Remove TRU8 ransomware (Decrypt Locked Files)
TRU8 ransomware: Total Removal Instruction
TRU8 ransomware has been identified by security researchers as a devastating kind of PC threat that prevents users from accessing their files by encrypting those data. It comes from the family of Matrix ransomware and often uses a combination of AES-128 and RSA-2048 ciphers to lock videos, audios, images, documents, presentations etc. By doing so, it makes those files completely inaccessible and thus, victims are not able to open them afterwards. The compromised data can easily be identified as it renames them by adding attackers’ email address, a string of random characters and appending “.TRU8” extension with each of them.
Depth Analysis of TRU8 ransomware:
Following successful encryption, TRU8 ransomware leaves a ransom note titled “!README_TRU8!.rtf” on each affected folder and informs victims about the unkind situation. It also states that the files can only be opened by using a unique decryption key and special software which is stored on a remote server only for seven days. After that, it will be deleted and hence, data can’t be retrieved then after. To get information on how to purchase the tools, victims have to contact the attackers via the provided email addresses. Eventually, users may have to pay the crooks a ransom amount of $200 to $1500 in BitCoins cryptocurrency.
Should You Pay The Ransom?
Even though, data encrypted by TRU8 ransomware can’t be accessed without using the proper decryption tool, still, you should never pay the demanded ransom fee to the criminals. You have absolutely no guarantee that they will send you the required decryptor even after taking the extortion. It has been tendency of such hackers that they often disappear once the ransom is paid cause victims to lose both files as well as money. Sometimes, they deliver rogue software in the name of decryption tool which causes even more hazards when installed.
What Should The Victims Do?
If you are a victimized person, the first thing you need to do here is to perform TRU8 ransomware removal from the computer immediately. As far as restoring the infected files is concerned, you should use a recently made backup as this is the only method to restore the compromised data without losing your money. But the problem here is that all people don’t have an appropriate backup. If this is the case with you, then the only option left for you is to try a powerful file-recovery program that you can download right here via the link provided under this article. Paying ransom to the attackers is never recommended as it will only urge them to trigger more such attacks for future revenues.
Threat Summary
Name: TRU8 ransomware
Type: Ransomware, File-encrypting malware, Crypto-virus
Short Description: Hazardous malware that locks crucial data and then asks victims to pay the attackers a huge sum of ransom to get the decryption software/key.
Extension: “.TRU8”
Ransom Notes: !README_TRU8!.rtf
Attackers’ contact: [email protected], [email protected], [email protected]
Symptoms: Data become unusable stored inside infected systems, previous functional files now have different extension, a ransom demanding note is displayed. Victims are asked to pay an amount of ransom to decrypt their encrypted files.
Distribution methods: Spam emails, peer to peer network sharing, unofficial activation and updating tools.
Damage: All files are encrypted and cannot be accessed without paying ransom, Additional password stealing Trojans and malware infections can be installed along with ransomware infections and other malware.
Removal: To remove this virus from the system, we advise you to use a reliable anti-malware tool. Once malware gets removed, you can recover your files by using existing backup or data-recovery software.
Penetration of TRU8 ransomware:
There are various deceptive methods through which these file-encrypting viruses sneak into the target PCs but the most common one is spam email campaign. You often receive emails from unknown sender that pretend to be from some well-known companies or institutions but usually include malicious attachments or websites links that are designed to download some nasty files. The vicious attachment could be in any of these formats: executable files like .exe, MS office documents, archive files like ZIP and RAR, and JavaScript files etc. Once you click on the mail and open those attachments, it triggers the installation of ransomware.
And therefore, it is necessary to ignore suspicious mails coming from unknown source as you never know what they are containing. These emails are specially designed to trick recipients into downloading their attachment, so very attentive. In case your system is already infected with this crypto-malware, you must remove TRU8 ransomware from the machine without wasting any time.
Text Presented In The Ransom Note:
HOW TO RECOVER YOUR FILES INSTRUCTION
ATENTION!!!
