Ransomware: All you need to know
All about ransomware
Ransomware is a type of computer threat that blocks users’ access to their files stored in their devices, or even to the computer in some cases, and demands certain amount of fee as a ransom. The first ever ransomware developed in the late 1980 and the payments were to be sent via snail mail. Today, ransomware authors order to make payment via crypto-currency or credit card.

They use different techniques for the ransomware distribution such as malicious spam, in which some unsolicited email is used to deliver malware, and mal-advertising where no user interaction required. They use an infected iframe to redirect users to criminals’ servers where they inject malicious code through exploit kit.
Some malware versions claim the payment is need to be done to avoid punishment form government authority, while others inform that they have the only way to get the files back is to purchase the decryption tool from the crooks. These threats can involve in stealing password and other sensitive data, showing surveys warnings and other fake alert issue and causing other unwanted activities as well.
Types of Ransomware
Ransomware are divided into four categories according to their peculiarities. These are:
File Encrypting Ransomware
Trojans are used as carrier of such viruses. After the install, these viruses encrypt the most used files including photos, music files, videos, art, business and other important data. In addition, they start display a warning message that claims that the only possible option to get the files back is to pay a ransom.
Non-encrypting ransomware
Those ransomware viruses fall on this category that block the entire PC system and seek to threaten the victims into paying fine. For this, they display warning messages, presenting as are from government authorities such as FBI, Police and others. After the install, it is easy for them to check for illegal files such pornographic content or unlicensed program versions. Then, they prepare the warning messages regarding these illegal files and ask for pay a fine to avoid getting jail.
Browser locking Ransomware
These viruses block installed browsers using JavaScript and start displaying various warning messages. These messages are almost similar to those displayed by any non-encrypting ransomware. In most of the claims, users’ illegal activities on the Internet are shown and then they are asked for fine to avoid getting jail. Obviously, FBI, Police and other government authority have nothing to do with these scam messages.
Ransomware-as-a-service (RaaS)
For those who want to create their own malware, but are not of technical background, ransomware developers open a darknet where they invite the engage in their distribution campaign. Crooks gain access to the malware configuration and spread them via their networks. These businesses are conducted on secret servers.
History of Ransomware
In 1980, PC Cyborg or AIDS named first ransomware virus was developed. This virus would encrypt all files on C: directory after 90 reboots. It then demanded $189 by mail to PC Cyborg Corp to the users for renew their license. As the encryption was quite simple enough to reverse and it posed little threat to the victims.
In 2004, GpCode used a weak RSA encryption to hold personal files and then in 2007, WInLock Heralded designed a malware which is different from known ransomware encryption at that time. This malware, instead of encrypting files, locked people out of their desktops. The payment was demanded through SMS.
In 2012, Reveton developed a new form of ransomware in which victims would be locked out of their desktop and were asked to pay fine for committed a crime like computer hacking, downloading illegal file or being involved in child pornography. They were shown an official looking page for this that include credentials for law enforcement agencies like FBI and Interpol. Average users easily believed that they were truly done something wrong. Most viruses of the law enforcement family asked for a fine from $100 to $3,000 with a pre-paid cash such as UKash or PaySafeCard.
CryptoLocker registered their entry in 2013. During that time, they were far more dangerous. They locked files using military grade encryption and stored the key required to unlock the files on a remote server. This means, it was virtually impossible to get the files back without paying the ransom. In 2018, Trojans like Emotet or TrickBot led the infection of some ransomware infection. And in 2019, with the sdinokibi ransomware, the attackers used a compromised MSP (Managed Service Providers) for the attack.
Understand the Modus operandi of file encrypting viruses
Ransomware viruses encrypt sensitive data such as business documents, videos, photos and other similar data and then demand ransom exchange to the encrypted files. They can delete predetermined documents, multimedia objects and other important information. They can manifest the functions of crucial system components or important parts. Some viruses can steal log-ins, passwords, valuable personal documents and other confidential information as well. All these data are stored on some remote location, sent through a background Internet connection. Such viruses can cause troubles with Operating System performances, more specifically; they may bring frequent system restarts or affect the CPU speed. Certain malware can even shut down the security related software installed on the device. More on, these viruses do all such activities before the files encryption and thus it is already being late when you come to know the files stored on your device are now not accessible or unusable due to a ransomware attack.
