Attackers abuses Google Ads with a new campaign to bypass email filters
Unknown attackers come with a new phishing scam, abusing Google ads to bypass secure email gateway in order to redirect the employees of the targeted organization to some phishing pages so as to steal their Microsoft accounts.
SEGs or Secure Emails Gateways are designed to block spam and phishing messages using filtering attacks that scan the incoming emails for malicious content before them being reaching to the users’ mailboxes.
It is likely that they are taking advantage of the fact that domains used Google Ads platform is overlooked by SEGs. This allows the attackers to deliver their phishing messages to the targeted inboxes by bypassing the email filters.
Cofense Phishing Defender Centre (PDC) researchers were the one who spotted the campaign first. According to them, the phishing messages were sent to employees of multiple organizations from compromised accounts.
The potential victims are informed of some policy changes and are asked to accept the changes so as to continue to services. Clicking on the accept button which is embedded on the phishing messages will redirect them to some phishing pages with the help of Google Ads redirect.
This hints to the fact that the attackers are likely paying for a Google ad and then use the ad’s URL to redirect the targets to the pages so as to steal Office 365 accounts, thus making ensure that the phishing messages reach to the targets.
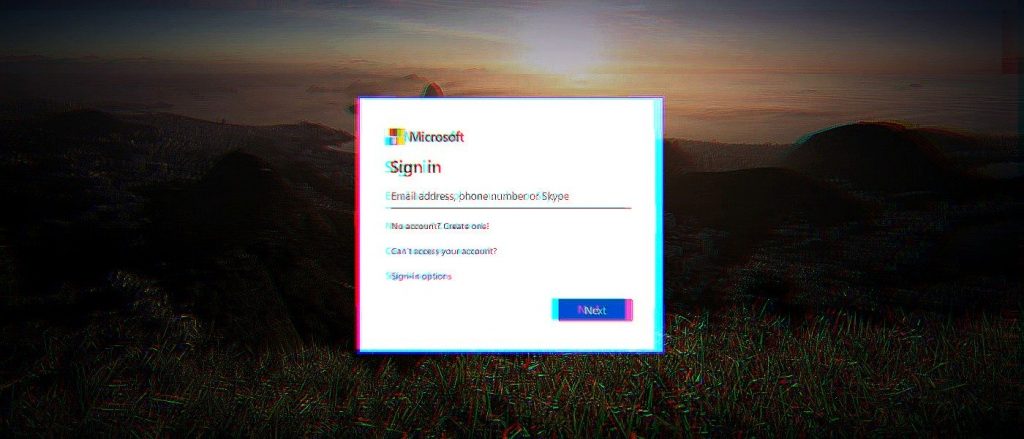
The phishing pages mimic legit Microsoft page, featuring a Microsoft logo and the targets’ company logo. Targets are first sent a clone privacy policy page from Microsoft and then to the final phishing page that mimics the victims’ company branded Office 365 sign-in pages.
When they enter the credentials and then click on the Next button, their account info will automatically be sent to the scammers. The will receive the text “We’ve updated our terms.” At the final stage, the employees who fall for the scam will be sent to the Microsoft Service Agreement page.
Recent Bank of America phishing campaign is an example that the phishes have a wide array of tactics to make ensure that their phishing messages have a higher chance of circumvent their targets’ email protection filters. In this campaign, the scammers sent emails with body contents free of links to malicious looking domains, using SendGrid to successfully pass SPF, DKIM and DMARC authentic checks. Older campaigns used QR codes and WeTransfer file-sharing notifications to bypass the security filters.
The attackers were also seen abusing the Google, Docs, Google Drive and Microsoft SharePoint as a part of phishing campaigns to dodge SEGs with the purpose to steal credentials. They can use the scam for other purposes such malware distribution and financial data ex-filtration.




