How To Remove iTerm2 Malware From Mac
iTerm2 Malware: Simple Delete Process
iTerm2 Malware is a perilous computer infection categorized as a trojan virus, that works as a backdoor-type vicious application. It seems almost similar to the legitimate iTerm2 app, however, this dubious software inserts malevolent code onto the compromised Mac devices which leads to the additional malware intrusions inside. It is worth mentioning that this trojanized program has been spread through websites presented as the official iTerm2 site. Moreover, these shady webpages have been noticed being promoted by specific search engines. Due to this parasite, you may have to deal with frequent system crashes, hard drive failure, boot errors, application malfunctioning, and other hazardous issues.
iTerm2 Malware Performs Several Evil Deeds:
iTerm2 Malware has ability to plant vicious code and applications into the PC systems. Depending on the purpose of the con artists behind this notorious trojan, it injects malicious apps into the work-station. In general, such backdoor type viruses can contaminate PCs with ransomware, Trojans, cryptominers, RATs, and other malware. Trojan is a kind of computer virus that includes several malevolent traits, e.g., stealing data, enabling remote access/control over the infected devices, disabling installed applications, and so on.
iTerm2 Malware can proliferate ransomware which tends to encrypt data stored inside the computer and then force victims into paying the attackers a hefty sum of ransom for their encryption. If such type of destructive crypto-threats could manage to intrude your machine, nothing can be worse than that. Furthermore, cryptominers are used to mine digital currencies like Bitcoin or Monero bu eating by enormous amount of CPU and GPU resources. It slows down the overall PC performance drastically and causes the system to take more than usual time to complete any task,