Recent released ransomware: Fob Ransomware, WastedLocker Ransomware, CryCryptor Ransomware, LOLYTA Ransomware, PYKW Ransomware, MOBA ransomware
Techniques used for ransomware distribution
Various methods are nowadays used to distribute ransomware viruses with the attempt to extort ransom payment form victims. The major ones are being discussed one by one just below:
Fake pop-up notifications: Such notifications can be seen on illegal or on legitimate websites. These are set to report the users of some missing updates and inform them to run a scan and fix the errors for free. These ads are filled with unsuspicious names and logos that give the impression legit to them. Two things we want to point out here: firstly, it is not the duty of the websites to tell you about infection on your device or updates required of software and OS. Second and the most important, the sites that show such pop-up notifications have the common motive to make users fall on some scam and end up them to install rogue apps or malware.
Spam emails: This is the most profitable technique used for ransomware distribution. In this method, ransomware payload is wrapped under a legitimate looking file. These files could be a MS Office Document, PDF files, Executable Files, JavaScript Files and etc. By emphasizing the importance of such files, victims are persuaded to extract them. When the users open these files, they are asked to enable macros commands. If they are enabled, the corrupted files download and install the malware. You should pay attention of the content of such emails. These emails usually have grammatical errors and spelling errors.
Trojans and other malware: The most of the ransomware viruses are spread with the help of Trojans. They are included of some ransomware malware, in such cases. They get in the device without users’ consent through opening spam emails. Once they enter, they activate the payload of the malware and install it on the device.
Browser extensions: This is a new technique, in which a compromised web page is injected with a specific script. On visiting this page, the content is transformed into an unreadable collection and numbers. The users are asked to update a specific font browser add-on to read the content. Once this is done, the file-encrypting virus gets its way to enter inside the device.
Exploit kits: Exploit kits are usually adopted by sophisticated and large-scale viruses. These kits abuse vulnerabilities of some outdated software and use mal-advertising techniques to lure into users’ device. Rig Exploit kit, Grandsoft Exploit kit and Magnitude Exploit kit are couple of examples of such exploit kits.
What to do when I get infected?
In such a case, you should firstly think of how to remove the ransomware -guide below the post will help you in this – and thereafter you should consider about the files recovery. Remember, the crooks try their best to make you fall on their scam and pay for their decryptor. However, you should keep the only things in mind that they are not here to help you. After all, they are cybercriminals. You should think of data recovery of the encrypted files using backup or other alternatives that you will when you go through the article.
Ways to protect PC from ransomware infection
The first step in ransomware prevention is to invest in awesome cyber-security – a program that provides real-time protection to advanced threats such as ransomware. Next, you need to create regular backup of the data on your device so that you will have no problem in a case with ransomware attack and files encryption. Then, be sure about systems and software are updated, as you see ransomware viruses are nowadays use exploit kits to target vulnerabilities caused due to the outdated software bugs/flaws. Finally, you should surf the session with caution – avoid opening any irrelevant emails and those suspicious attachments, stay away from any unprotected pages recommending fake system issue, error, non-existing viruses and updates of software and prevent any untrustworthy pages used for any software download and installation.
Below, the complete guide on remove ransomware viruses and various ways to attempt files recovery are provided for you. Hope so, you will get the happy result after proceeding with it. In case, the recovery options do not let all the files accessible on your device, do not lose hope as cyber-security works become prominent when any ransomware virus is reported to crack the key it used and develop an official decryption key, which is free for all.
