Remove Zhen ransomware And Restore Encrypted Files
Simple Steps To Delete Zhen ransomware
Zhen ransomware is a kind of highly dangerous file-locking virus that was first discovered by security researcher GrujaRS. This hazardous malware tends to encrypt files stored inside the Windows computers and then demand a huge amount of ransom from its victims. It often infiltrates the targeted PCs by stealth without users’ approval and then modifies the default registry settings in order to get automatically activated with each system reboot. After that, it starts file-locking process. It uses a sophisticated encryption algorithm to encrypt files and documents and makes users unable to open them again.
Depth Analysis of Zhen ransomware:
Zhen ransomware is a kind of virus that can compromise almost all types of files including videos, audios, music, PDFs, spreadsheets etc. The infected files can be easily identified as it appends “.zhen” extension with each of them as suffix. After completing the encryption process, this precarious crypto-malware displays couple of ransom notes in a pop-up window and “read.ini” file. These notes inform the affected people regarding the attack and also provide them file-recovery instruction.
Ransom notes exhibited by Zhen ransomware state that all your files and data have been encrypted and ask victims to pay the ransom. Crooks demand 0.3 BTC (BitCoin cryptocurrency) which is approx. $3000 (at the time of writing) to get the decryption software and open the locked files. Criminals state that once the ransom is paid, the decryption process will begin automatically. Victims are also warned not to delete the ransom notes. Moreover, they are also asked to deactivate their anti-virus suites as this tool can remove the virus.
Text Presented In The Ransom Notes:
Pay to get your files back!
Status
Payment Status: Unpaid!
Check Payment
Steps;
[+] Do not remove this file.
[+] Disable security applications.
[+] Dont waste your time and pay.
What Happened to My Computer?
Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are
busy looking for a way to recover your files, but do not waste your time. Nobody can recover your files without our decryption service.
Can I Recover My Files?
Sure. We guarantee that you can recover all your files safely and easily. But you have not so enough time.
If you want to decrypt all your files, you need to pay.
How Do I Pay?
Payment is accepted in Bitcoin only. For more information, click .
Please check the current price of Bitcoin and buy some bitcoins. For more information, click .
And send the correct amount to the address specified in this window.
After your payment, click .
Once the payment is checked, you can start decrypting your files immediately.
We strongly recommend you to not remove this software, and disable your anti-virus for a while, until you pay and the payment gets processed. If
your anti-virus gets updated and removes this software automatically, it will not be able to recover your files even if you pay!
- To pay us, you have to use Bitcoin currency. You can easily buy Bitcoins at following sites:
hxxps://cex.io/
hxxps://www.binance.com/
hxxps://www.coinbase.com/
- After then, if you already have Bitcoins, pay us 0.3 BTC on following our Bitcoin address.
- Then, press the “Check Payment” button. We will automatically decrypt your files, after bitcoin transfer.
Pay to this address (0.3 BTC): 14Fb82z4s345Ur6xSBHWZ7jidxXiQUDvAc
About Bitcoin How to Buy Bitcoin
Should You Pay the Ransom?
Zhen ransomware lays you in a situation where you may consider dealing with the attackers. However, you are highly recommended doing against this as there is a huge possibility that you will be scammed and end up with losing both files as well as money. Remember that the only purpose of such criminals is to swindle money from the victimized users. You shouldn’t trust on such people since most of the times they ignore the victims once the ransom is paid.
What Should The Victims Do?
If you are a victimized person, the first thing you need to do is to perform Zhen ransomware removal from the device immediately. As far as restoring the infected files is concerned, you should use alternative methods such as backups that you have saved on your external drive or a powerful data-recovery application. Paying ransom to the hackers is not a clever thing to do under any circumstance as it will only motivate them to drop more such viruses in the machine for further revenues.
Threat Details
Name: Zhen ransomware
Type: Ransomware, Crypto-virus
Short Description: Destructive malware which encrypts users’ important data and then asks them to pay the attackers an amount of ransom to get the decryption software.
Extension: “.zhen”
Ransom Demanding Message: Text presented in the pop-up window and read.ini
Ransom Amount: 0.3 BTC (Bitcoin cryptocurrency)
BitCoins Wallet address: 14Fb82z4s345Ur6xSBHWZ7jidxXiQUDvAc
Symptoms: Victims cannot open files stored on their system, previous functional files now have different extension, A ransom demanding message is displayed on the desktop screen. Users are asked to pay an amount of ransom to unlock their encoded data and files.
Distribution methods: Spam emails, Torrent websites, peer to peer network sharing, unofficial activation and updating tools.
