Remove Exploit.GetShell Trojan From Mac OS
Easy Steps To Delete Exploit.GetShell
Exploit.GetShell is a heuristic detection by various antivirus suites that may refer to a Trojan virus. Multiple cybersecurity networks relate this detection with a Trojan, though, in fact, it can be associated to any other malware type, including ransomware, keylogger, spyware, adware, and etc. In most of the cases, this alert may be attended by high CPU usage, long system boot time, and software freezes. This pernicious trojan may indicate a newly released virus that displayed never-seen-before activities that an AV program identifies as spiteful. However, it may also denote a new variant of a virus that is already spreading in the wild.
Depth Analysis of Exploit.GetShell:
The criminals behind the Exploit.GetShell virus may try to start a multitude of vicious deeds, such as:
- compromise web browser’s settings in a way to trigger redirects to phishing websites;
- initiate tracking activities with an intention to collect confidential information, including credit card details, passwords, login data, etc.
- generate aggressive pop-ups, hyperlinks, banners, and another context that may expose a potential victim to dangerous viruses or offensive material;
- diminish the Mac system’s protection to open a backdoor for other malware threats;
- connect to remote servers and download infections without user’s awareness;
Exploit.GetShell can represent a variety of different threats, the goal of the virus might also differ. For example, it can steal sensitive data in the background, with the help of various functions, including screenshot taking, keylogging, etc. Unfortunately, such a virus generally works silently, complicating its termination if no security software is used.
Personal data is among the most desired attributes in the cyber-criminal world. The information can be sold on the dark web for revenue or leveraged to steal money from bank accounts and similar. Without a doubt, such activity can harm the infected users greatly, resulting in vast financial losses, as well as identity theft.
Nevertheless, this notorious trojan might have other goals, including crypto mining. This process helps cybercriminals to acquire digital currency, such as Bitcoin or Monero, by using a botnet of infected computers. In such a case, the infected users could experience lag, high usage of hardware (fan in particular), OS reboots, software crashes, and high CPU/GPU usage. And hence, instant removal of Exploit.GetShell is highly required.
How Does This Threat Intrude Your PC?
Although there are various tactics for malware distribution, the most common places where people get tricked into installing such malicious pieces of software are pirated software or freeware download websites, infected websites, and leaked email accounts.
Despite the fact that users are not attentive of a possible virus attack, the installation of Trojan, spyware or other malware is seldom possible with the user’s interference. In most of the cases, people are redirected to phishing websites or websites with hacked URLs after clicking on a questionable popup, hyperlink or visiting adult content web domains purposely.
The best piece of advice is to raise awareness about dangers online. Do not rely on freeware just because they are offered for free. Keep in mind that these sites get monetized in other ways, for example, receive commissions for distributing malware. To prevent all the damages caused by this Trojan, you are highly recommended to remove Exploit.GetShell from the Mac computer.
Summarize Information
Name– Exploit.GetShell
Category– Mac virus, Trojan, banking malware, password-stealing virus, spyware,
Description– Steals Mac users’ important data for advertising purposes and also to generate illicit income for the creators by misusing those details, Deactivates all the running security services of the infected device and drop more parasites in the machine as well as help the criminals to get access to system.
Symptoms– Slowness of system’s performance, fake error messages, security alerts, intrusive ads and pop-ups, unwanted redirects to questioning sites and so on.
Distribution– Spam email campaigns, malicious file downloads, P2P file sharing, and many more.
