How to Remove Malware From Mac
Malware is a kind of precarious software which upon getting into a Mac device, conducts a series of malicious activities in the background and wreaks havoc onto the machine. Such types of computer infections are usually created by cyber actors with their sole motive to gain access to the targeted device without users’ knowledge for malicious purpose. Traditionally, the goal of such parasites is to generate revenues for the developers through deceptive ways such as by encrypting data and demanding ransom amount from the victims in order to regain access to their files or by stealing users’ sensitive information for resale on the dark web.
Depth Analysis of Mac Malware:
There are several kinds of malware from low risk to high risk like adware, Trojans, spyware, rootkits, ransomware etc. People think that Mac devices are safer than other PCs, however, this platform can be also compromised by such infections. Cyber hackers can use spyware to steal users’ personally identifiable information (PII) which may include their debit card and credit card numbers, social security numbers, banking account user IDs and passwords and many more details. The stolen data could make people vulnerable to identity theft. That’s a mighty reason you should know the signs of infection and consider the process of malware removal.
Some of the indications of having such threat in your Mac system are several pop-up windows, slow performance of the device, an unfamiliar browser toolbar, ads with inappropriate images or that are not easy to close, desktop wallpaper replaced with ransom note, files get encrypted and their extension changed etc. A ransomware is the most dangerous kind of malware that locks users’ important files and documents stored inside their PCs and then asks them to pay the attackers a sum of ransom to get the decryption tool. Such types of Mac viruses often rename the infected files by appending its own extension with their names and make them completely inaccessible or unusable. They also show threatening messages stating that they will reveal your crucial data to Online domains if the demanded amount is not paid within time.
Know About Adware And Browser Hijacker Kind Malware:
Other very intrusive Mac malware is adware or browser hijacker. Such types of infections often make critical changes in your default browser’s settings and replaces the current homepage and new tab page with their own nasty URLs. They also force people to browse through a customized search engine which only delivers inorganic results that are mixed with commercial contents and sponsored links. Their presence inside the computer also interrupts victims with intrusive ads and frequent redirects all the time. After getting infected with these potentially unwanted programs, you are bombarded with thousands of annoying ads all over the day that makes your Online sessions very complex and problematic. An adware displays eye-catching offers, deals, discounts, banners, promo codes, coupons etc. and tries to make users click on them in order to earn revenues via pay-per-click mechanism. However, these ads include sponsored links and redirect you to unknown web portals that might be also malware-laden.
Some of the examples of adware malware are Search baron, SearchRange, Smart Search etc. They usually enter the Mac PCs secretly without users’ consent and then start performing evil activities inside such as altering default browser’s settings, displaying intrusive contents, redirecting users’ to affiliated sites and so on. Trojan is another kind of malware that can be very dangerous for your system’s security. Such types of malware infection disable the working of all the running security measures and make the device vulnerable for more hazardous threats. They may easily bring other kinds of Online parasites in your Mac PC and turn it into a malware-hub. They also enable cyber hackers to get access to the work-station and perform evil deeds inside for their delicate welfare.
How Does A malware Enter The Mac Systems?
There are multiple precarious ways through which your Mac devices can get infected with such threats. For example, an adware, browser hijacker or other PUPs mostly enter the targeted systems along with freeware or shareware programs. This is the most common method used by PUP creators to spread these infections into every targeted PC systems without users’ approval. Such intruders get bundled with software and find the way on computer without requiring any permission. The unpacking of these extra tools is not taking place and you don’t get notified about the adware installation.
On The other hand, ransomware and Trojan viruses generally infiltrate the targeted system through multiple illusive techniques such as spam email campaigns, fake software updaters, questionable download sources, unofficial software activation tools, other Trojan etc. Nevertheless, the most common method used by Cyber actors to spread such parasites is by sending emails that contain malevolent attachments. Hackers usually attach MS office, PDF documents, exe files, and JavaScript files. Once you open the attachment, those spiteful files install some pernicious application.
How To Prevent malware Intrusion?
To prevent the installation of adware, hijacker or other similar PUAs, you should always choose Custom or Advanced installation options where you can take complete control over the incoming objects. You just have to untick the components that give a concerning look and pick only the main software. Custom wizard allows you to untick any of those additional extras, so experts always recommend staying away from Quick or Recommended configuration settings. You should avoid such services and pages where application is downloaded for free or always pay close attention to sources, distributors, authors of programs.
Moreover, you should not trust and ignore suspicious emails coming from stranger. Never open such emails that contain questionable attachment or web links. Moreover, avoid using software cracking tools since it is not legal. Additionally, use a reliable anti-malware program and keep updating it from time to time. However, in case you are one of those users who are already a victim of one of these notorious threats, don’t waste any time. Just take an immediate action and remove the existing malware from the computer by following the complete removal steps given below.
