How to Remove Check-tl-ver-157-3.com Pop-ups
Check-tl-ver-157-3.com is an unreliable and deceptive site. It tricks visitors into accepting notifications, which then leads to frequent, unwanted ads appearing on their screens. These ads can be intrusive and misleading, disrupting your browsing experience. Clicking on them might direct you to unsafe or harmful websites, increasing your risk of security issues and making your computer more vulnerable to threats.
Special Offer (For Windows)
Check-tl-ver-157-3.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Check-tl-ver-157-3.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
What is Check-tl-ver-157-3.com?
Check-tl-ver-157-3.com is a deceptive website that utilizes misleading tactics to trick visitors into granting permission for browser notifications. When accessing the site, users are presented with a video player that closely resembles the style of YouTube. The player prominently displays a message instructing users to click the “Allow” button in order to watch the video.
However, this video player and the accompanying instructions are nothing more than a ploy to deceive visitors. If users fall for this trick and click the “Allow” button, they inadvertently give Check-tl-ver-157-3.com permission to send browser notifications.
The main objective of this deceptive tactic is to entice users into enabling notifications, which ultimately leads to the delivery of unwanted advertisements and promotional content. By mimicking the appearance of a popular video platform like YouTube, the website capitalizes on users’ familiarity and trust, making them more likely to believe that granting notification permission is necessary to access the desired video content.
It is important for users to exercise caution when encountering websites like Check-tl-ver-157-3.com. Granting browser notification permission to such deceptive sites can result in an influx of intrusive ads and unwanted pop-ups. To protect personal privacy and avoid unwanted advertising, it is advisable to decline notification requests from unfamiliar or suspicious websites, especially if they employ manipulative tactics to lure users into granting permission.
By staying vigilant and being aware of such deceptive practices, users can safeguard their browsing experience and avoid falling victim to misleading schemes.
How did I land on Check-tl-ver-157-3.com?
Unwanted redirects can be caused by various factors such as adware, malware, browser hijackers, phishing attacks, or compromised websites that have malicious scripts or links. Adware can redirect users to fake push notification sites by displaying misleading pop-up messages or using scripts to manipulate the user’s browser.
To prevent this, users can install reputable anti-malware software, use ad blockers, and be vigilant when clicking on suspicious links or pop-ups. They can also adjust browser settings to block notifications from unreliable webpages and regularly clear their browser cache and cookies to remove Check-tl-ver-157-3.com adware that is installed.
Reasons how an adware/browser may impact a device?
Speaking about the possible reasons why traits like Check-tl-ver-157-3.com or other malware may impact a targeted device includes many possible factors such as:
- Opting freeware or shareware applications on your device seeking enhancement to performance.
- Visiting various unreliable websites in search of freebies.
- Downloading applications, multimedia files, etc from unreliable sources.
- Clicking any email or its attachments or links without any prior security concerns.
- Clicking advert campaigns on suspicious or malicious websites.
- Installing unwanted browser extensions or addons.
In actual, the reasons may vary from computer to computer, but it totally depends on user’s own interaction with unsafe resources over web.
Threat Summary |
| Name: Check-tl-ver-157-3.com |
| Category: Browser hijacker, Redirect virus, Adware |
|
Features: Modifies browser settings to replace values for new tab, search engine, homepage, and even more, that redirects you to unsafe web locations throughout the day. |
| Danger Level: Normal to moderate |
|
Symptoms: The symptoms include eruption of intrusive advert pop ups, unexpectedly lowered down internet speed, and even more. The hijacker often promotes malicious web sources that can drive more high potential threats as well. |
|
Distribution: Freeware or shareware installer packages, malicious links or ads, software installer packages, bundled applications, fake software installers, and even more. |
|
Removal: If you suspect your device is infected with Check-tl-ver-157-3.com, run a scan with Spyhunter to check and clean all threats inside. |
How did Check-tl-ver-157-3.com install on targeted device?
A user often end up having their browser infected by an adware or browser hijacker through some browser extension or ads. Most of the times, the criminals use to promote their illicit content over web through deceptive marketing measures including advert campaigns, bundled applications, software installer packages, and even more. Even they can distribute cracked software packages that lurks malicious codes within. A user often interacts with such instances while surfing over the web and rush into installing such options without checking or reading its agreement terms. Let’s discuss each possible factor in detail below:
Intrusive Advert Campaigns

The criminals prefer to advertise their malware resources through a number of advert campaigns. They actually promote their malicious codes in various forms over web resources who are ready to promote such campaigns. Often those promoters can be non reliable websites, and a user must be cautious while dealing with those.
Bundled Software Packages
Software Bundling is a legitimate process allowing developers to bundle additional applications to create a complete software suite. However, the criminals misuse this technique to pack their malicious codes with other free browser extensions or applications. This leads to secret installation of malware codes on targeted device, and that’s require no permission in prior from users.
Malicious Gaming/Multimedia Portals
In many cases as researched, the malware devs use multimedia or gaming based web portals to distribute their malware codes as well. Actually, these web resources often get billions of user base in search of free games or media, however, this increases the risk of having their device infected by some malicious sort of applications.
Spam/Junk Email Attachments

Email Marketing is one of the cheaper and mostly preferred option for promoting any product or services. So, how the criminals remain stuck behind to misuse not this resource. They promote their malware codes in form of customized invoice or pdf files, which are further circulated through emails that even appears to be legitimate. It’s better to stay away against such deceptive email campaigns.
Data Distribution Channels
Cloud data storage and other options that helps to share a file through internet is quite rewarding. However, it can even curse a user and their device with a malware code. The bundled applications or other malware resources can be promoted through such online channels as well, and thus it’s necessary to be cautious while dealing with data sharing options including p2p, and so on.
How an adware/browser hijacker helps hackers?
The malware developers who creates adware or browser hijacker like traits are often partnered with illicit campaign advertisers. Means, the criminals use to promote their partnered advertisements through the adware, which appears on browsers in form of banners, or push notifications. Even such promotional contents can be injected in SERP which encourage the users to click or open such pages. Although these impacts become hassle for users, but this helps criminals to earn commissions based on PPC or PPV promotions. This is why the adware or browser hijacker like traits are created and promoted over web in abundance, as it causes the hackers to earn a very large revenue.
