How to Remove ResearchSecure Unwanted Application
Intro to ResearchSecure
ResearchSecure is an app with extensions for Chrome and Edge that tracks user activity anonymously, claiming to study online trends and behaviors. However, its data collection practices may raise privacy concerns. It has been promoted using suspicious methods, leading to its classification as a Potentially Unwanted Application (PUA). This means it may not be harmful but can still cause issues or discomfort for users.
Special Offer (For Windows)
Malware/Spyware/Virus can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter 5 antimalware scanner to check if the program can help you getting rid of this virus.
Special Offer (For Macintosh) If you are a Mac user and Malware/Spyware/Virus has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
What is ResearchSecure?
ResearchSecure is a sketchy application that you might stumble upon while wandering through websites that offer illegal software cracks. Now, the tricky part is, we aren’t really sure what this app does because its purpose remains kind of mysterious. The catch here is that when you grab ResearchSecure, it often brings along a bunch of other dubious apps as well.
Why the caution? Well, ResearchSecure is like a shady character from an unknown source, and that’s never good news. It could potentially be carrying malware, spyware, or other not-so-friendly things. Trusting this app might open the door to unauthorized access to your private info, mess with your device’s integrity, and lead to some serious problems.
But wait, there’s more to the mystery. ResearchSecure might not be playing fair – it could be up to some tricky business, like collecting your data without asking and throwing intrusive ads your way. To stay safe, it’s crucial to be picky about where you get your apps. Stick to the reputable sources, do your homework before hitting that download button, and keep your digital life secure.
Now, here’s the twist – ResearchSecure doesn’t come alone. It brings along some suspicious friends like adware and browser hijackers. Adware loves to shower you with annoying ads, making your browsing experience a headache. Meanwhile, browser hijackers are like the unwanted decorators of your web browser, changing settings without your say-so and sending you to places you didn’t plan on visiting.
Having these dubious elements around with ResearchSecure could seriously mess up your user experience. So, steer clear of these shady apps or, if you’ve got them, kick them out pronto to keep your digital life drama-free.
How does ResearchSecure impact a device?
The cyber criminals inject this malicious program into the browsers for several reasons. In many cases, the hackers proliferate malware into browsers to capture the user’s sensitive information. The information of interest of may include user IDs, passwords, full names, addresses, social security numbers and finance related data. After collecting this information the cyber criminals use the information to access accounts that users log in to on the internet. Sometimes the crooks also misuse the victims’ financial data for unauthorized purchase.
While some inject this malicious program into your PC just to track these sites the users visit and how long they spend on those web pages. Afterwards they either use the information themselves to target their ad campaigns or sell it to the others.
It must be noted that such type of malware should not be entertained in any case. Once these files are inserted into browsers it takes up the storage space and slow down your machine. In order to summarize, the presence of ResearchSecure on device may result in system infections, severe privacy issues, financial losses and even identity theft.
Threat Summary |
| Name: ResearchSecure |
| Category: Browser hijacker, Redirect Virus |
|
Features: Modifies critical settings in browsers like homepage, new tab, search engine, DNS, and even more. Apart of these, it can also be responsible to show irritating advert pop ups or banners to promote illicit commercials. |
| Danger Level: Medium |
|
Symptoms: The unwanted application can cause several adverse effects, such as displaying intrusive pop-up ads and slowing down internet browsing. The threat can manipulate the settings of an internet browser. This manipulation forces users to visit the hijacker’s website and conduct internet searches using their search engine. |
|
Distribution: Browser hijackers are often distributed through open or unsafe online channels, social engineering tricks, and even more. |
|
Removal: To remove the threat, scan your system with powerful Combo Cleaner anti-malware software |
How does a system get infected by ResearchSecure?
There are a number of factors that are responsible for infecting your PC from browser hijackers. Following are some of the distribution strategies:
Malicious Websites: Such Malware also spread through malicious websites. These rogue sites are designed to manipulate the users into downloading and installing software. People land on such sites often by clicking on suspicious links in spam emails, a social post or a search engine result.
Bundled Software: Browser Hijackers and Adware often gets bundled with legitimate software that users download from internet. This could be a free utility or game that is made available for download from a website. When the users download or install a program, the bundled software also gets installed in your PC out of your knowledge. This bundled software may include browser hijacker or adware.
Social Engineering: Social engineering is the most common trick to manipulate the users for downloading malware into the user’s PC. The crooks create a fake advertisement or pop-up message that claims the users need to update their software. These pop-up messages may contain convincing messages such as “Your PC is infected with Virus” click here to remove the virus. Once you click on these links the malware gets installed into your PC.
Should I Remove ResearchSecure?
Browser hijackers are not considered tough contenders as Trojan and ransomware but it is imperative to know that it has potential to inject more hazardous malware to your PC. Once your PC is infected with hijacking app you cannot surf the net properly. These malicious programs not only consume a large storage space but also keep running in the background continuously as a result users face high CPU usage. In order to stay longer in your PC it may also disable your Antivirus Software for preventing its detection. Browser hijackers should not be entertained for a long time in any cases as it may lead to serious system infections, sever data loss, financial losses and identity theft as well. So if you suspect if you have unintentionally installed this malware into your PC remove it immediately.
What harms ResearchSecure can cause?
ResearchSecure is a type of malicious software that can take control of your web browser and modify its settings without your consent. Such apps are typically designed to redirect your web traffic to other sites, display unwanted advertisements, and collect your personal information. Browser hijackers can be very harmful, and can cause a wide range of problems for your computer and your privacy. Below, we will discuss some of the harms that ResearchSecure can cause.
- Modify Your Browser Settings: It can modify your browser settings, such as your homepage, default search engine, and new tab page. This can be very frustrating, as it can take a long time to reset these settings back to their original state.
- Display Annoying Ads: This hijacking app often displays unwanted ads, pop-ups, and banners on your screen. These ads can be very annoying, and can even lead to more harmful content if you click on them. In some cases, the ads may even be used to trick you into downloading more malware.
- Redirect Your Web Traffic: It can redirect your web traffic to other sites, even if you didn’t intend to visit those sites. This can be very dangerous, as the sites you are redirected to may contain harmful content, such as malware, phishing scams, or other types of scams.
- Slow Down Your Computer: One of the most obvious harms of hijackers or adware like ResearchSecure is that they can slow down your computer. This is because they are constantly running in the background, using up valuable system resources. This can cause your device to become sluggish, unresponsive, and even crash.
- Cause Browser Crashes: ResearchSecure can also cause your browser to crash or freeze. This can be very frustrating, as it can cause you to lose any work you were doing, or even cause you to lose important data if you haven’t saved your work.
- Decrease Your Online Privacy: This undesired software piece can decrease your online privacy by tracking your browsing habits, collecting your personal information, and displaying unwanted ads. This can be very harmful, as it can expose you to identity theft, fraud, and other types of cybercrime.
In short, ResearchSecure can cause a wide range of harms to your device and your privacy. Therefore, it is important to take steps to protect your computer from this hijacking application, such as using antivirus software, keeping your browser and operating system up to date.
Commonly asked questions about ResearchSecure
Is ResearchSecure dangerous virus?
