Mailto (NetWalker) Ransomware compromises enterprise networks
A yet another ransomware infection added in the list of the particular that targets enterprise networks. The name of this virus is Mailto (NetWalker) Ransomware. It asks for high ransom prices by compromising their networks and encrypting all the Windows devices in connected.
MalwareHunterTeam shared a sample of the Mailto (NetWalker) Ransomware, the executable of the virus attempts to impersonate the Sticky Password software.
When users execute this file, the ransomware uses the embedded configuration that included the options like the ransom note template, ransom note file names, length of Id/extension, white listed files, folders and extensions and so on.
Vitali Kremez upon analyzing the ransomware finds that the configuration is so sophisticated as compared to other ransomware infections.
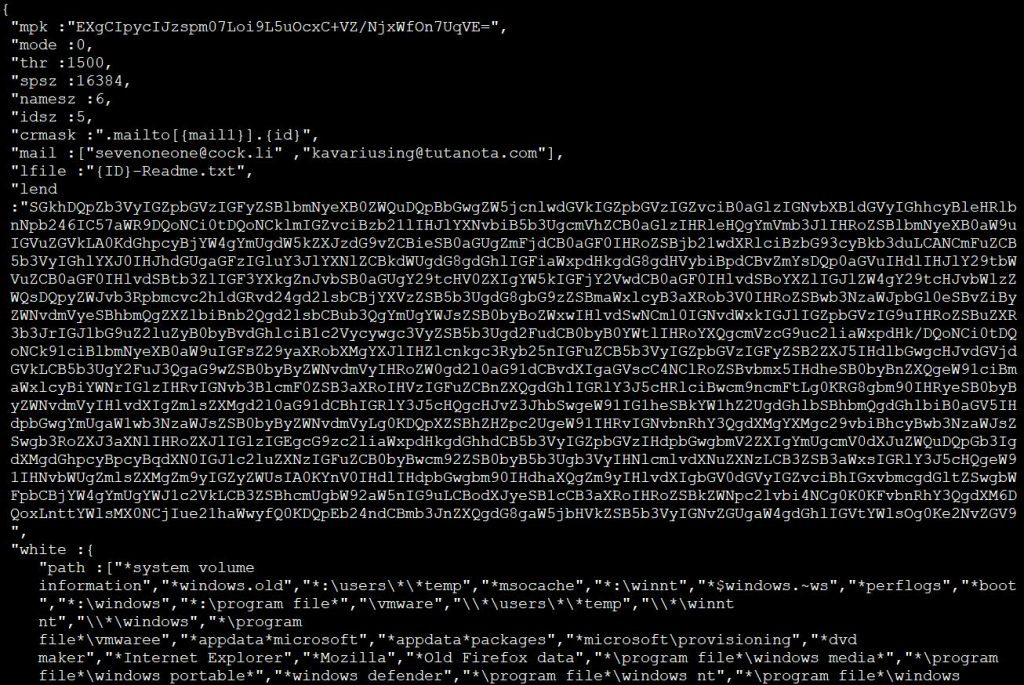
While other viruses of this type utilize a whitelist of folders, folders and extensions that will be skipped, Mailto ransomware utilizes a much longer than usual. As for example, below is the list of the folders that will be skipped from being encrypted.
*system volume information
*windows.old
*:\users\*\*temp
*msocache
*:\winnt
*$windows.~ws
*perflogs
*boot
*:\windows
*:\program file*
\vmware
\\*\users\*\*temp
\\*\winnt nt
\\*\windows
*\program file*\vmwaree
*appdata*microsoft
*appdata*packages
*microsoft\provisioning
*dvd maker
*Internet Explorer
*Mozilla
*Old Firefox data
*\program file*\windows media*
*\program file*\windows portable*
*windows defender
*\program file*\windows nt
*\program file*\windows photo*
*\program file*\windows side*
*\program file*\windowspowershell
*\program file*\cuas*
*\program file*\microsoft games
*\program file*\common files\system em
*\program file*\common files\*shared
*\program file*\common files\reference ass*
*\windows\cache*
*temporary internet*
*media player
*:\users\*\appdata\*\microsoft
\\*\users\*\appdata\*\microsoft
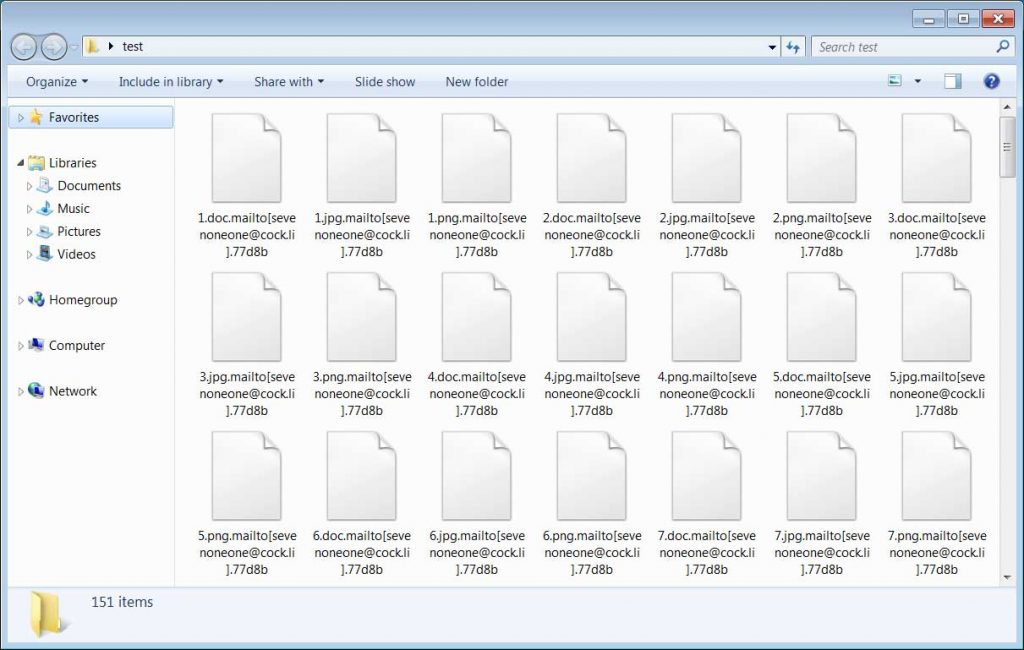
During the files encryption, the Mailto ransomware will append the filenames using a pattern .mailto[{mail1}].{id}. For example, a file 1.jpg becomes 1.jpg.mailto[[email protected]]77d8b.
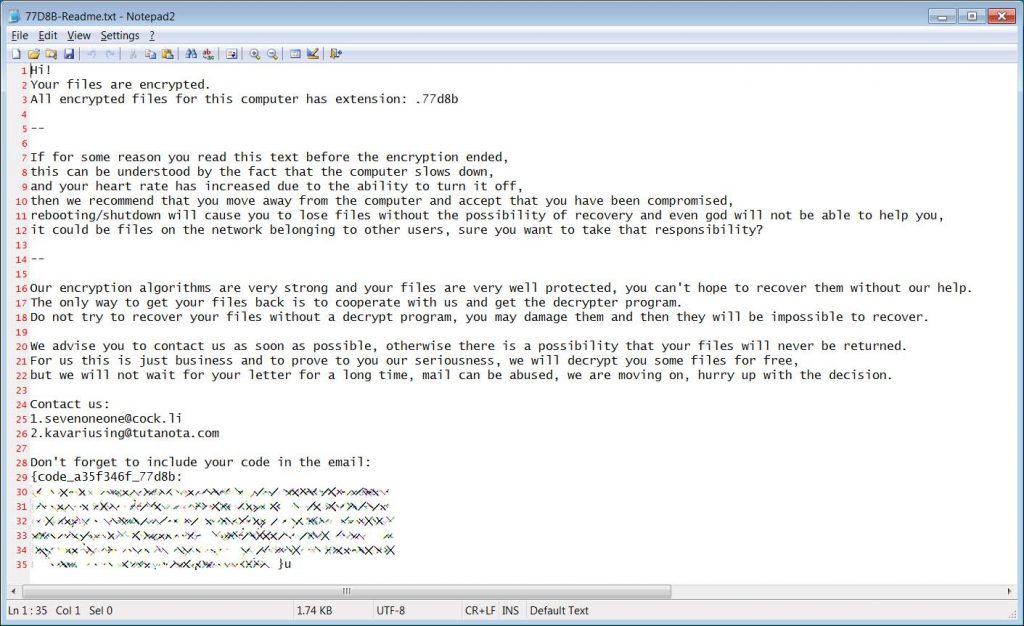
The ransomware will create a ransom demanding note in a file whose name is the format of ID-Readme.txt. This ransom note provides the information about the files encryption and provides two email addresses that are to be used for the payment of the amount and instructions.
The ransomware is still being analyzed to know if any weakness in the encryption algorithm to used to decrypt the files for free.
Mailto and Netwatcher -both are same
The Mailto ransomware is also called Netwatcher ransomware. The name Mailto is based on what the extension the ransomware uses to append the filename of the encrypted files. While the other one that is Netwatcher is what the name by which the crooks behind it call for the decryption tool/software within the ransom note.






