Remove Merlin Ransomware And Recover Infected Files
Step-by-step Guide To Delete File-Encrypting Virus
Merlin Ransomware is a hazardous crypto-malware that is known for sneaking into Windows computers by stealth and then locking up all the files stored therein. The main motive of the hackers behind file-locking viruses like this, Hhee Ransomware, and others is to prevent their victims from accessing their own important data and making them pay the ransom for the decryption. Merlin virus can contaminate almost all types of files, be they pictures, documents, audio and video files, etc. and make them completely unusable. During the encryption course, it also appends the “.Merlin” extension to the infected filenames, which tends to strengthen the hold.
Threat Summary
Name: Merlin Ransomware
Class: Ransomware, Crypto-virus
Characteristics: Locks important users’ files and then forces them to pay ransom fee to release those files
Extension: .Merlin
Ransom note: Merlin_Recover.txt
Danger level: High
Attackers’ Contact: Via Session messenger, [email protected], [email protected], [email protected]
Signs: Data cannot be opened, weird file extension, display of ransom note
Penetration: Spiteful email attachments, torrents sites, deceptive web content
Merlin Ransomware: Depth Analysis
Soon after finishing the encryption process, Merlin Ransomware puts a ransom note titled “Merlin_Recover.txt” which includes information about what occurred to users’ data as well as the instruction on what to do. It is stated that victims’ files have been encrypted and their sensitive data has been exfiltrated. In order to regain access to those files, they must pay the attackers an amount of ransom or else the stolen information will be revealed on the dark web. Victims can test the decryption by sending two infected files via the provided email addresses, and also warned against certain activities.
Should The Ransom Be Paid?
Despite the fact that files encoded by Merlin Ransomware cannot be opened without the interference of the attackers, you should not pay to these people. Reason behind this is they are cyber criminals and they have no ethics. Nobody can say whether you will have your files decrypted or not even after meeting all the crooks’ demands. It is more likely that they will disappear once you make the payment or send you a malicious tool that will cause even more hazardous issues inside the device. Instead of paying to the attackers, you should remove Merlin Ransomware from the system and then try to recover the data via other options.
How To Restore The Locked Files?
For data recovery, the best thing you can do is using backup if you have any. If you are a regular computer user, it is vital for you to keep backing up your crucial data as it will be very helpful for you in such precarious situations. Those who don’t possess an appropriate backup cannot do much here. So, we recommend employing our efficient file-recovery software that has been particularly crafted to retrieve the compromised information. You must go for it, but make sure to eliminate the virus from the system once and for all.
Frequently Asked Questions
Why did Merlin Ransomware encrypt my files?
Ransomware infections tend to encrypt users’ valuable data in order to extort ransom money from them for their decryption. Once these files are locked, they turn out to be completely inaccessible and cannot be opened no matter what you try or what tool you employ.
How to prevent ransomware infections?
If you don’t want to get assaulted by these nasty crypto-viruses, you need to avoid interaction with random online content, websites, irrelevant email messages, and other hateful web material. Also, use a professional security app and keep it up-to-date as it will safeguard you against these hazards.
Message In The Ransom Note:
Your ID is: –
Q: How to contact us?
A: Install session messenger from this link : hxxps://getsession.org/download And chat with us.
This is our sessions ID: 05752759728f65ca92b3d98fc72500cdb7c5b11eb7b17f7d8afc6b8ecdcbdedf6d
OR
Contact with these email addresses:
** Make sure to include the ID in the first line of massages or subject of email, otherwise we won’t answer your massages.
Q: What’s Happened?
A: Your files have been encrypted and now have the “Merlin” extension. The file structure has been changed to unreadable format, so they are inaccessible.
Your critical information has been downloaded, including databases, financial/developmental, accounting, and strategic documents.
Q: How to recover files?
A: If you want to decrypt all of your data and return your systems to operative state, you require a decryption tool.
We are the only ones who own it, and also, if you want your stolen data will be wiped out from our systems, you better contact us.
Q: What about guarantees?
A: we decrypt 2 non_important files under 5MB for free (they should not include sensitive information). We will decrypt them and send them back to you.
They can be from different computers on your network to be sure that one key can decrypts your whole systems. That is our guarantee.
It’s just a business and we don’t pursue any political objectives. We absolutely do not care about you and your data
except the money and our reputation are the only things that matters to us. if we do not do our work and liabilities, nobody will cooperate with us which is not in our interests.
Q: How will the decryption process proceed after payment?
A: After payment, we will send you our decryption program + detailed instructions for use. With this program, you will be able to decrypt all your encrypted files.