ResearchSecure may inject other malware to the compromised PC. While many don’t consider it as a destructive virus but such malware can make your PC more venerable to other cyber attacks. These browser based infections are often designated to collect user’s personal data. This data can be further used by the cyber criminals for identity theft, fraud and other malicious activities.
What are the symptoms when your PC is infected with ResearchSecure?
It’s quite easy to track if your system is infected with browser hijacker. Here we have listed some signs that indicate your system is infected by an adware or browser hijacker:
- Every time you attempt to surf the web, it may redirect you to various scam pages which are not safe at all.
- The sites you usually visit will not open properly.
- Unwanted programs get installed on your PC out of your knowledge.
How did ResearchSecure infiltrate my PC?
Browser hijackers are distributed through bundled program installers, dubious and scam websites, freeware and shareware, spam browser notifications and intrusive ads as well.
Should we prefer automatic solution over manual solution for the removal of ResearchSecure?
Yes, we highly recommend you to prefer automatic solution over manual because manual method is quite lengthy and moist importantly it required tech skills. So it’s better to go for a reliable Anti Malware tool to remove this malicious program from your Operating System.
Easy Tips to Secure Your Device

Well in order to prevent your PC from such malware attack you can adopt the following prevention methods.
- Always use a legitimate Antivirus Software and keep it up-to-date with the latest virus definitions.
- Keep your browser and your Operating System updated. Updates software can defend against malware attacks.
- Do not click on links in emails or websites unless you are sure that they are legitimate and safe for your PC.
- Be very careful while downloading software from reputable websites such as from official page of the software. Do not rely on freeware, shareware and other unverified sources to install software. While installing software you need to pay heed to the each step of the installation process. During the installation process choose the custom installation option instead of the default or express installation.
- Do not install unnecessary programs on your PC.
- Exercise caution while web surfing.
ResearchSecure Redirection Leads to Unsafe Sites
The redirection chain triggered by ResearchSecure may force the browser to send the user to a variety of different webpages. Nonetheless, it’s pertinent to note that most of the websites it sends people to are malicious and even dangerous and may pose a serious threat to the device and the browser. This undesired software piece may take users to following sites:
Tech Support Scam Sites

Many people are falling victim to tech support scam websites that have become increasingly widespread. These sites often imitate the appearance of legitimate operating system error messages, making it difficult for individuals to discern whether the message is genuine or a scam. As a result, users are easily fooled into giving scammers access to their personal information or paying for unnecessary and expensive services.
Unsafe Dating Website
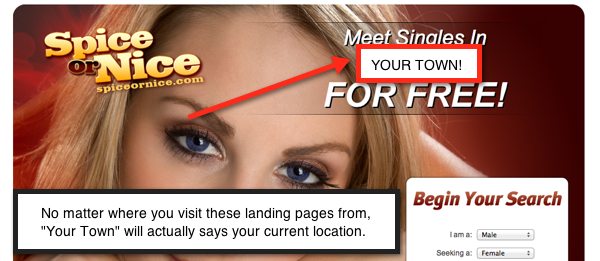
ResearchSecure pop-ups may lead you to dubious dating sites that are entirely controlled by robots. Such websites often display deceptive notifications and pop-ups that mislead users into believing that they have multiple chat requests or messages waiting for them. These false alerts may be designed to look convincing and may even use persuasive language to create a sense of urgency, tricking users into clicking on them. In reality, these notifications are usually a tactic employed by scammers to lure individuals into interacting with their fraudulent websites or downloading malicious software.
Websites Showing Fake Virus Alert:
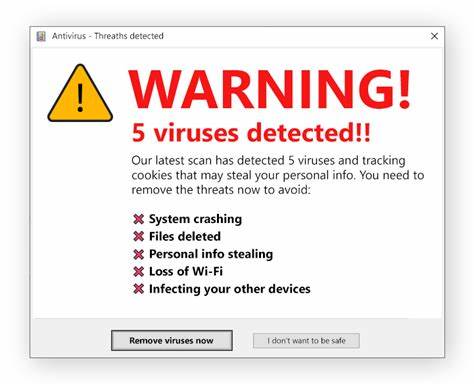
These sites tend to display fake security alerts claiming that users’ PCs are infected with several viruses. They are designed to trick visitors into believing that they are in trouble of having their computers infected and to compel them into taking immediate actions. Scammers behind these deceptions aim to mislead users into downloading and installing malicious software or extracting money from them for useless services.
Drive-by Download Malware Sites
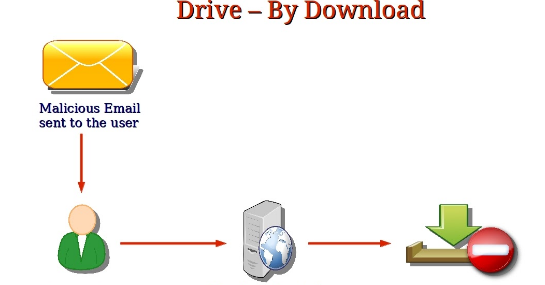
Users may also be taken to drive-by download websites, which is a type of cyberattack in which malware is automatically downloaded to a computer without the user’s knowledge or consent. Drive-by downloads are a serious security threat, as they can result in the installation of viruses, spyware, or other types of malicious software, which can compromise the security and privacy of your computer and personal data.
Fake Giveaway Survey Websites
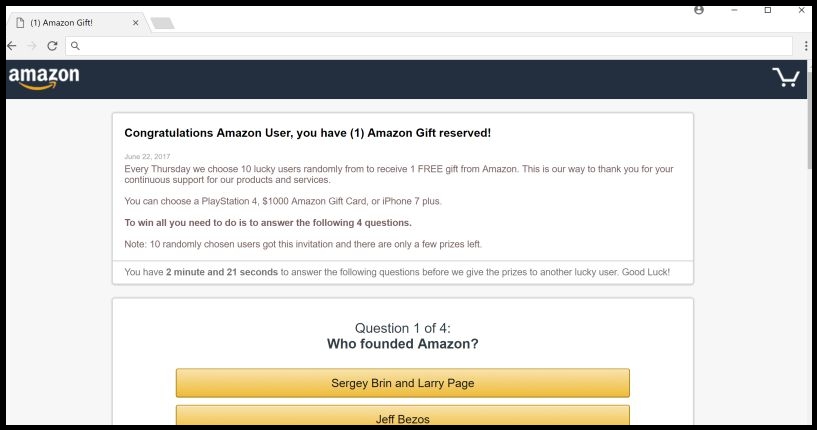
These dubious sites tend to promote bogus surveys aiming to trick users into stealing their personal information such as their credit card details, banking credentials, etc. This sort of information could later be used for various malicious purposes and may lead to a number of unpleasant issues.
Unsafe Pop-Ups Causes Online Scam

Unsafe pop-ups are a common method used by online scammers to deceive unsuspecting internet users. These pop-ups can appear on users’ browser when their system is contaminated with an unwanted application; they visit a website or click on a link, and often try to convince them to take some action, such as downloading a program or providing personal information.
Once users interact with the pop-up, they can be redirected to a fraudulent website that looks legitimate, but is actually designed to steal their sensitive data or money. For example, a ResearchSecure pop-up might claim that users’ device is infected with a virus and prompt them to download software that is actually malware.