Damage: All files are encrypted and cannot be accessed without paying ransom, Additional password stealing Trojans and malware infections can be installed along with ransomware infections and other malware.
Removal: To remove this virus from the system, we advise you to use a reliable anti-malware tool. Once malware gets removed, you can recover your files by using existing backup or data-recovery software.
Infiltration of Zhen ransomware:
Spam campaigns are the most common method through which, these crypto-viruses are spread. During such campaigns, fraudulent emails are sent by the thousand. These mails are usually presented as “official”, “urgent”, “important” and similar. However, they contain download links of infectious files or the files are merely attached to the letters. Virulent files can be in several formats (e.g. PDF and Microsoft Office documents, archives, JavaScript, executables, etc.) and when they are opened – the infection process is triggered.
To prevent this, you should not open the attachment of the mails that you receive from suspicious sender. First check the sender and content of the mail and if you find anything suspicious, ignore this. But at the moment, you must remove Zhen ransomware from the computer without wasting any time.
Special Offer (For Windows)
Zhen ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove Zhen ransomware through “Safe Mode with Networking”
Step 2: Delete Zhen ransomware using “System Restore”
Step 1: Remove Zhen ransomware through “Safe Mode with Networking”
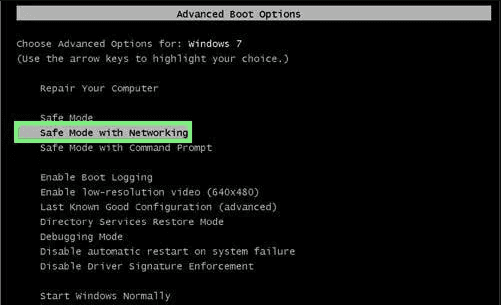
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
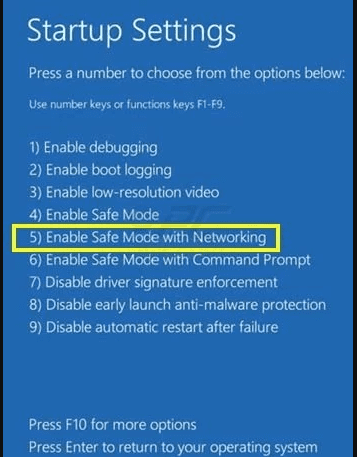
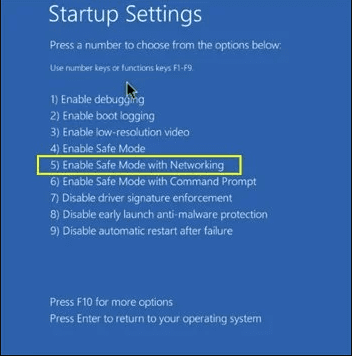
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
Step 2: Delete Zhen ransomware using “System Restore”
Log-in to the account infected with Zhen ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
Zhen ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
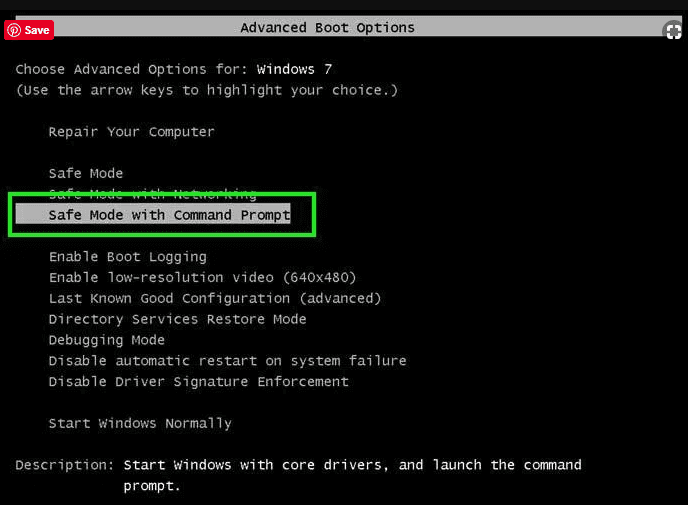
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
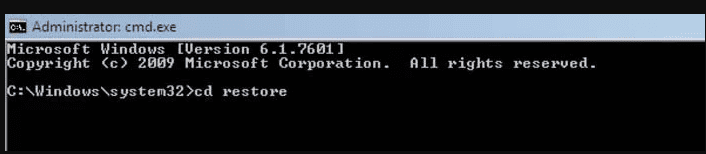
- Type: rstrui.exe and Press “ENTER”
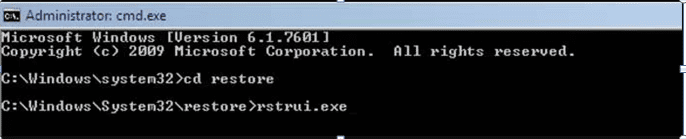
- Click “Next” on the new windows
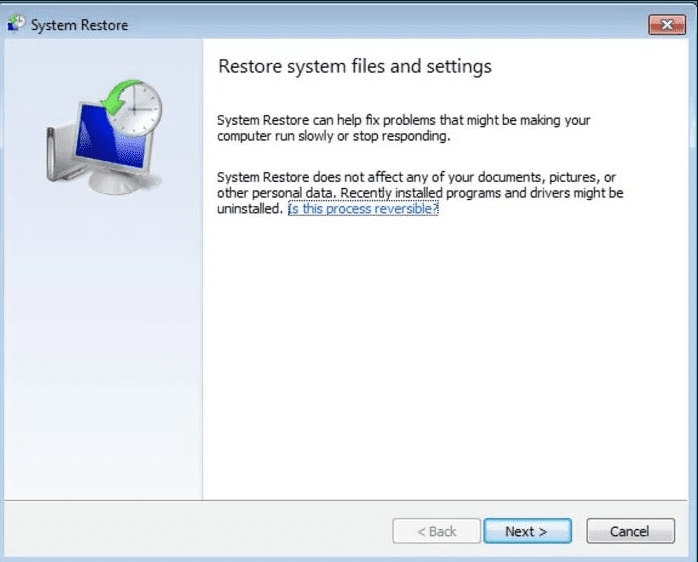
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to Zhen ransomware infiltration in the PC.