Harmful consequences of Check-tl-ver-157-3.com?
Although, a hijacked browser can be disturbing to users in various concerns, but this never means it’s just limited to show just adverts or redirect to unwanted pages. In addition to these, the long term presence of Check-tl-ver-157-3.com can also lead to other problems like data loss or identity theft. Many adware devs keep a keen eye over all user inputs, search preferences, browsing history, and other information, which can be further misused by criminals for more intense illicit sake. And therefore, the instant detection and removal of Check-tl-ver-157-3.com is highly necessary.
Special Offer (For Windows)
Check-tl-ver-157-3.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Check-tl-ver-157-3.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
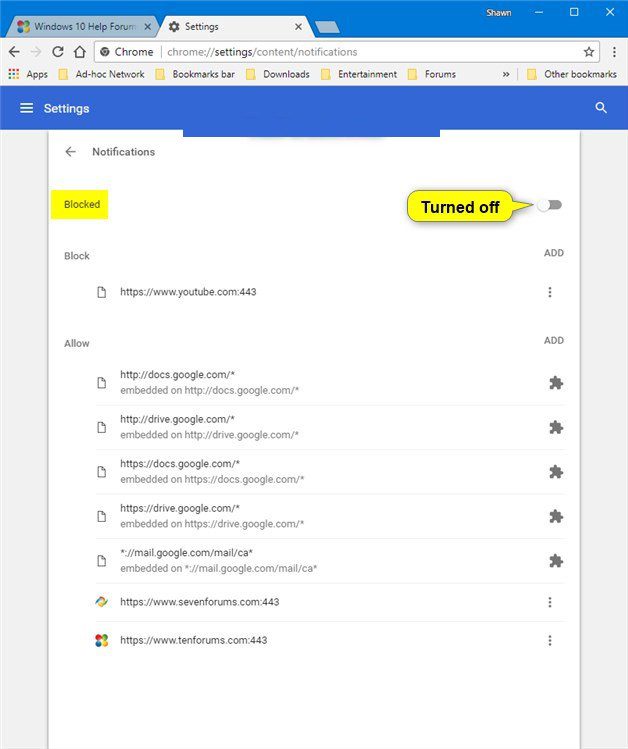
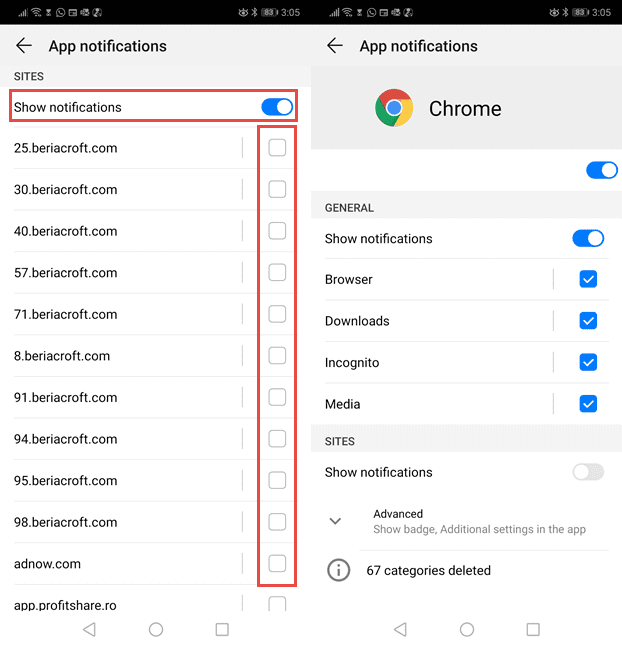
Google Chrome (Android)
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
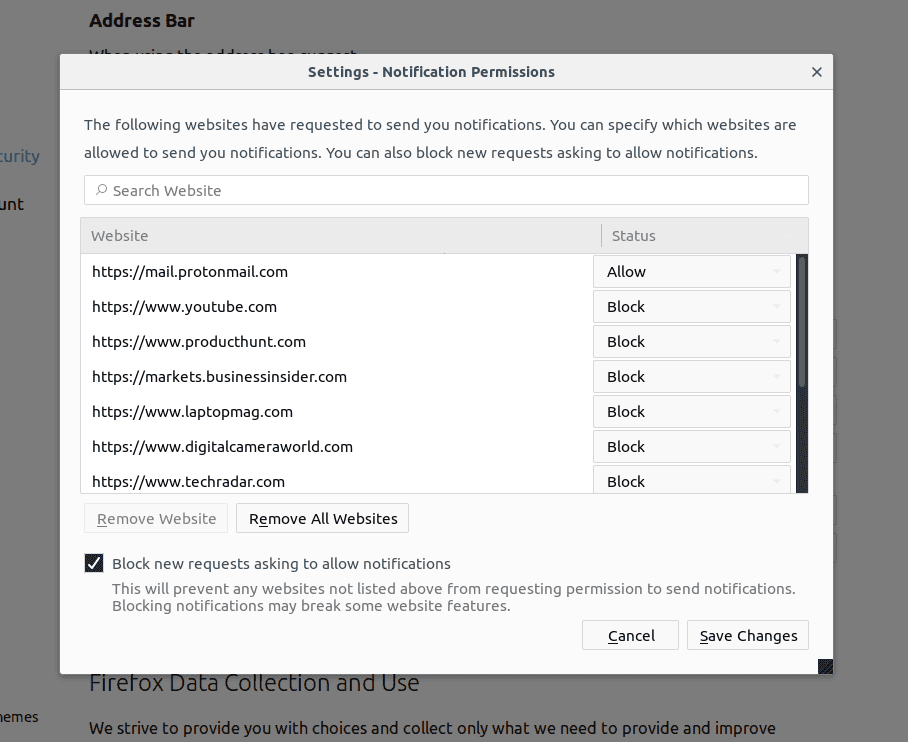
Mozilla Firefox
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
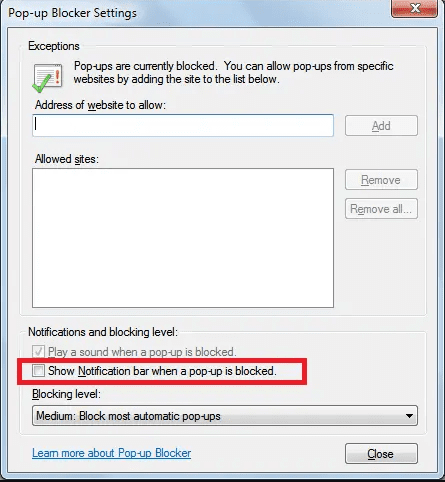
Internet Explorer
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
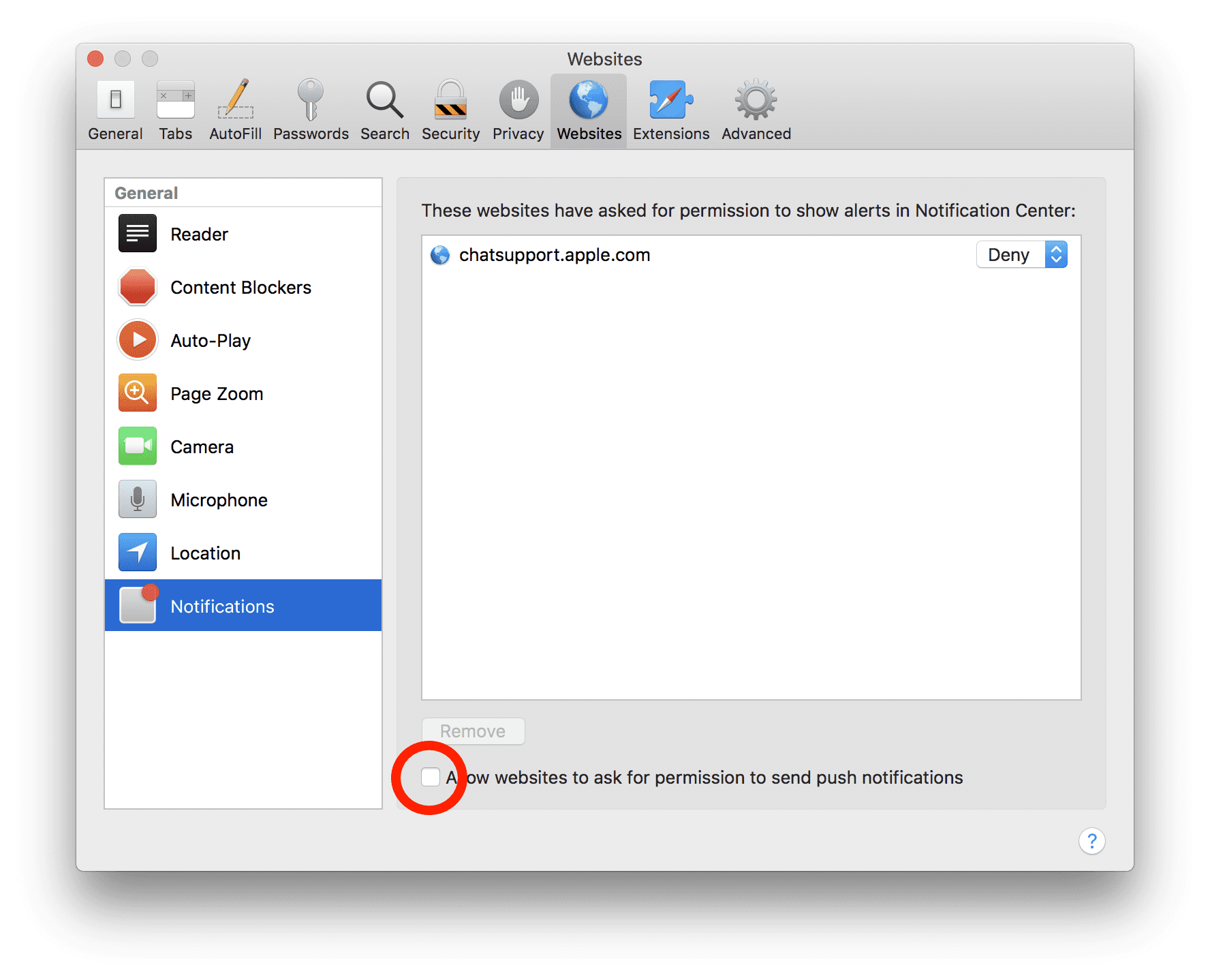
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Check-tl-ver-157-3.com:
Remove the related items of Check-tl-ver-157-3.com using Control-Panel
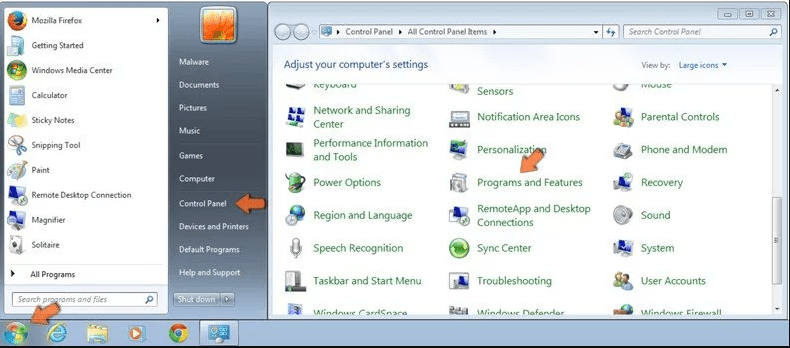
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
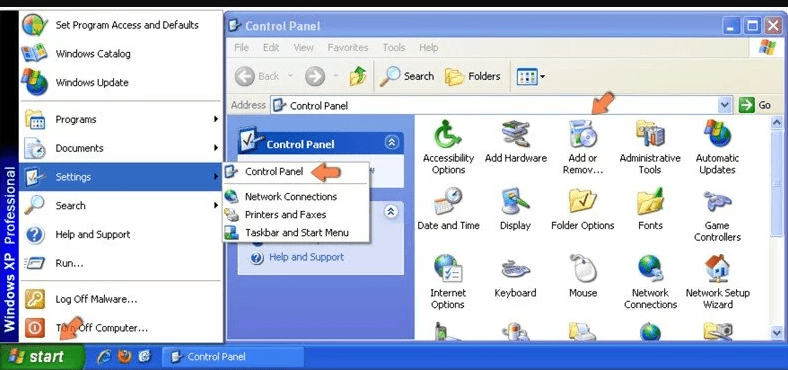
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
