Remove Kelly (Leen) Ransomware and recover encrypted files
Easy tips to delete Kelly (Leen) Ransomware and restore data
Ransomware type of viruses deny users’ access to their crucial files by performing files encryption on the compromised host machine and then display ransom demanding message. Crooks monetize through ransomware by selling decryption tools. The Kelly (Leen) Ransomware encrypts files and renames them with .locky extension. For example, it changes the file 1.jpg to 1.jpg.locky, 2.jpg to 2.jpg.locky and so on. Following to it, it displays a pop-up window as its ransom note. The ransom message is written in Chinese language.

In most cases, ransom notes from ransomware contain contact details and payment information such as the price of the decryption tool, cryptocurrency wallet address, and email address belongs to the crooks and payment deadline. As written in the ransom note that Kelly (Leen) Ransomware displays, this ransomware encrypts all stored files that cannot be restored for 0.05 BTC by transferring the amount of Bitcoin to the provided wallet address. It ends with a warning to the users that if they do not make the payment before time runs out, the price of the decryption tool will be doubled and the files will be deleted if they are not going to pay the ransom for a long time.
Usually, malicious actors behind ransomware promise to send some type of decryption tool once the payment is done. However, it is commonly observed that victims do not receive any such tool even if they fulfill all the demands. In other words, they get scammed. Thus, it is recommended not to trust crooks. Unfortunately, ransomware viruses perform files encryption using some strong cipher algorithms that make it impossible to decrypt the files without the right decryption tool.
You have the option to wait until the official decryptor of Kelly (Leen) Ransomware is released by security researchers after cracking the code used. Meanwhile, you can try alternatives such as Shadow Copies or data recovery tools for the files recovery – in the data recovery section below the post, you will find complete step-by-step guide how to use these options to recover the files. However, if you have existing backups, you have nothing to look back. Simply remove Kelly (Leen) Ransomware and restore the files using backup. For the malware removal process, refer our instruction provided below the post or use some reputable antivirus tool.
How did Kelly (Leen) Ransomware enter my system?
Usually, crooks use spam emails, Trojans, fake software updaters, files on questionable sources and software cracking tools to distribute malware. When emails are used, they contain malicious files or links for such files as email attachments. The crooks have the only goal to trick people into opening the malicious files that are designed to download malware. Usually, they try to trick people into opening malicious Microsoft Office documents, PDFs, Archives, JavaScript and so on. It is common that malware can be distributed through Trojans. These are malicious programs especially designed to download/ install additional malware on compromised systems.
Fake software updaters are disguised as legit installers that supposedly install updates of fixes. However, they either install malware or infect systems by exploiting bugs, flaws of outdated software installed on system. Examples of untrustworthy downloading channels are p2p networks, free file hosting sites and third party downloaders/ installers. Users infect systems when they open malicious files downloaded via the aforementioned channels. Usually, those malicious files look like regular files. Software cracking tools supposedly bypass the activation keys of paid software, although these tools often install malicious malware before activating licensed software.
Text presented in Kelly (Leen) Ransomware‘s pop-up window:
Leen
FILE ENCRYPTED BY KELLY
我的电脑出了什么问题
您电脑内的重要文件被加密保存了,无法正常打开访问
除了我们以外,没有任何方式您可以恢复这些档案
如何恢复这些文件
答案是肯定的,只能透过我们的解密服务才能恢复
这个服务需要收费,且有时效性
费用与时效
我们仅接受比特币(Bitcoin)做为付款方式,比特币付款地址和数量将显示于下方栏位中,
同时提醒您若在期效内没有收到付款,费用将会翻倍,时间过久您的档案将会被全数删除。
强烈建议,在档案恢复之前,请不要关闭或是删除此软件,并且关闭您所有的防毒软件,否则您的档案有可能永远无法复原。
Bitcoin address: 1FuPAucXqBXvhzzXguCyQAH7AbGHg6xfrM
How to prevent ransomware intrusion?
Websites links and attachments received from emails that are irrelevant, suspicious and unknown should never be opened, especially when they are sent from unknown, suspicious addresses. It is common that links or files in emails of this kind are used to deliver malware. Files and programs should always be downloaded from official websites and direct links. Files downloaded from unofficial pages, third party downloaders, free file hosting sites and etc can be malicious. Installed software should have to be activated/ updated using implemented tools/ functions from official software developers. Third party/ unofficial tools are often designed to infect systems with malware. Also, it is illegal to activate software using cracking tools.