iTerm2 Malware has keylogging feature and records keystrokes. It extracts data from installed browsers and other applications. Moreover, it spies on victims’ online activities and gathers several browsing-related information like IP addresses, locations, search queries typed, sites visited, links clicked, and even private data such as saved passwords, credit card and banking details. Afterwards, the collected information is shared with third-parties and can be utilized for advertising purpose, making fraudulent transactions, unauthorized purchases, and so on. Hence, this perilous trojan may lead to severe privacy issues, identity theft, and significant financial losses. Therefore, an instant iTerm2 Malware removal is strongly recommended.
Penetration Of iTerm2 Malware:
This malicious software has been spread through webpages that imitate the legitimate iTerm2 website. People often visit these vicious domains through deceptive ads, other shady sites, etc. The misleading sites have been also observed being promoted on the Baidy search engine when “iTerm2” is searched. Nonetheless, reports say that this search provider has already removed fraudulent websites from its search results. Typically trojan viruses are distributed through shady download channels (e.g., unofficial sites, Peer-to-Peer sharing networks, etc.).
Spam emails are the most commonly used sources to proliferate such infections. These phishing mails are specially designed to trick recipients into downloading and opening the attached vicious file which triggers the installation of the virus. Thus, suspicious or irrelevant emails coming from unknown addresses should not be opened. Moreover, all applications should be downloaded from official and verified sources only. Stay away from suspicious ads as links inserted into them may redirect to potentially insecure portals. And last but not the least, it is expressly advised to have a reputable anti-malware tool and keep updating it from time-to-time. But at the moment, you must remove iTerm2 Malware from the Mac as soon as possible.