Other pop-ups might offer a prize or gift in exchange for the user’s personal information, such as their name, address, and credit card number. Once the scammers have this information, they can employ it to make unauthorized purchases or commit identity theft. This can lead to serious privacy issues, identity fraud, high-risk system infections, and even significant monetary losses.
Special Offer (For Windows)
Malware/Spyware/Virus can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter 5 antimalware scanner to check if the program can help you getting rid of this virus.
Special Offer (For Macintosh) If you are a Mac user and Malware/Spyware/Virus has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
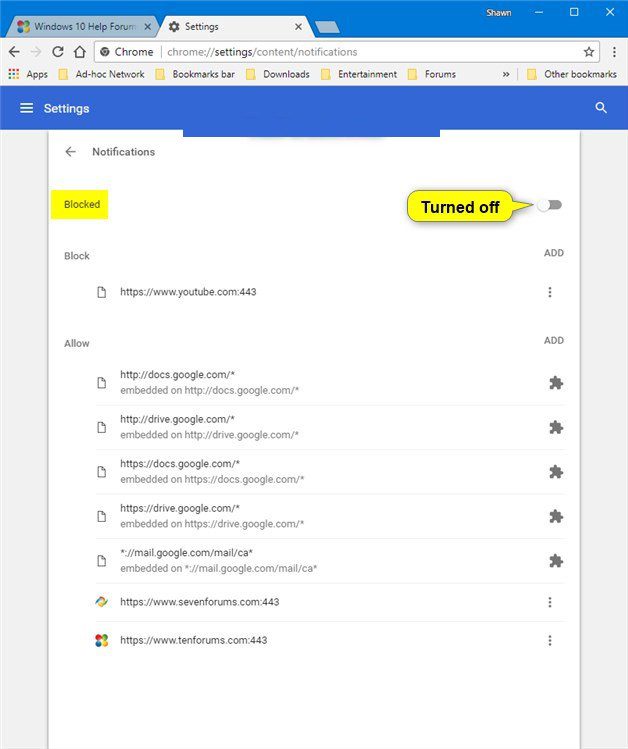
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
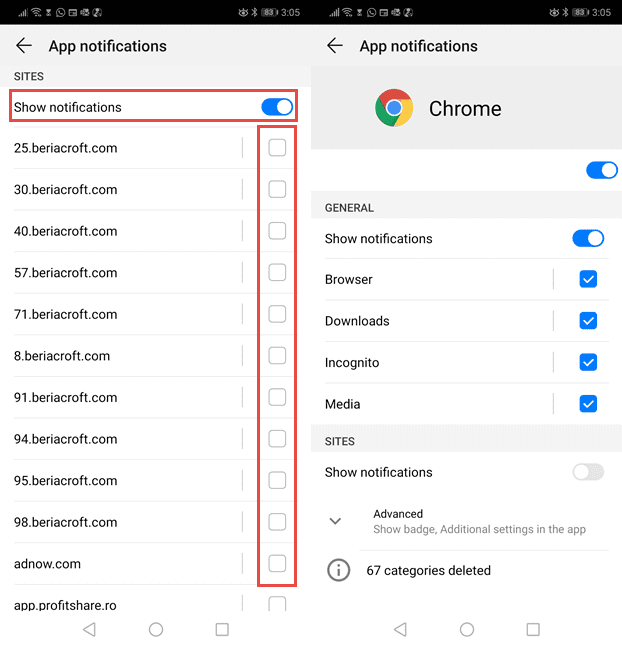
Google Chrome (Android)
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