We are realy sorry to inform you that ALL YOUR FILES WERE ENCRYPTED
by our automatic software. It became possible because of bad server security.
ATENTION!!!
Please don’t worry, we can help you to RESTORE your server to original
state and decrypt all your files quickly and safely!
INFORMATION!!!
Files are not broken!!!
Files were encrypted with AES-128+RSA-2048 crypto algorithms.
There is no way to decrypt your files without unique decryption key and special software. Your unique decryption key is securely stored on our server. For our safety, all information about your server and your decryption key will be automaticaly DELETED AFTER 7 DAYS! You will irrevocably lose all your data!
* Please note that all the attempts to recover your files by yourself or using third party tools will result only in irrevocable loss of your data!
* Please note that you can recover files only with your unique decryption key, which stored on our side. If you will use the help of third parties, you will only add a middleman.
HOW TO RECOVER FILES???
Please write us to the e-mail (write on English or use professional translator):
You have to send your message on each of our 3 emails due to the fact that the message may not reach their intended recipient for a variety of reasons!
In subject line write your personal ID:
25D36D56AAC78345
We recommed you to attach 3 encrypted files to your message. We will demonstrate that we can recover your files.
* Please note that files must not contain any valuable information and their total size must be less than 5Mb.
OUR ADVICE!!!
Please be sure that we will find common languge. We will restore all the data and give you recommedations how to configure the protection of your server.
We will definitely reach an agreement 😉 !!!
ALTERNATIVE COMMUNICATION
If yоu did nоt rеcеivе thе аnswеr frоm thе аfоrеcitеd еmаils fоr mоrе then 24 hours please sеnd us Bitmеssаgеs frоm а wеb brоwsеr thrоugh thе wеbpаgе hxxps://bitmsg.me. Bеlоw is а tutоriаl оn hоw tо sеnd bitmеssаgе viа wеb brоwsеr:
- Оpеn in yоur brоwsеr thе link hxxps://bitmsg.me/users/sign_up аnd mаkе thе rеgistrаtiоn bу еntеring nаmе еmаil аnd pаsswоrd.
- Уоu must cоnfirm thе rеgistrаtiоn, rеturn tо уоur еmаil аnd fоllоw thе instructiоns thаt wеrе sеnt tо уоu.
- Rеturn tо sitе аnd сlick “Lоgin” lаbеl оr usе link hxxps://bitmsg.me/users/sign_in, еntеr уоur еmаil аnd pаsswоrd аnd click thе “Sign in” buttоn.
- Сlick thе “Сrеаtе Rаndоm аddrеss” buttоn.
- Сlick thе “Nеw mаssаgе” buttоn.
- Sеnding mеssаgе:
Tо: Еntеr аddrеss: empty
Subjесt: Еntеr уоur ID: –
Mеssаgе: Dеscribе whаt уоu think nеcеssаrу.
Сlick thе “Sеnd mеssаgе” buttоn.