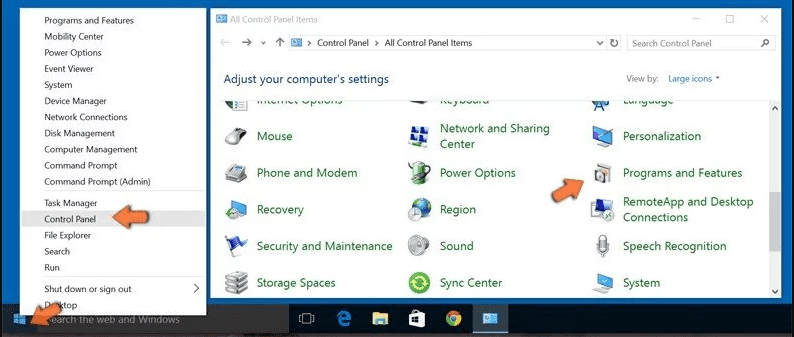
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
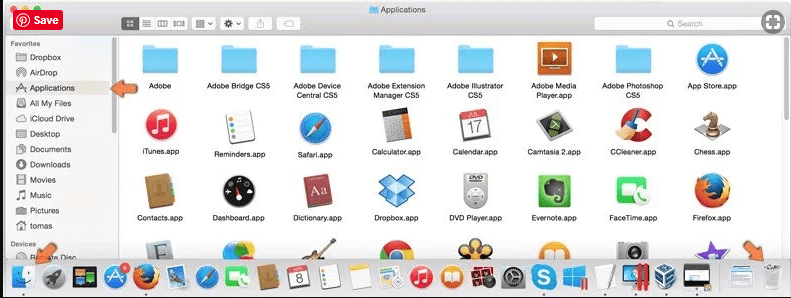
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
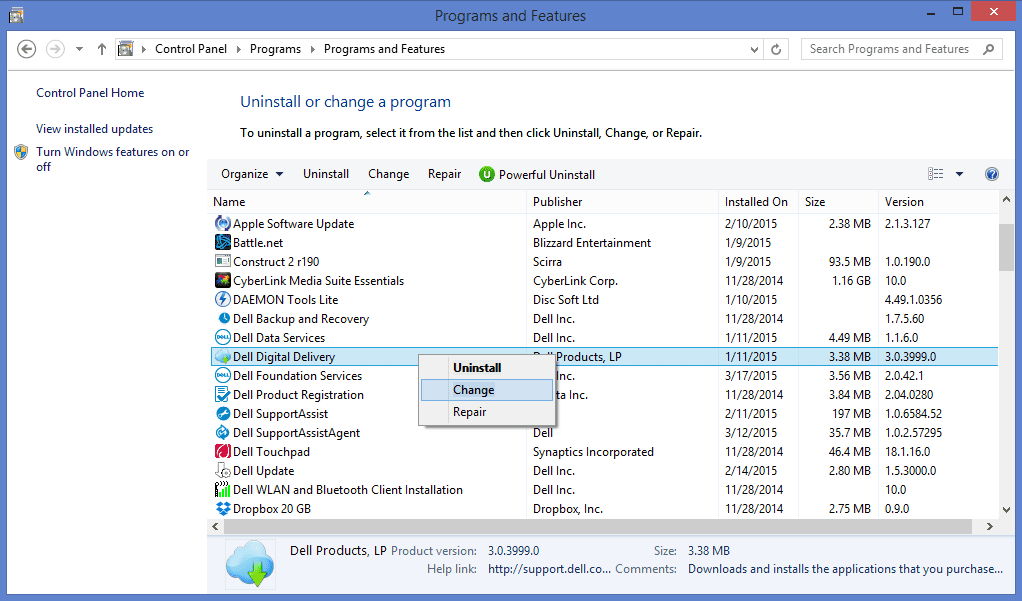
After you uninstall all the potentially unwanted program causing Check-tl-ver-157-3.com issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Check-tl-ver-157-3.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Check-tl-ver-157-3.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Check-tl-ver-157-3.com) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
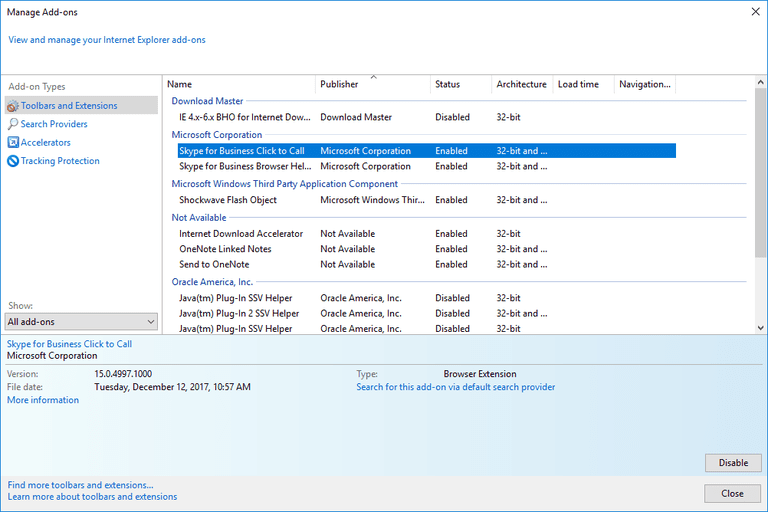
Additional Option
If you still face issues related to Check-tl-ver-157-3.com removal, you can reset the Internet Explorer to its default setting.