Special Offer (For Macintosh)
Malware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Remove Files and Folders Related to Malware
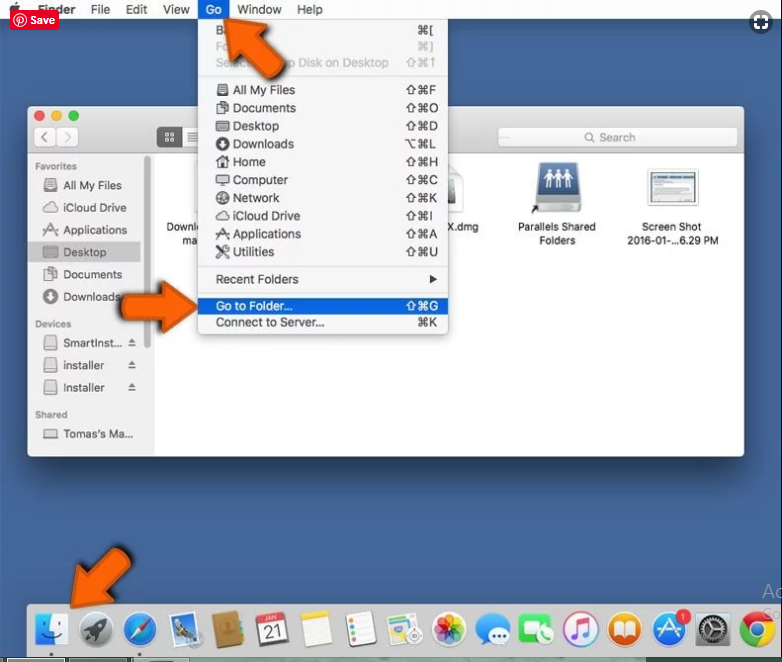
Open the “Menu” bar and click the “Finder” icon. Select “Go” and click on “Go to Folder…”
Step 1: Search the suspicious and doubtful malware generated files in /Library/LaunchAgents folder
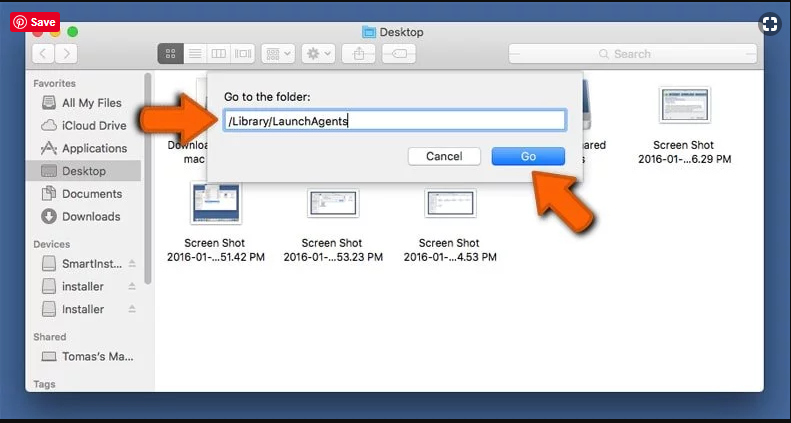
Type /Library/LaunchAgents in the “Go to Folder” option
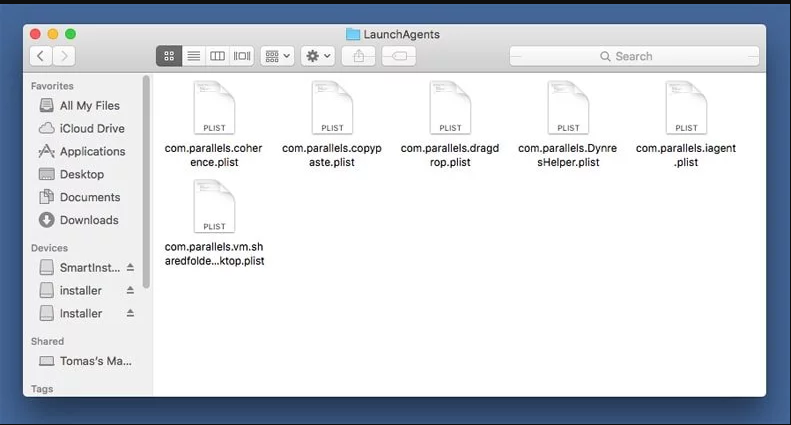
In the “Launch Agent” folder, search for all the files that you have recently downloaded and move them to “Trash”. Few of the examples of files created by browser-hijacker or adware are as follow, “myppes.download.plist”, “mykotlerino.Itvbit.plist”, installmac.AppRemoval.plist”, and “kuklorest.update.plist” and so on.
