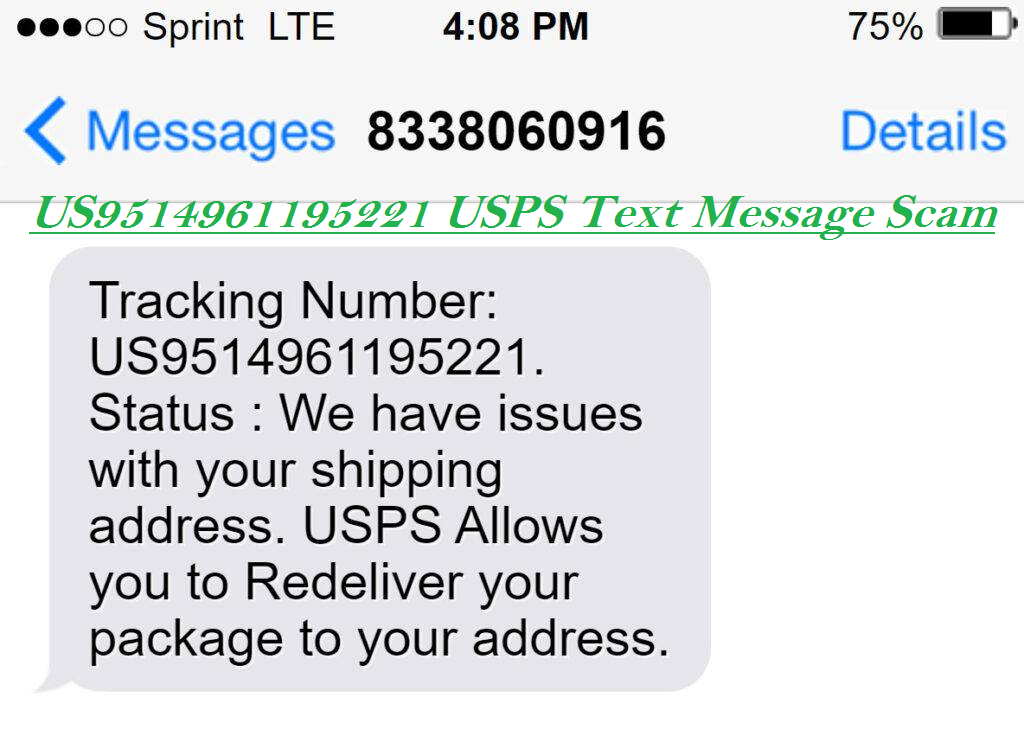
US9514961195221 USPS Text Message Scam
Contents
- What is US9514961195221 – USPS Text Message Scam?
- Is this a scam or real?
- What should we do now?
- Check if your device is infected by malware.
- Conclusion
It is a kind of scam which targets users through text messages; basically it sends texts messages containing links of fake USPS website. The message says you have an order which can’t be delivered because it has some problems with the delivery of the package. This message seems normal delivery message so it is easy to be a victim of such kinds of scam.
What is US9514961195221 – USPS Text Message Scam?
There are lots of scams coming over internetevery day. It is also a kind of scam which says that click on the link to get your package delivered. They also share a link along with the message.If you click on the link, it will redirect you to a suspicious website where you will be asked to fill your personal information like bank details, address, credit card details etc. This collected information are later misused or shared illegally with third-parties.
US9514961195221 – USPS Text Message is designed in such way that it seems real. Design of the website makes everyone trust it easily; here people are trapped because website seems real, so most of the person visiting here shares their personal information without any doubt which later on creates problems.
How does this scam work?
Scammers use different techniques for scams, there is a method called as spoofing which comes under phishing is used by scammers to make exact copy of the genuinewebsite which they use to trap the user. By the help of spoofing, scammers design their website which is a disguise of the original USPS website.
Scammers often send the link in the message which is a malicious link, andif someone clicks such link is redirected to a phishing website. Scammers also use same logo and the graphics of the original USPS website which makes duplicate website more trustworthy.