*** Important ***
1- certain files that were encrypted but not renamed to “Merlin” extension, they will also be recovered by the decryption tool.
2- If you want the decryption procedure to be effective, DO NOT delete or modify the encrypted files, it will cause issues with the decryption process.
3- Beware Any organization or individual who asserts they can decrypt your data without paying us should be avoided. They just deceive you and charge you much more money as a consequence; they all contact us and buy the decryption tool from us.
Q: If you don’t want to pay to us?
A: it does not matter to us, but you have to accept its consequences:
1- Your data will be leaked for free on TOR darknet and your competitors can have access to your data.
2- We know exactly what vulnerabilities exist in your network and will inform google about them. The money we asked for is nothing compare to all of these damages to your business
so we recommend you to pay the price and secure your business. If you pay we will give you tips for your security so it can’t be hacked in the future
besides you will lose your time and data cause we are the only ones that have the private key. In practice – time is much more valuable t
Special Offer (For Windows)
Merlin Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove Merlin Ransomware through “Safe Mode with Networking”
Step 2: Delete Merlin Ransomware using “System Restore”
Step 1: Remove Merlin Ransomware through “Safe Mode with Networking”
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
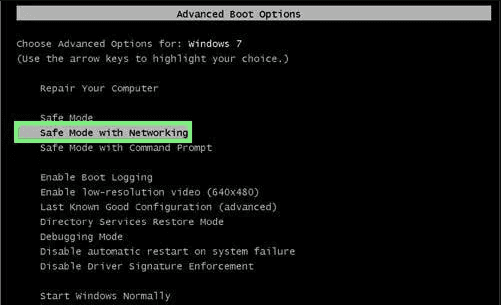
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
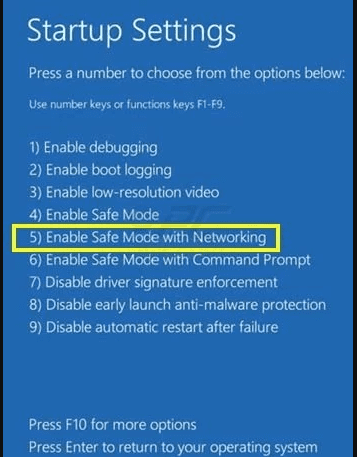
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
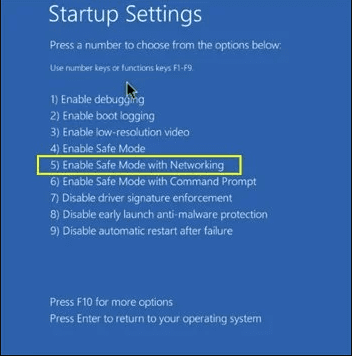
Step 2: Delete Merlin Ransomware using “System Restore”
Log-in to the account infected with Merlin Ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
Merlin Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
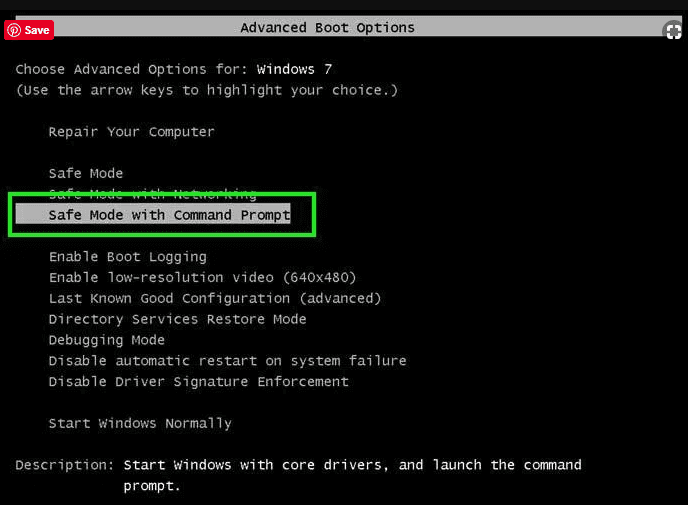
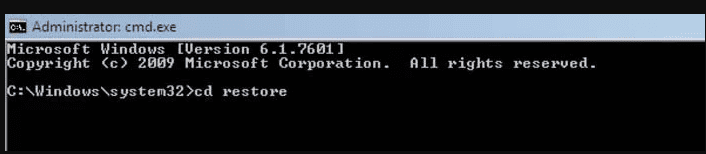
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
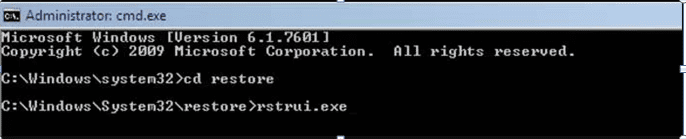
- Type: rstrui.exe and Press “ENTER”
- Click “Next” on the new windows
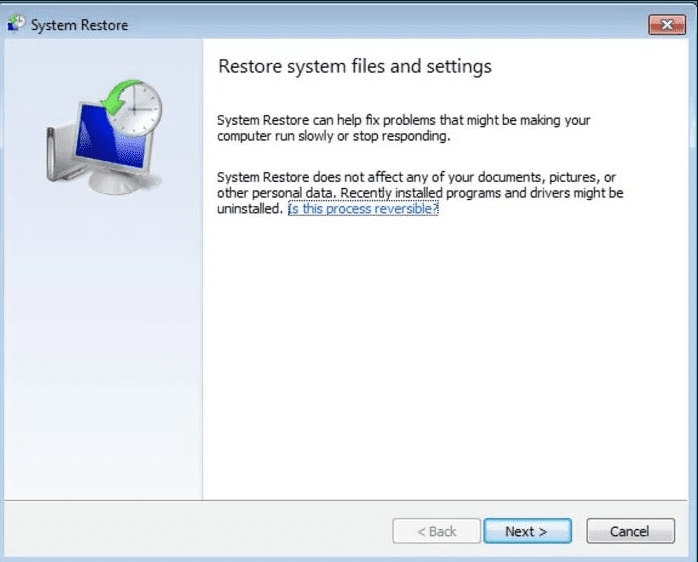
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to Merlin Ransomware infiltration in the PC.