Step 2: Detect and remove the files generated by the adware in “/Library/Application” Support folder
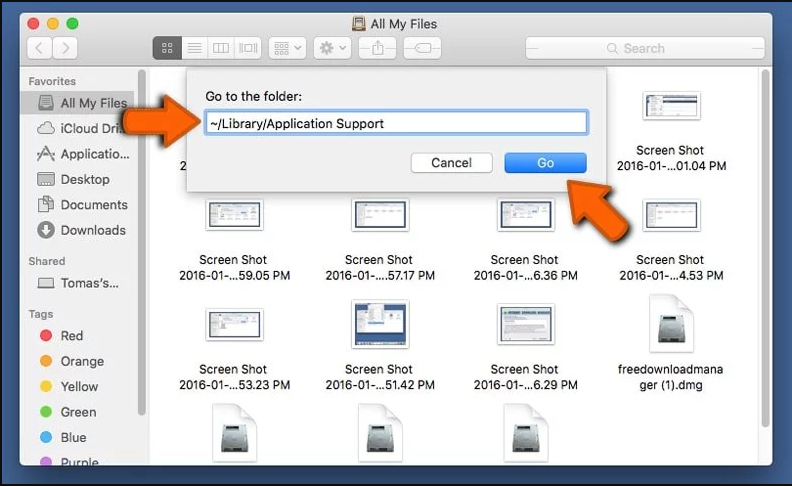
In the “Go to Folder..bar”, type “/Library/Application Support”
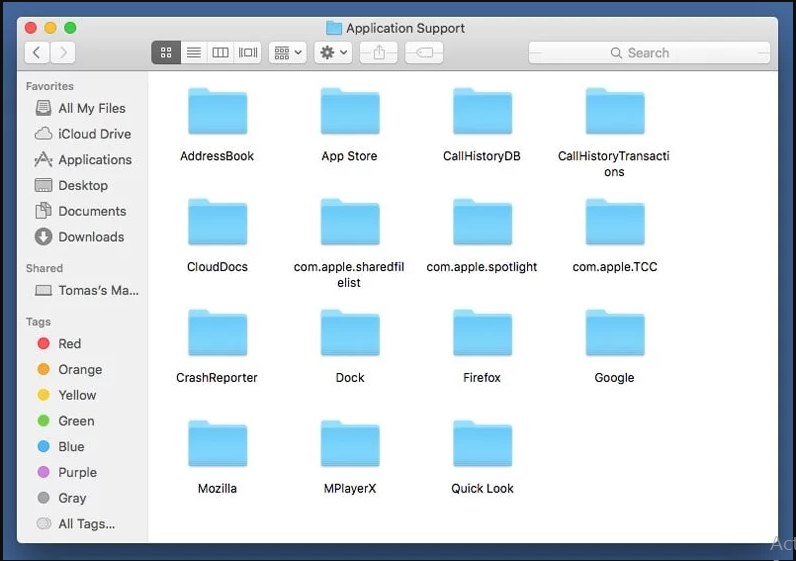
Search for any suspicious newly added folders in “Application Support” folder. If you detect any one of these like “NicePlayer” or “MPlayerX” then send them to “Trash” folder.
Step 3: Look for the files generated by malware in /Library/LaunchAgent Folder:
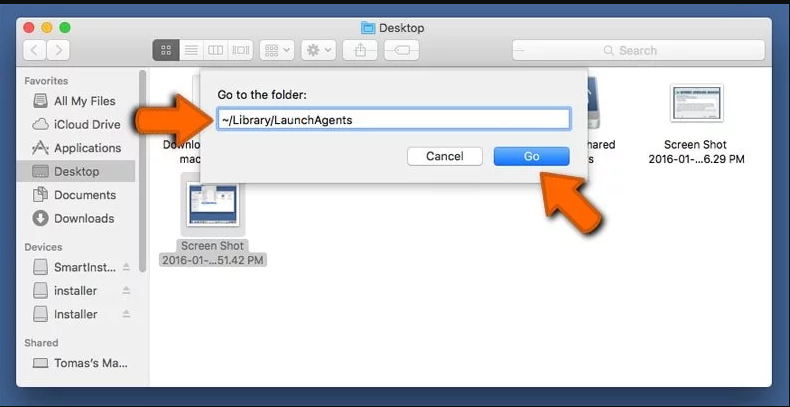
Go to Folder bar and type /Library/LaunchAgents
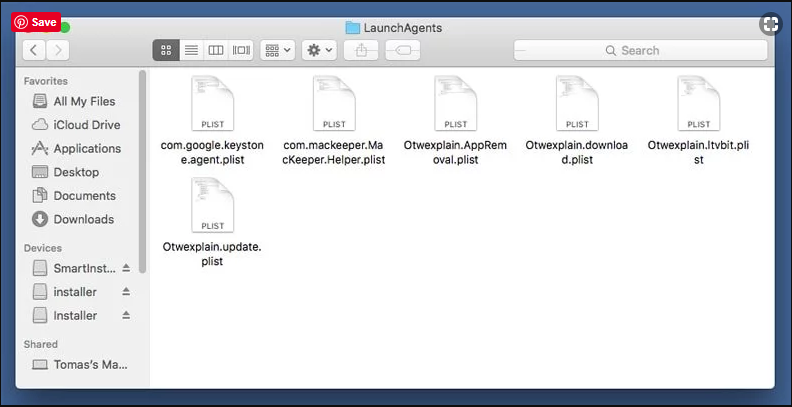
You are in the “LaunchAgents” folder. Here, you have to search for all the newly added files and move them to “Trash” if you find them suspicious. Some of the examples of suspicious files generated by malware are “myppes.download.plist”, “installmac.AppRemoved.plist”, “kuklorest.update.plist”, “mykotlerino.ltvbit.plist” and so on.