Special Offer (For Windows)
TRU8 ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove TRU8 ransomware through “Safe Mode with Networking”
Step 2: Delete TRU8 ransomware using “System Restore”
Step 1: Remove TRU8 ransomware through “Safe Mode with Networking”
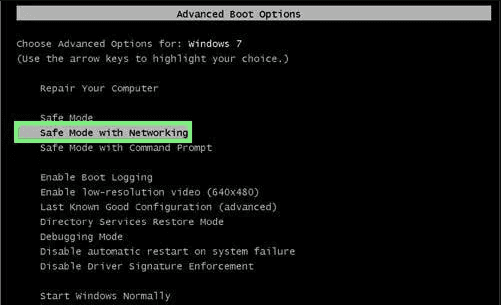
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
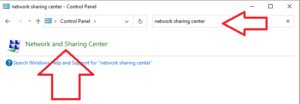
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
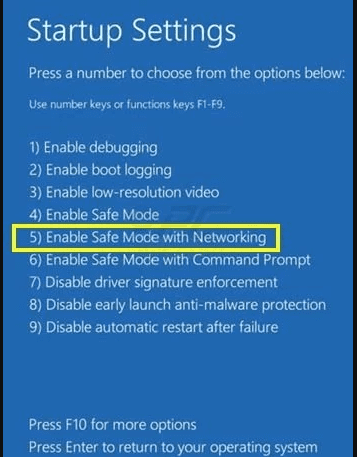
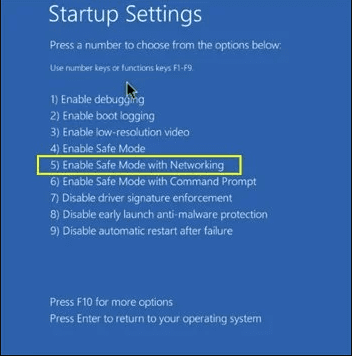
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
Step 2: Delete TRU8 ransomware using “System Restore”
Log-in to the account infected with TRU8 ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
TRU8 ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
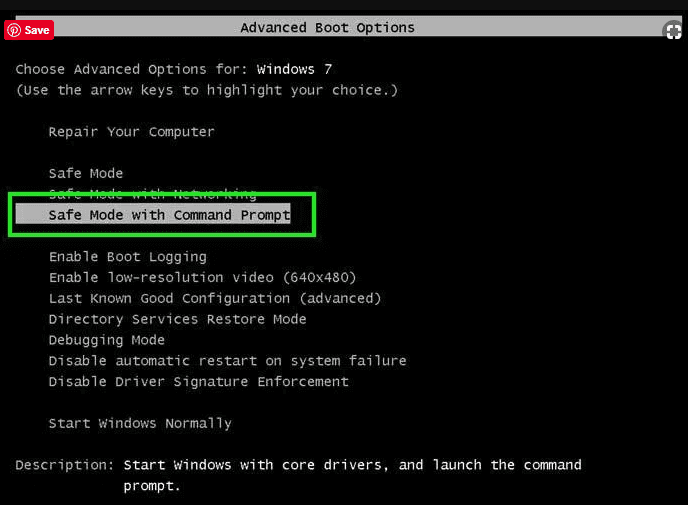
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
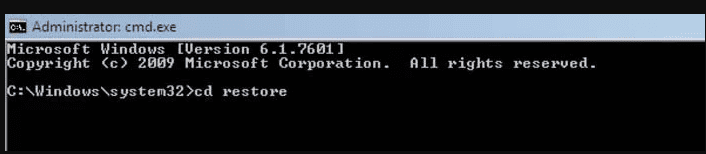
- Type: rstrui.exe and Press “ENTER”
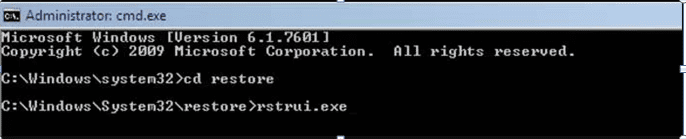
- Click “Next” on the new windows
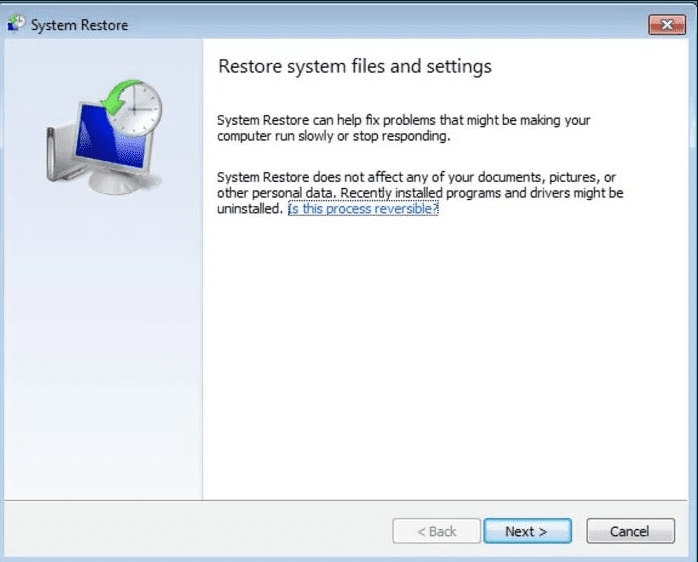
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to TRU8 ransomware infiltration in the PC.