Special Offer (For Macintosh)
iTerm2 Malware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Remove Files and Folders Related to iTerm2 Malware
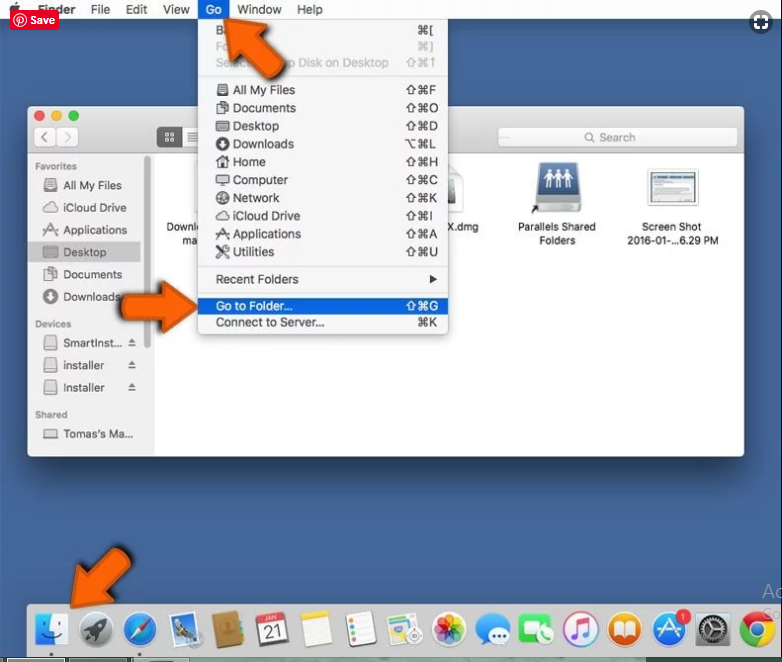
Open the “Menu” bar and click the “Finder” icon. Select “Go” and click on “Go to Folder…”
Step 1: Search the suspicious and doubtful malware generated files in /Library/LaunchAgents folder
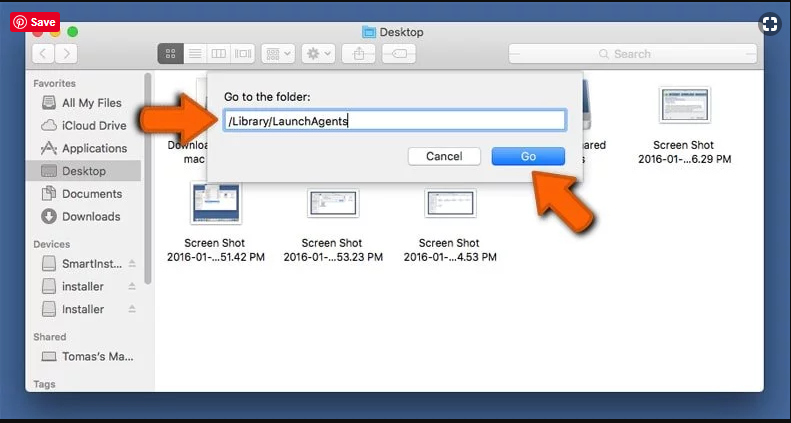
Type /Library/LaunchAgents in the “Go to Folder” option
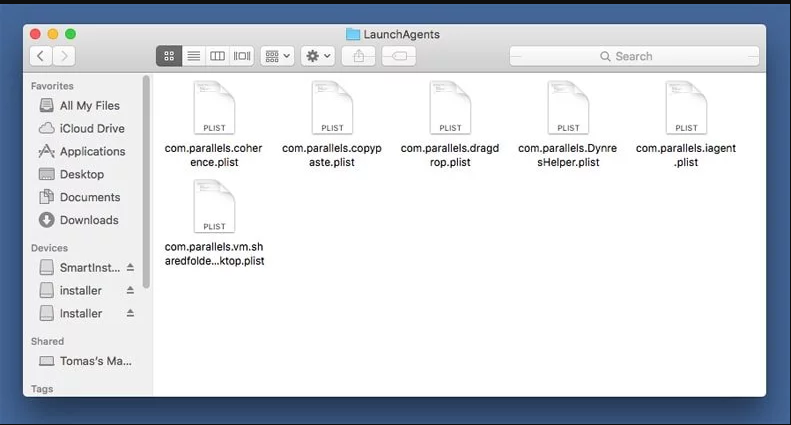
In the “Launch Agent” folder, search for all the files that you have recently downloaded and move them to “Trash”. Few of the examples of files created by browser-hijacker or adware are as follow, “myppes.download.plist”, “mykotlerino.Itvbit.plist”, installmac.AppRemoval.plist”, and “kuklorest.update.plist” and so on.
Step 2: Detect and remove the files generated by the adware in “/Library/Application” Support folder
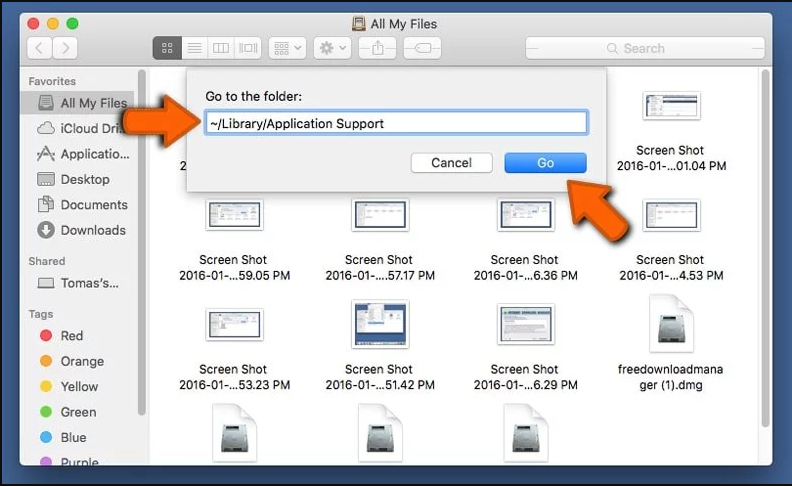
In the “Go to Folder..bar”, type “/Library/Application Support”
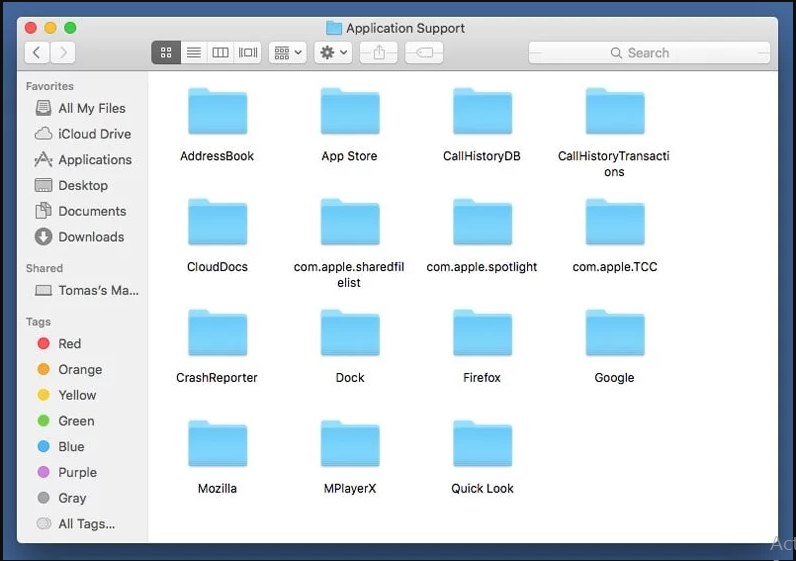
Search for any suspicious newly added folders in “Application Support” folder. If you detect any one of these like “NicePlayer” or “MPlayerX” then send them to “Trash” folder.
Step 3: Look for the files generated by malware in /Library/LaunchAgent Folder:
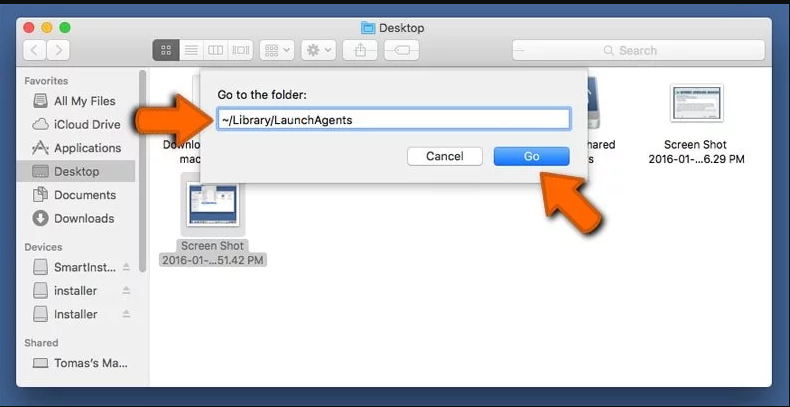
Go to Folder bar and type /Library/LaunchAgents
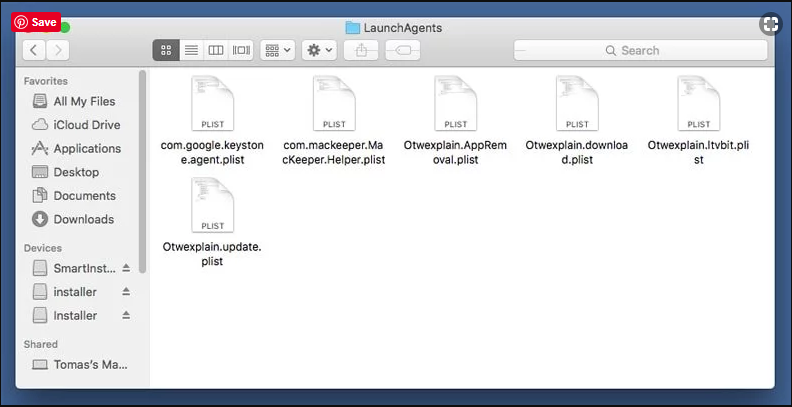
You are in the “LaunchAgents” folder. Here, you have to search for all the newly added files and move them to “Trash” if you find them suspicious. Some of the examples of suspicious files generated by malware are “myppes.download.plist”, “installmac.AppRemoved.plist”, “kuklorest.update.plist”, “mykotlerino.ltvbit.plist” and so on.
