Microsoft and partners takes down the dangerous Necurs bot
Necurs botnet, the largest botnet that was used by cybercriminals in order to distribute spam and infect computer devices with malware now have been taken down entirely by the Microsoft and their representatives from 35 different countries.
The final step of the eight years of persistence technical and legal operations occurred on March 5, 2020, when the company acquired permission from the US District Court for the Eastern district of New York to control the Infrastructure of the Necurs Botnet:
“With this legal action and through a collaborative effort involving public-private partnerships around the globe, Microsoft is leading activities that will prevent the criminals behind Necurs from registering new domains to execute attacks in the future.”
Necurs Botnet was firstly spotted back in 2012 and is believed to be compiled by Russian cybercriminals. Over the years, it was used in order to distribute various threats such as GameOVer Zeus, Locky ZeroAcces, and Dridex. During the period, the Necurs affected over 9 million devices.
Botnet is a network infected with malware. Cybercriminals have command and control over it. They can input command and communicate with the host from their remote servers. The servers are hosted by domains that are created by botnet’s generation algorithm, also known as DGA. This algorithm creates random domains that are pre-registered by the operators for months in advance. If this component is taken down, the servers are no longer been supported and consequently ends up the Necurs operators to send any command on the network -what exactly the Microsoft and their partners did:
“We were then able to accurately predict over six million unique domains that would be created in the next 25 months. Microsoft reported these domains to their respective registries in countries around the world so the websites can be blocked and thus prevented from becoming part of the Necurs infrastructure. By taking control of existing websites and inhibiting the ability to register new ones, we have significantly disrupted the botnet.”
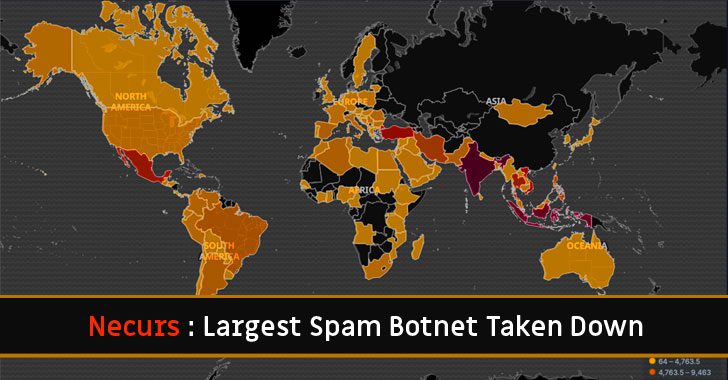
As per Tom Burl, Microsoft’s corporate Vice President, the victims of the botnet were tracked to almost every country in the world. Each infected device sent out 3.8 million spam emails to 40.6 million victims over the 58 days alone. The countries like India, Indonesia, Turkey, Vietnam and Mexico are the ones having the most number of users infected.
The botnet was used for hiring purpose as well. The malicious actors used the botnet for variety of purposes like distributing malware like ransomware, cryptominers, RATS, data stealers and etc, initiating DoS attack to disrupt the operations of the domains as well as stealing the confidential data such as logins and passwords and banking related information.