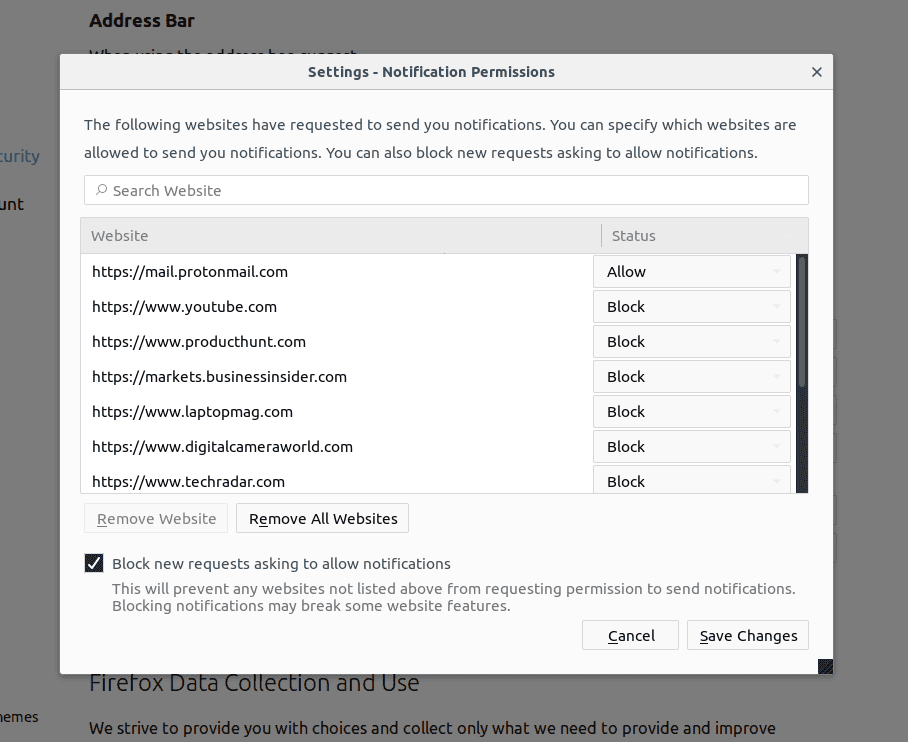
Mozilla Firefox
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
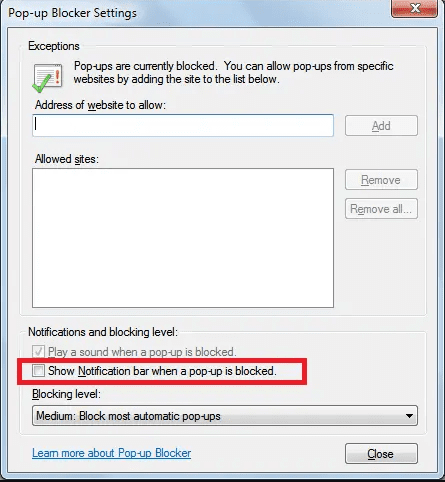
Internet Explorer
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
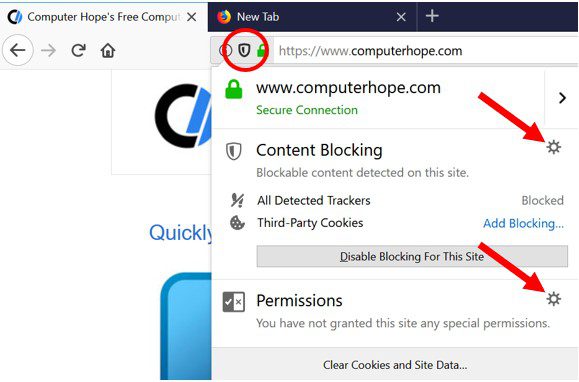
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
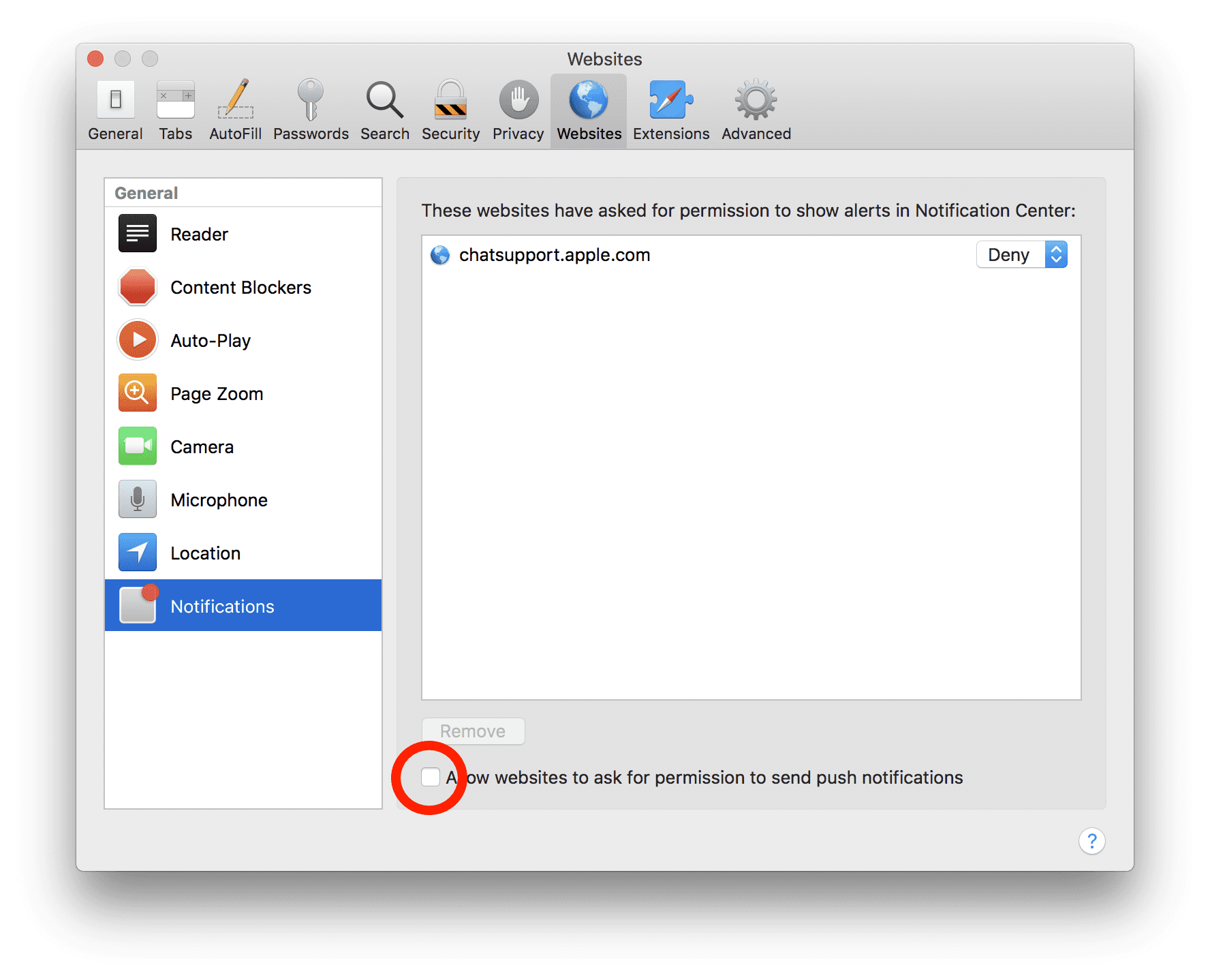
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove ResearchSecure:
Remove the related items of ResearchSecure using Control-Panel
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
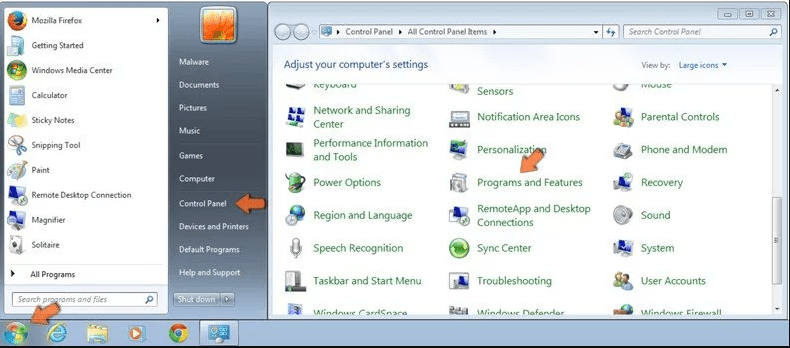
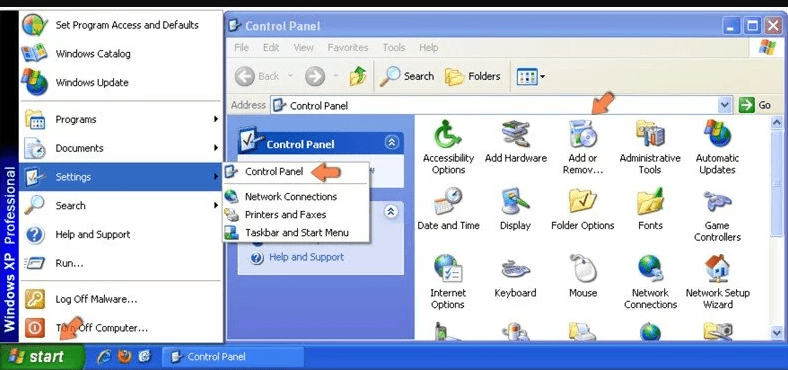
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
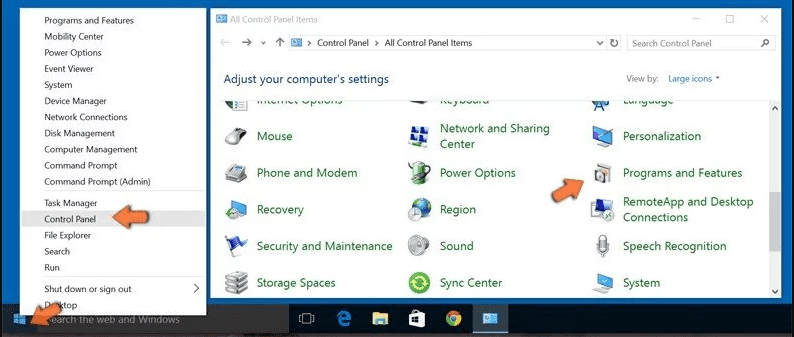
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
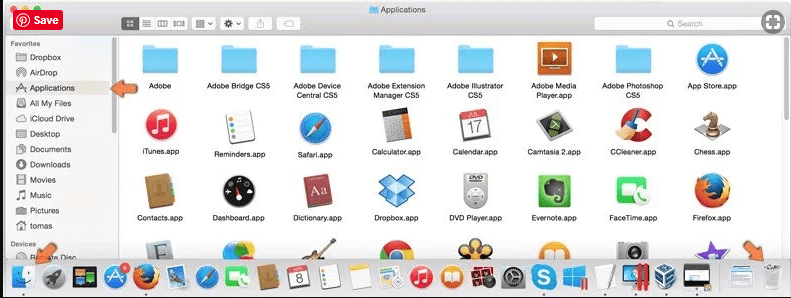
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
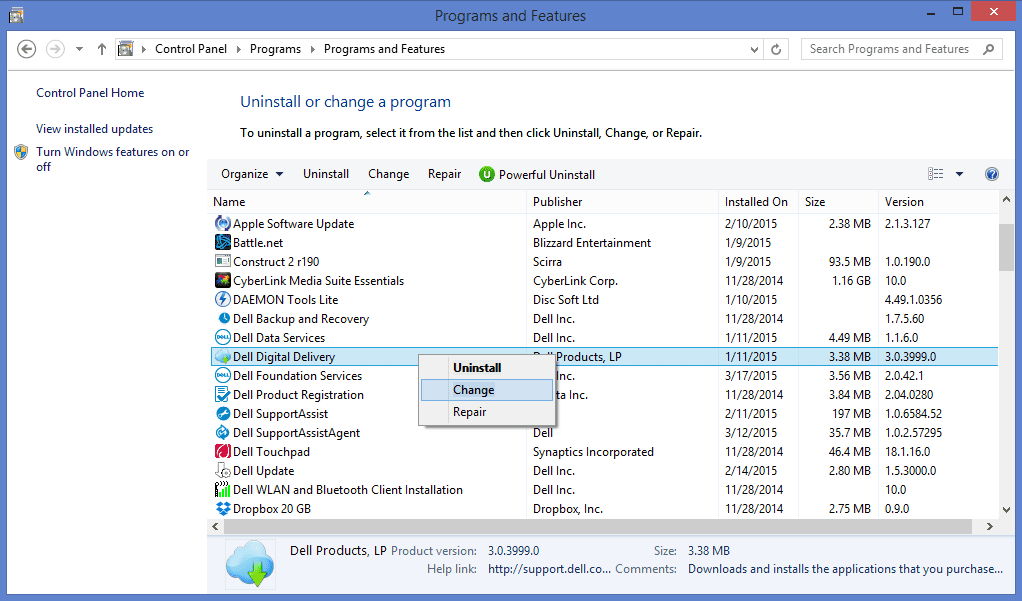
