Google releases fix of bug allowing attackers to send spoofed emails
Google released the fix of the bug on Gmail and G Suite, allowing attackers to send spoofed emails as any other Google user or enterprise customer.

The bug, discovered by security researcher Allison Husain, is caused by missing verification when configuring mail routes. “both Gmail’s and any G Suite customer’s strict DMARC/SPF policy may be subverted by using G Suite’s mail routing rules to relay and grant authenticity to fraudulent messages,” he said.
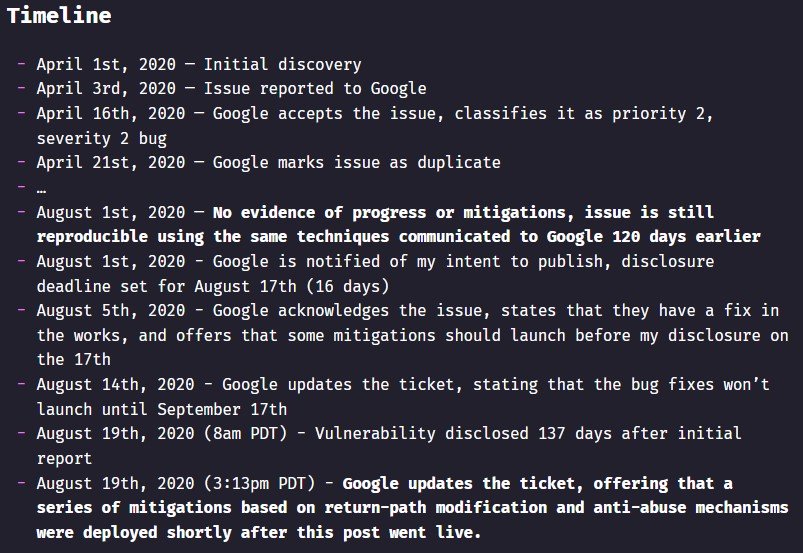
Attackers would abuse the recipient issue in Google’s mail validation rules and use an inbound email gateway to resend message from Google’s backend to gain the trust of downstream mail servers.
“This is advantageous for an attacker if the victim they intend to impersonate also uses Gmail or G Suite because it means the message sent by Google’s backend will pass both SPF and DMARC as their domain will, by nature of using G Suite, be configured to allow Google’s backend to send mail from their domain,” Husain explained.
“Additionally, since the message is originating from Google’s backend, it is also likely that the message will have a lower spam score and so should be filtered less often.”
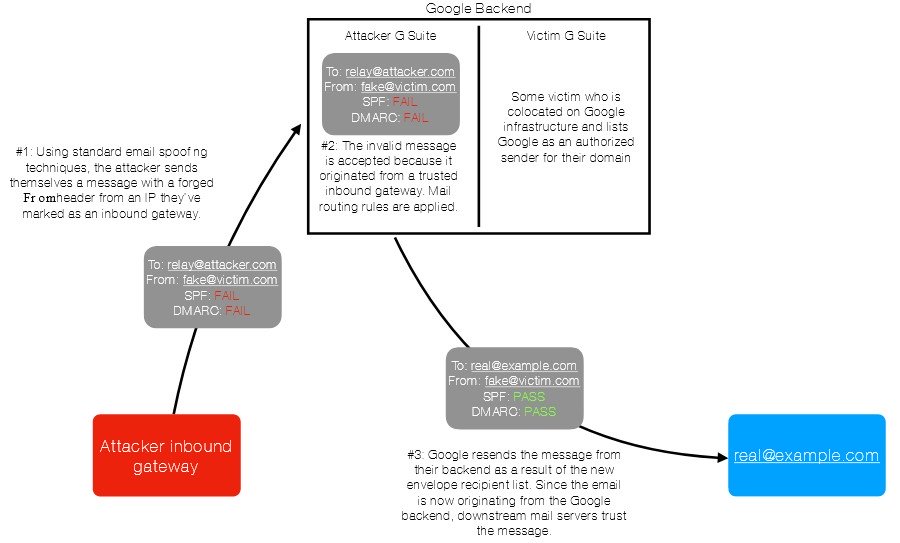
Husain reported the issue to the Google on April 3rd, 2020. Google accepted this issue on 16th of April (as the disclosure timeline published by the researcher says) classified it as a priority 2, severity 2 bug, subsequently marking it as duplicate.
The researcher initially notified the company that the bug would be disclosed on 17th of August. That time, Google said that a fix is being developed with an estimated time of rollout of September 17th.
However, when the company failed to fix the issue reported by Husain for 137 day, the researcher disclosed the findings on August 19th (two days after the disclosure of the timeline). Within 7 hours of this disclosure, Google deployed “mitigations based on return-path modification and anti-abuse mechanisms.”