Removal– Manual and automatic guidelines as provided under this article
Special Offer (For Macintosh)
Exploit.GetShell can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Remove Files and Folders Related to Exploit.GetShell
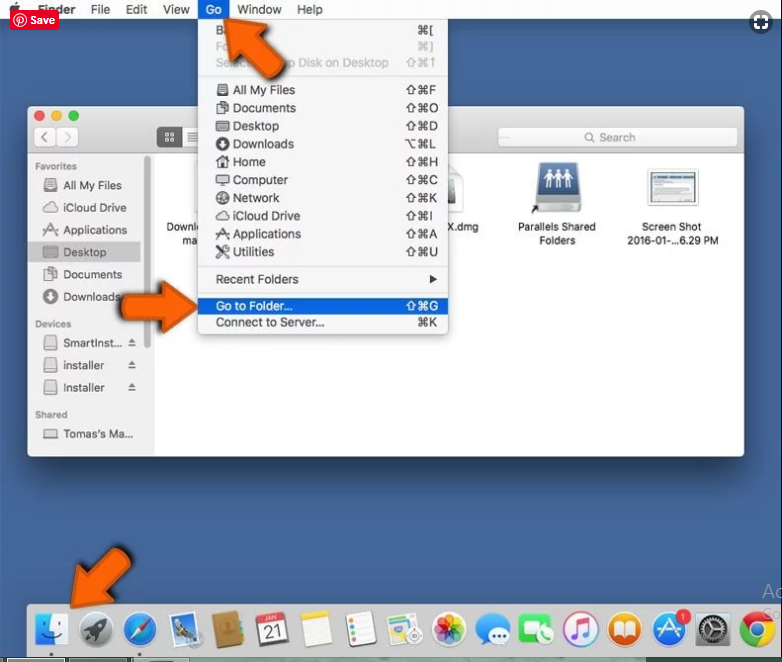
Open the “Menu” bar and click the “Finder” icon. Select “Go” and click on “Go to Folder…”
Step 1: Search the suspicious and doubtful malware generated files in /Library/LaunchAgents folder
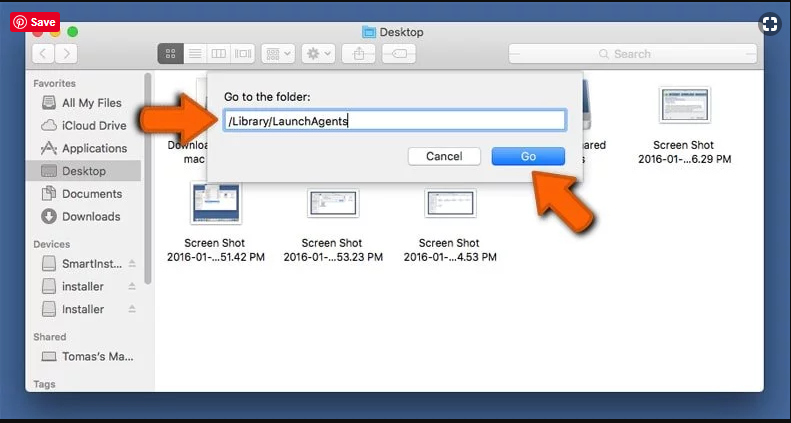
Type /Library/LaunchAgents in the “Go to Folder” option
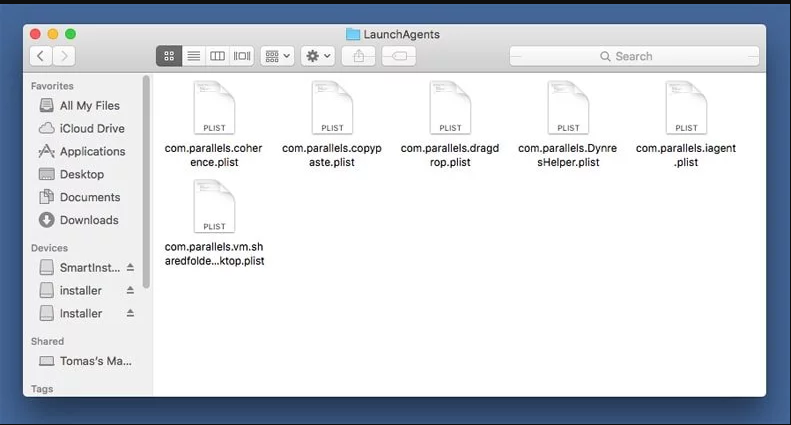
In the “Launch Agent” folder, search for all the files that you have recently downloaded and move them to “Trash”. Few of the examples of files created by browser-hijacker or adware are as follow, “myppes.download.plist”, “mykotlerino.Itvbit.plist”, installmac.AppRemoval.plist”, and “kuklorest.update.plist” and so on.