After you uninstall all the potentially unwanted program causing ResearchSecure issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Malware/Spyware/Virus can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter 5 antimalware scanner to check if the program can help you getting rid of this virus.
Special Offer (For Macintosh) If you are a Mac user and Malware/Spyware/Virus has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (ResearchSecure) from Internet Browsers
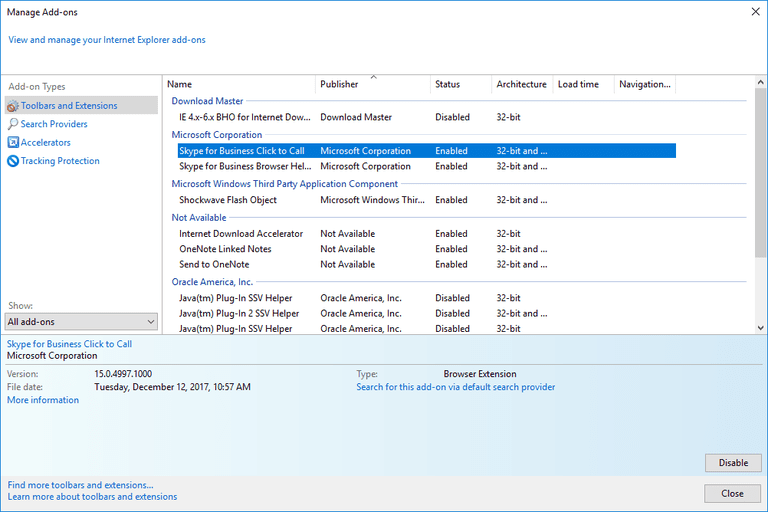
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
Additional Option
If you still face issues related to ResearchSecure removal, you can reset the Internet Explorer to its default setting.
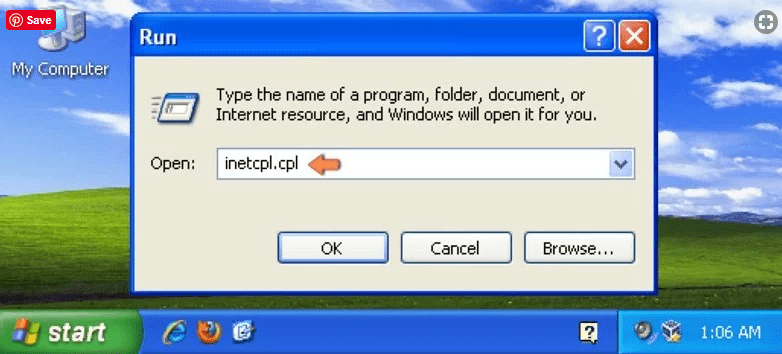
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
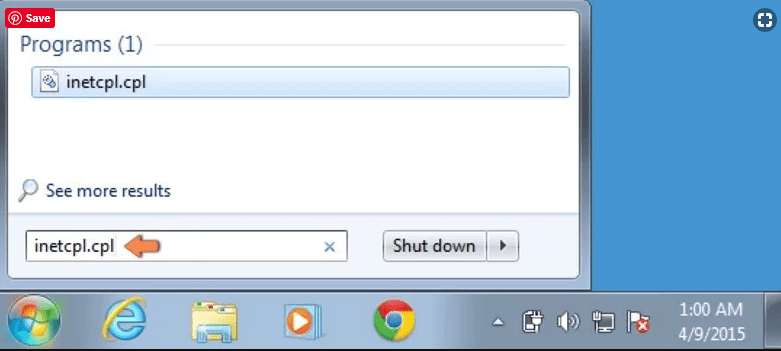
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
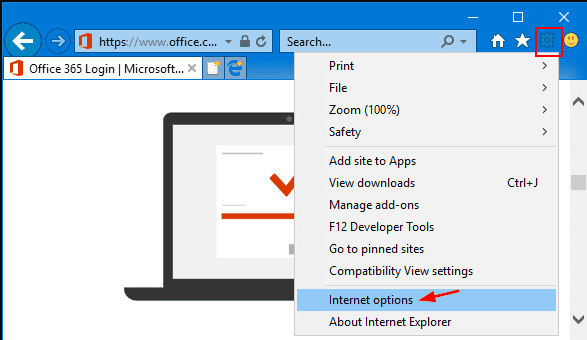
Select the “Advanced” tab in the newly opened window