Special Offer (For Windows)
Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove Ransomware through “Safe Mode with Networking”
Step 2: Delete Ransomware using “System Restore”
Step 1: Remove Ransomware through “Safe Mode with Networking”
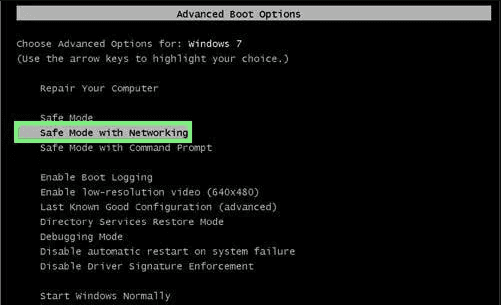
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
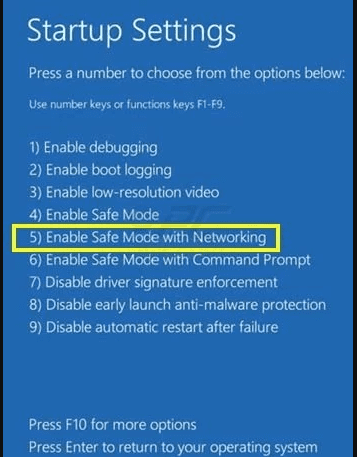
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
Step 2: Delete Ransomware using “System Restore”
Log-in to the account infected with Ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
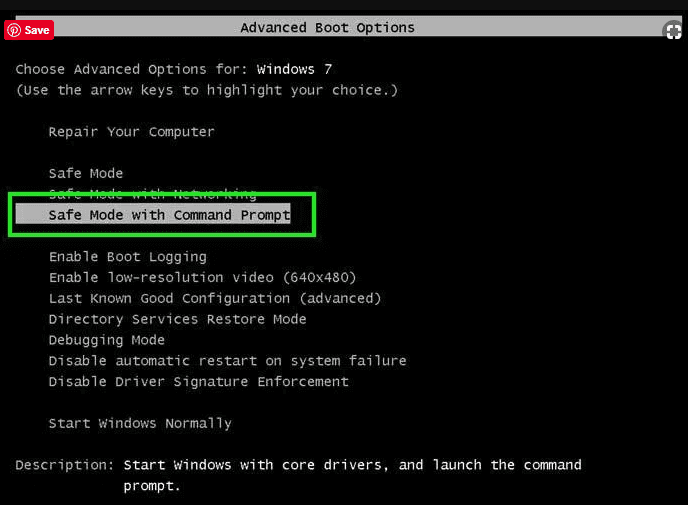
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
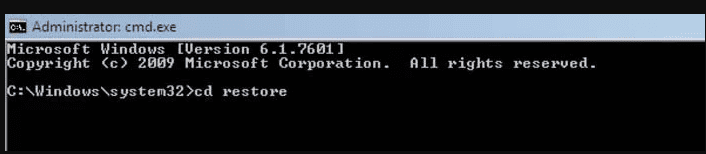
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
- Type: rstrui.exe and Press “ENTER”
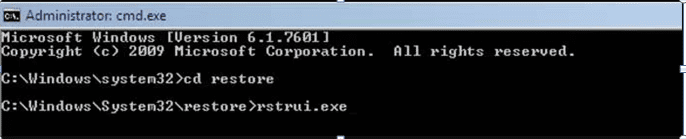
- Click “Next” on the new windows
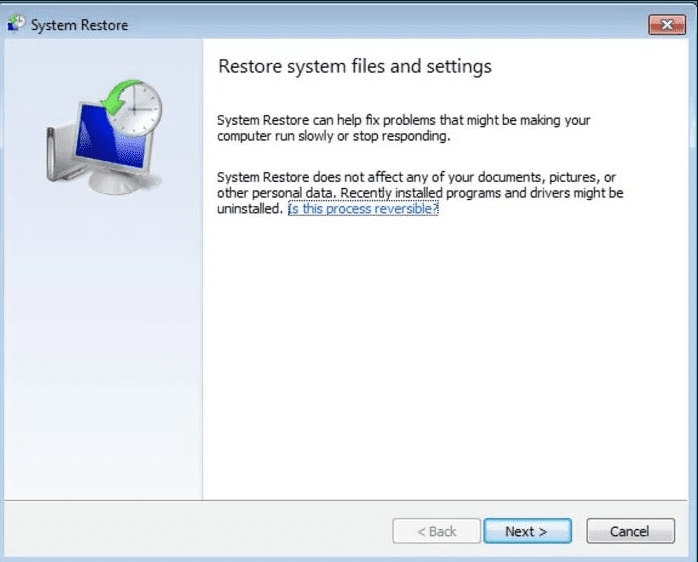
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to Ransomware infiltration in the PC.