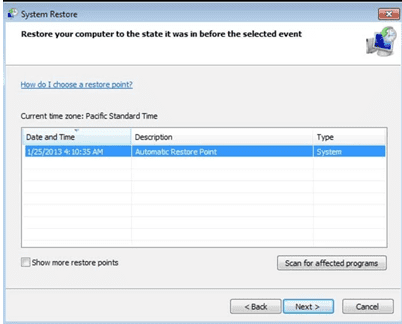
- In the newly opened windows, press on “Yes”.
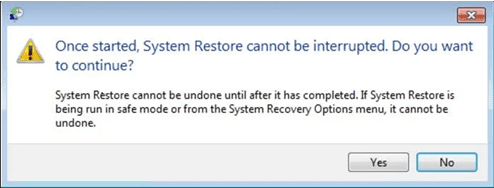
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove TRU8 ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of TRU8 ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
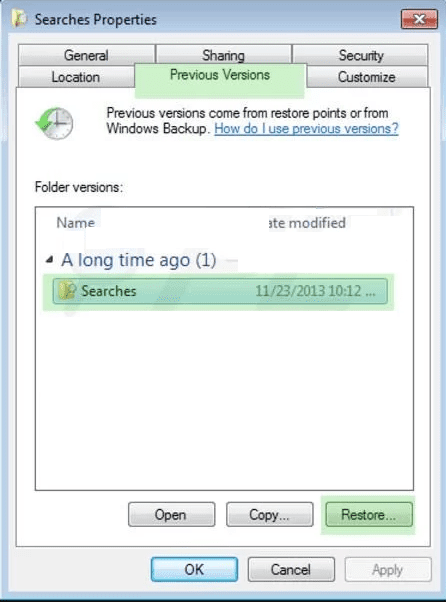
How to Restore Individual Encrypted File:
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
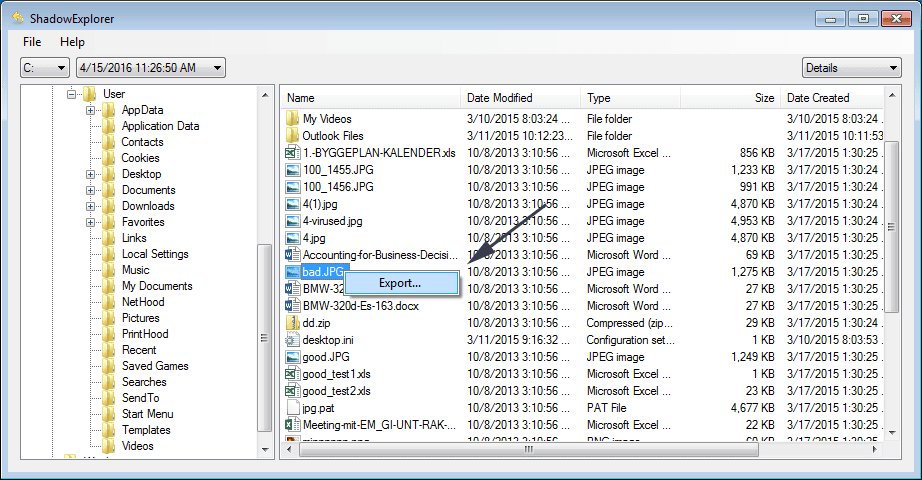
In order to access the files encrypted by TRU8 ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like TRU8 ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