Step4: Go to /Library/LaunchDaemons Folder and search for the files created by malware
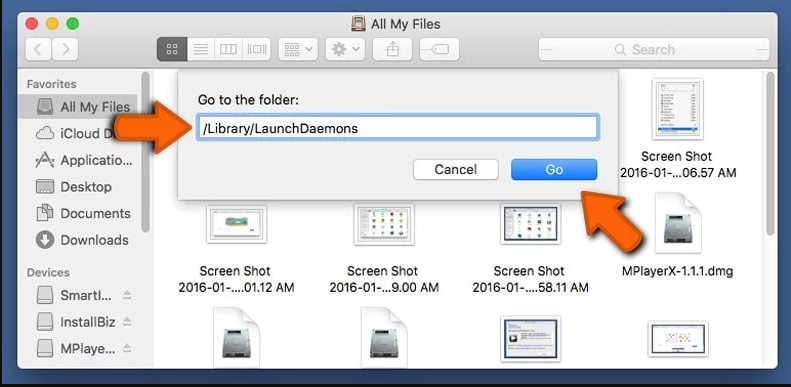
Type /Library/LaunchDaemons in the “Go To Folder” option
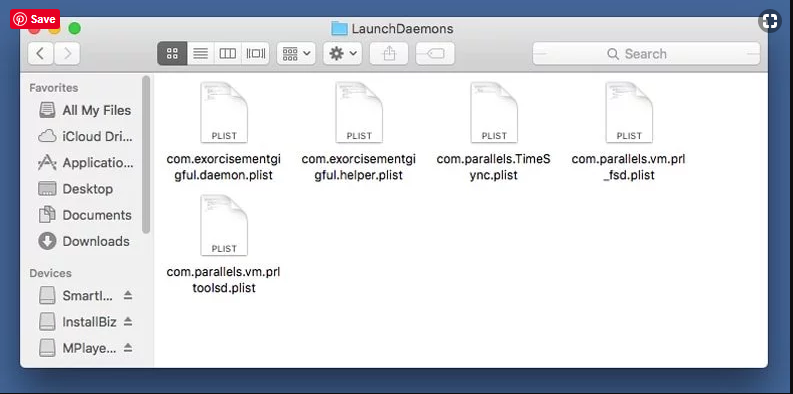
In the newly opened “LaunchDaemons” folder, search for any recently added suspicious files and move them to “Trash”. Examples of some of the suspicious files are “com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, “com.myppes.net-preference.plist”, “com.aoudad.net-preferences.plist” and so on.
Step 5: Use Combo Cleaner Anti-Malware and Scan your Mac PC
The malware infections could be removed from the Mac PC if you execute all the steps mentioned above in the correct way. However, it is always advised to be sure that your PC is not infected. It is suggested to scan the work-station with “Combo Cleaner Anti-virus”.
Special Offer (For Macintosh)
Malware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Once the file gets downloaded, double click on combocleaner.dmg installer in the newly opened window. Next is to open the “Launchpad” and press on “Combo Cleaner” icon. It is advised to wait until “Combo Cleaner” updates the latest definition for malware detection. Click on “Start Combo Scan” button.
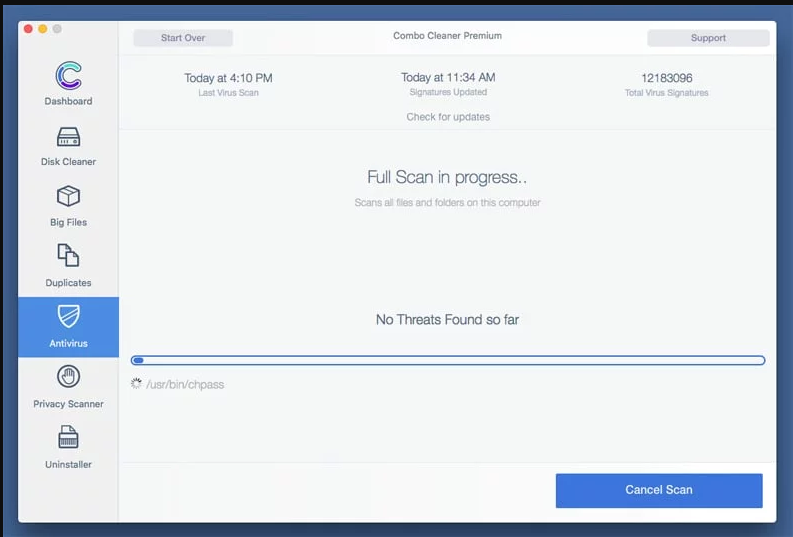
A depth scan of your Mac PC will be executed in order to detect malware. If the Anti-virus scan report says “no threat found” then you can continue with guide further. On the other hand, it is recommended to delete the detected malware infection before continuing.