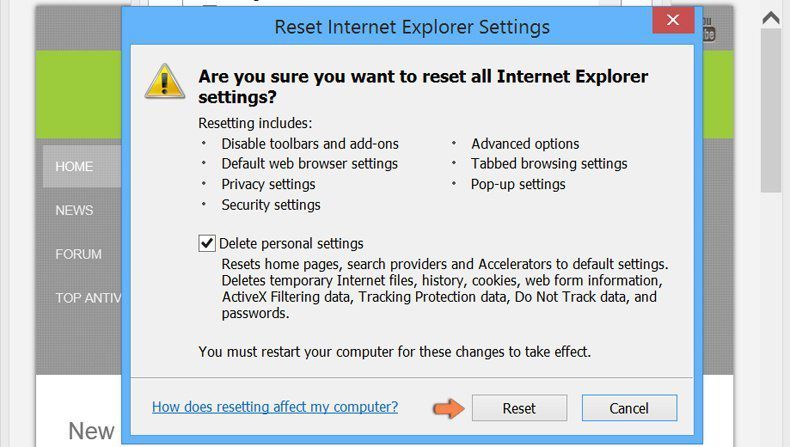
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
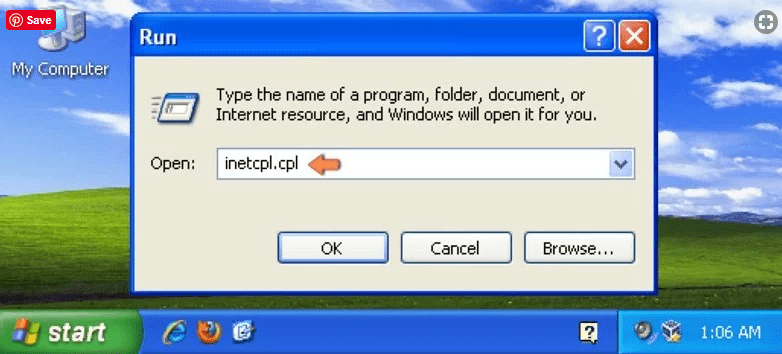
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
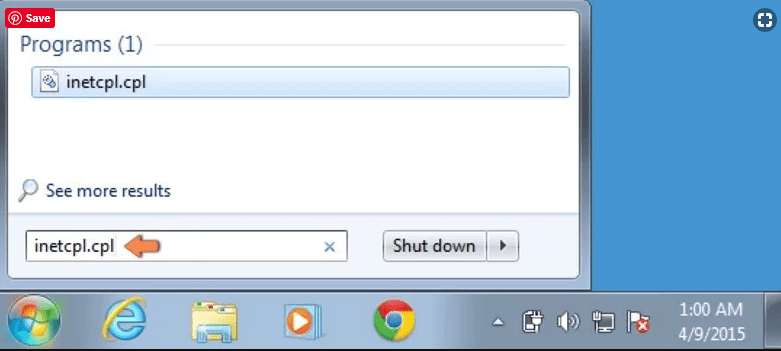
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
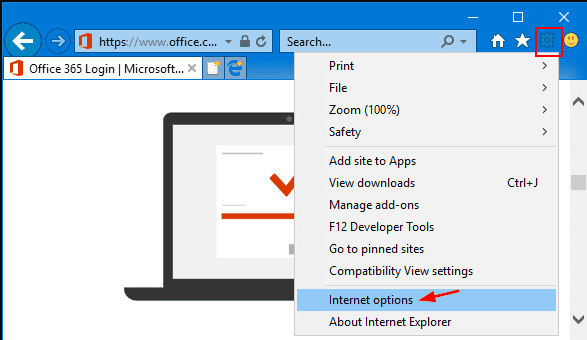
Select the “Advanced” tab in the newly opened window
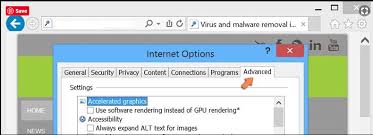
Press on “Reset” option
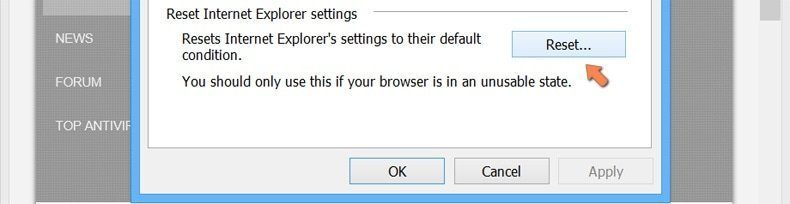
You have to press on the “Reset” button again to confirm that you really want to reset the IE
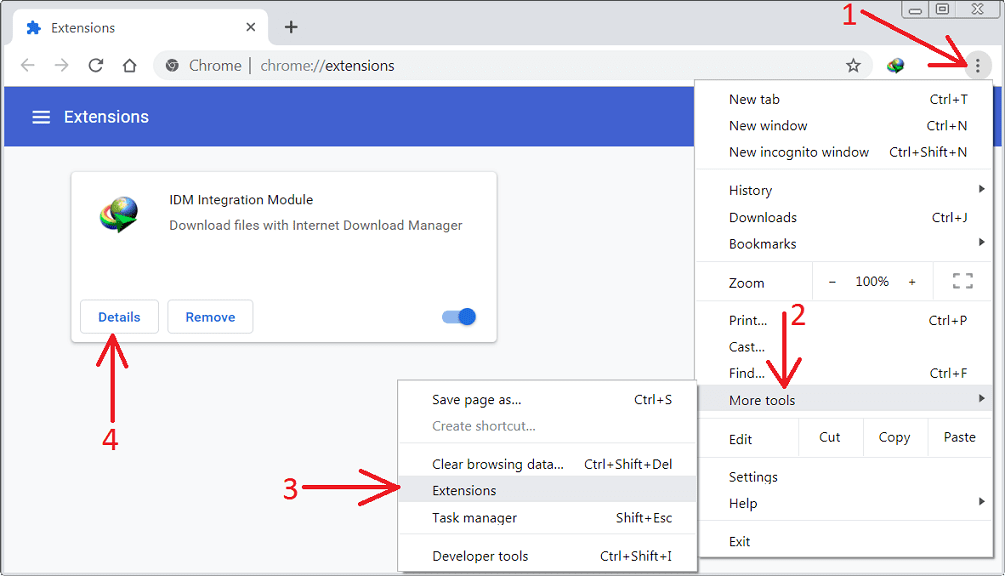
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
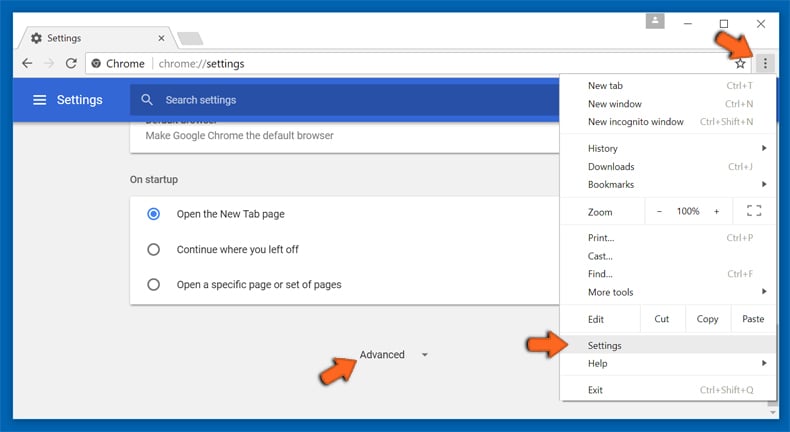
Optional Method
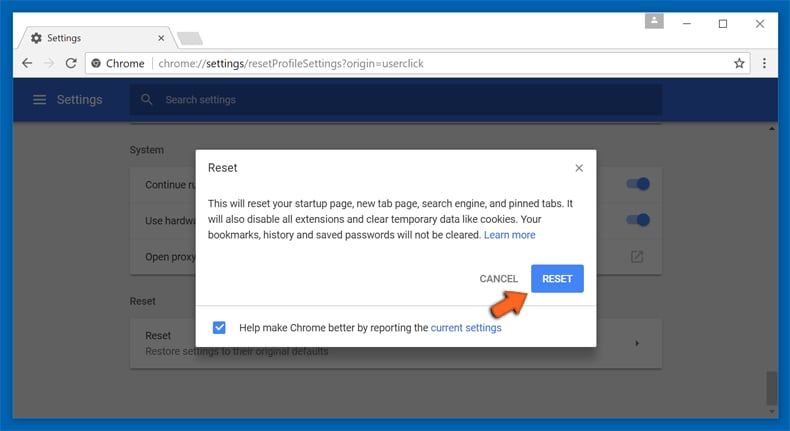