Step4: Go to /Library/LaunchDaemons Folder and search for the files created by malware
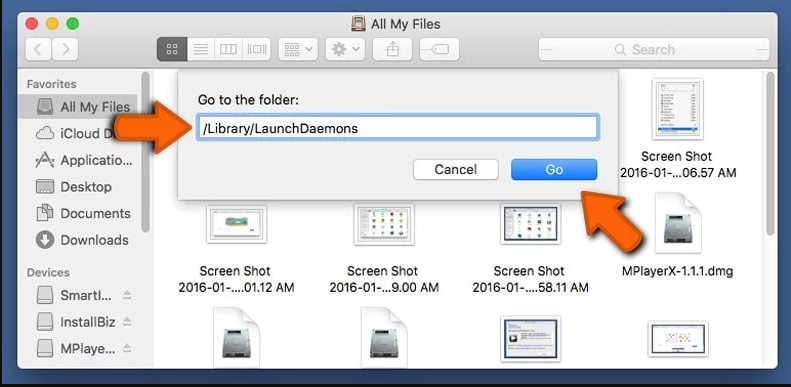
Type /Library/LaunchDaemons in the “Go To Folder” option
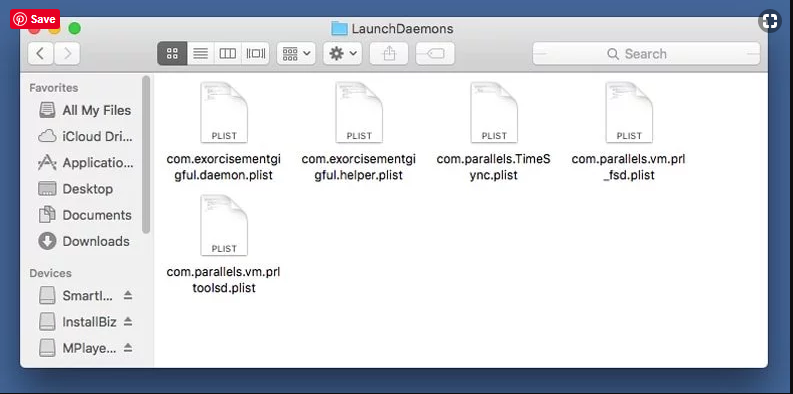
In the newly opened “LaunchDaemons” folder, search for any recently added suspicious files and move them to “Trash”. Examples of some of the suspicious files are “com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, “com.myppes.net-preference.plist”, “com.aoudad.net-preferences.plist” and so on.
Step 5: Use Combo Cleaner Anti-Malware and Scan your Mac PC
The malware infections could be removed from the Mac PC if you execute all the steps mentioned above in the correct way. However, it is always advised to be sure that your PC is not infected. It is suggested to scan the work-station with “Combo Cleaner Anti-virus”.
Special Offer (For Macintosh)
iTerm2 Malware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Once the file gets downloaded, double click on combocleaner.dmg installer in the newly opened window. Next is to open the “Launchpad” and press on “Combo Cleaner” icon. It is advised to wait until “Combo Cleaner” updates the latest definition for malware detection. Click on “Start Combo Scan” button.
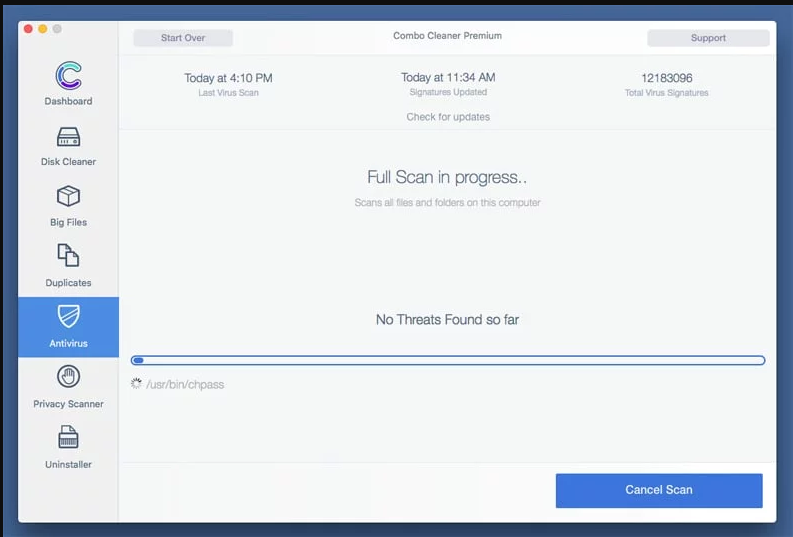
A depth scan of your Mac PC will be executed in order to detect malware. If the Anti-virus scan report says “no threat found” then you can continue with guide further. On the other hand, it is recommended to delete the detected malware infection before continuing.
Now the files and folders created by the adware is removed, you have to remove the rogue extensions from the browsers.