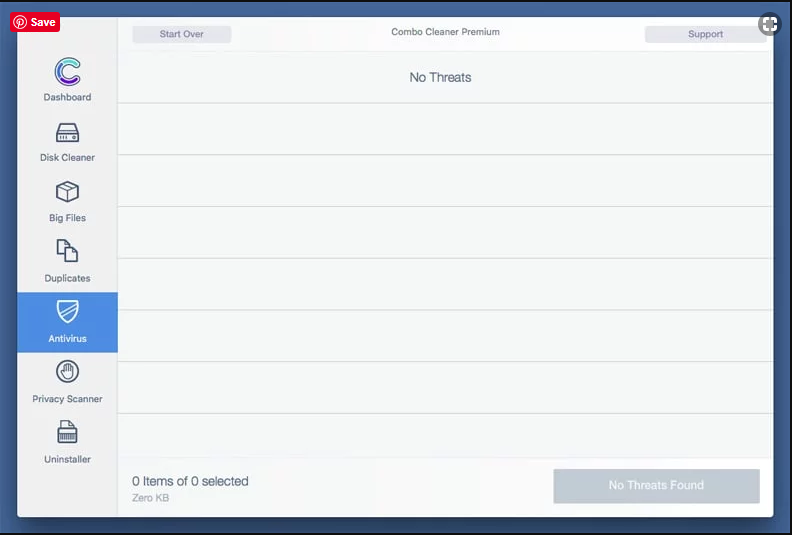
Now the files and folders created by the adware is removed, you have to remove the rogue extensions from the browsers.
Remove Malware from Internet Browsers
Delete Doubtful and Malicious Extension from Safari
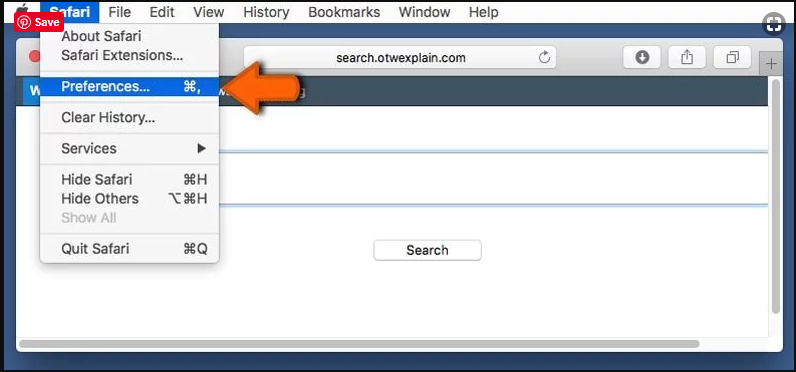
Go to “Menu Bar” and open “Safari” browser. Select “Safari” and then “Preferences”
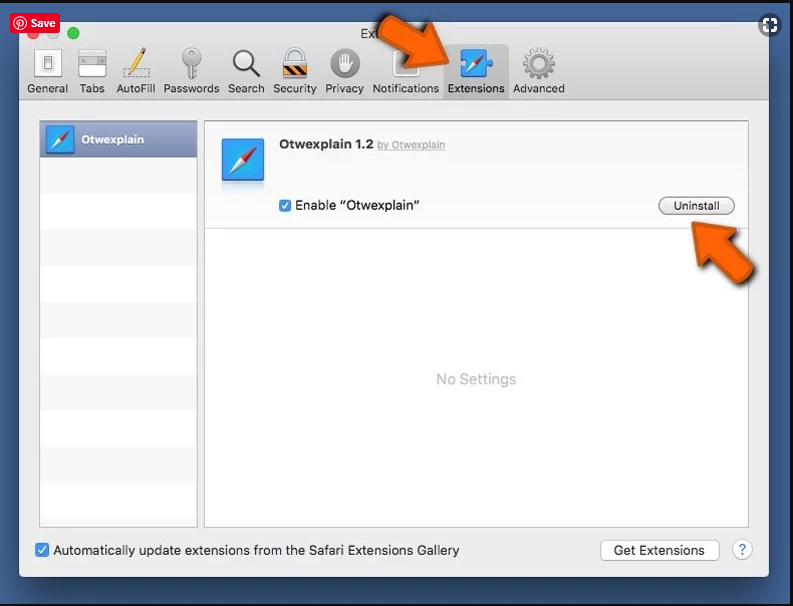
In the opened “preferences” window, select “Extensions” that you have recently installed. All such extensions should be detected and click the “Uninstall” button next to it. If you are doubtful then you can remove all the extensions from “Safari” browser as none of them are important for smooth functionality of the browser.
In case if you continue facing unwanted webpage redirections or aggressive advertisements bombarding, you can reset the “Safari” browser.
“Reset Safari”
Open the Safari menu and choose “preferences…” from the drop-down menu.