People are asked to share their personal information like bank details, credit card details, and addresses. They also ask the victims to pay for the re-delivery. These personal information shared to the scammers may be misused in many ways, they may do identity fraud, make fraudulent purchases and also may sell these information to the criminals.
How to spot scams?
Whenever you receive such messages you have to look at few details of it before clicking on the links shared in the message. I am sharing few points to look at before clicking on the link.
First thing you can do is, if you have any doubt about the message that it may be a scam or malicious than avoid clicking on it. If the text message you have got is creating urgency, be doubtful there because authentic website does notdo such things. It is a common trick used by phishing scams to create a sense of urgency. There is high possibility that you will click on the link and share your personal information immediately without thinking or taking much time.
Copy the tracking code from the text message and track it on the official USPS website. https://tools.usps.com/go/TrackConfirmAction_input
If you receive any text messages regarding deliveries or package which you haven’t ordered, stop and think for a while before clicking on the link. Just think that how can you get a message regarding delivery or redelivery if you haven’t ordered anything?
The most common ways to identify a scam is inconsistencies in domain names and the numbers from which you have got the message, if message says to be from USPL than why is it delivering from a random number.
What actions should be taken whenever we receive your package can not be delivered text.
In conclusion, here are few ways recommended by us to do whenever you get such messages
You are strongly suggested to not pay any redelivery fee or delivery fee. Do not trust any such messages; it is a scam to get you trapped. Do not click on any of the links shared in the message it may trick you to download malicious software. You should immediately report the scam text to the FTC at https://www.ftc.gov/
By any chance you have sent the payment to scammer you should instantly contact the related authority to stop your transaction and get a refund or get your transaction reversed. Click on the link to contact the FTC. (https://consumer.ftc.gov/articles/what-do-if-you-were-scammed) FTC stands for Federal trade commission which is a government body that regulates scam.
You are advised to install an antivirus or anti phishing software.
Few examples of scam-texts
Here are some examples of messages that are sent by scammers.
- Your package cannot be delivered to you temporarily because the delivery address is unknown, please update the address in time. https://ups-reyact.us
- Your order will not be shipped due to the wrong address you delivered to. Please update in time. usplocommbt.info
- Your package cannot be delivered due to incorrect house number. Please fill in the correct address online for re-deliver: https://usp-sopwd.top
- USP-Delivery of your package can’t be completed due to your incomplete address info. Please update your address online asap. https://tiny.one/upustous-us
- Your package cannot be delivered due to an incorrect street address. Modify the address in time to ensure delivery as scheduled. tinyurl.com/USP-Service-uspcx
- There is an error in your address, which prevents the package from being delivered accurately, pls modify it
- US/P.S Your street information is incorrect and cannot be delivered, please confirm your address now: www.ups-e4vhs.us.
- There is an error in your address, which prevents the package from being delivered accurately, pls modify it
- We are unable to deliver your package to your door because your package does not have your house number, please update
- The carrier was unable to deliver your order because the shipping information is missing a house number. Check, please. uspaddetast.info/
- Your package could not be delivered due to incorrect house number information. Please fill in the correct address online for re-deliver. https://usp-sbnth.top
- Your package is on hold at the post office because of delivery address is wrong, please fill in the address online [US-PS] https://t.co/…
- We were unable to deliver your package to you because your home address is incomplete.
- Your package has been returned due to wrong house number, please change your address in time to arrange delivery.[US-PS]
- We were unable to deliver your package because the shipping address could not be verified. Please resubmit your address for verification.