Remove iTerm2 Malware from Internet Browsers
Delete Doubtful and Malicious Extension from Safari
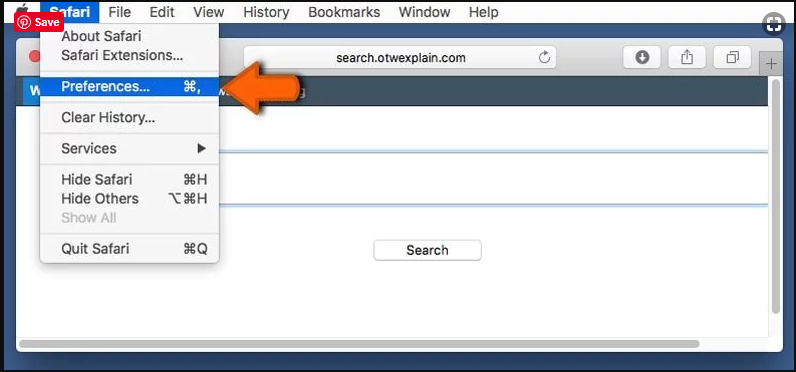
Go to “Menu Bar” and open “Safari” browser. Select “Safari” and then “Preferences”
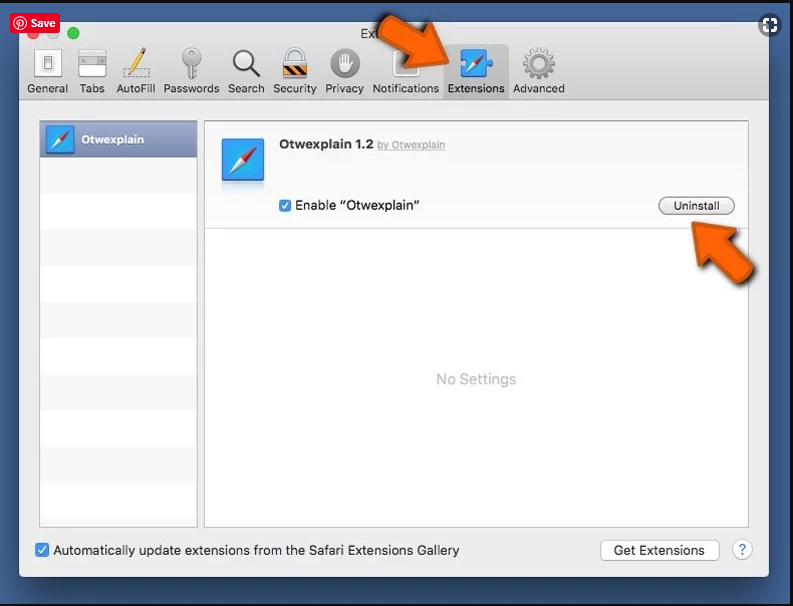
In the opened “preferences” window, select “Extensions” that you have recently installed. All such extensions should be detected and click the “Uninstall” button next to it. If you are doubtful then you can remove all the extensions from “Safari” browser as none of them are important for smooth functionality of the browser.
In case if you continue facing unwanted webpage redirections or aggressive advertisements bombarding, you can reset the “Safari” browser.
“Reset Safari”
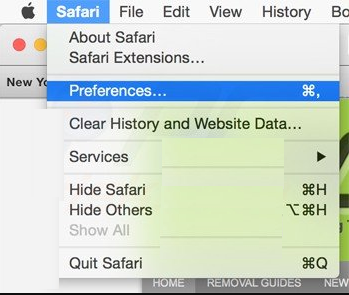
Open the Safari menu and choose “preferences…” from the drop-down menu.
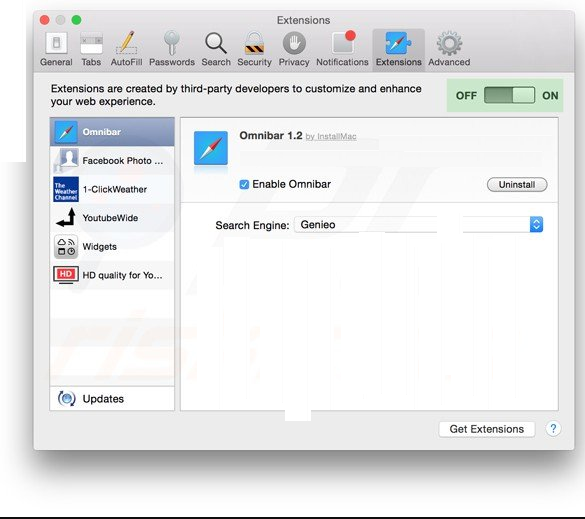
Go to the “Extension” tab and set the extension slider to “Off” position. This disables all the installed extensions in the Safari browser
Next step is to check the homepage. Go to “Preferences…” option and choose “General” tab. Change the homepage to your preferred URL.