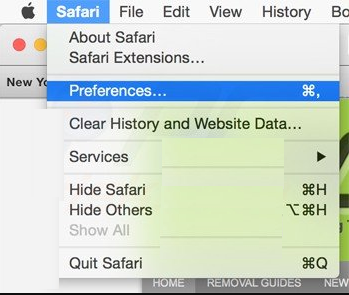
Go to the “Extension” tab and set the extension slider to “Off” position. This disables all the installed extensions in the Safari browser
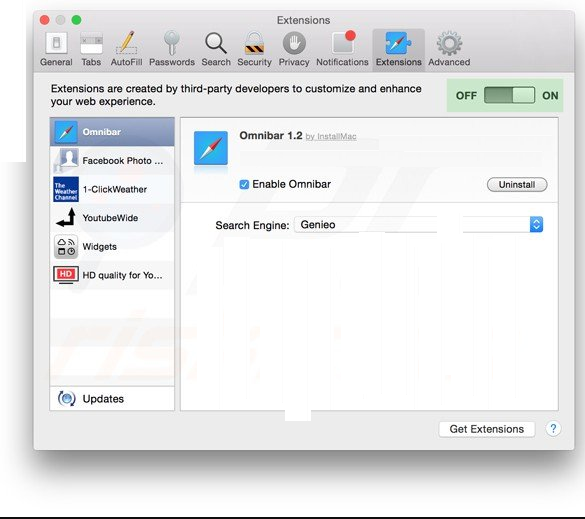
Next step is to check the homepage. Go to “Preferences…” option and choose “General” tab. Change the homepage to your preferred URL.
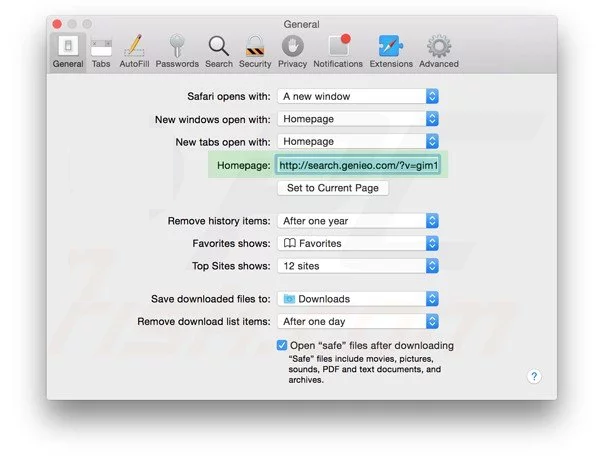
Also check the default search-engine provider settings. Go to “Preferences…” window and select the “Search” tab and select the search-engine provider that you want such as “Google”.
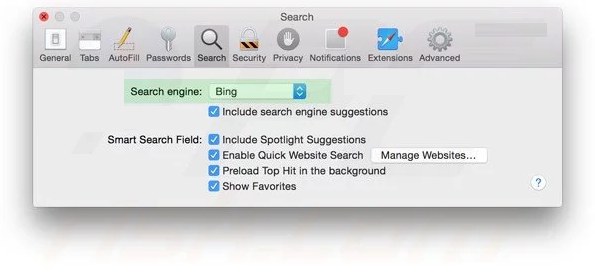
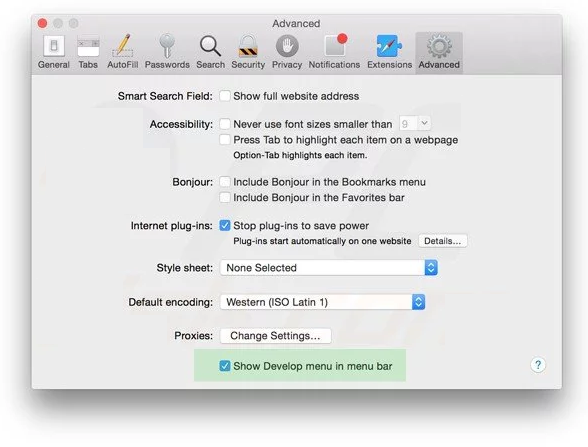
Next is to clear the Safari browser Cache- Go to “Preferences…” window and select “Advanced” tab and click on “Show develop menu in the menu bar.“
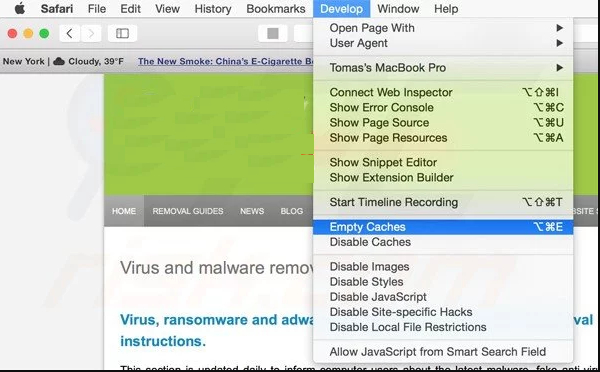
Go to “Develop” menu and select “Empty Caches”.
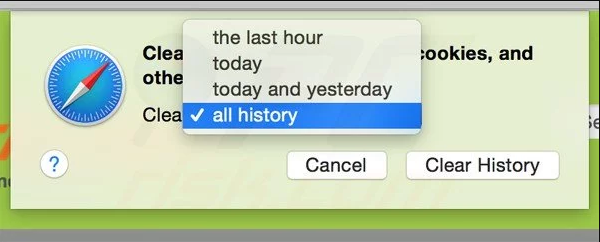
Remove website data and browsing history. Go to “Safari” menu and select “Clear History and Website Data”. Choose “all history” and then click on “Clear History”.