- Your package has arrived at the fulfillment center, but the delivery address is incorrect and the package is awaiting delivery. uspunewdata.info
- Package could not be delivered due to missing street number information for delivery address. Please update complete address information. usparllcsub.info
- USPS: We are unable to ship due to incomplete address information on the package label. Fill in the correct address information via the link
- [US-PS] Your courier could not be delivered due to incorrect street information. Fill in the correct address for re-delivery:https://useuhy.com
- The package could not be delivered to your door because your street address information is incomplete. Please update or it will be returned. uspconying.info/FAQ
- Postal: Your expedited parcel address is insufficient and cannot be delivered to your door. Please update it in time. http://qiyidyw.com
- USPS: Because your address is not detailed on the package label, we are unable to deliver to your door. View, close: parldate.info/FAQs
- Package delivery failed. schedule redelivery. Please confirm the information: https://www.us-ps-trac9k.us
- U.S.P.S: Your package has arrived at the fulfillment center, but we cannot deliver it due to an incomplete address. Please update usptacriex.info
In terms of email-based cyber threats, what are the different types of malicious emails?
Emails having Malicious Attachments

Email spam containing malicious attachments is a commonly employed method by cybercriminals to compromise users’ computers with malware. Malicious attachments often harbor trojans that possess the ability to pilfer sensitive data such as banking details, passwords, and other confidential information.
The primary objective of cybercriminals in these attacks is to deceive their potential victims into accessing a compromised email attachment. They commonly employ email messages that discuss recently obtained invoices, faxes, or voice messages to accomplish this aim.
If an unsuspecting individual succumbs to the trap and opens the attachment, their computer becomes infected, allowing cybercriminals to gather a substantial amount of confidential data.
Although it is a more intricate technique to pilfer personal data (as spam filters and antivirus programs typically identify such endeavors), if cybercriminals achieve success, they can access a broader spectrum of information and continue accumulating data over an extended duration.
Phishing Emails

Typically, cybercriminals employ deceitful emails to deceive individuals on the internet into divulging their confidential personal information, such as login credentials for diverse online platforms, email accounts, or online banking details.
These types of attacks are commonly known as phishing. In a phishing attack, cybercriminals typically send an email that mimics the branding of popular services like Microsoft, Amazon, DHL, or Netflix. They craft messages with a sense of urgency, such as incorrect shipping details or expired passwords, and include a hyperlink, hoping to entice unsuspecting recipients into clicking on it.
Upon clicking the provided link in these email messages, victims are redirected to a counterfeit website that closely resembles the legitimate one. In this deceptive environment, victims are prompted to enter their password, credit card information, or other sensitive data, which is subsequently harvested by cybercriminals for malicious purposes.
Spam Emails

Spam emails are unsolicited, bulk messages sent to a large number of recipients simultaneously. They often contain unwanted advertisements, scams, or fraudulent offers. The primary purpose of spam emails is to promote products, services, or websites, sometimes of dubious nature.
These emails can be sent by individuals or automated bots, and they often target a wide range of recipients without their consent. Spam emails can clog up inboxes, consume storage space, and pose risks such as phishing attempts or malware distribution.
Sextortion Emails

This type of email is a form of phishing known as a “sextortion scam.” It preys on individuals’ fears and attempts to blackmail them into paying a ransom. The scam email falsely claims that a cybercriminal has gained unauthorized access to the victim’s webcam and possesses a compromising video recording of them engaging in explicit activities.
The scammers leverage the potential embarrassment and shame associated with such content to coerce the victim into paying a ransom, often in the form of cryptocurrency, to prevent the release of the alleged video. However, it is crucial to understand that these claims are entirely false and fabricated.
What are some indicators or signs that can help identify a malicious email?

To spot a malicious email you can look for the following indicators:
Suspicious Sender: Check the sender’s email address and verify if it matches the official contact information of the organization or person they claim to represent. Be cautious of email addresses that contain misspellings, random numbers, or unfamiliar domain names.
- Poorly Written Content: Pay attention to grammar and spelling mistakes, unusual language, or poor formatting. Legitimate organizations usually maintain professional communication standards.
- Urgent or Threatening Language: Beware of emails that create a sense of urgency, pressure you to take immediate action, or threaten negative consequences if you don’t comply. Scammers often use fear or time-sensitive situations to manipulate victims.