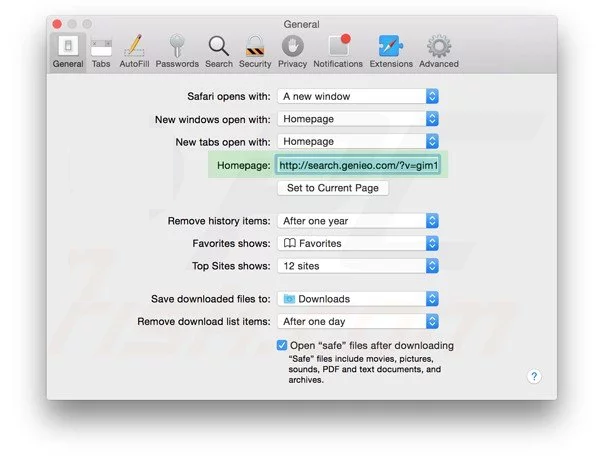
Also check the default search-engine provider settings. Go to “Preferences…” window and select the “Search” tab and select the search-engine provider that you want such as “Google”.
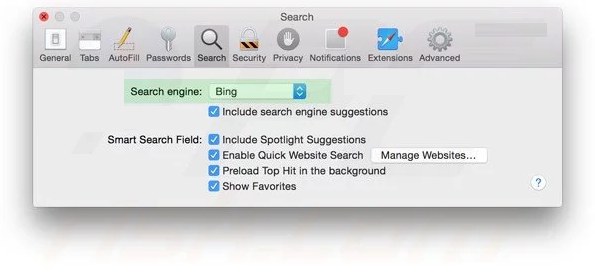
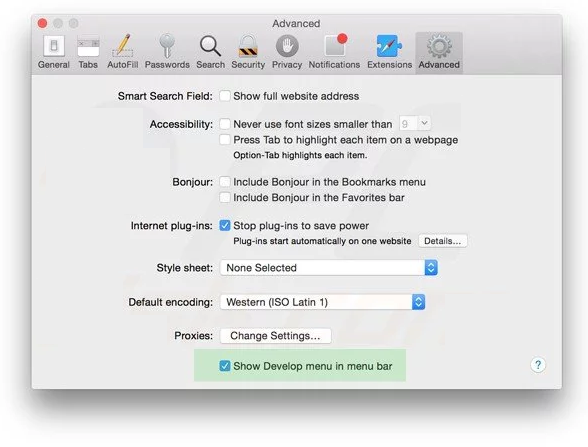
Next is to clear the Safari browser Cache- Go to “Preferences…” window and select “Advanced” tab and click on “Show develop menu in the menu bar.“
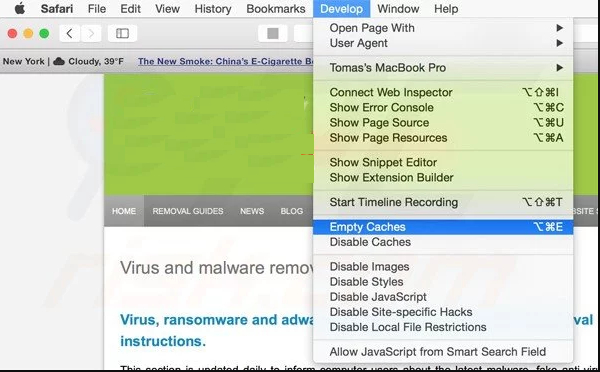
Go to “Develop” menu and select “Empty Caches”.
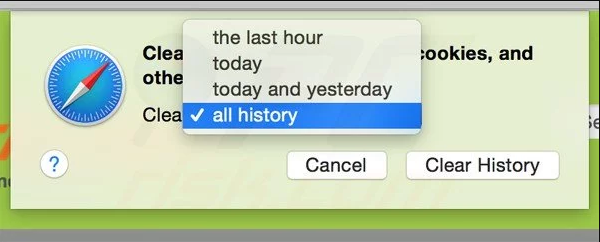
Remove website data and browsing history. Go to “Safari” menu and select “Clear History and Website Data”. Choose “all history” and then click on “Clear History”.
Remove Unwanted and Malicious Plug-ins from Mozilla Firefox
Delete iTerm2 Malware add-ons from Mozilla Firefox

Open the Firefox Mozilla browser. Click on the “Open Menu” present in the top right corner of the screen. From the newly opened menu, choose “Add-ons”.