Remove Unwanted and Malicious Plug-ins from Mozilla Firefox
Delete Malware add-ons from Mozilla Firefox

Open the Firefox Mozilla browser. Click on the “Open Menu” present in the top right corner of the screen. From the newly opened menu, choose “Add-ons”.
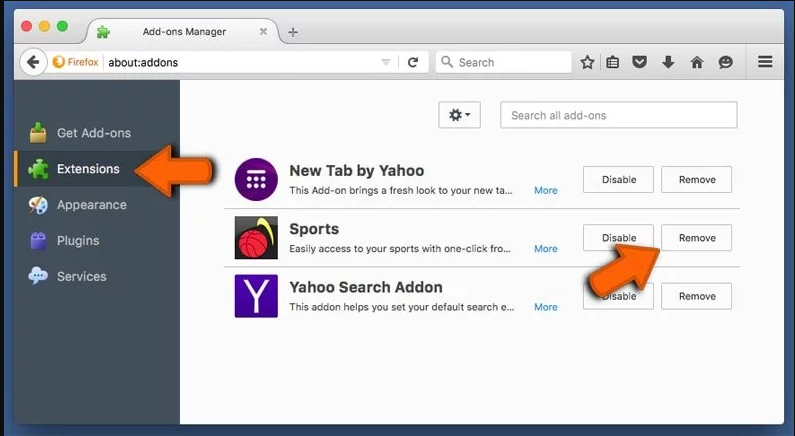
Go to “Extension” option and detect all the latest installed add-ons. Select each of the suspicious add-ons and click on “Remove” button next to them.
In case if you want to “reset” the Mozilla Firefox browser then follow the steps that has been mentioned below.
Reset Mozilla Firefox Settings
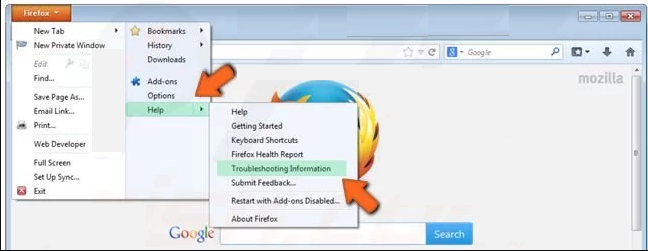
Open the Firefox Mozilla browser and click on “Firefox” button situated at the top left corner of the screen.

In the new menu, go to “Help” sub-menu and choose “Troubleshooting Information”
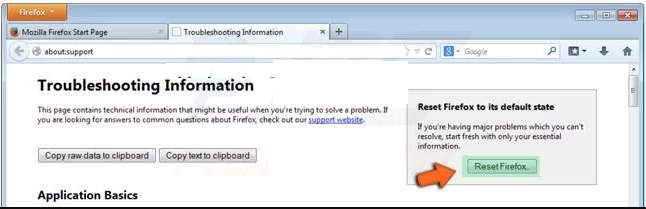
In the “Troubleshooting Information” page, click on “Reset Firefox” button.
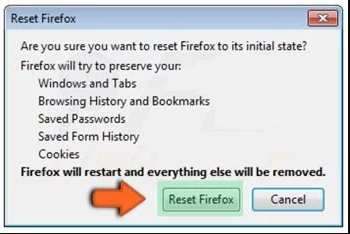
Confirm that you want to reset the Mozilla Firefox settings to default by pressing on “Reset Firefox” option
The browser will get restarted and the settings changes to factory default
Delete Unwanted and Malicious Extensions from Google Chrome
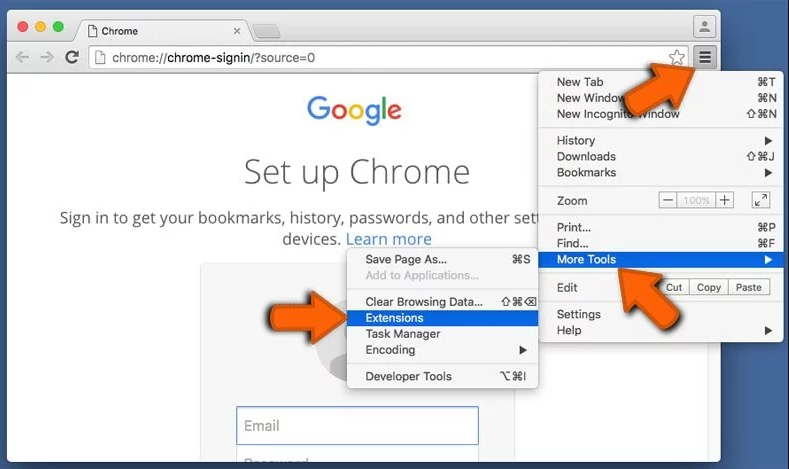
Open the chrome browser and click on “Chrome menu”. From the drop down option, choose “More Tools” and then “Extensions”.