Special Offer (For Windows)
Kelly (Leen) Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove Kelly (Leen) Ransomware through “Safe Mode with Networking”
Step 2: Delete Kelly (Leen) Ransomware using “System Restore”
Step 1: Remove Kelly (Leen) Ransomware through “Safe Mode with Networking”
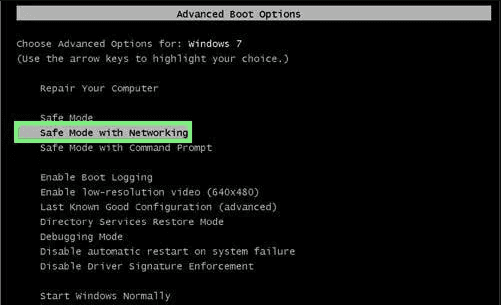
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
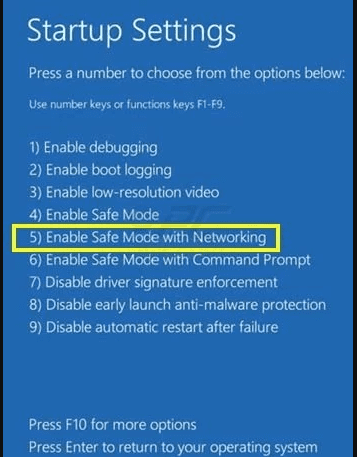
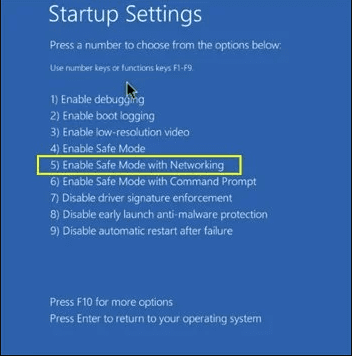
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
Step 2: Delete Kelly (Leen) Ransomware using “System Restore”
Log-in to the account infected with Kelly (Leen) Ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
Kelly (Leen) Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
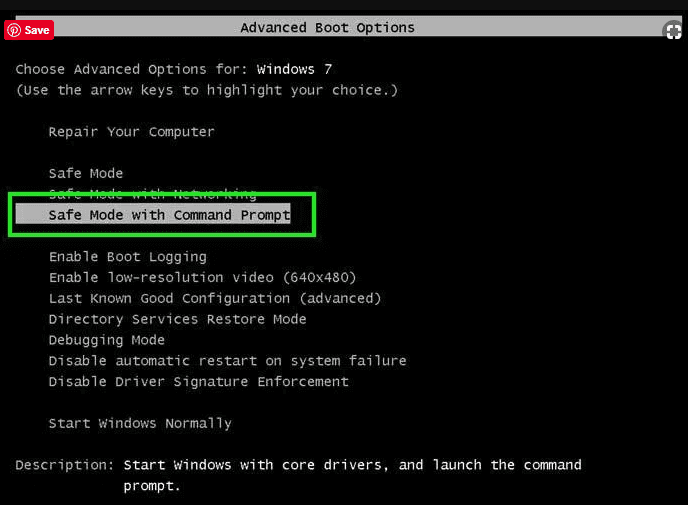
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
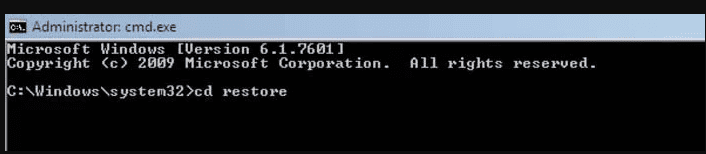
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
- Type: rstrui.exe and Press “ENTER”
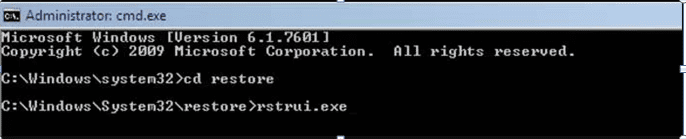
- Click “Next” on the new windows
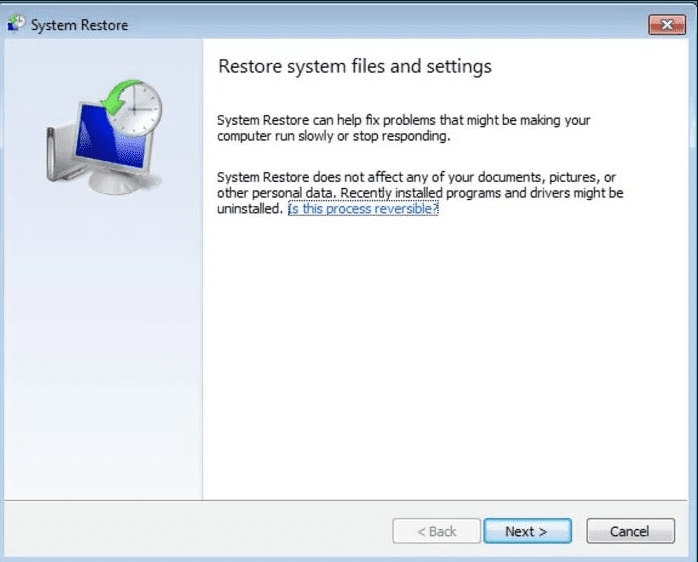
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to Kelly (Leen) Ransomware infiltration in the PC.