Step 2: Detect and remove the files generated by the adware in “/Library/Application” Support folder
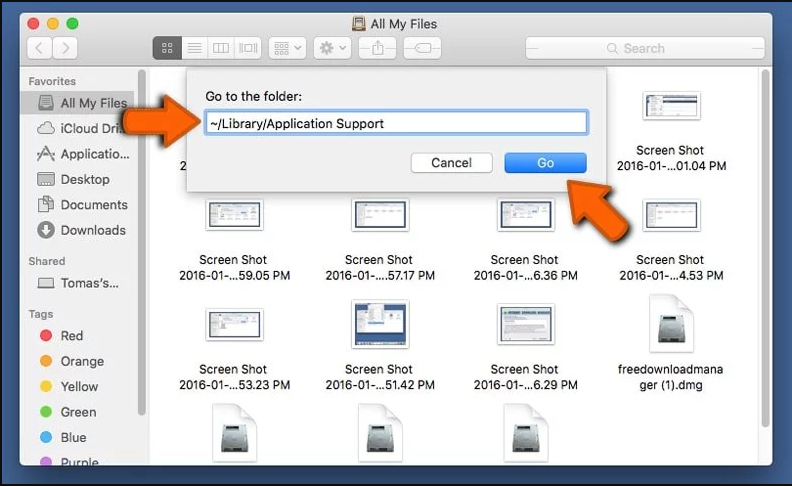
In the “Go to Folder..bar”, type “/Library/Application Support”
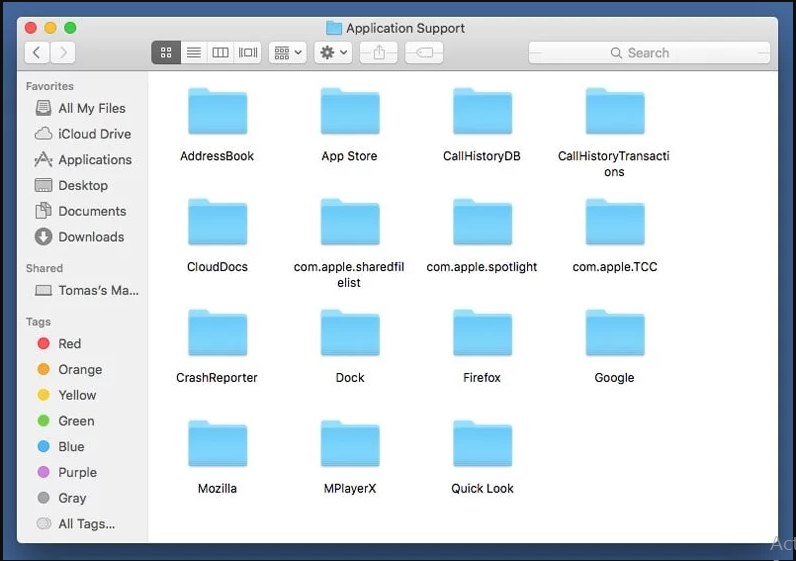
Search for any suspicious newly added folders in “Application Support” folder. If you detect any one of these like “NicePlayer” or “MPlayerX” then send them to “Trash” folder.