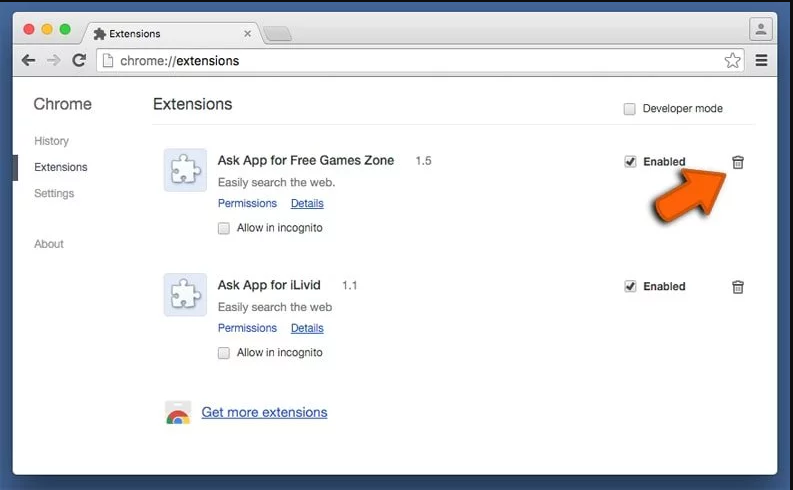
In the “Extensions” option, search for all the recently installed add-ons and extensions. Select them and choose “Trash” button. Any third-party extension is not important for the smooth functionality of the browser.
Reset Google Chrome Settings
Open the browser and click on three line bar at the top right side corner of the window.
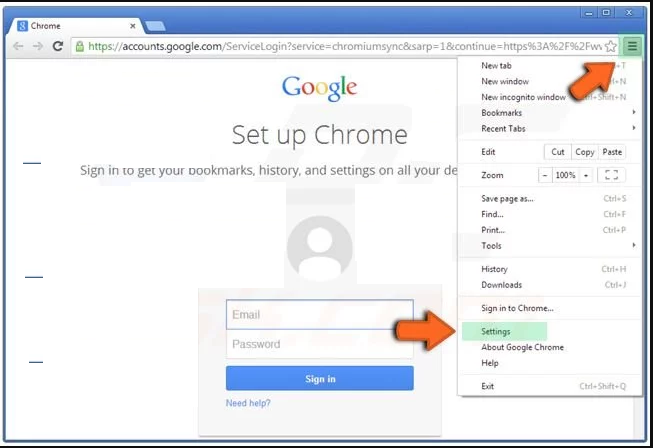
Go to the bottom of the newly opened window and select “Show advanced settings”.
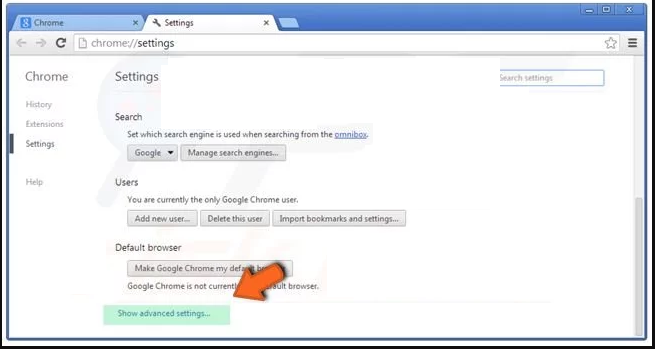
In the newly opened window, scroll down to the bottom and choose “Reset browser settings”
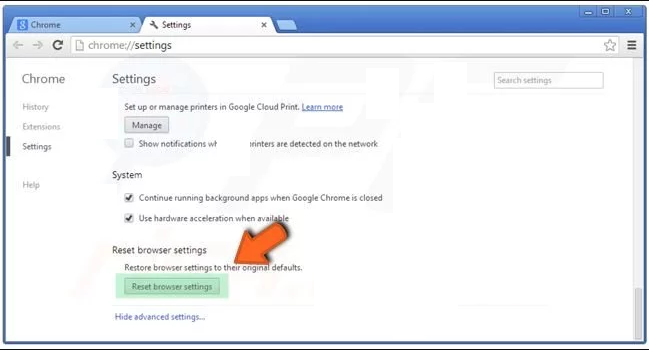
Click on the “Reset” button on the opened “Reset browser settings” window
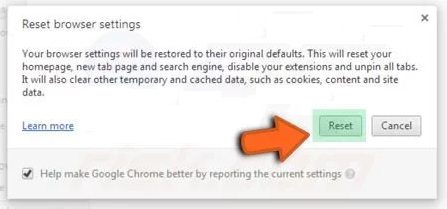
Restart the browser and the changes you get will be applied
The above mentioned manual process should be executed as it is mentioned. It is a cumbersome process and requires a lot of technical expertise. And hence it is advised for technical experts only. To be sure that your PC is free from malware, it is better that you scan the work-station with a powerful anti-malware tool. The automatic malware removal application is preferred because it doesn’t requires any additional technical skills and expertise.
Special Offer (For Macintosh)
Malware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Download the application and execute it on the PC to begin the depth scanning. Once the scanning gets completed, it shows the list of all the files related to Malware. You can select such harmful files and folders and remove them immediately.