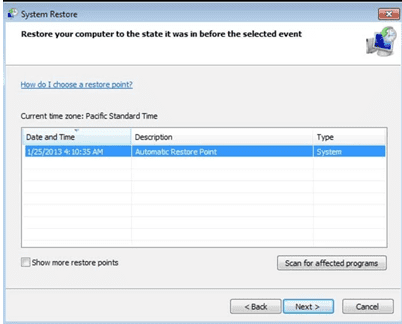
- In the newly opened windows, press on “Yes”.
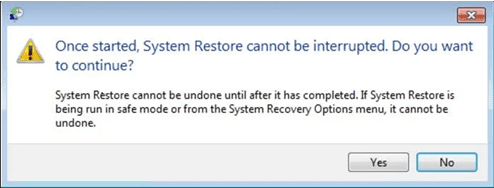
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove Zhen ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of Zhen ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
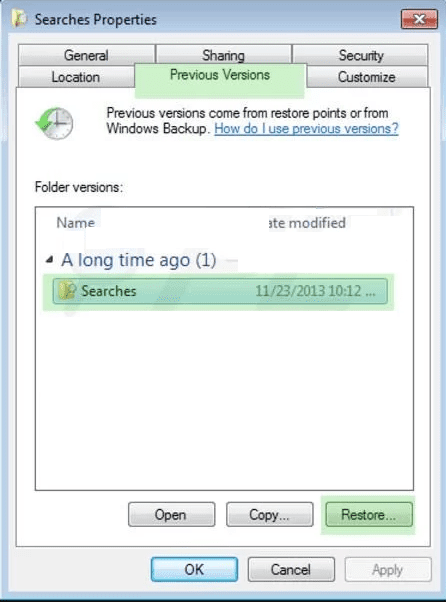
How to Restore Individual Encrypted File:
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
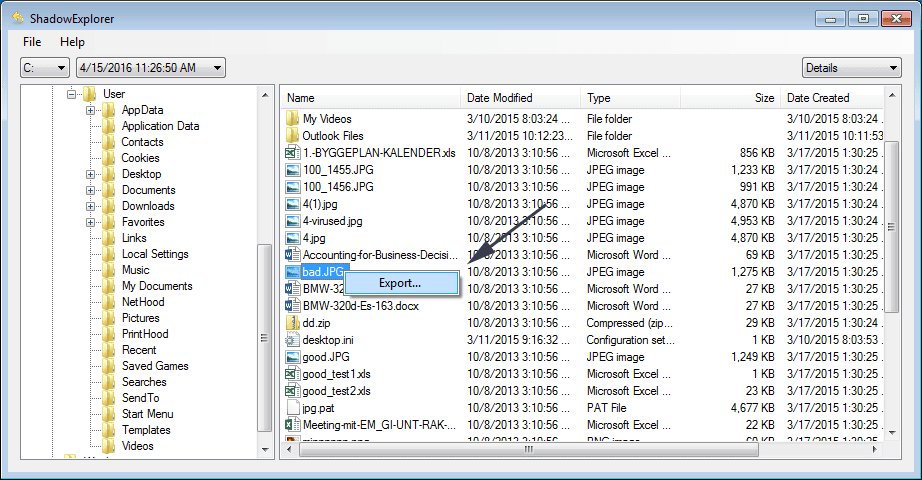
In order to access the files encrypted by Zhen ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like Zhen ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
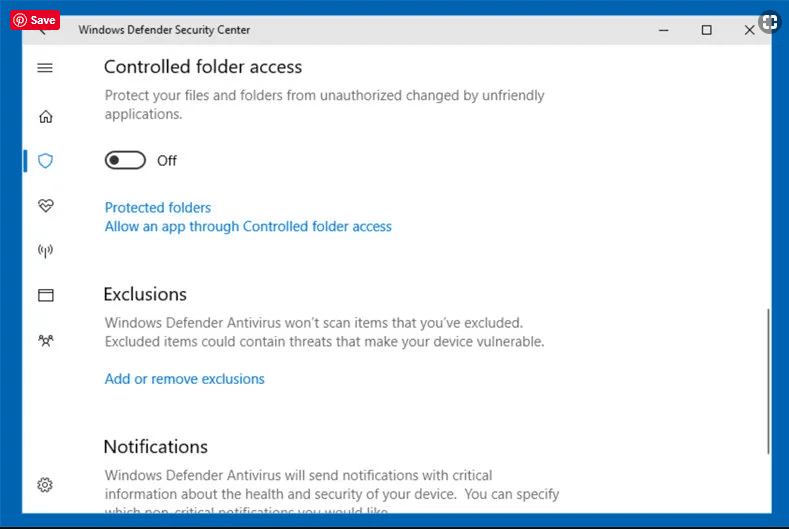
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by Zhen ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with Zhen ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove Zhen ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

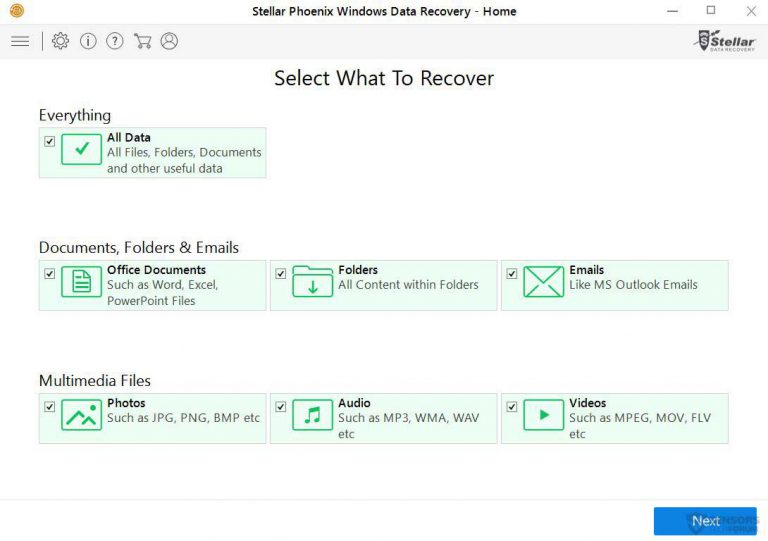
Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
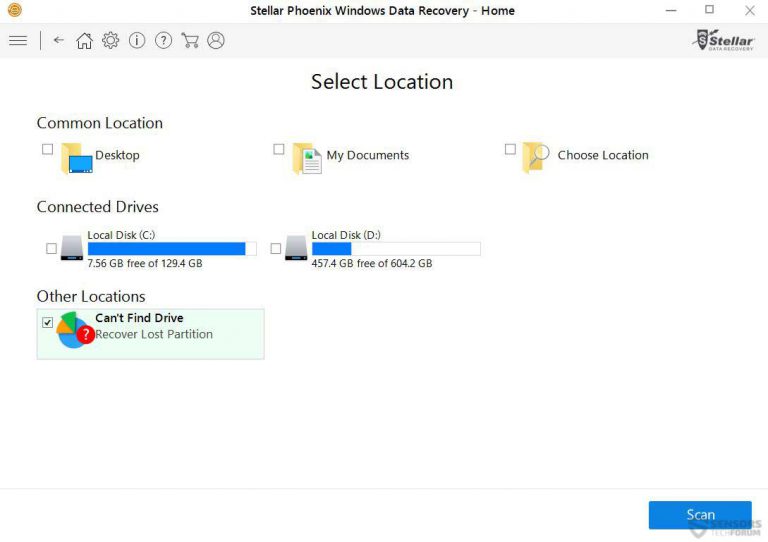
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
Zhen ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.