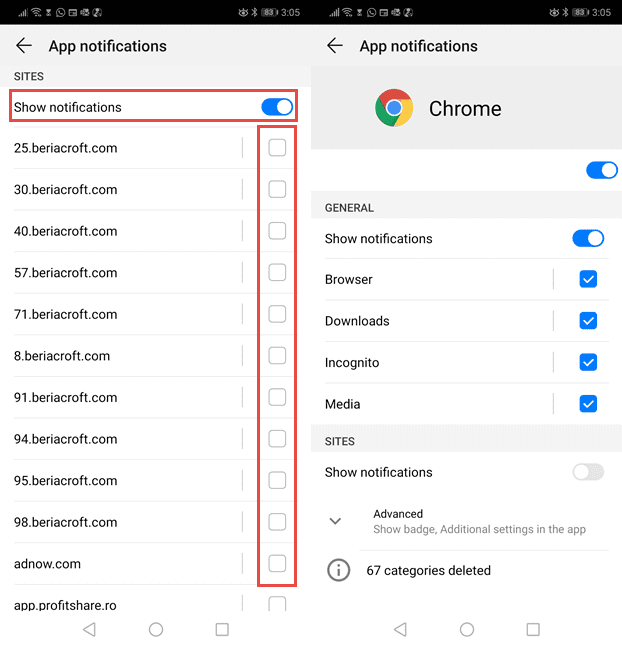
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
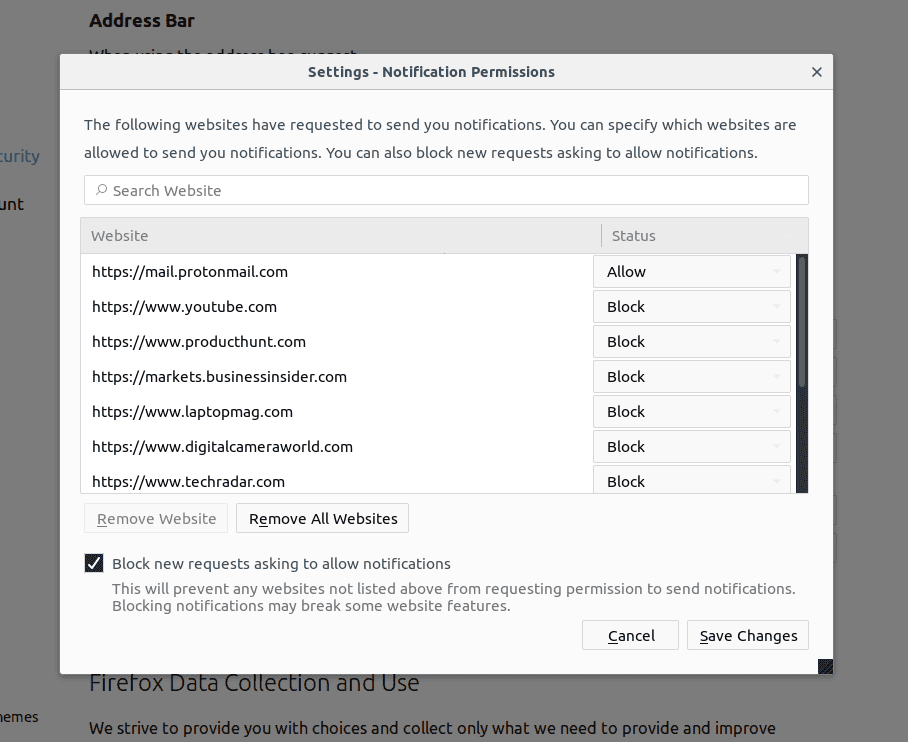
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
Internet Explorer
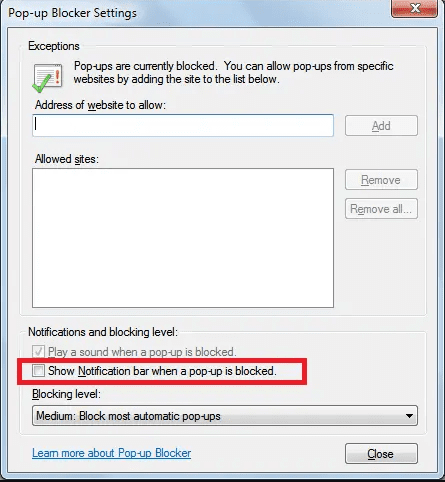
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
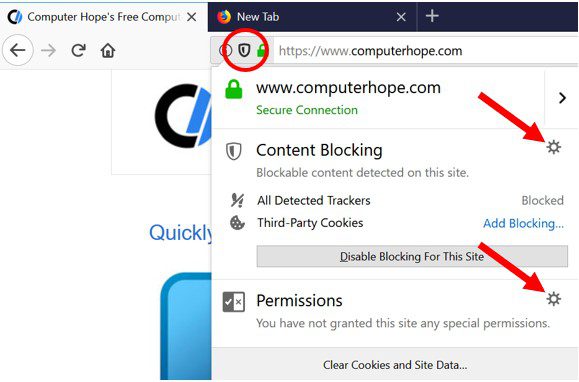
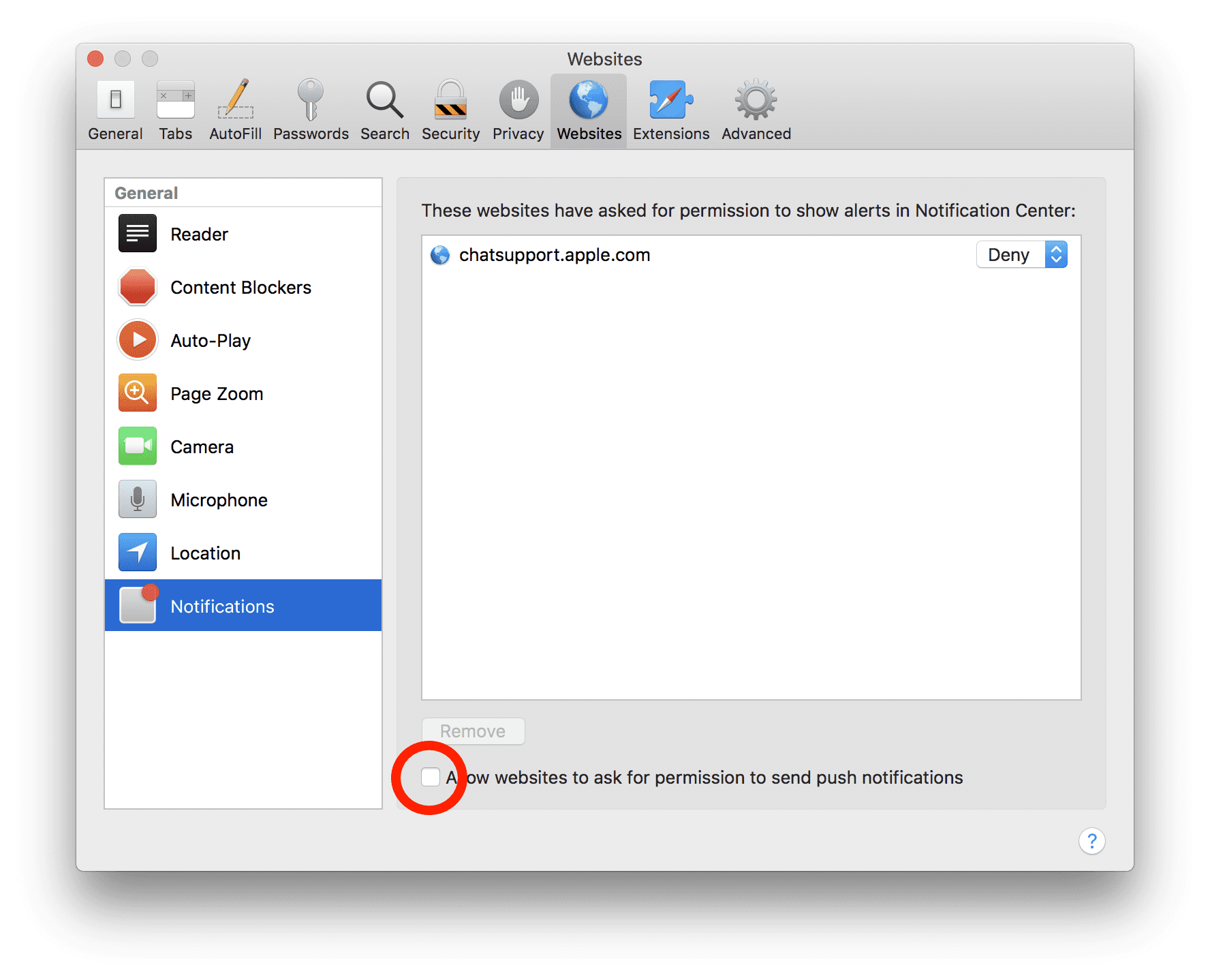
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Im in possession of all of your private data Email Scam :