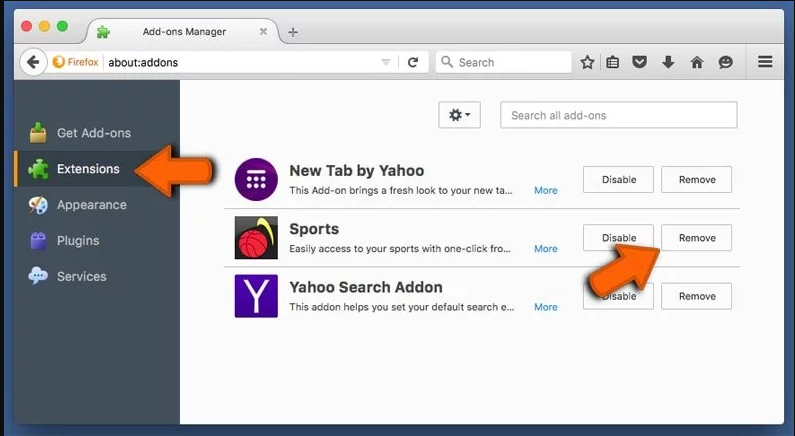
Go to “Extension” option and detect all the latest installed add-ons. Select each of the suspicious add-ons and click on “Remove” button next to them.
In case if you want to “reset” the Mozilla Firefox browser then follow the steps that has been mentioned below.
Reset Mozilla Firefox Settings
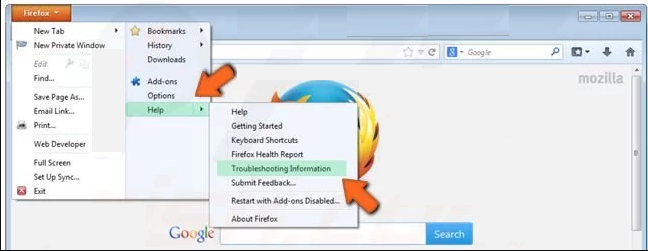
Open the Firefox Mozilla browser and click on “Firefox” button situated at the top left corner of the screen.

In the new menu, go to “Help” sub-menu and choose “Troubleshooting Information”
In the “Troubleshooting Information” page, click on “Reset Firefox” button.
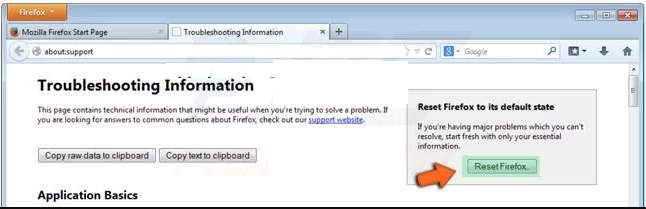
Confirm that you want to reset the Mozilla Firefox settings to default by pressing on “Reset Firefox” option
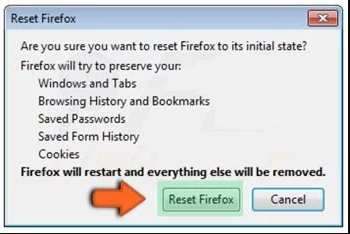
The browser will get restarted and the settings changes to factory default
Delete Unwanted and Malicious Extensions from Google Chrome
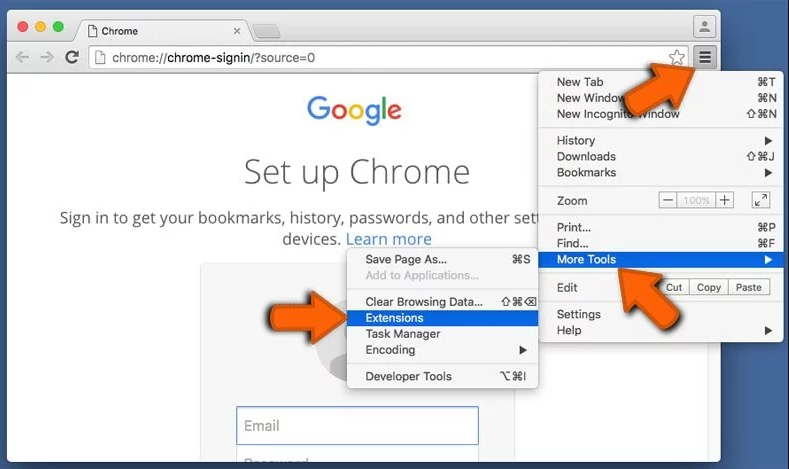
Open the chrome browser and click on “Chrome menu”. From the drop down option, choose “More Tools” and then “Extensions”.