Step 3: Look for the files generated by malware in /Library/LaunchAgent Folder:
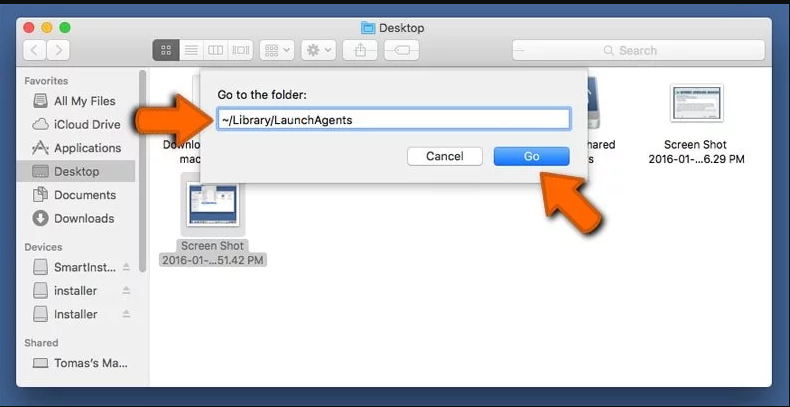
Go to Folder bar and type /Library/LaunchAgents
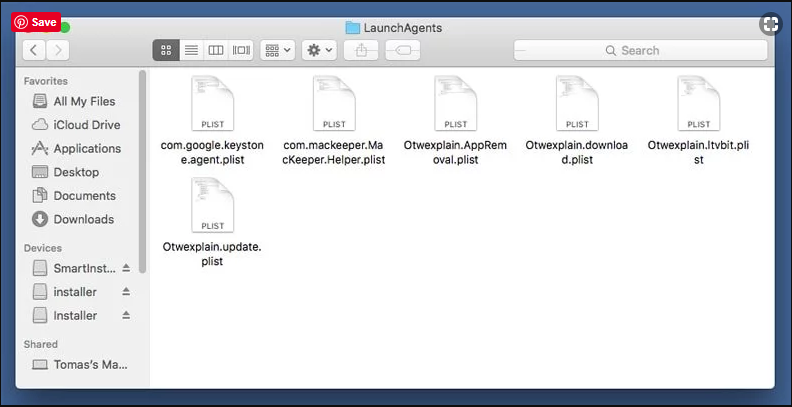
You are in the “LaunchAgents” folder. Here, you have to search for all the newly added files and move them to “Trash” if you find them suspicious. Some of the examples of suspicious files generated by malware are “myppes.download.plist”, “installmac.AppRemoved.plist”, “kuklorest.update.plist”, “mykotlerino.ltvbit.plist” and so on.
Step4: Go to /Library/LaunchDaemons Folder and search for the files created by malware
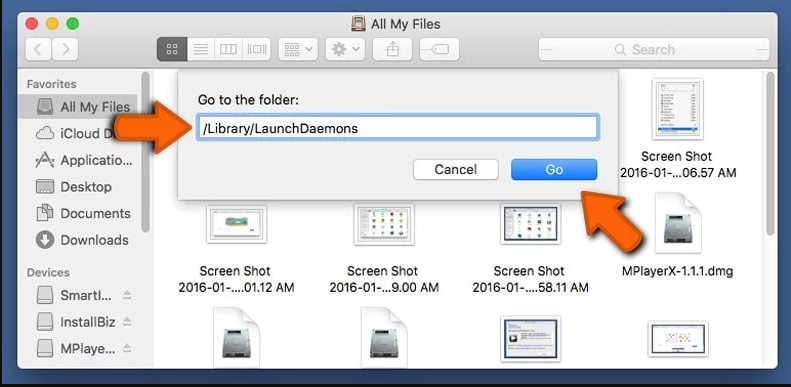
Type /Library/LaunchDaemons in the “Go To Folder” option
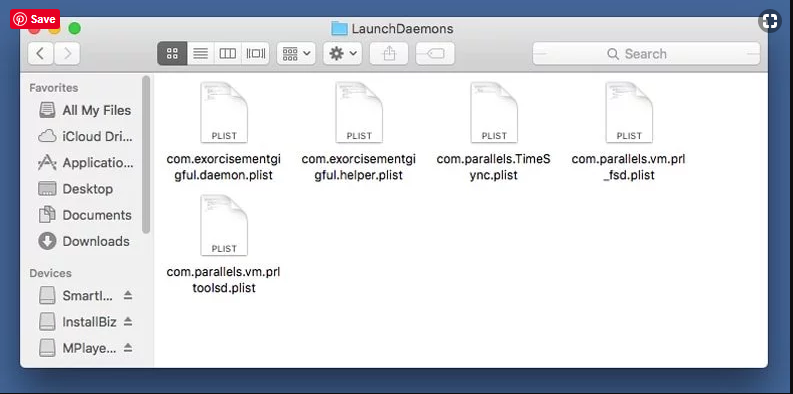
In the newly opened “LaunchDaemons” folder, search for any recently added suspicious files and move them to “Trash”. Examples of some of the suspicious files are “com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, “com.myppes.net-preference.plist”, “com.aoudad.net-preferences.plist” and so on.