Remove the related items of Im in possession of all of your private data Email Scam using Control-Panel
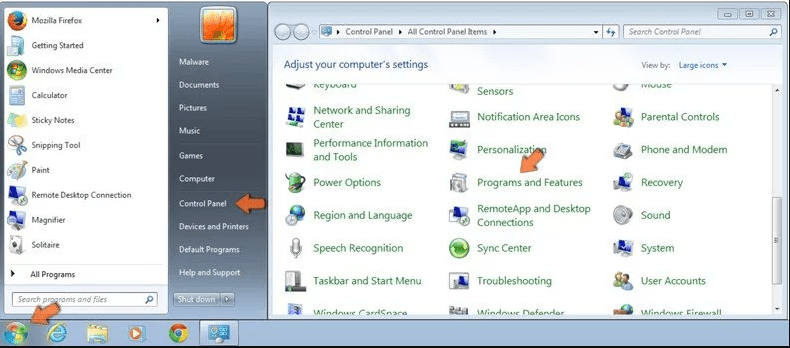
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
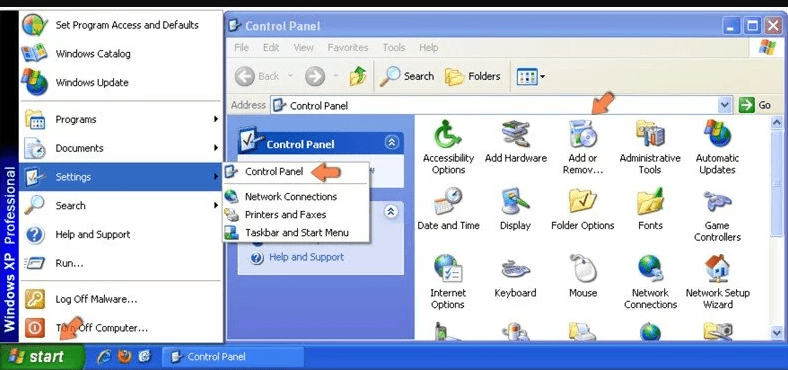
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
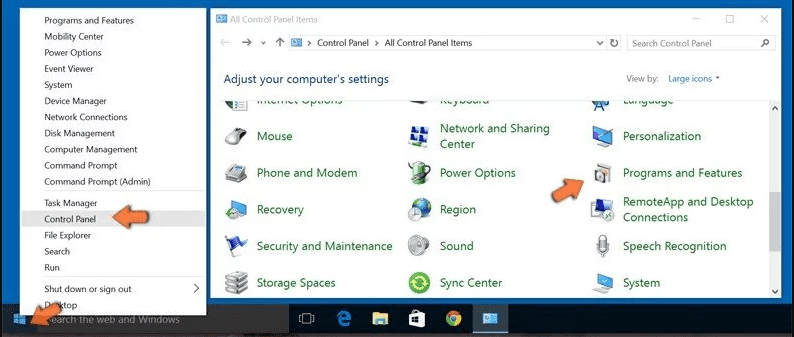
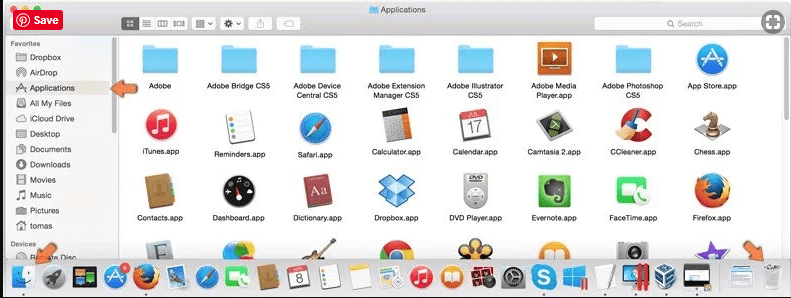
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
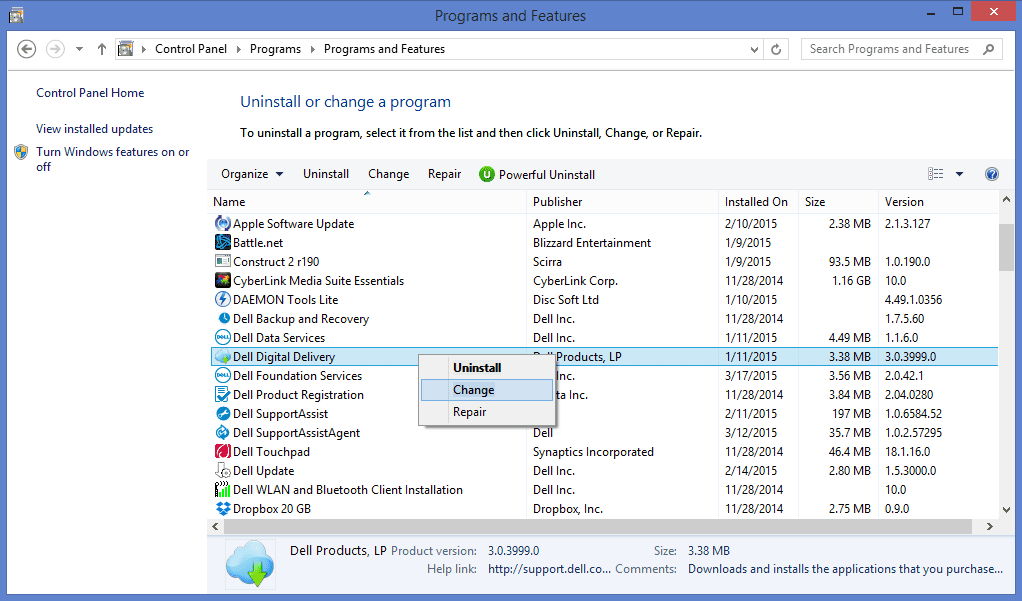