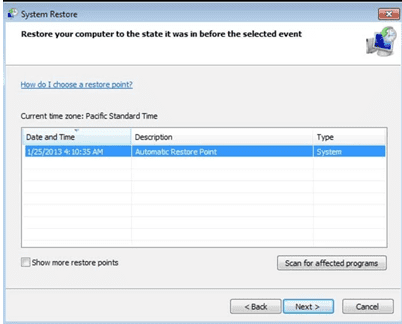
- In the newly opened windows, press on “Yes”.
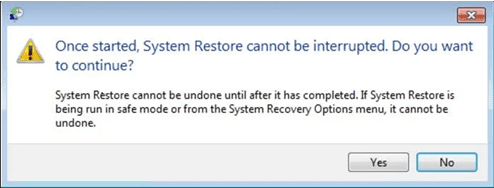
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove Ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of Ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
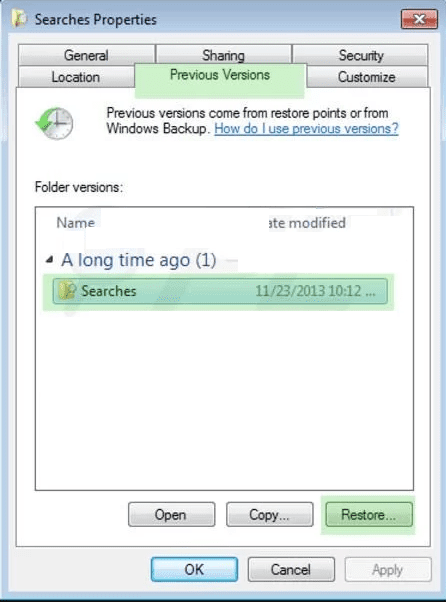
How to Restore Individual Encrypted File:
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
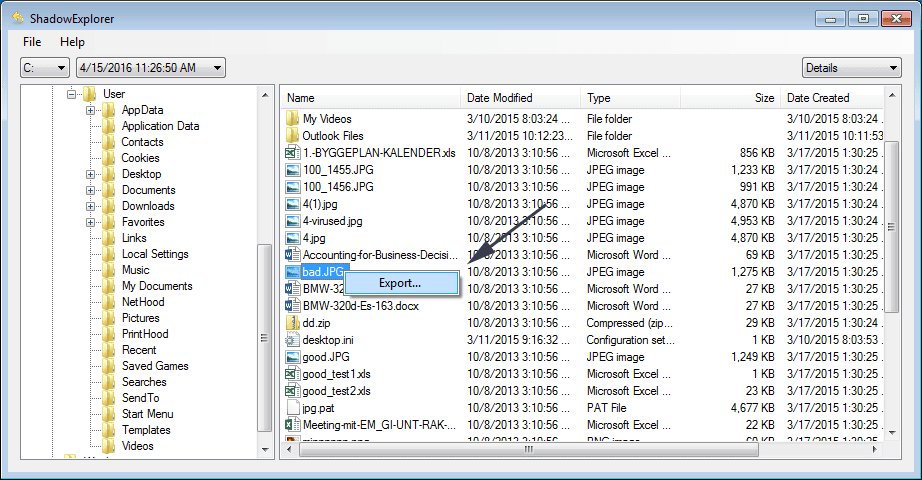