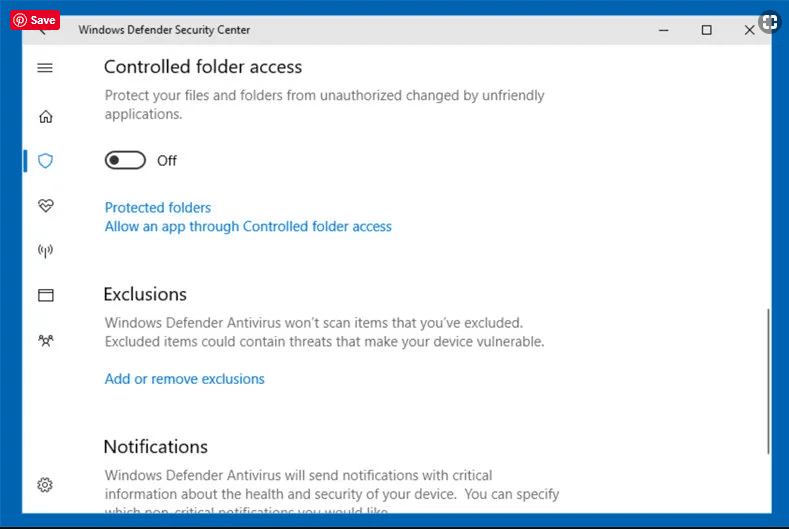
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by TRU8 ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with TRU8 ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove TRU8 ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
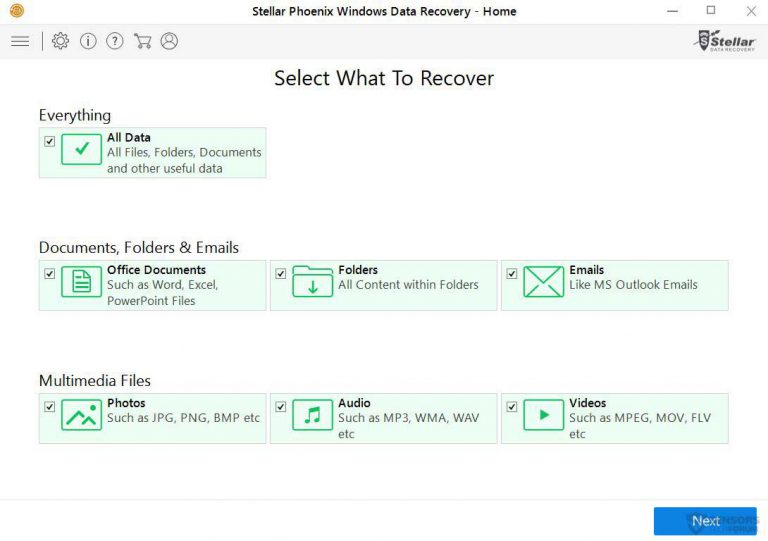
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
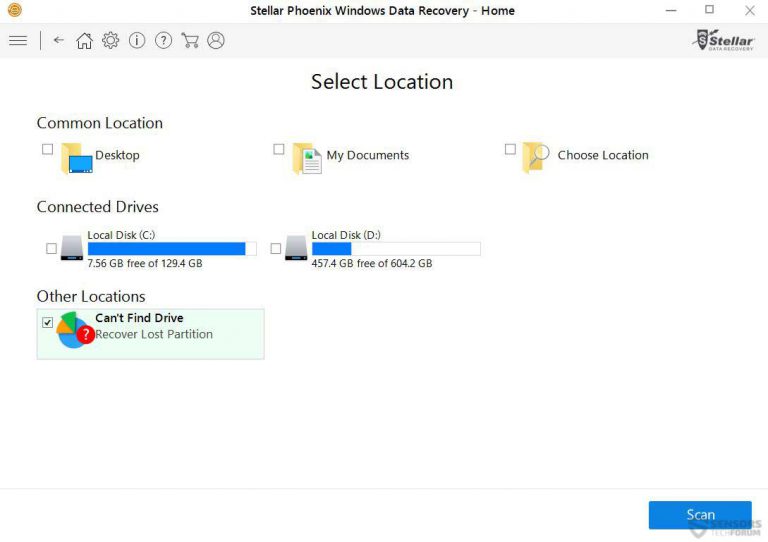
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
TRU8 ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.