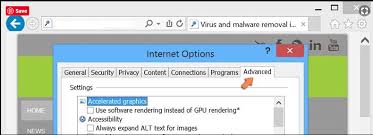
Press on “Reset” option
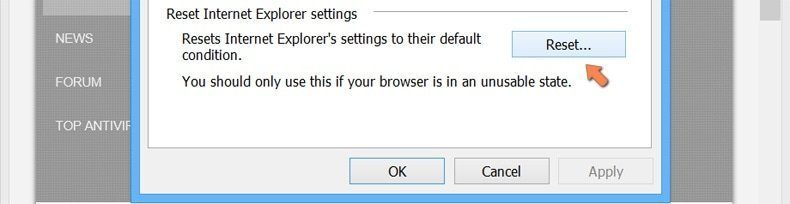
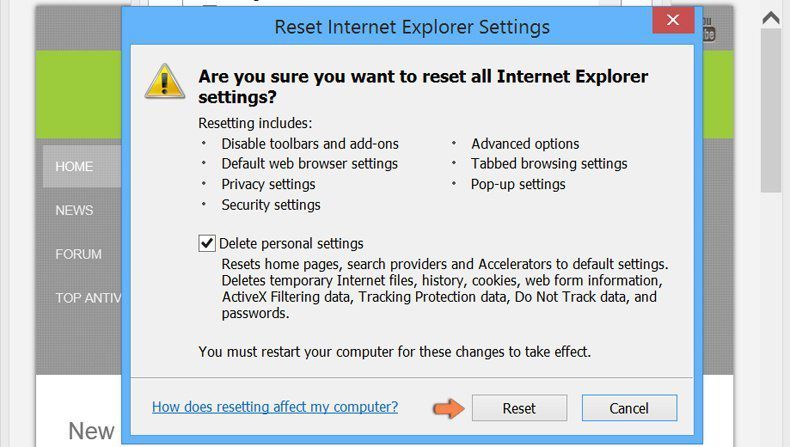
You have to press on the “Reset” button again to confirm that you really want to reset the IE
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
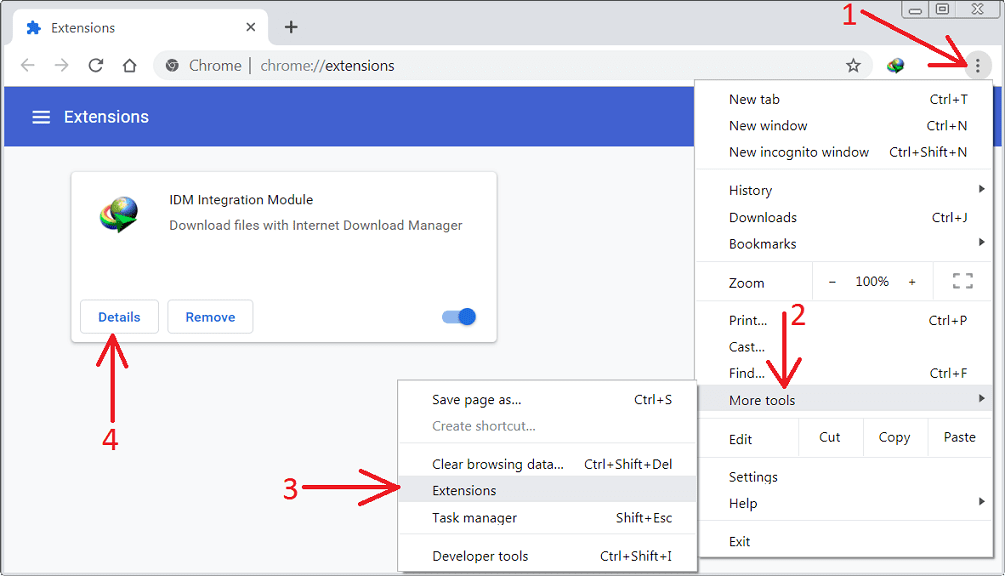
Optional Method
If the problems related to ResearchSecure still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
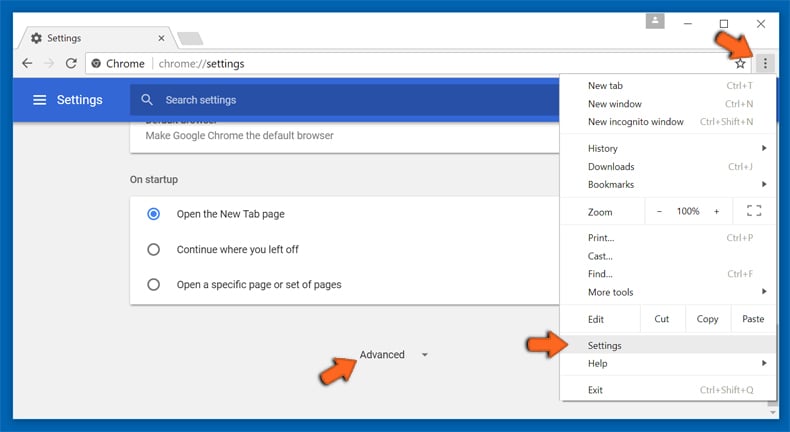
At the bottom, notice the “Reset” option and click on it.
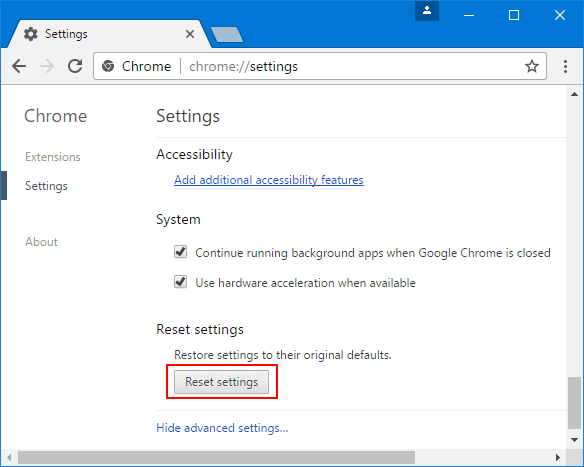
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
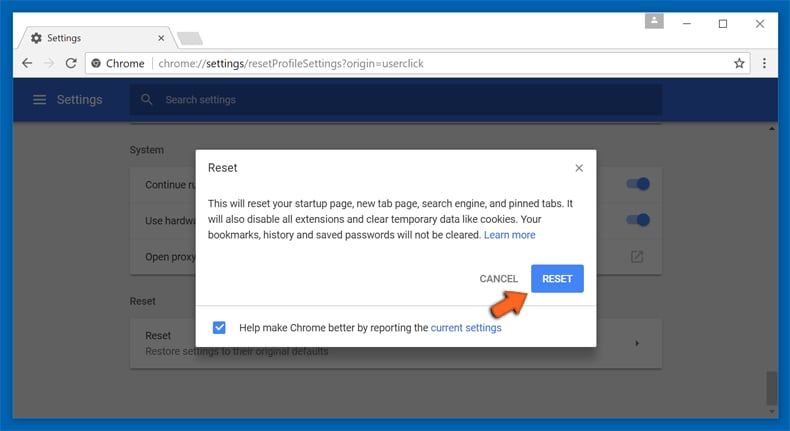
Remove ResearchSecure plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
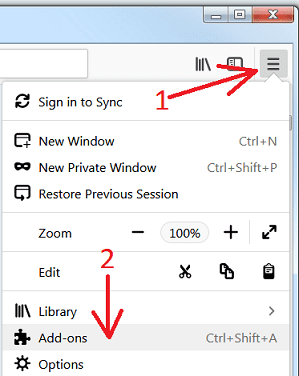
Optional Method
If you face problems in ResearchSecure removal then you have the option to rese the settings of Mozilla Firefox.