If the problems related to Check-tl-ver-157-3.com still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
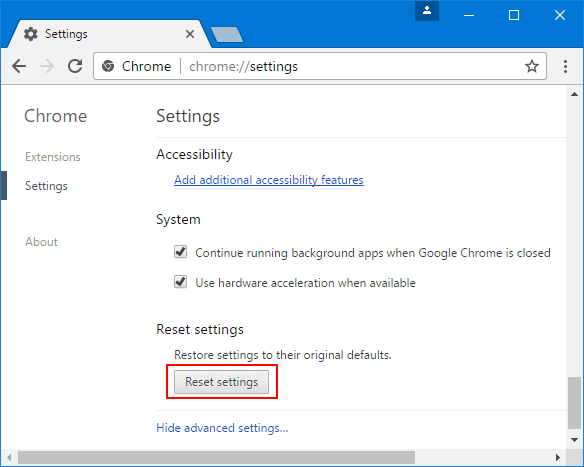
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
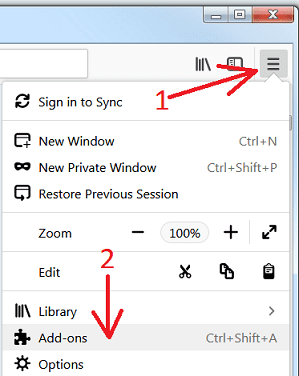
Remove Check-tl-ver-157-3.com plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Check-tl-ver-157-3.com removal then you have the option to rese the settings of Mozilla Firefox.
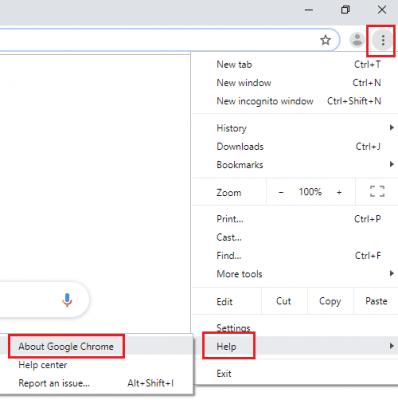
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
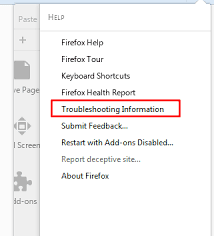
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
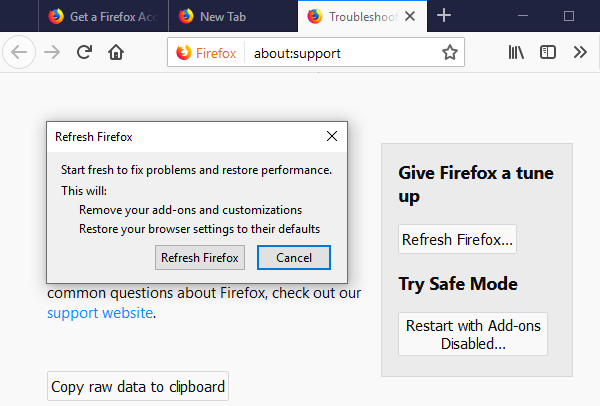
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
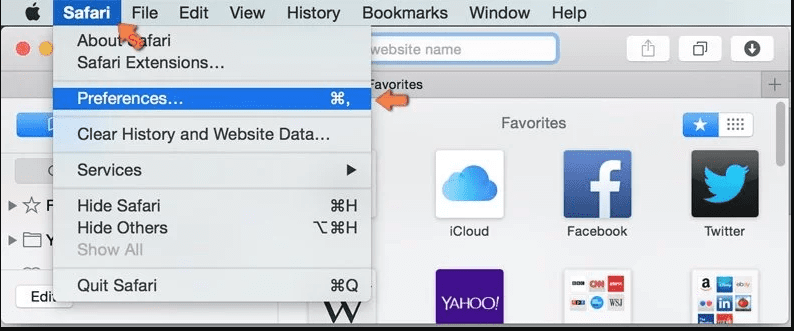