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Im in possession of all of your private data Email Scam issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Im in possession of all of your private data Email Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Im in possession of all of your private data Email Scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Im in possession of all of your private data Email Scam ) from Internet Browsers
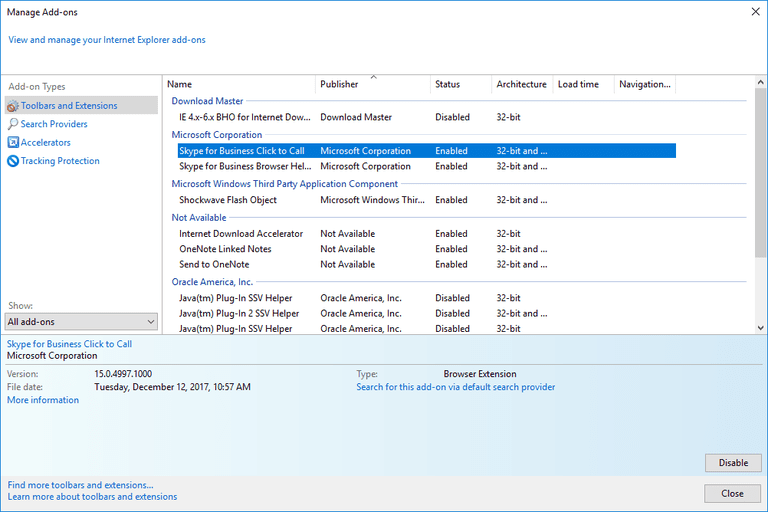
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
Additional Option
If you still face issues related to Im in possession of all of your private data Email Scam removal, you can reset the Internet Explorer to its default setting.
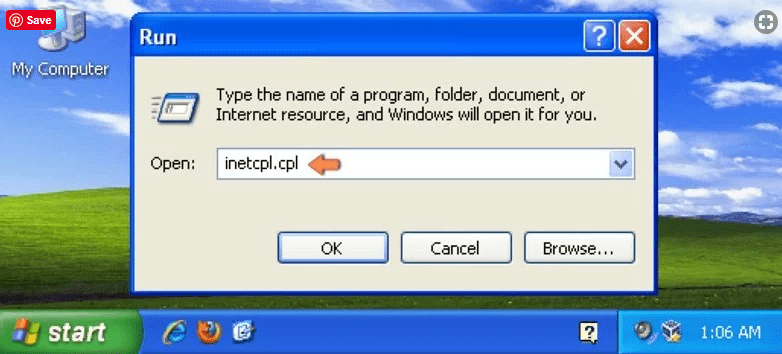
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
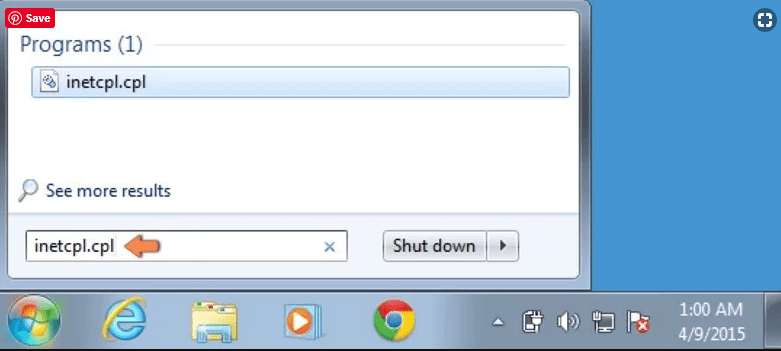
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
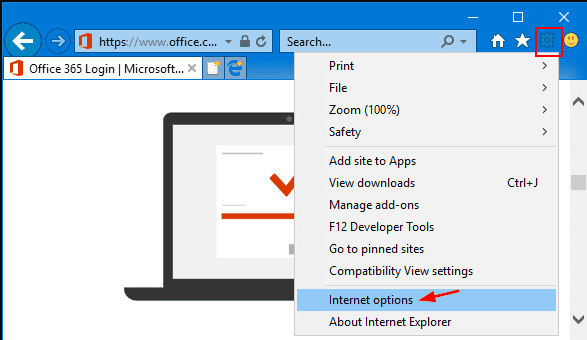
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
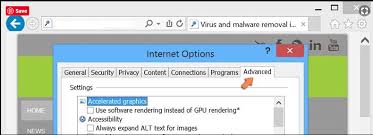
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
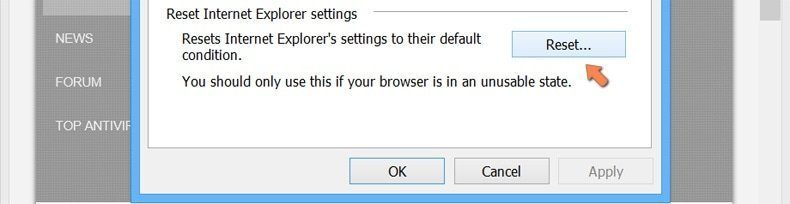
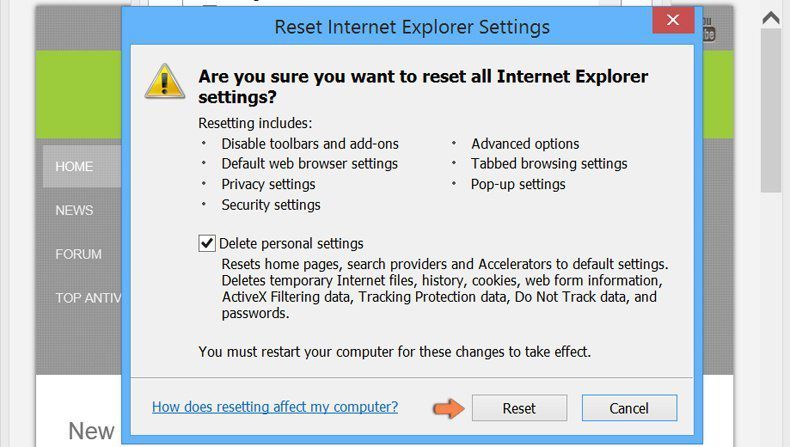
You have to press on the “Reset” button again to confirm that you really want to reset the IE
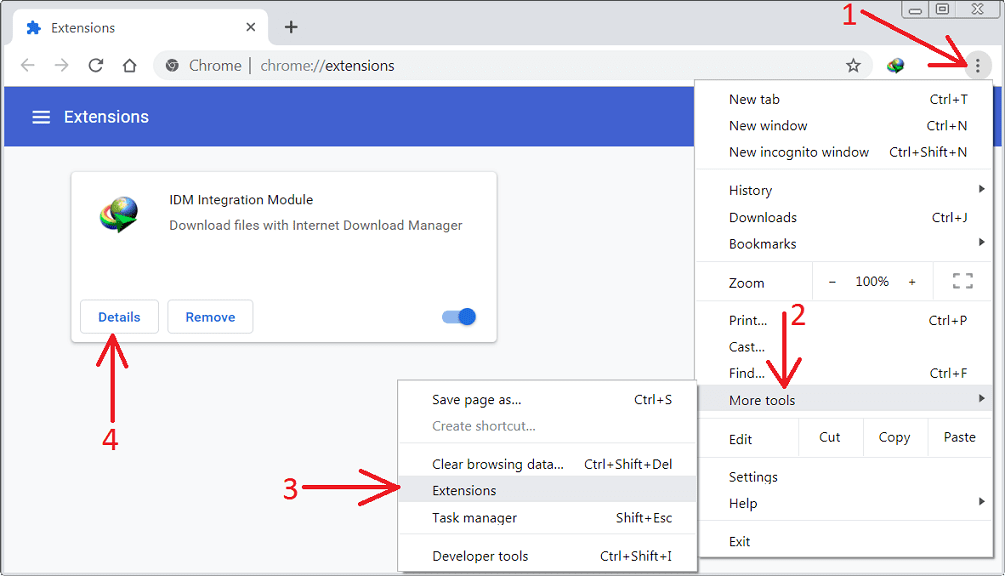
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
Optional Method
If the problems related to Im in possession of all of your private data Email Scam still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
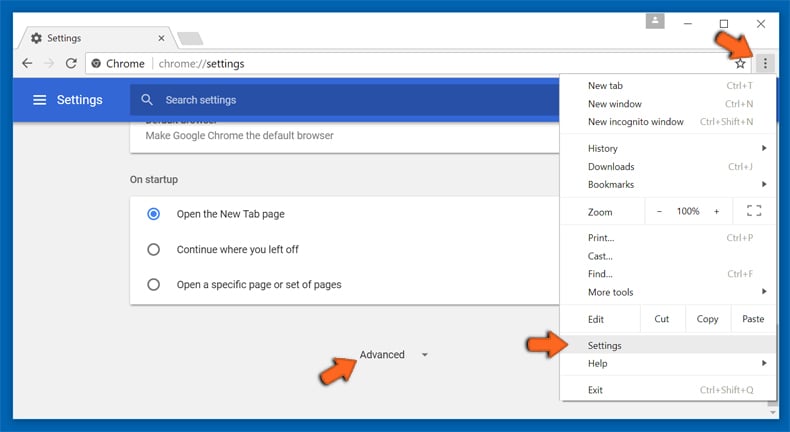
At the bottom, notice the “Reset” option and click on it.
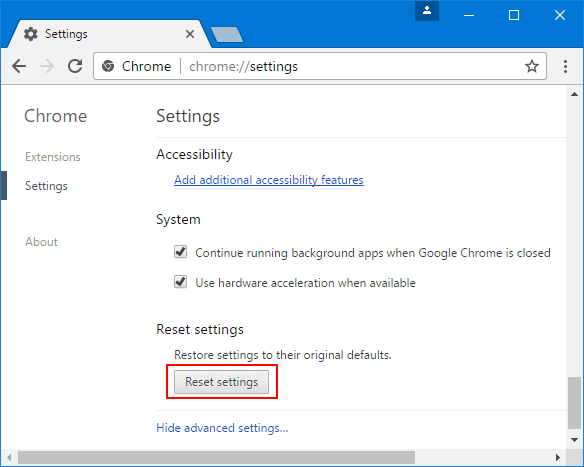
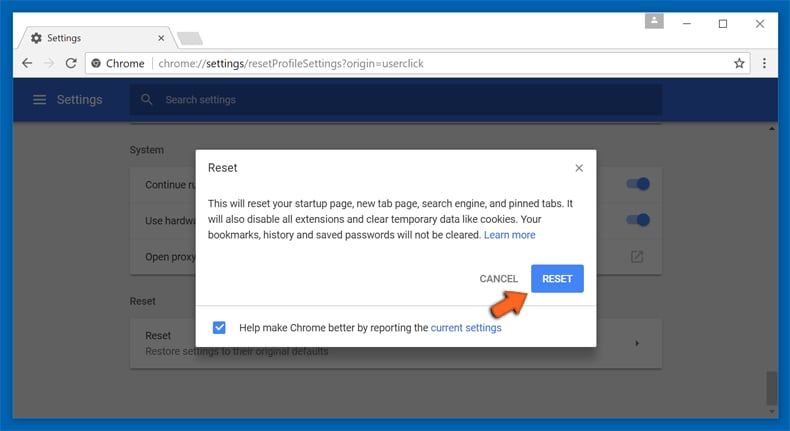
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove Im in possession of all of your private data Email Scam plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Im in possession of all of your private data Email Scam removal then you have the option to rese the settings of Mozilla Firefox.
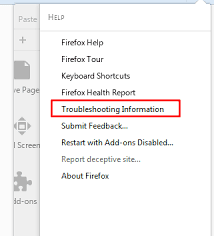
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
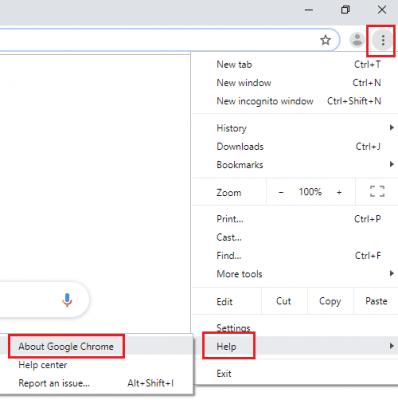
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
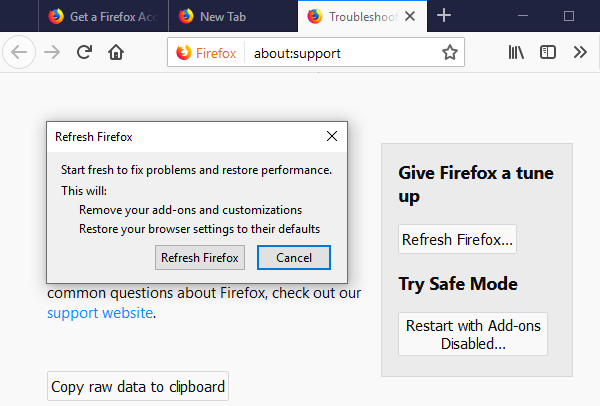
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
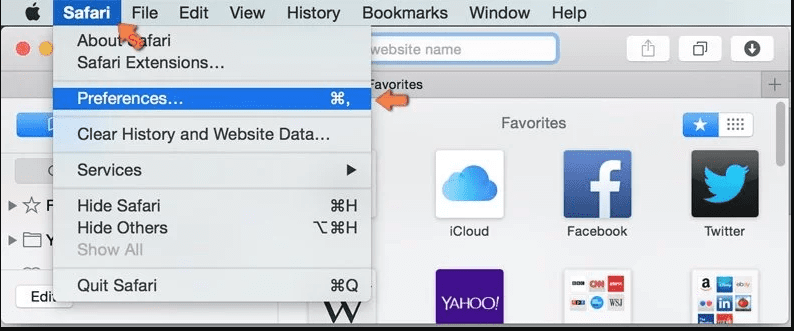
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
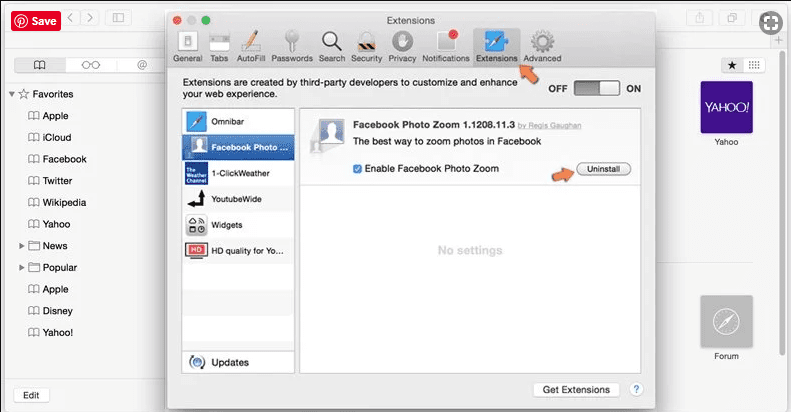
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
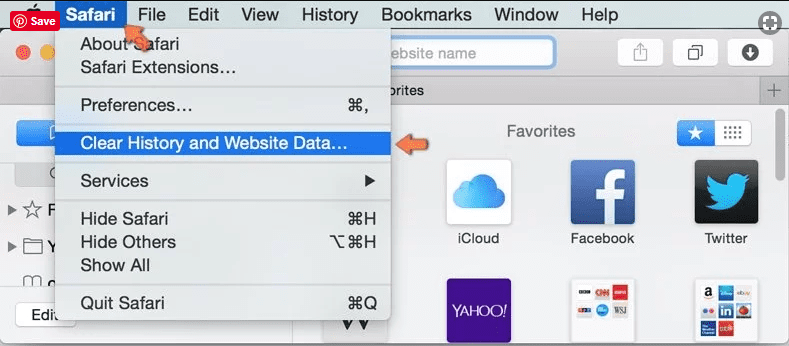
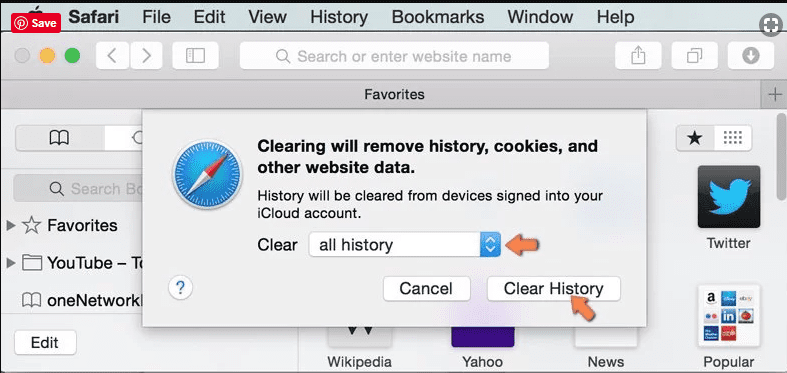
In the newly opened window, select “All History” and then press on “Clear History” option.