- Suspicious Attachments or Links: Be careful of email attachments or links, especially from unknown or unexpected sources. Don’t open attachments or click on links unless you are confident about their legitimacy. Hover over links to see the actual URL before clicking.
- Requests for Personal Information: Legitimate organizations typically don’t request senstive information, such as passwords, Social Security numbers, or credit card details, via email. Avoid providing personal data unless you are certain of the email’s authenticity.
- Unusual Requests or Offers: Be wary of emails offering unexpected rewards, prizes, or financial opportunities. If something seems too good to be true or doesn’t align with your normal interactions, it could be a sign of a scam.
- Suspicious Email Design: Poorly designed or visually inconsistent emails may indicate a scam. Watch for generic greetings, mismatched logos, or distorted images.
If you have doubts about an email’s legitimacy, it’s best to err on the side of caution. Avoid clicking on links or downloading attachments, and consider contacting the sender through a verified channel to verify the email’s authenticity.
What actions can be taken if you have fallen for an email scam?

Below are the steps you should take if you’ve fallen prey to the US9514961195221 USPS Text Message Scam.
- If you have mistakenly provided your credit card information after clicking on a link in a phishing email, it is crucial to immediately contact your bank and inform them about the situation. It is highly likely that you will need to take steps to cancel the compromised credit card and request a replacement for enhanced security.
- If you have inadvertently provided your password after falling for an email scam, it is essential to promptly change your password. Typically, cybercriminals gather stolen login details and sell them to other malicious groups for potential exploitation. By changing your password immediately, you reduce the likelihood of criminals having sufficient time to cause harm or unauthorized access to your accounts and information.
- If you notice any indications of identity theft, it is important to promptly reach out to the Federal Trade Commission (FTC). The FTC will gather information about your situation and develop a personalized recovery strategy.
- Assist in safeguarding fellow internet users by reporting phishing emails to organizations such as the National Fraud Information Center, Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, and the U.S. Department of Justice.
- If you have inadvertently opened a malicious attachment, it is likely that your computer has been compromised. To address this, it is advised to conduct a thorough scan of your system using a reliable antivirus software. We suggest utilizing SpyHunter 5 for Windows to help mitigate any potential threats.
⇓⇓Download Spyhunter 5 Free Scanner⇓⇓
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Frequently Asked Questions
Why was I included in the distribution of this email?
Phishing emails are often disseminated by threat actors through extensive campaigns, leading to thousands of recipients receiving comparable messages.
If I have viewed a spam email but refrained from opening the attachment, is there a possibility that my computer has been infected with malware?
Simply opening or reading an email does not pose a direct risk of malware infection. The actual threat arises when you interact with malicious attachments or links contained within the email, triggering potential malware download or installation processes.
If I downloaded and opened a file from a spam email, does that mean my computer is infected? How can this question be asked in a different form?
If the file you opened from a spam email was an executable file (.exe, .run, etc.), there is a high chance that your computer may be infected. However, if the file was a document format (.doc, .xls, .one, .pdf, etc.), the risk of infection may be lower as these formats usually require additional actions to initiate the download or installation of malware, such as enabling macros or clicking on embedded content.
If I have unknowingly shared your personal information in response to a deceptive spam email, what steps should I take to mitigate the potential risks?
If you have mistakenly shared your login credentials, it is crucial to change the passwords for all affected accounts promptly. Additionally, if sensitive personal information like identification documents or credit card details were disclosed, it is important to promptly notify the relevant authorities or organizations responsible for handling such incidents.
Is SpyHunter 5 capable of detecting and eliminating malware infections that may be present in email attachments?
SpyHunter 5 is powerful security software that is specifically designed to scan devices and effectively remove various types of malware infections. With its comprehensive scanning capabilities, it can detect and eliminate most known malware threats, including those that may be present in email attachments and pop-up notifications. Running a thorough system scan is crucial to ensure that all potential threats are identified and removed from your device.