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
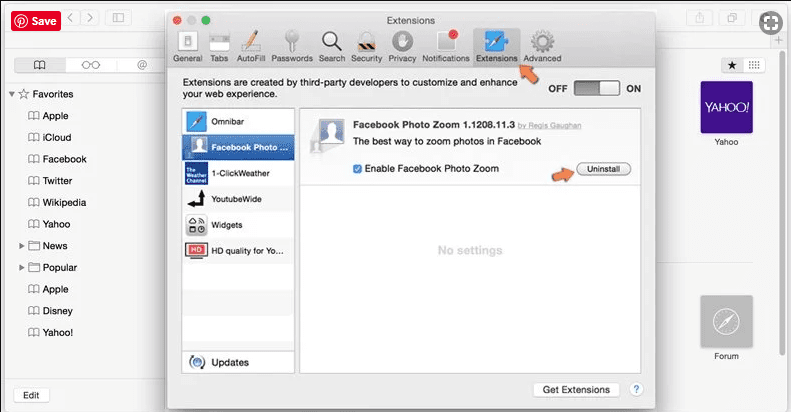
Optional Method
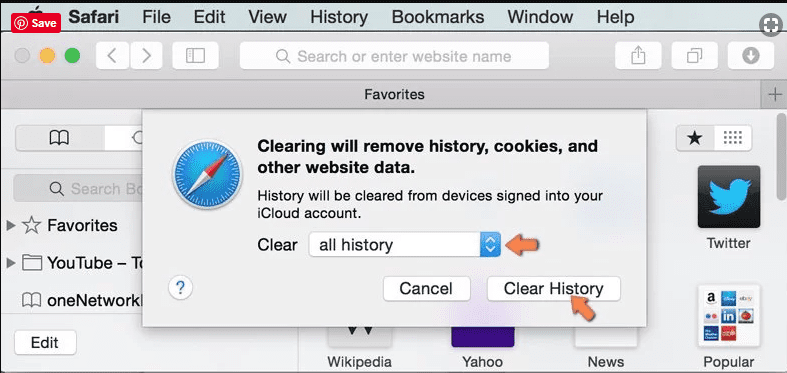
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
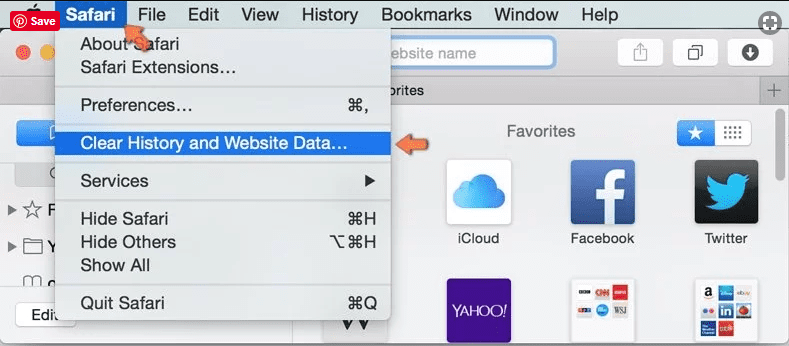
In the newly opened window, select “All History” and then press on “Clear History” option.
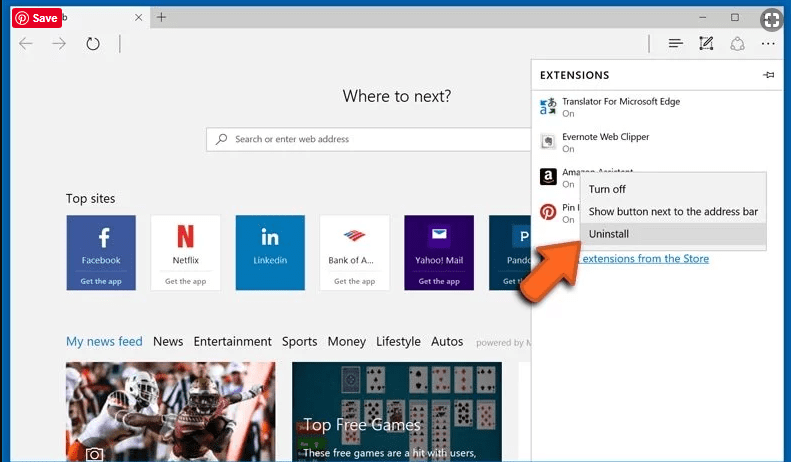
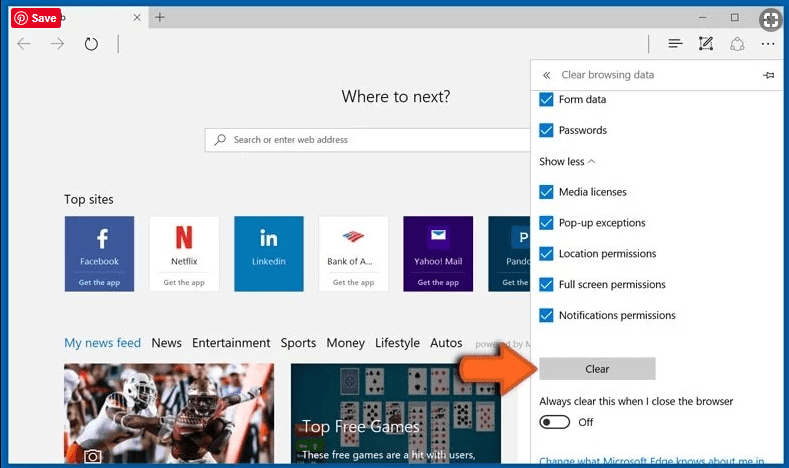
Delete Check-tl-ver-157-3.com (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
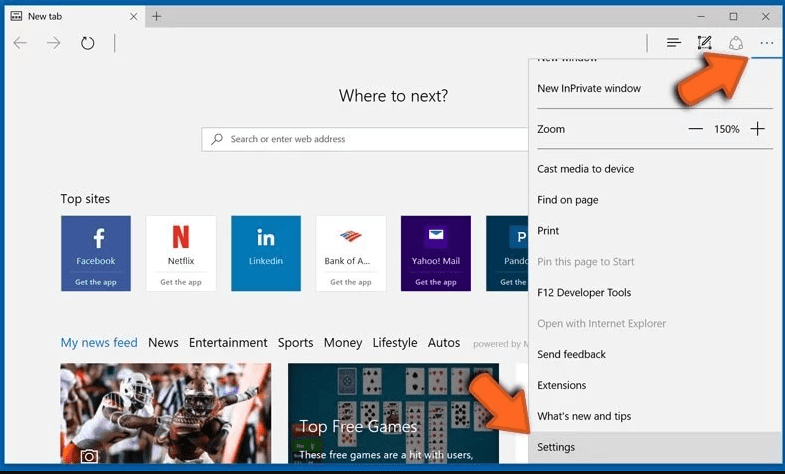
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
Next steps is to click on “Choose what to clear” button
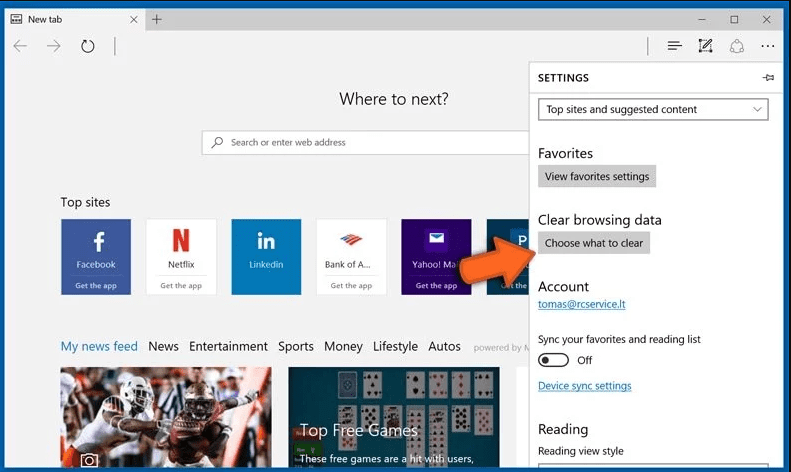
Click on “show more” and then select everything and then press on “Clear” button.