In order to access the files encrypted by Ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like Ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
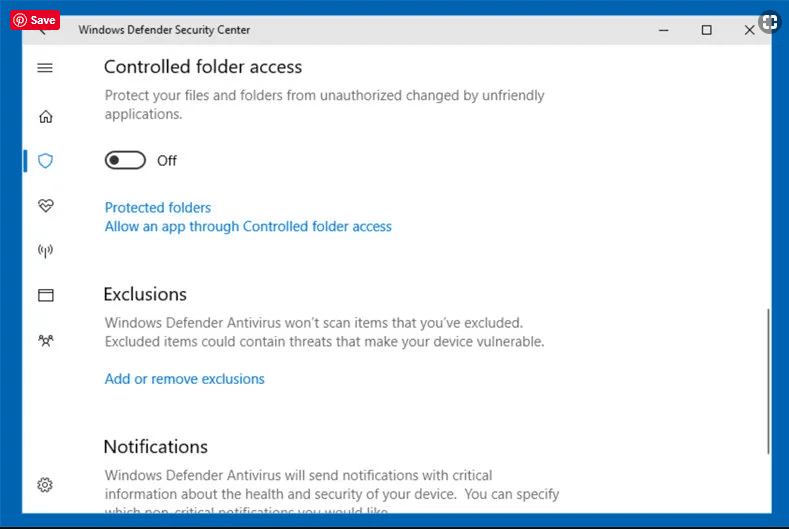
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by Ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with Ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove Ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

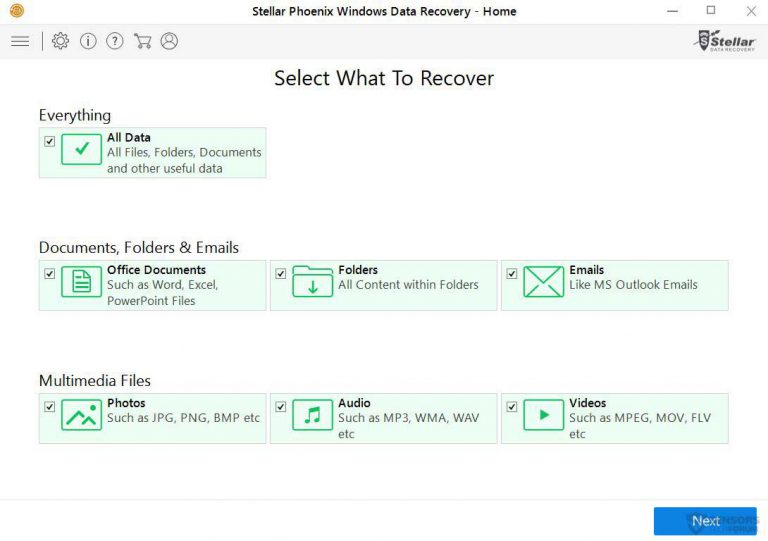
Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
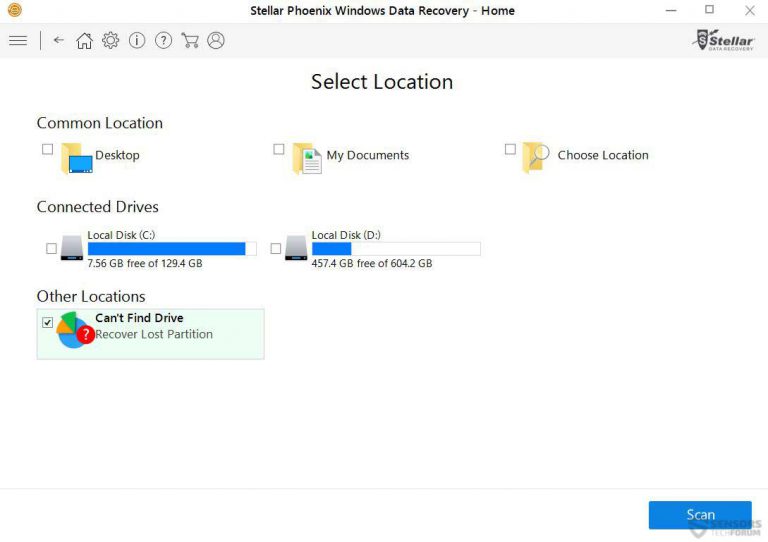
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.