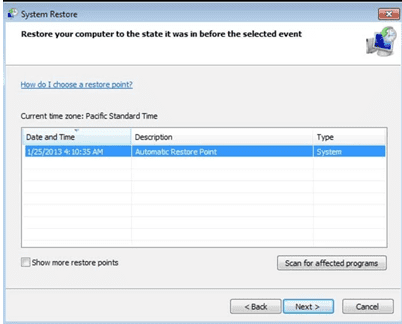
- In the newly opened windows, press on “Yes”.
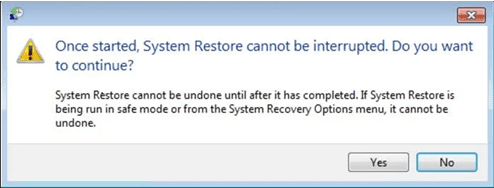
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove Kelly (Leen) Ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of Kelly (Leen) Ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
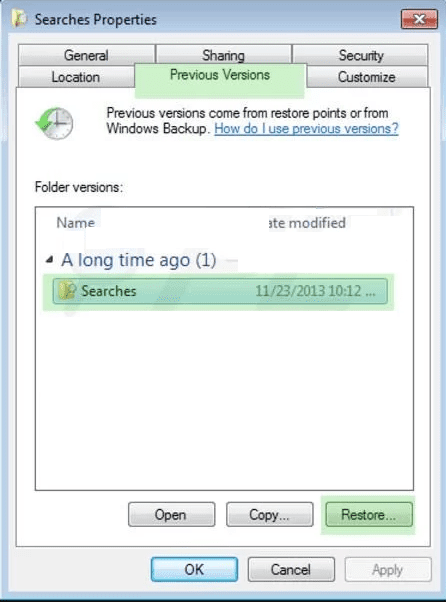
How to Restore Individual Encrypted File:
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
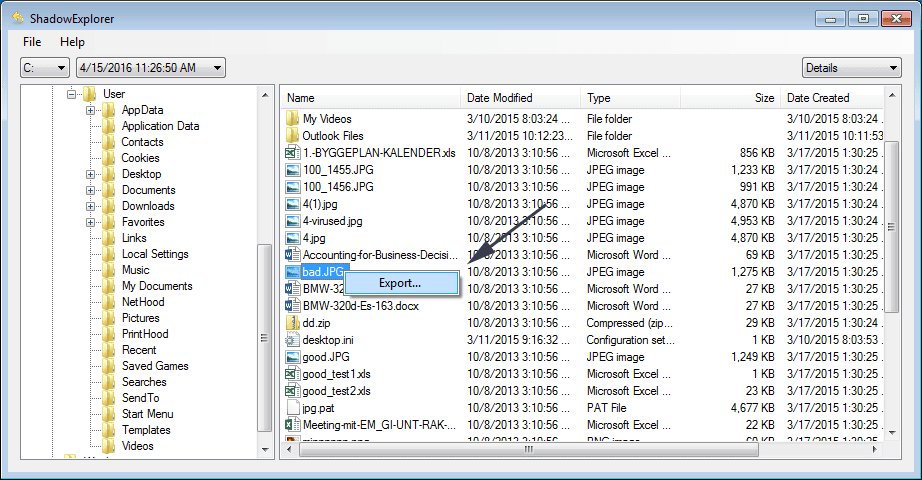
In order to access the files encrypted by Kelly (Leen) Ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like Kelly (Leen) Ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