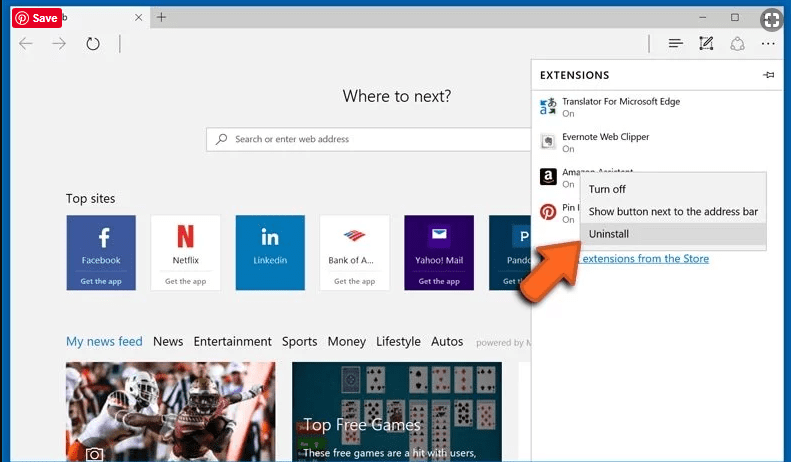
Delete Im in possession of all of your private data Email Scam (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
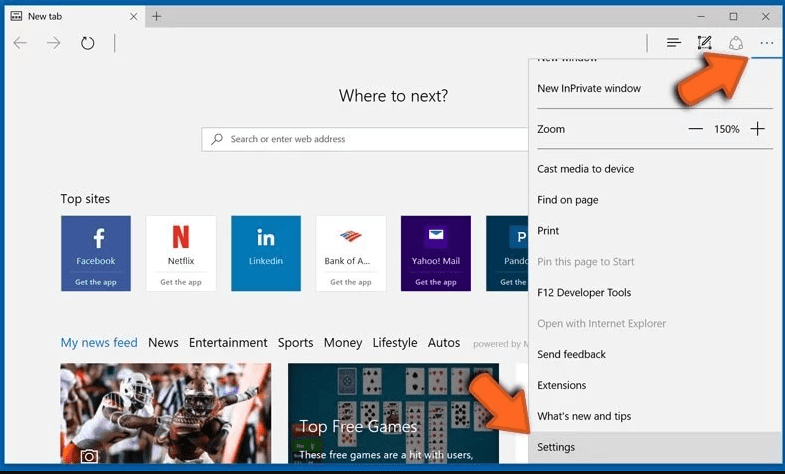
Next steps is to click on “Choose what to clear” button
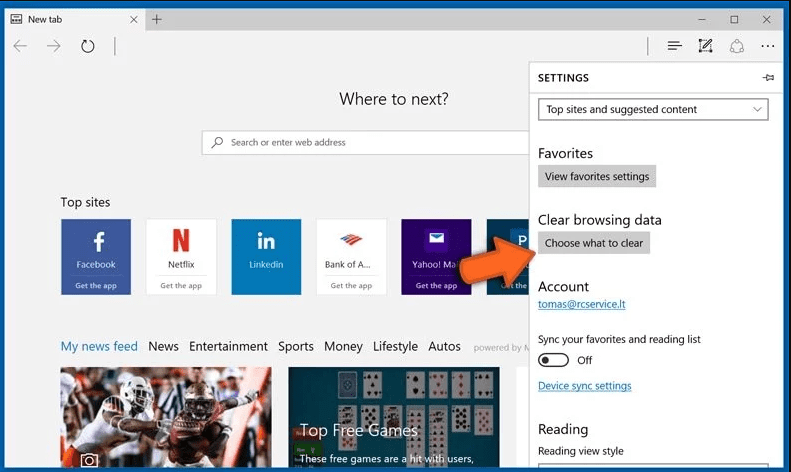
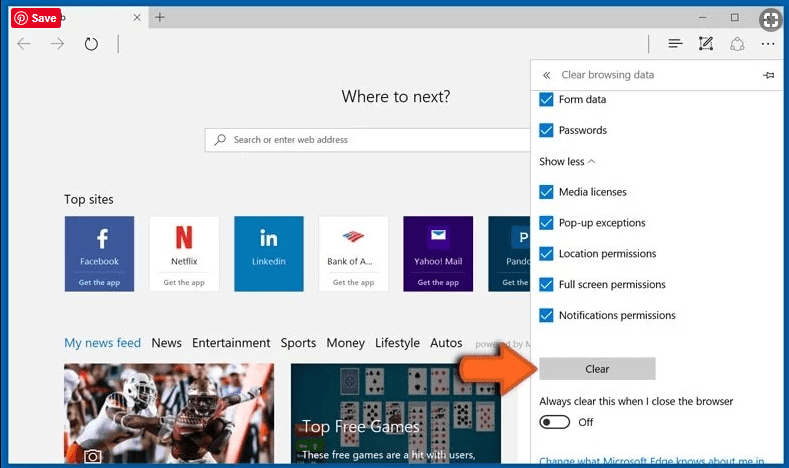
Click on “show more” and then select everything and then press on “Clear” button.
Conclusion
In most cases, the PUPs and adware gets inside the marked PC through unsafe freeware downloads. It is advised that you should only choose developers website only while downloading any kind of free applications. Choose custom or advanced installation process so that you can trace the additional PUPs listed for installation along with the main program.
Special Offer (For Windows)
Im in possession of all of your private data Email Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Im in possession of all of your private data Email Scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.