Step 5: Use Combo Cleaner Anti-Malware and Scan your Mac PC
The malware infections could be removed from the Mac PC if you execute all the steps mentioned above in the correct way. However, it is always advised to be sure that your PC is not infected. It is suggested to scan the work-station with “Combo Cleaner Anti-virus”.
Special Offer (For Macintosh)
Exploit.GetShell can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Once the file gets downloaded, double click on combocleaner.dmg installer in the newly opened window. Next is to open the “Launchpad” and press on “Combo Cleaner” icon. It is advised to wait until “Combo Cleaner” updates the latest definition for malware detection. Click on “Start Combo Scan” button.
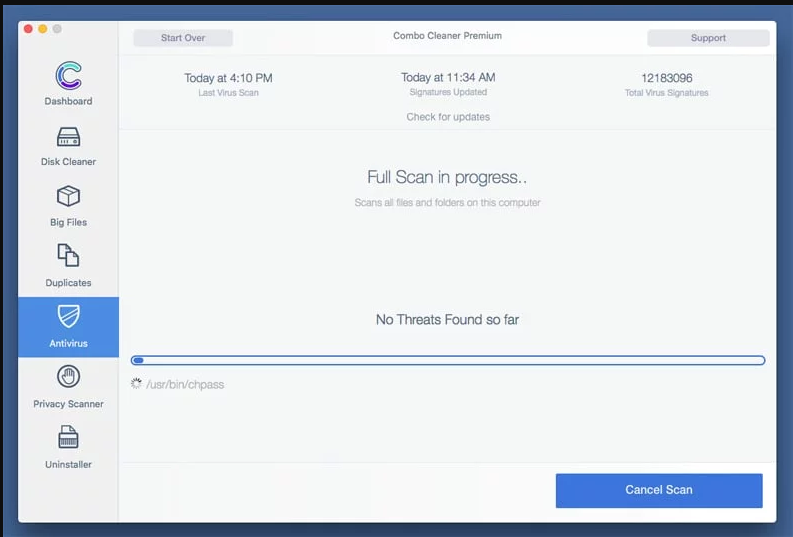
A depth scan of your Mac PC will be executed in order to detect malware. If the Anti-virus scan report says “no threat found” then you can continue with guide further. On the other hand, it is recommended to delete the detected malware infection before continuing.
Now the files and folders created by the adware is removed, you have to remove the rogue extensions from the browsers.
Remove Exploit.GetShell from Internet Browsers
Delete Doubtful and Malicious Extension from Safari
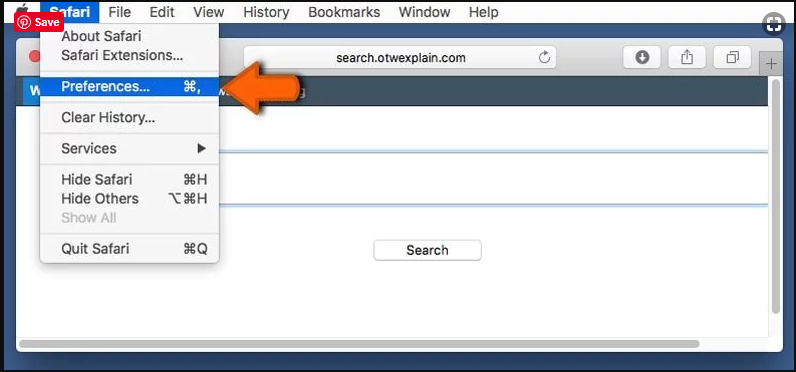
Go to “Menu Bar” and open “Safari” browser. Select “Safari” and then “Preferences”
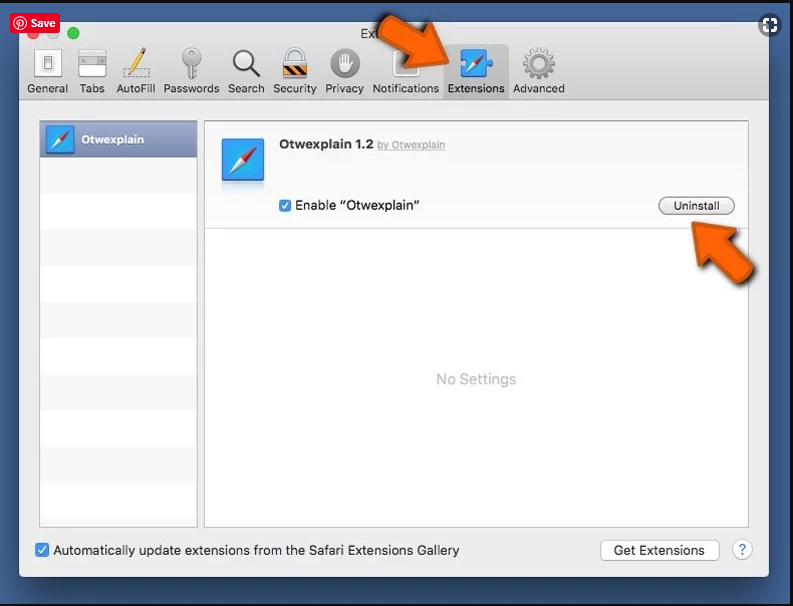
In the opened “preferences” window, select “Extensions” that you have recently installed. All such extensions should be detected and click the “Uninstall” button next to it. If you are doubtful then you can remove all the extensions from “Safari” browser as none of them are important for smooth functionality of the browser.
In case if you continue facing unwanted webpage redirections or aggressive advertisements bombarding, you can reset the “Safari” browser.
“Reset Safari”
Open the Safari menu and choose “preferences…” from the drop-down menu.
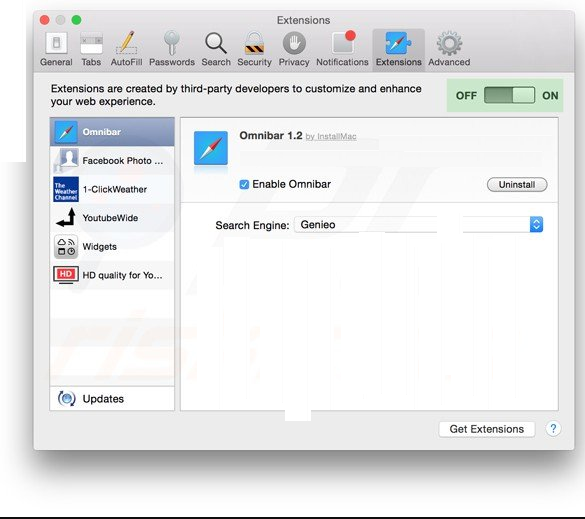
Go to the “Extension” tab and set the extension slider to “Off” position. This disables all the installed extensions in the Safari browser
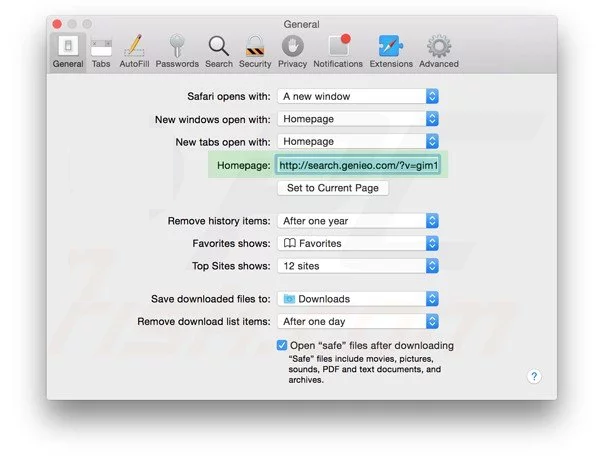
Next step is to check the homepage. Go to “Preferences…” option and choose “General” tab. Change the homepage to your preferred URL.
Also check the default search-engine provider settings. