How to Remove Trojan:Win32/Smokeloader.RA!MTB from PC
If you want to remove Trojan:Win32/Smokeloader.RA!MTB, it can be a difficult process for you if you are an inexperienced user. To get rid of this malware completely, you must uninstall all related items from your Control Panel, Registry, and system files. If you lack technical skills, the easiest way to remove Trojan:Win32/Smokeloader.RA!MTB is to use a reputable anti-malware tool that can scan your system and eradicate the threat automatically. Additionally, you should ensure that your operating system and all software are up-to-date, avoid opening suspicious emails or downloading files from unknown sources.
Special Offer (For Windows)
Trojan:Win32/Smokeloader.RA!MTB can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Trojan:Win32/Smokeloader.RA!MTB has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Simple Steps To Eliminate Malicious Application
Trojan:Win32/Smokeloader.RA!MTB is a nasty type of software that can sneak into your computer without you even knowing it. The problem with these sneaky programs, called Trojan Horses, is that they often hide so well that you might not realize your PC has been infected. It could be weeks or even months before you discover there’s a dangerous program like Trojan:Win32/Smokeloader.RA!MTB inside your work-station.
The reason you don’t notice it is that Trojan Horse infections don’t always show obvious signs. However, there are some clues that might hint at a problem. Your device might start acting strangely, like running slower, freezing, or showing error messages. You could also see random pop-up windows on your screen from time to time. These things could be indicators that something is wrong.
If you suspect that your computer has been attacked by Trojan:Win32/Smokeloader.RA!MTB or a similar threat, it’s essential to get rid of it as soon as possible. Don’t hesitate – remove the malware to protect your device and your personal information. You can use antivirus software to help you with this. Also, it’s a good idea to be cautious when clicking on suspicious links or downloading files from unknown sources to avoid getting infected in the first place.
Threat Summary |
| Name: Trojan:Win32/Smokeloader.RA!MTB |
| Category: Trojan |
|
Characteristics: Threat actors behind this infection can employ it for several hateful purposes |
| Threat level: High |
|
Symptoms: Frequent system crashes and freezes, slow performance of the infected PC, error messages, etc. |
| Distribution: Fake email attachments, deceptive ads, insecure sites |
Trojan:Win32/Smokeloader.RA!MTB: Depth Analysis
Trojans like Trojan:Win32/Smokeloader.RA!MTB can be made use of for a variety of hateful activities. It’s a quite new malware, so we cannot yet inform you precisely what this virus is going to do inside your computer. However, there are so many things related to the infection that you need to beware of. It can be used to steal important information kept inside the device and also extract money from the victims using different tactics. It can allow cyber crooks remotely gain access to the compromised PCs who can then do all the criminals tasks themselves.
Furthermore, Trojan:Win32/Smokeloader.RA!MTB can spy on you and record your activities through camera, microphone and via other ways. It can log your keystrokes and collect all the data you type through your keyboard. Moreover, it can make your device as a part of botnet and attack other computer machines through the network. Threat actors can employ this parasite to mine cryptocurrencies as well. This is the process that requires a lot of system resources to be consumed. As a result, regular crashes and freezes as well as overall system slowdowns issues will be likely. To avoid this occurrence, remove Trojan:Win32/Smokeloader.RA!MTB from the device as quickly as possible.
What are the harmful effects of Trojan:Win32/Smokeloader.RA!MTB infection?
Trojan horses like Trojan:Win32/Smokeloader.RA!MTB are malicious programs that appear to be harmless or useful software but contain hidden malicious code. Once installed on a computer or device, Trojans can cause a range of harmful effects, including stealing sensitive information, controlling the system, and spreading malware to other devices. Some harmful abilities of Trojans are as follows:
- Stealing Sensitive Information: One of the primary objectives of Trojans like Trojan:Win32/Smokeloader.RA!MTB is to steal sensitive data, such as usernames, passwords, credit card numbers, and other personal information. Once the malware is installed on a PC, it can access and capture the user’s keystrokes, take screenshots, and even record audio and video. This info can then be used for identity theft, financial fraud, and other hateful activities.
- Controlling Devices: Trojan:Win32/Smokeloader.RA!MTB can also give hackers remote control of a device, enabling them to perform a range of malicious activities. For example, attackers can employ it to access and modify files, delete or encrypt data, and even take over a device’s camera and microphone. In some cases, internet criminals may use Trojans to create network of compromised systems, known as botnet, which can be used for further attacks.
- Spreading Malware: Threat actors can also use Trojan:Win32/Smokeloader.RA!MTB to spread malware to other devices, either by sending infected files or by exploiting vulnerabilities in software or operating systems. This can lead to a rapid spread of malware and a significant increase in the number of compromised devices.
- Encrypting Data: Some Trojans are designed to encrypt data on a computer and demand a ransom payment in exchange for the decryption key. This type of attack is known as ransomware and can be devastating for organizations and individuals that rely on their data to operate.
- Destructive Attacks: Trojans can also be used to launch destructive attacks, such as deleting or corrupting files, disrupting network activity, or even causing physical damage to systems. These attacks can be used to sabotage businesses, governments, and critical infrastructure, causing significant financial and reputational damage.
In short, Trojan:Win32/Smokeloader.RA!MTB is a significant threat to the security and privacy of both individuals and organizations. It can steal sensitive information, control devices, spread malware, encrypt data, and launch destructive attacks.
Trojan:Win32/Smokeloader.RA!MTB can spread ransomware infections:
Trojans are a common method used by cyber criminals to spread ransomware, a type of malware that encrypts the victim’s files and demands payment in exchange for the decryption key. Trojan:Win32/Smokeloader.RA!MTB is typically disguised as a legitimate program or file and is delivered to the targeted systems through email attachments, malicious links, or infected software downloads.