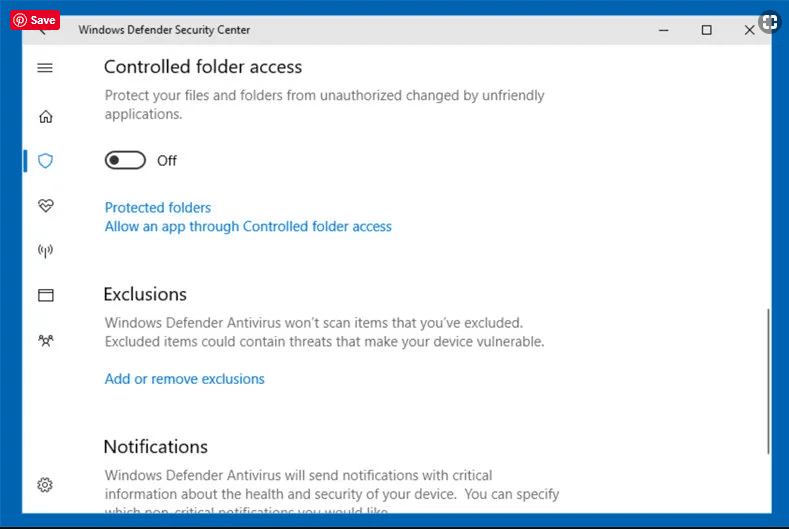
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by Kelly (Leen) Ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with Kelly (Leen) Ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove Kelly (Leen) Ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

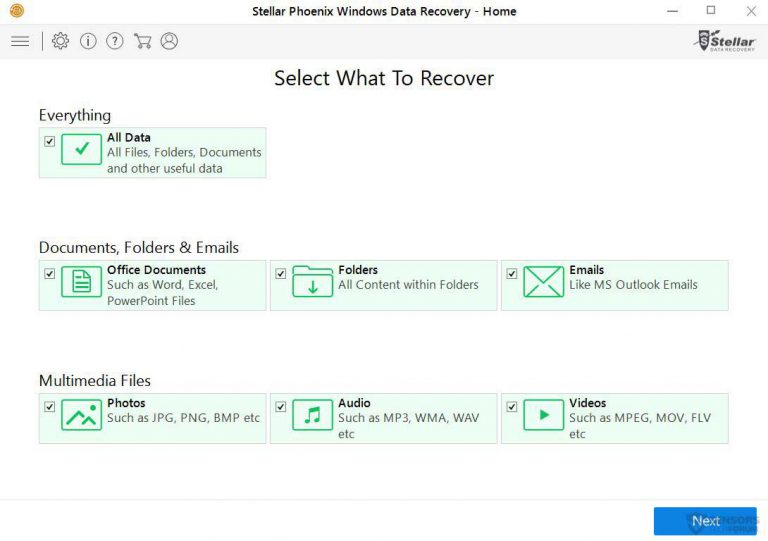
Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
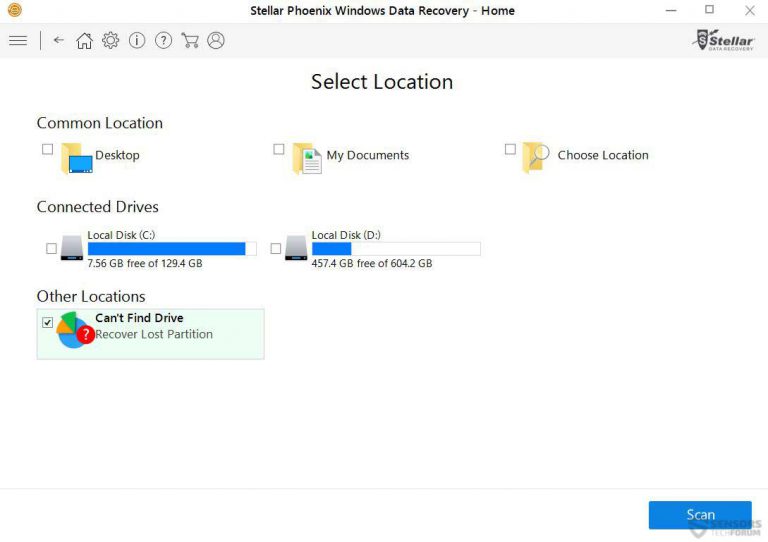
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
Kelly (Leen) Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.