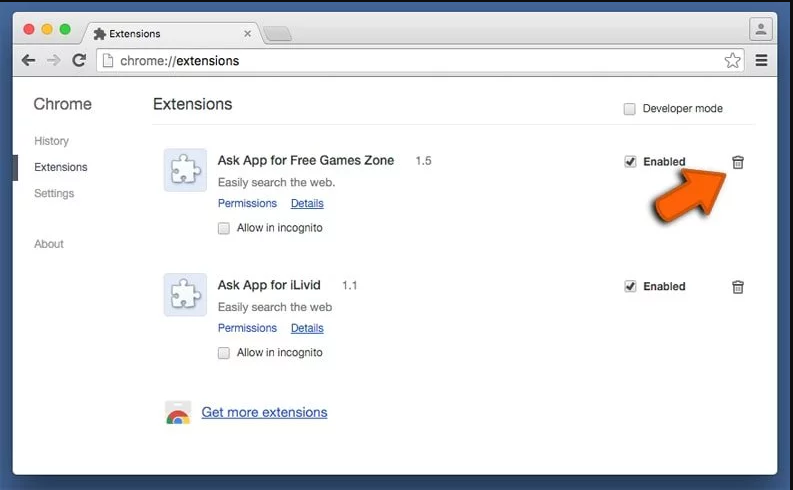
In the “Extensions” option, search for all the recently installed add-ons and extensions. Select them and choose “Trash” button. Any third-party extension is not important for the smooth functionality of the browser.
Reset Google Chrome Settings
Open the browser and click on three line bar at the top right side corner of the window.
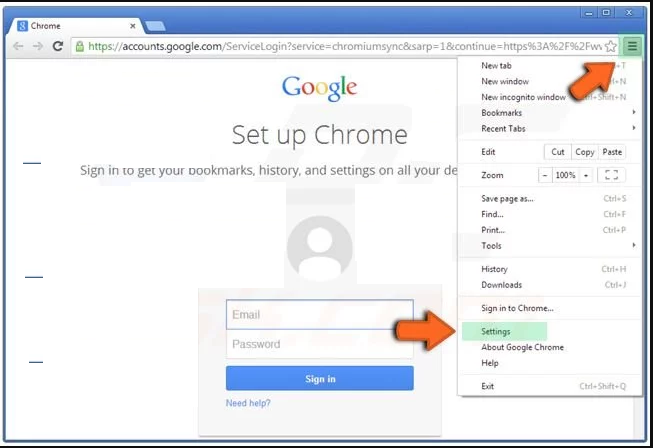
Go to the bottom of the newly opened window and select “Show advanced settings”.
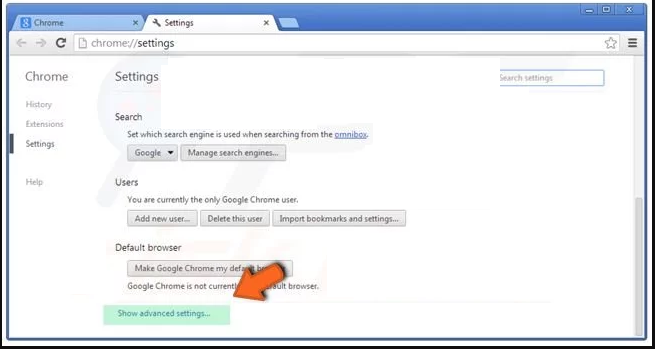
In the newly opened window, scroll down to the bottom and choose “Reset browser settings”
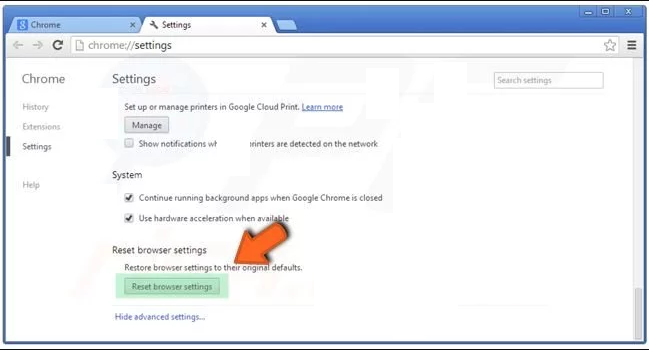
Click on the “Reset” button on the opened “Reset browser settings” window
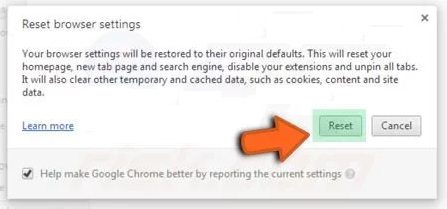
Restart the browser and the changes you get will be applied
The above mentioned manual process should be executed as it is mentioned. It is a cumbersome process and requires a lot of technical expertise. And hence it is advised for technical experts only. To be sure that your PC is free from malware, it is better that you scan the work-station with a powerful anti-malware tool. The automatic malware removal application is preferred because it doesn’t requires any additional technical skills and expertise.
Special Offer (For Macintosh)
iTerm2 Malware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Download the application and execute it on the PC to begin the depth scanning. Once the scanning gets completed, it shows the list of all the files related to iTerm2 Malware. You can select such harmful files and folders and remove them immediately.