Once the Trojan is installed on the computer, it silently downloads and installs the ransomware. The ransomware then begins encrypting the victim’s files, making them inaccessible to the user. The attacker then demands payment, typically in the form of cryptocurrency, in exchange for the decryption key that can unlock the files. The consequences of a ransomware attack can be severe, both for individuals and organizations. Here are some of the potential consequences of a ransomware attack spread by Trojans like Trojan:Win32/Smokeloader.RA!MTB:
- Loss of Data: Ransomware can cause the victim to lose access to important files, such as personal photos, financial records, and business documents. If the victim does not pay the ransom, the files may be permanently lost.
- Financial Loss: Ransomware attacks can be costly, both in terms of the ransom demanded and the cost of recovering lost data or repairing damage to the device or network.
- Reputation Damage: Organizations that suffer a ransomware attack may suffer damage to their reputation, particularly if sensitive data is compromised.
- Legal Consequences: If the victim’s data contains personal or sensitive information, the attacker may be in violation of data protection laws, leading to legal consequences.
- Disruption of Business: Ransomware attacks can disrupt business operations, leading to lost revenue, missed deadlines, and other negative consequences.
To sum up, Trojans are a common method used by cyber criminals to spread ransomware. The consequences of a ransomware attack can be severe.
What could be the consequences of Trojan:Win32/Smokeloader.RA!MTB’s ability of stealing data?
The consequences of Trojan:Win32/Smokeloader.RA!MTB’s ability to steal information can be severe and long-lasting. One of the primary consequences is identity theft. Threat actors can make use of the stolen data to create fake identities or take over existing ones. This can lead to financial losses, damage to credit scores, and legal problems for the victim. Additionally, victims of identity theft may spend months or even years trying to resolve the damage caused by the theft of their personal information.
Another effect of Trojan:Win32/Smokeloader.RA!MTB’s ability to steal data is financial fraud. Internet crooks can use the stolen data to make unauthorized purchases or withdrawal from the victim’s bank account. This can result in financial losses for the affected person, as well as damage to their credit score. In some cases, victims may not be able to recover the stolen funds, leading to long-term financial problems.
A Trojan’s ability to steal data can also lead to the loss of sensitive business information. Cyber criminals can use the stolen data to gain access to company networks and steal valuable business data, such as intellectual property or trade secrets. This can lead to significant financial losses and damage to the company’s reputation. In some cases, the loss of sensitive business information can lead to the failure of the company.
Finally, a Trojan’s ability to steal data can lead to the spread of malware. Cybercriminals can use the stolen data to send targeted phishing emails or malware-laden attachments to the victim’s contacts. This can lead to the spread of malware to other devices, creating a domino effect of security breaches and data thefts.
In brief, the consequences of Trojan:Win32/Smokeloader.RA!MTB’s ability to steal data are severe and can have long-lasting effects on the victim’s life. It is important for individuals and companies to take proactive steps to protect their devices and data from these types of threats, including using antivirus software, avoiding suspicious websites and downloads, and regularly updating their security software.
How did my PC get infected with this virus?
There are several ways through which such malware threat may find its way into your computer. Some of the common methods include:
- Spam emails: Suspicious links in spam emails can lead to the installation of viruses.
- Online free hosting resources: Free hosting resources available on the internet can also be a source of malware infection.
- Hidden installation: Viruses can be installed secretly along with other applications, especially freeware or shareware utilities.
- P2P resources: If you employ illegal peer-to-peer (P2P) resources to download pirated software, the risk of virus infection increases.
- Trojans: Trojans can be used to spread Trojan:Win32/Smokeloader.RA!MTB by disguising the threat as a legitimate file or program.
Trojan often spreads through spam emails that contain malicious attachments or links. Cybercriminals create convincing-looking emails that seem legitimate, such as a message from a bank, shipping company, or government agency. These emails entice recipients to download and open the attachment or click on the link. Once clicked, the malicious payload downloads and executes on the user’s computer, infecting it with the malware. In some cases, the payload may be embedded within the email itself, allowing it to execute as soon as the email is opened.
Instances have been reported where the Trojan:Win32/Smokeloader.RA!MTB was camouflaged as a legitimate tool, masquerading itself as messages that demand the launch of unwanted software or browser updates. Some online scams employ a technique to trick you into installing the virus manually, by making you an active participant in the process. Typically, these fake alerts will not indicate that you are installing ransomware. Instead, the installation will be disguised as an update for a legitimate program like Adobe Flash Player or some other suspicious program. The true nature of the installation will be concealed under these bogus alerts.
Using cracked apps and P2P resources for downloading pirated software can pose a significant threat to your device’s security, and it may lead to the injection of severe malware such as the Trojan:Win32/Smokeloader.RA!MTB.
Trojans are a popular attack vector for such infections. Hackers use Trojans to spread ransomware, RATs, cryptominers, data stealers by disguising the malware as a legitimate file or program. Once a victim downloads and executes the Trojan, the malware payload is unleashed on their system. Trojans can be spread through various channels, including malicious websites, social media platforms, and peer-to-peer networks. Cybercriminals often use social engineering tactics to trick users into downloading and executing Trojans.