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
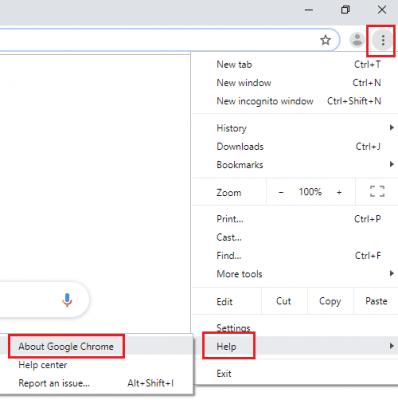
Choose “Troubleshooting Information”
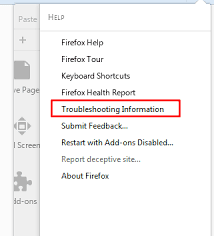
In the newly opened pop-up window, click “Refresh Firefox” button
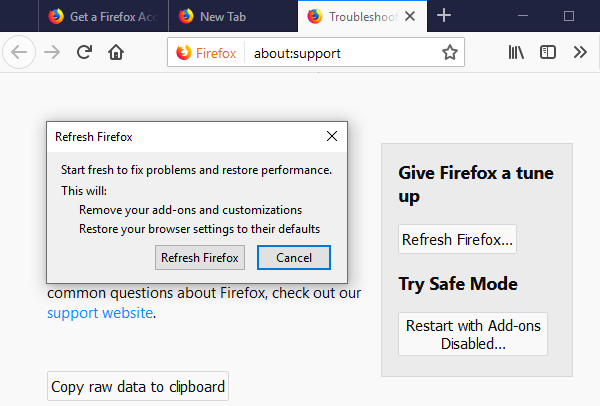
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
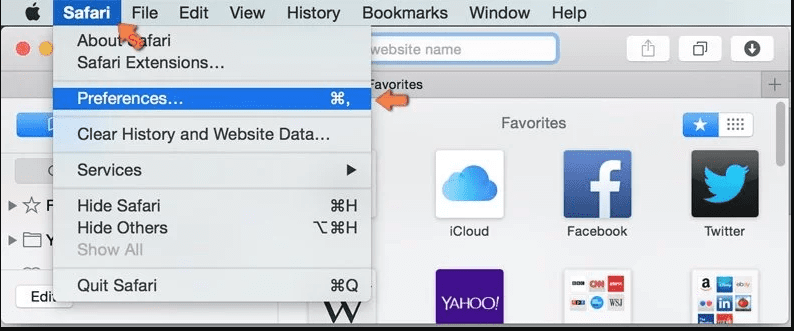
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
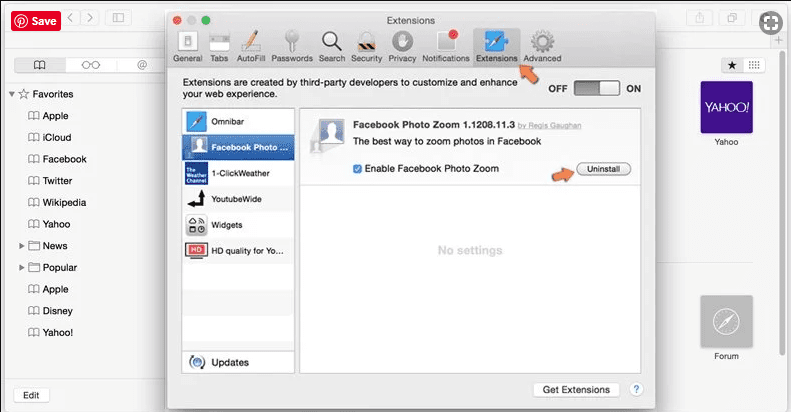
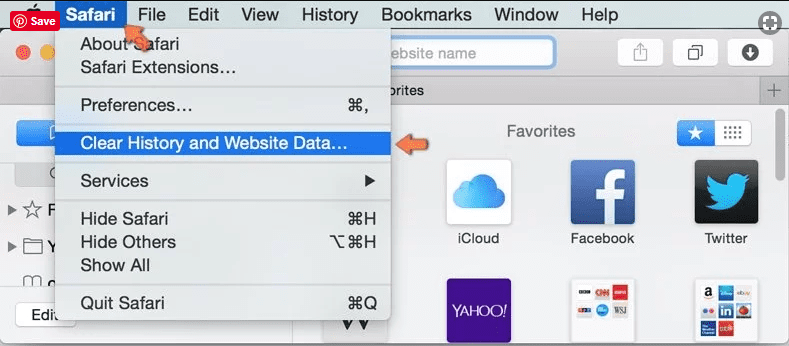
Optional Method
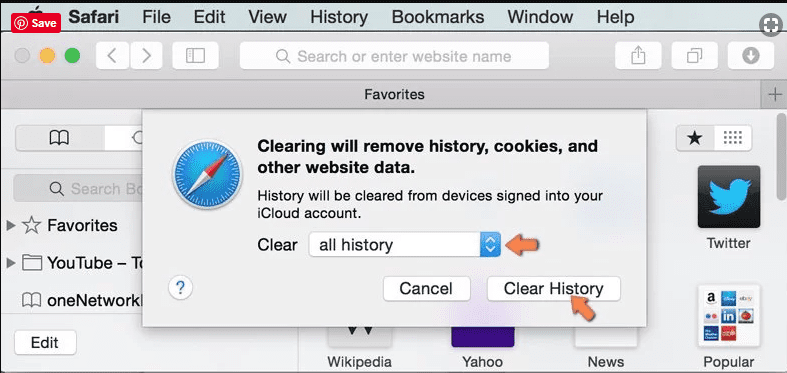
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
In the newly opened window, select “All History” and then press on “Clear History” option.