Recommended online habits you should acquire?
As soon as Check-tl-ver-157-3.com infiltrates the PC system, it starts carrying out malicious activities in the background and may lead to a number of unpleasant issues. To avoid getting infected with such browser-based pests, below are some steps you can take:
- Download software from reputable sources: Only download software from reputable websites, such as the official page of the software vendor or well-known download portals. Avoid downloading software from third-party websites or peer-to-peer networks, as these are often sources of bundled adware.
- Pay attention during the installation process: When installing software, pay attention to each step of the installation process. Look for the checkboxes that may indicate the installation of additional software, such as adware or browser extensions. Uncheck these boxes if you don’t want to install the additional software.
- Choose custom installation: During the installation process, choose the custom installation option instead of the default or express installation. This will allow you to select which components to install and to opt-out of installing any bundled adware or other unwanted software.
- Read the End User License Agreement (EULA): Read the EULA carefully before installing any software. Look for clauses that may allow the installation of additional software or adware like Check-tl-ver-157-3.com. If EULA contains such clauses, reconsider installing the software.
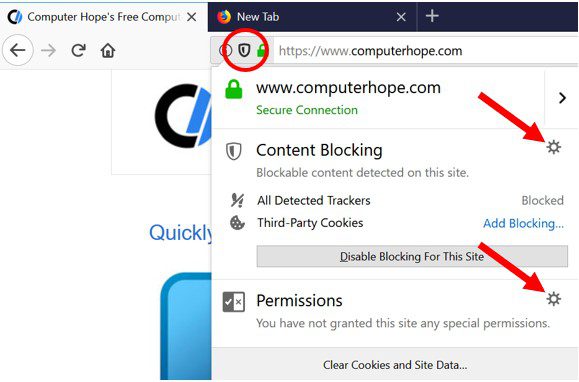
- Use a reputable web browser: Choose a reputable web browser, such as Google Chrome or Mozilla Firefox, and keep it up-to-date with the latest security patches.
- Install ad-blockers and pop-up blockers: You should use ad-blockers and pop-up blockers to prevent unwanted ads and pop-ups from appearing on your computer screen. Some web browsers have built-in ad-blocker and pop-up blockers, or you can install browser extensions that provide this functionality.
- Be careful when clicking on links: Don’t click on links in emails or on websites unless you are sure they are legitimate. Check the URL and ensure it is spelled correctly and is the correct website. Be wary of shortened URLs or URLs that lead to suspicious or unknown websites.
- Keep your web browser and operating system up-to-date: Regularly install software updates and security patches for your web browser and operating system. This will help to close any security vulnerabilities that adware, hijacker and other malware may exploit.
- Use a reputable antivirus program: A good antivirus program can detect and block infections like Check-tl-ver-157-3.com and other malware before they can infect your computer. Make sure you choose a reliable antivirus suite and keep it up-to-date with the latest virus definitions.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your PC system safe and secure.
Conclusion:
To sum up, Check-tl-ver-157-3.com can cause significant problems for computer users, including unwanted browser redirects, changes to homepage and search engine settings, and even the installation of additional malware. These infections typically result from downloading and installing software from untrusted sources or clicking on suspicious links. To prevent browser hijackers or adware, it is important to be cautious when downloading and installing software, use reputable antivirus tool, and keep browsers and operating systems updated with the latest security patches.
Related FAQs about Check-tl-ver-157-3.com
What are the Symptoms of Browser-hijacker (Check-tl-ver-157-3.com)?
The common symptoms of Check-tl-ver-157-3.com infection include changes to the default homepage and search engine, unwanted toolbars and extensions, pop-up ads, and redirects to unfamiliar websites. Additionally, the browser may slow down or crash frequently, and search results may be manipulated or irrelevant to the query.
What Should I do if my PC gets infected with virus like Check-tl-ver-157-3.com?
If your computer is infected with this browser-based threat, you should immediately run a virus scan using reputable antivirus software. If the software detects the malware, you should follow the removal instructions provided by it to eliminate the infection and restore your browser settings to default.
How can I protect my password and other personal credentials from Check-tl-ver-157-3.com?
To protect your password and other sensitive information from Check-tl-ver-157-3.com, you should employ reputable antivirus suite, enable two-factor authentication on all accounts, and use strong and unique passwords for each account. Also, you should avoid clicking on suspicious links or downloading software from untrusted sources.
Why I should trust your research conducted on Check-tl-ver-157-3.com?
It’s important to mention that our research is conducted independently and with the assistance of unbiased security experts, who provide us with daily updates on the latest definitions and threats related to malware, adware, and browser hijackers. Moreover, our study on the Check-tl-ver-157-3.com threat is supported by VirusTotal.
Special Offer (For Windows)
Check-tl-ver-157-3.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Check-tl-ver-157-3.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.