Special Offer (For Windows)
Trojan:Win32/Smokeloader.RA!MTB can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Trojan:Win32/Smokeloader.RA!MTB has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
Google Chrome (PC)
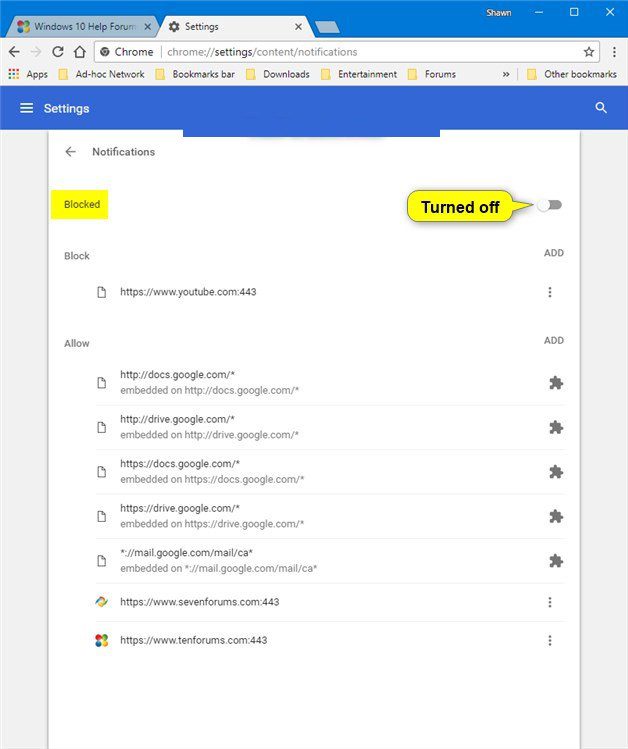
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
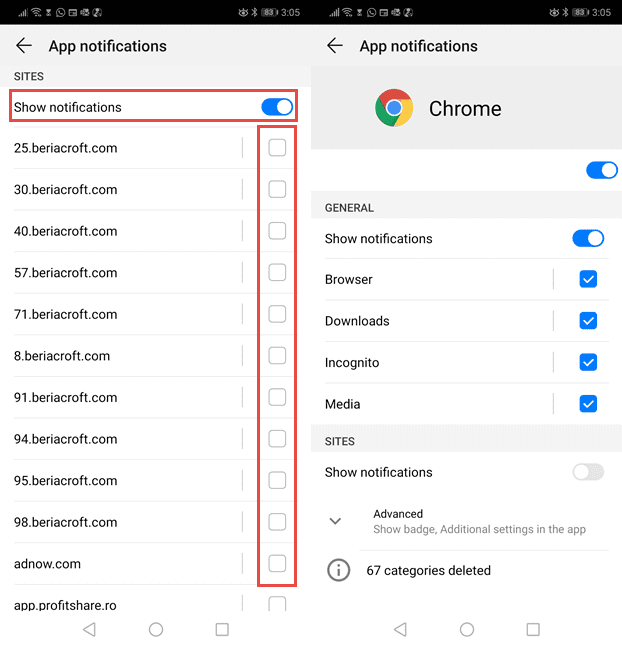
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
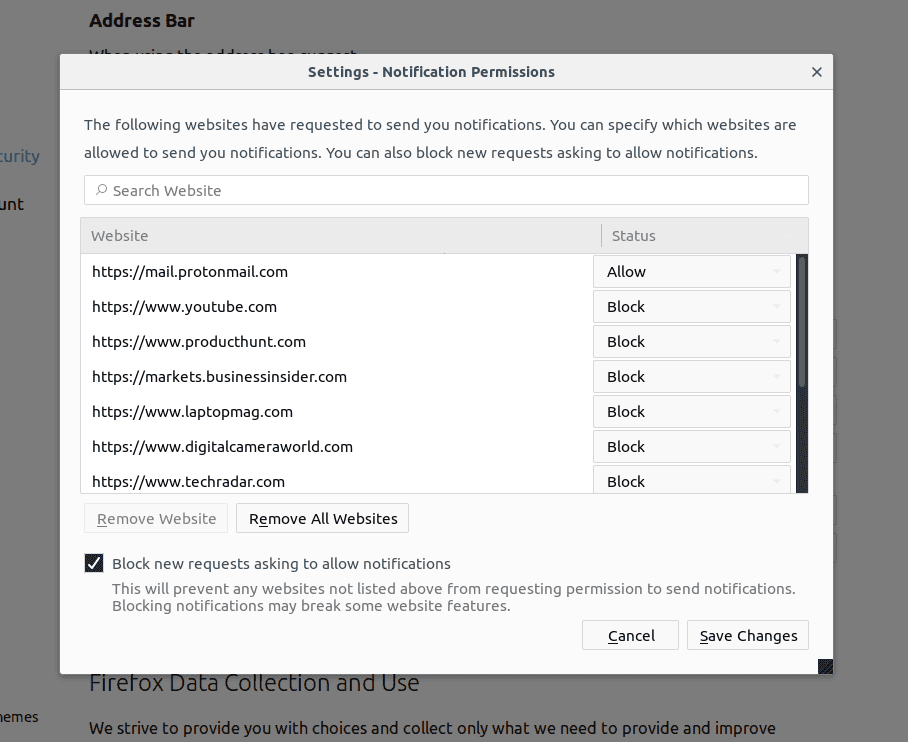
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
Internet Explorer
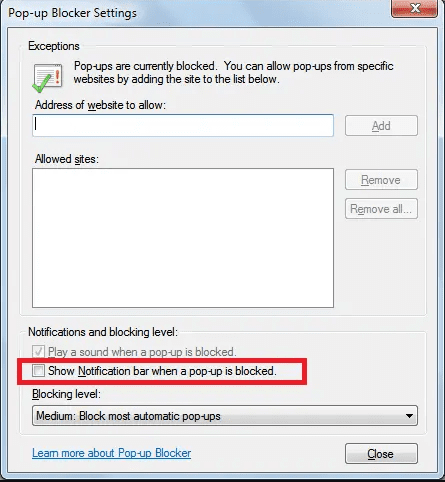
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
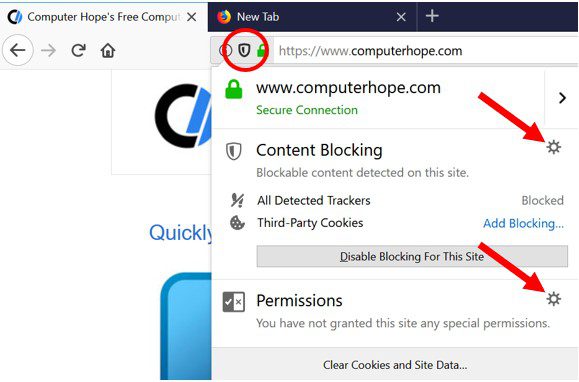
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
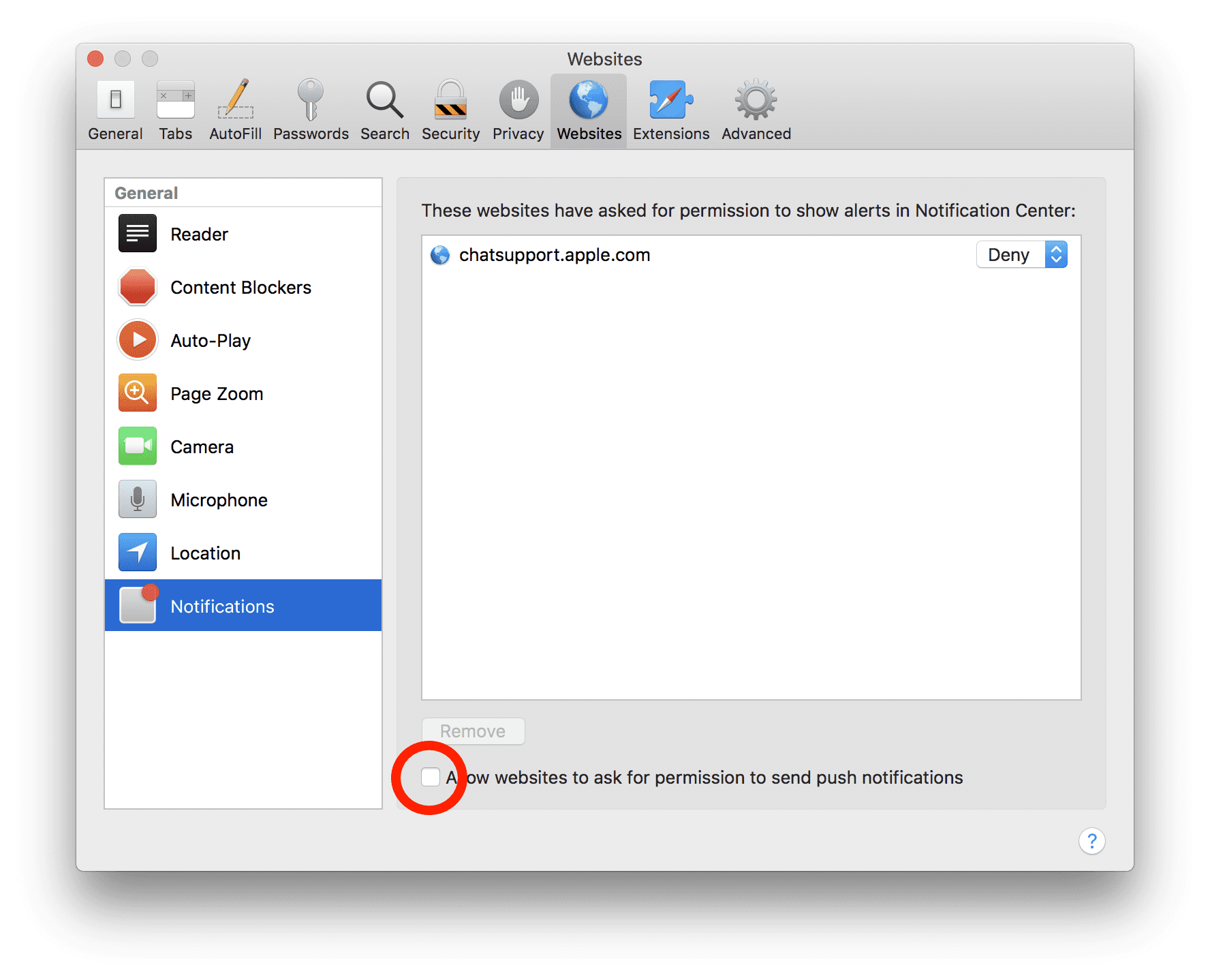
Manual Steps to Remove Trojan:Win32/Smokeloader.RA!MTB:
Remove the related items of Trojan:Win32/Smokeloader.RA!MTB using Control-Panel
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
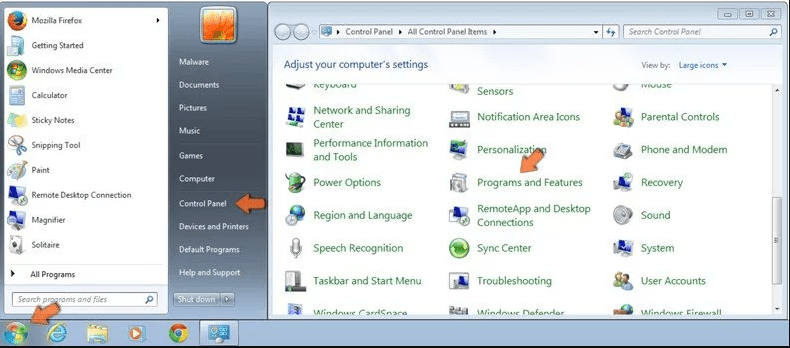
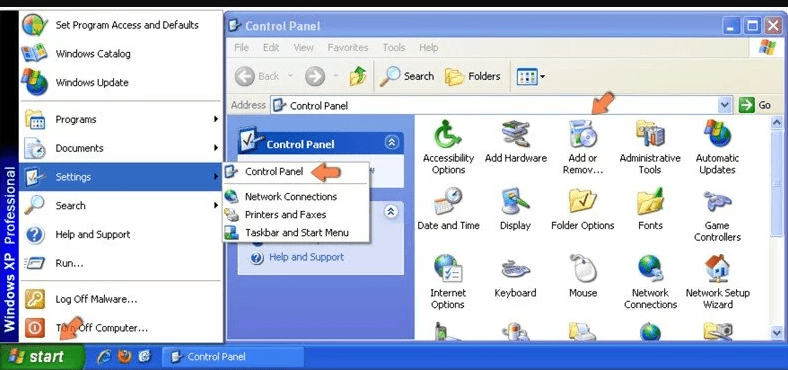
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
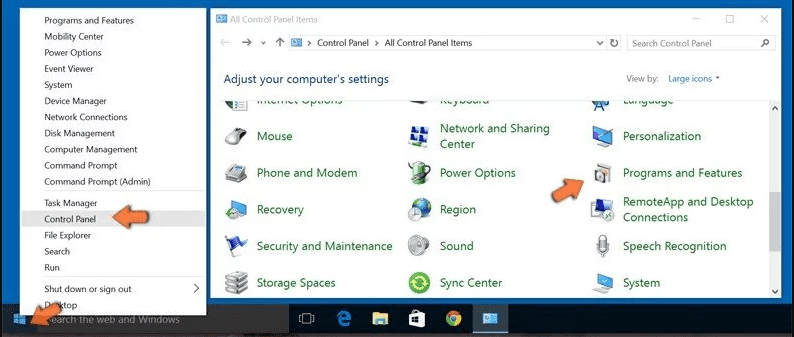
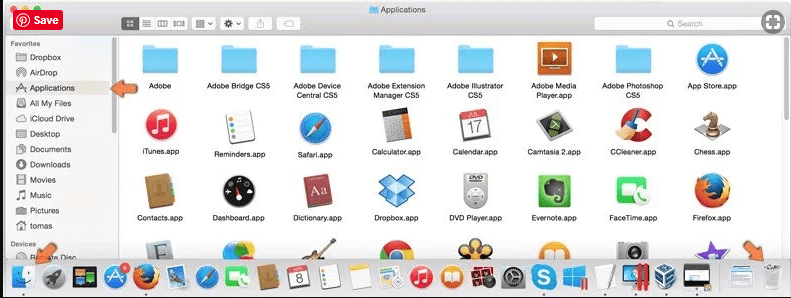
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
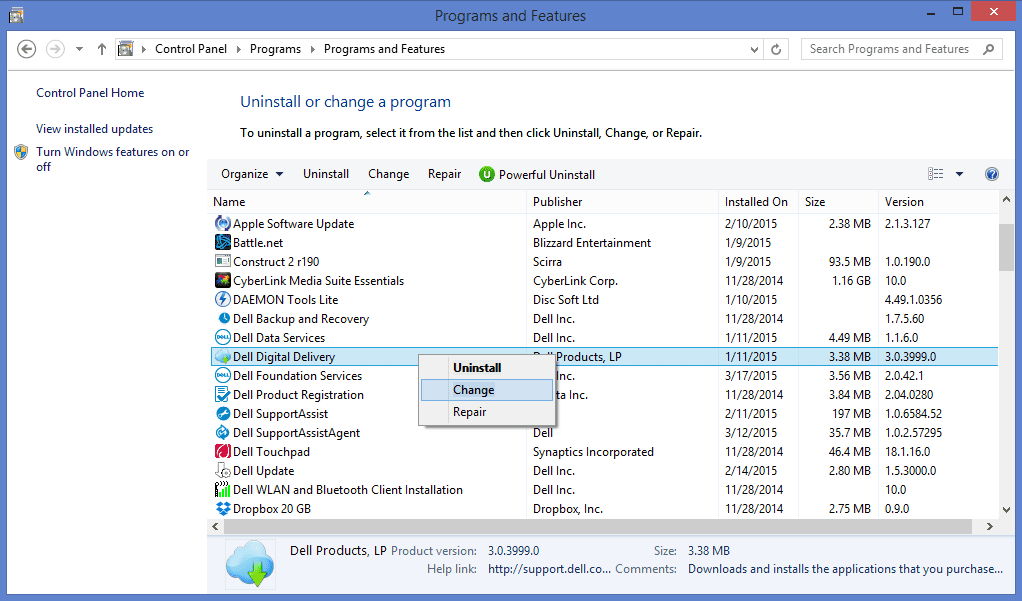
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Trojan:Win32/Smokeloader.RA!MTB issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Trojan:Win32/Smokeloader.RA!MTB can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Trojan:Win32/Smokeloader.RA!MTB has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Trojan:Win32/Smokeloader.RA!MTB) from Internet Browsers
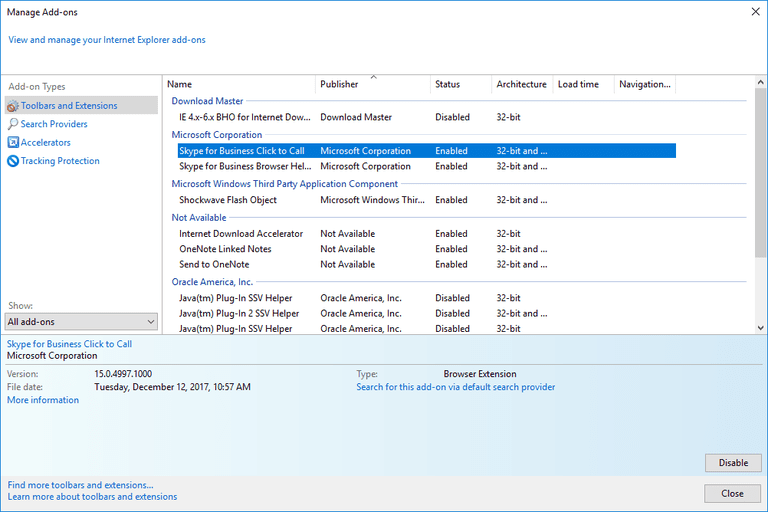
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
Additional Option
If you still face issues related to Trojan:Win32/Smokeloader.RA!MTB removal, you can reset the Internet Explorer to its default setting.
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
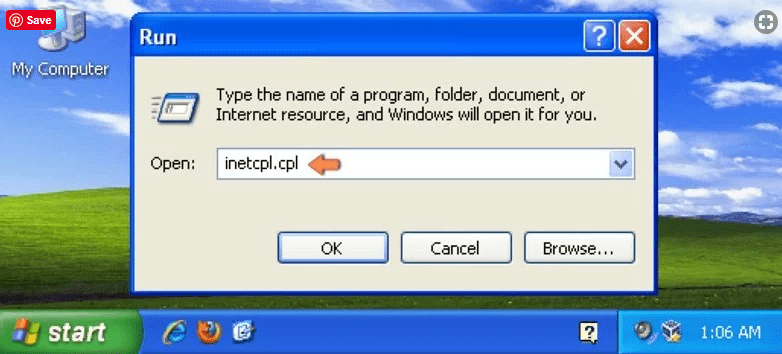
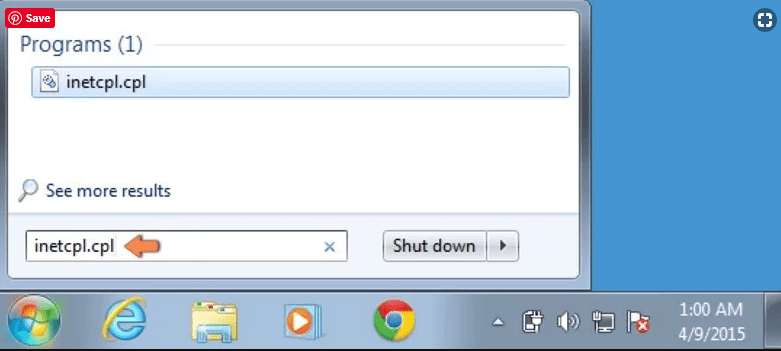
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
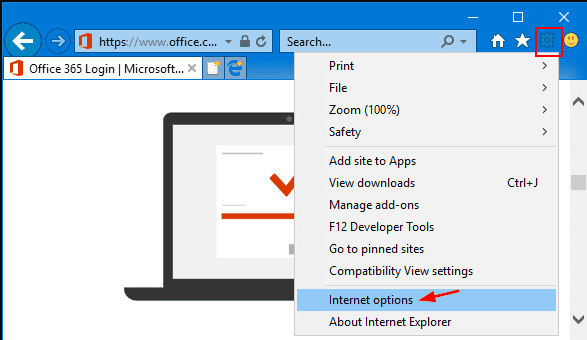
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
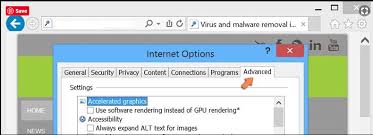
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
You have to press on the “Reset” button again to confirm that you really want to reset the IE
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
Optional Method
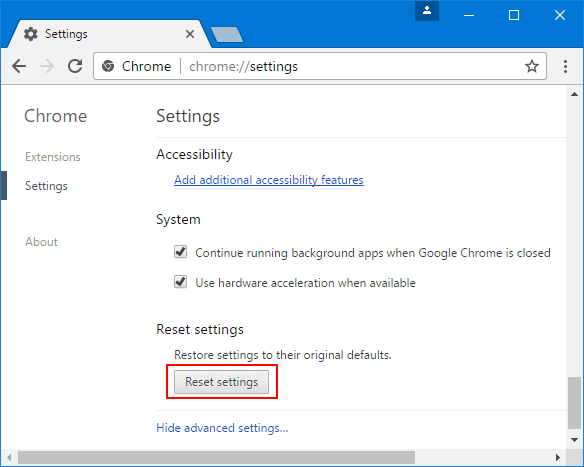
If the problems related to Trojan:Win32/Smokeloader.RA!MTB still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
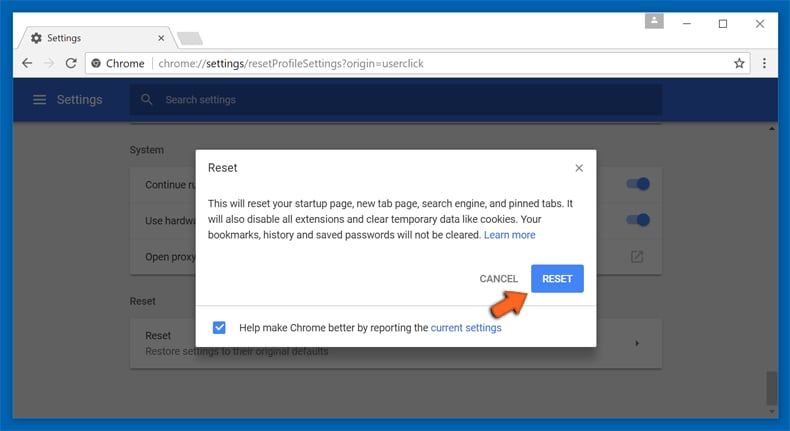
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove Trojan:Win32/Smokeloader.RA!MTB plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Trojan:Win32/Smokeloader.RA!MTB removal then you have the option to rese the settings of Mozilla Firefox.
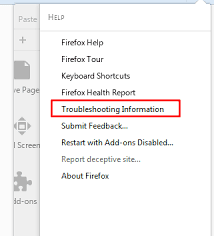
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
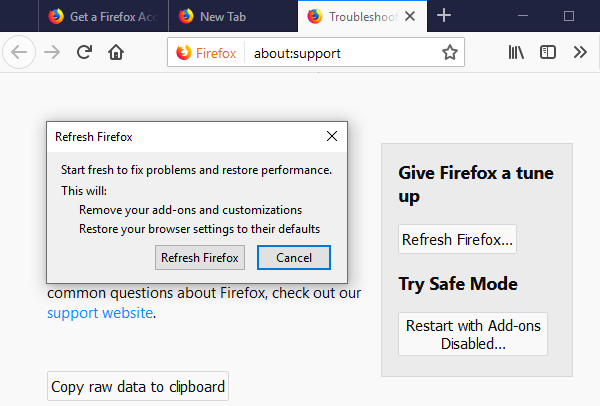
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
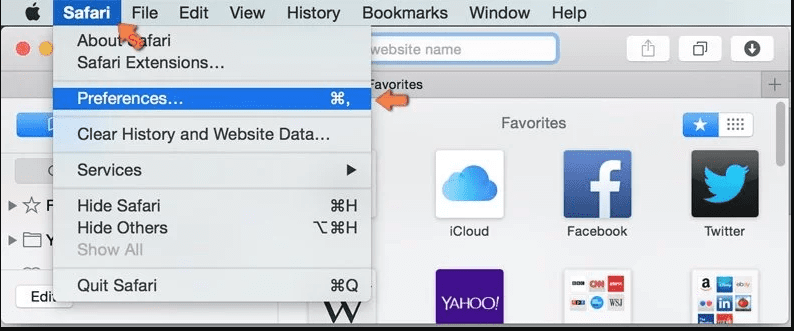
Open the Safari and go to its “Menu” and select “Preferences”.
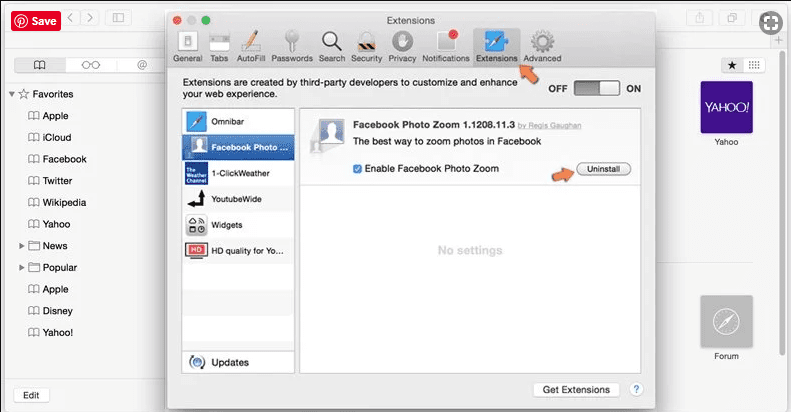
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
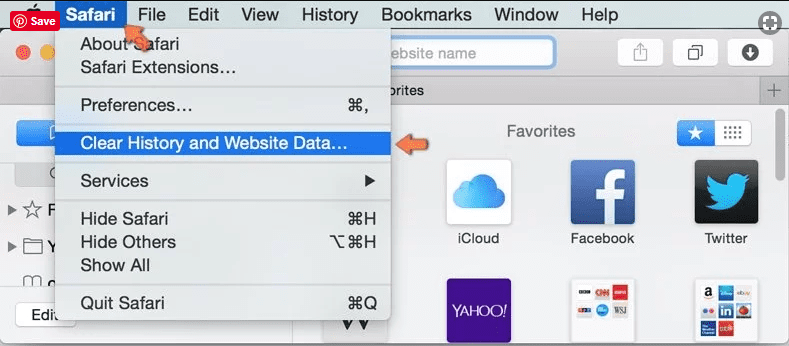
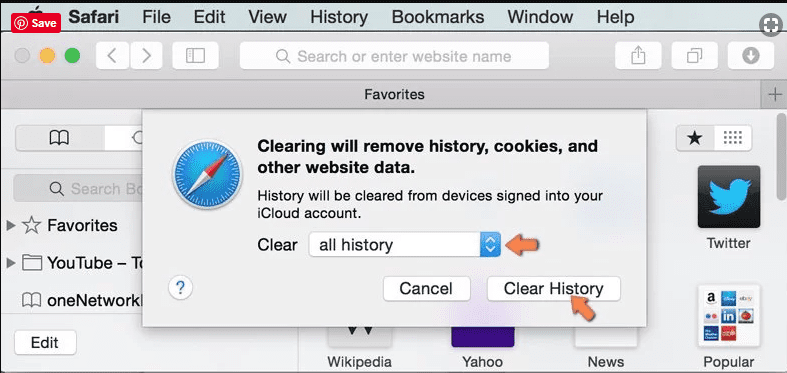
In the newly opened window, select “All History” and then press on “Clear History” option.
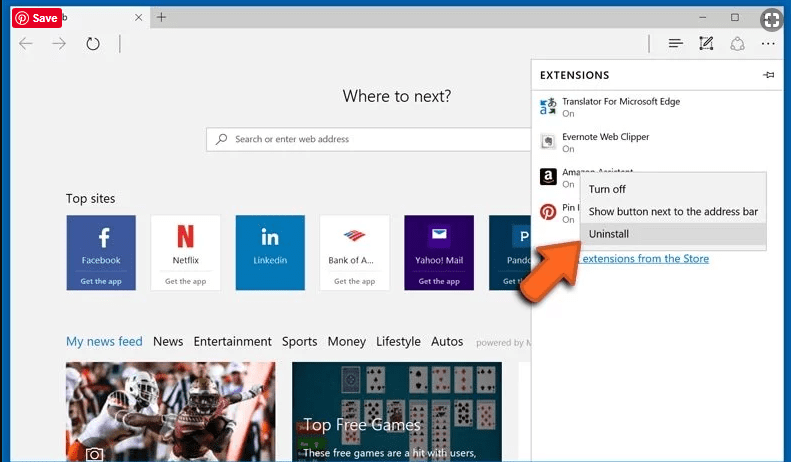
Delete Trojan:Win32/Smokeloader.RA!MTB (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
Optional Method
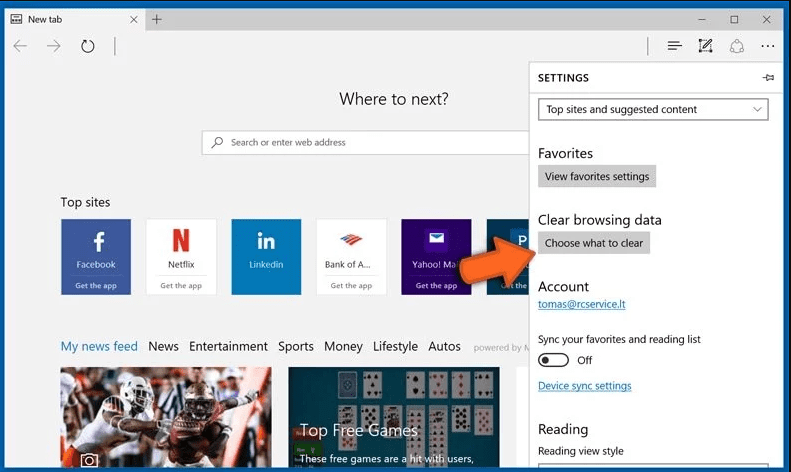
Open the browser (Microsoft Edge) and select “Settings”
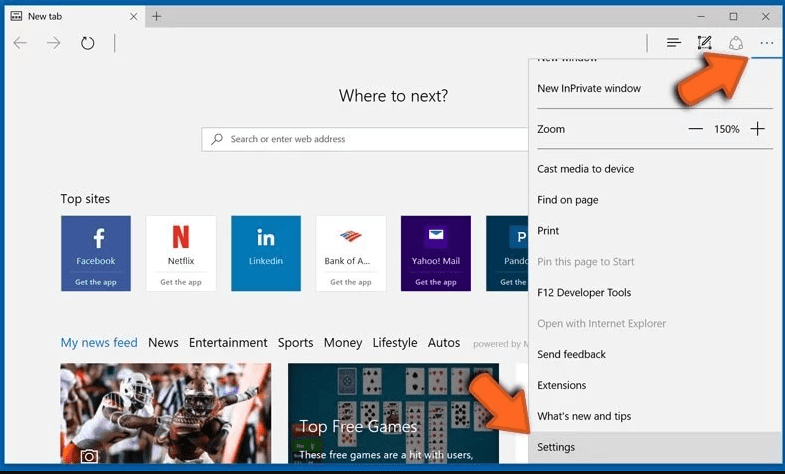
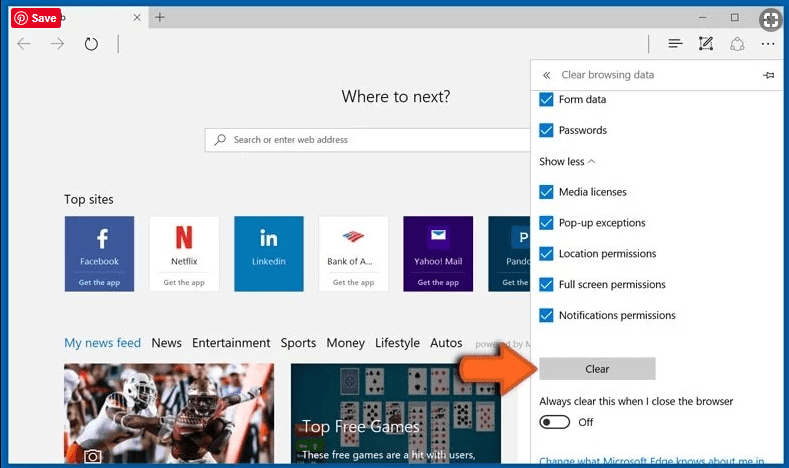
Next steps is to click on “Choose what to clear” button
Click on “show more” and then select everything and then press on “Clear” button.
How to Prevent Trojan:Win32/Smokeloader.RA!MTB Attack?
Although no security measures can guarantee complete protection against malware, there are certain precautions you can take to prevent dreadful cyber threats from infecting your device. Be vigilant while installing free software, and read through the installer’s additional offers carefully.
Users should be cautious when opening emails from unknown senders or any messages that seem suspicious or out of the ordinary. If the sender or address is unfamiliar, or the content is unrelated to anything you are expecting, it is best not to open the message. It is highly unlikely that you could win a prize in a contest you didn’t enter, so be wary of any emails claiming that you won something. If the email subject appears to be related to something you are anticipating, it is important to thoroughly examine all aspects of the message. Scammers often make mistakes, so carefully scrutinizing the content of the email could help you identify any fraudulent activity. Remember, it is always better to err on the side of caution and avoid opening emails or letters that appear suspicious.
It is also crucial to keep all software and security programs up-to-date to prevent vulnerabilities that malware can exploit. Using cracked or unknown programs is a significant risk for Trojan-based attacks. Cybercriminals often distribute Trojans disguised as legitimate software, such as patches or license checks. However, it is challenging to differentiate between trustworthy software and malicious Trojans since some Trojans may even have the functionality that users seek.
To mitigate this risk, it is crucial to avoid using untrusted programs altogether and only download software from reputable sources. Before downloading any program, users should research it thoroughly and read reviews from trusted sources. It is also recommended to consult anti-malware message boards to gather additional information on any software that may raise suspicion. Ultimately, the best defense against Trojan attacks is to exercise caution and avoid downloading software from untrusted sources.
Conclusion
In most cases, the PUPs and adware gets inside the marked PC through unsafe freeware downloads. It is advised that you should only choose developers website only while downloading any kind of free applications. Choose custom or advanced installation process so that you can trace the additional PUPs listed for installation along with the main program.
Special Offer (For Windows)
Trojan:Win32/Smokeloader.RA!MTB can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Trojan:Win32/Smokeloader.RA!MTB has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.