Delete ResearchSecure (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
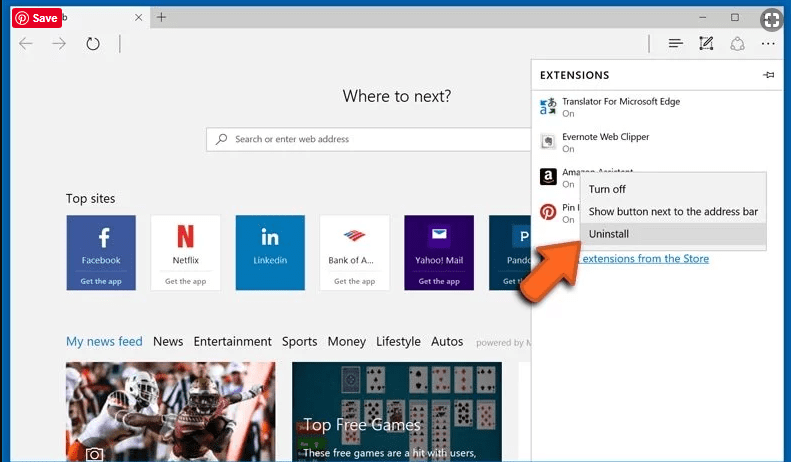
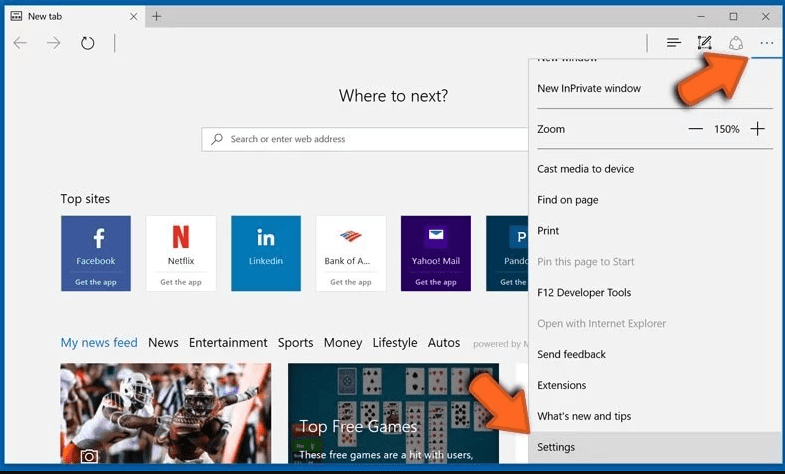
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
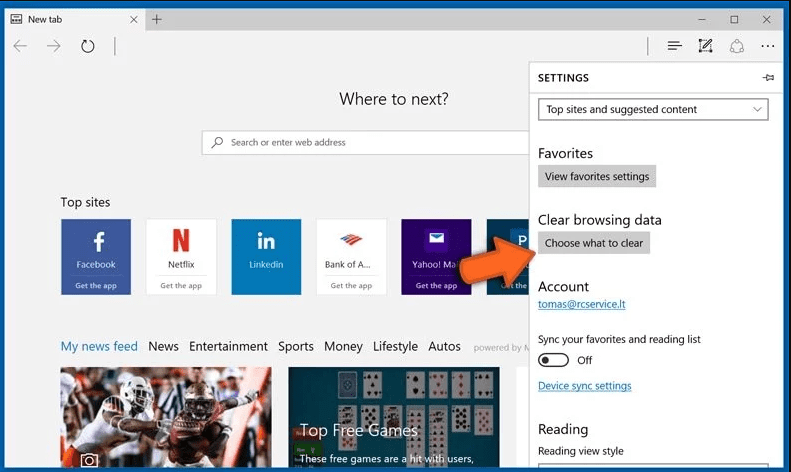
Next steps is to click on “Choose what to clear” button
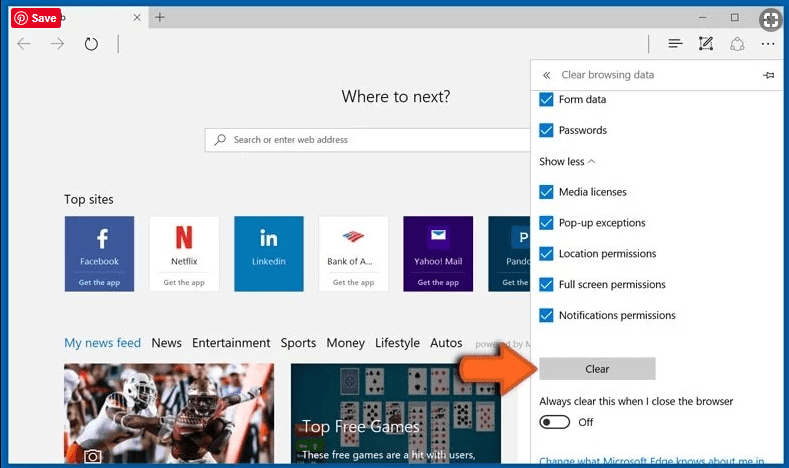
Click on “show more” and then select everything and then press on “Clear” button.
Recommended online habits you should acquire?
As soon as ResearchSecure infiltrates the PC system, it starts carrying out malicious activities in the background and may lead to a number of unpleasant issues. To avoid getting infected with such browser-based pests, below are some steps you can take:
- Download software from reputable sources: Only download software from reputable websites, such as the official page of the software vendor or well-known download portals. Avoid downloading software from third-party websites or peer-to-peer networks, as these are often sources of bundled adware.
- Pay attention during the installation process: When installing software, pay attention to each step of the installation process. Look for the checkboxes that may indicate the installation of additional software, such as adware or browser extensions. Uncheck these boxes if you don’t want to install the additional software.
- Choose custom installation: During the installation process, choose the custom installation option instead of the default or express installation. This will allow you to select which components to install and to opt-out of installing any bundled adware or other unwanted software.
- Read the End User License Agreement (EULA): Read the EULA carefully before installing any software. Look for clauses that may allow the installation of additional software or adware like ResearchSecure. If EULA contains such clauses, reconsider installing the software.
- Use a reputable web browser: Choose a reputable web browser, such as Google Chrome or Mozilla Firefox, and keep it up-to-date with the latest security patches.
- Install ad-blockers and pop-up blockers: You should use ad-blockers and pop-up blockers to prevent unwanted ads and pop-ups from appearing on your computer screen. Some web browsers have built-in ad-blocker and pop-up blockers, or you can install browser extensions that provide this functionality.
- Be careful when clicking on links: Don’t click on links in emails or on websites unless you are sure they are legitimate. Check the URL and ensure it is spelled correctly and is the correct website. Be wary of shortened URLs or URLs that lead to suspicious or unknown websites.
- Keep your web browser and operating system up-to-date: Regularly install software updates and security patches for your web browser and operating system. This will help to close any security vulnerabilities that adware, hijacker and other malware may exploit.
- Use a reputable antivirus program: A good antivirus program can detect and block infections like ResearchSecure and other malware before they can infect your computer. Make sure you choose a reliable antivirus suite and keep it up-to-date with the latest virus definitions.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your PC system safe and secure.
General FAQ Regarding Malware/Virus
Is Malware/Virus is capable for stealing your passwords?
Yes, malware are very much capable for stealing your passwords. In fact some malware are only injected to your PC with the sole purpose of stealing your sensitive information. The collected information can be further used by the cyber criminals to exploit the victim.
Why do cyber criminals use Malware/Virus?
Malware/ Virus are considered hazardous and have a potential to damage your PC. Keep in mind not all the viruses are dangerous and have no potential to harm a PC drastically. But some malware like browser hijackers, Trojan and ransomware are quite dangerous and can bring in a good chunk of money for their developers.
Why I should trust your research conducted on ResearchSecure?
It’s important to mention that our research is conducted independently and with the assistance of unbiased security experts, who provide us with daily updates on the latest definitions and threats related to malware, adware, and browser hijackers. Moreover, our study on the ResearchSecure threat is supported by VirusTotal.
Special Offer (For Windows)
Malware/Spyware/Virus can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter 5 antimalware scanner to check if the program can help you getting rid of this virus.
Special Offer (For Macintosh) If you are a Mac user and Malware/Spyware/Virus has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.