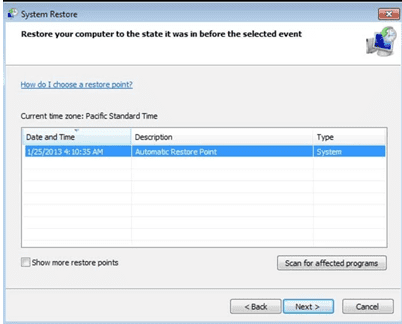
- In the newly opened windows, press on “Yes”.
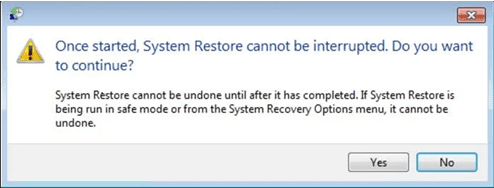
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove Merlin Ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of Merlin Ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
How to Restore Individual Encrypted File:
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
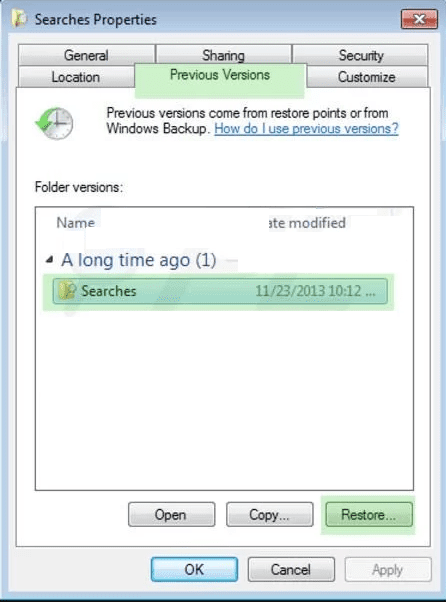
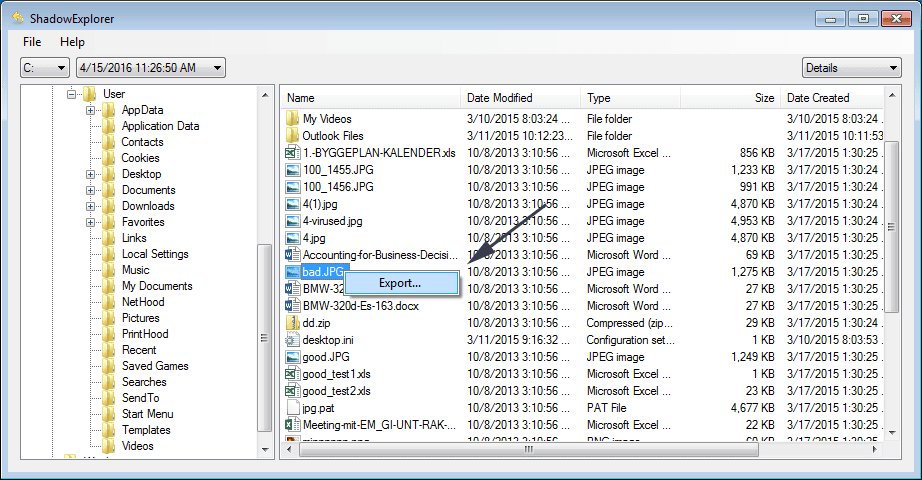
In order to access the files encrypted by Merlin Ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like Merlin Ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
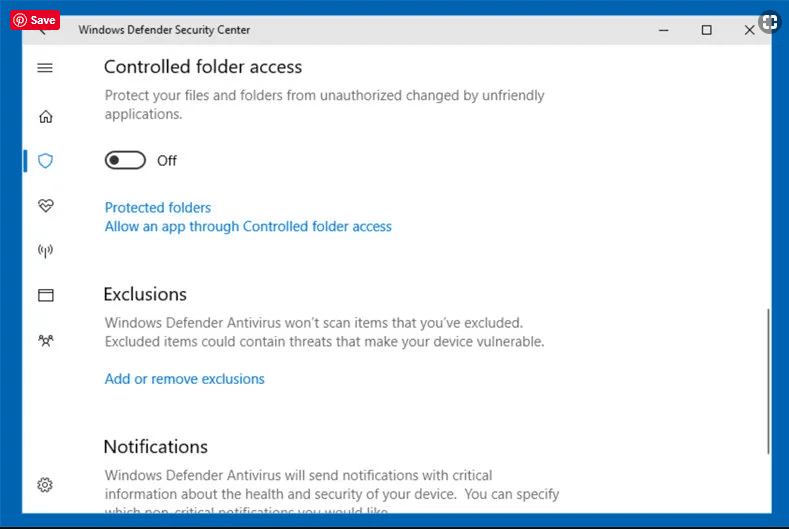
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by Merlin Ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with Merlin Ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove Merlin Ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

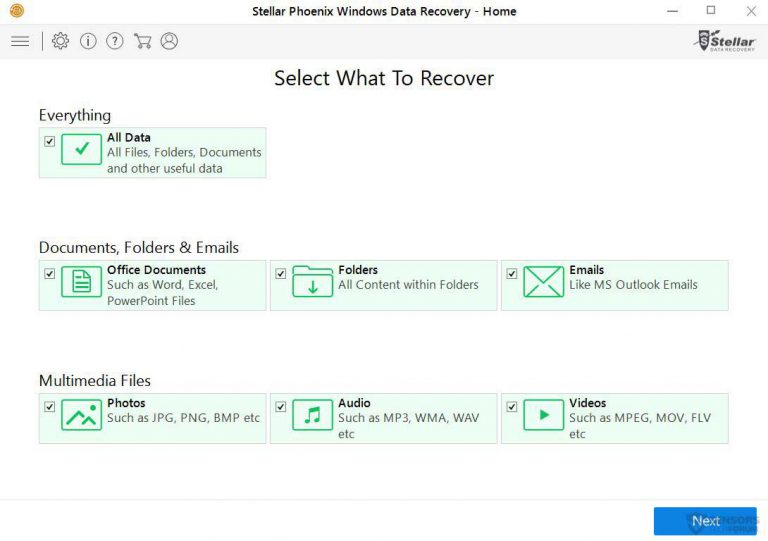
Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
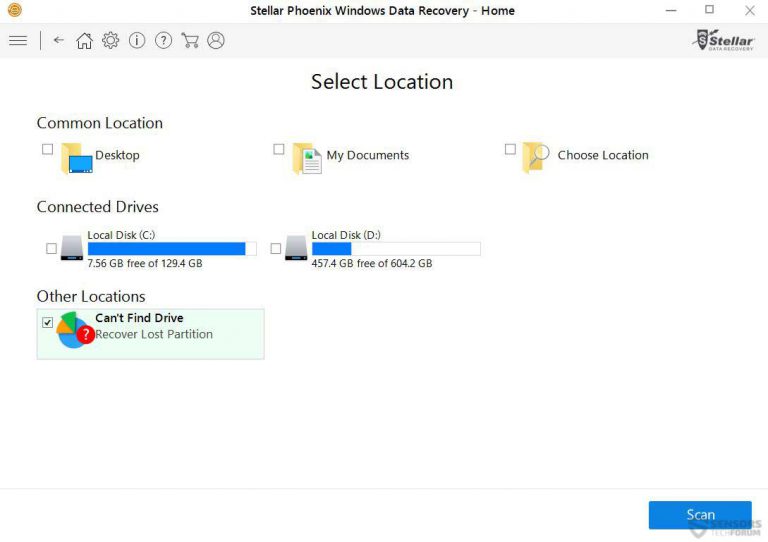
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
Merlin Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.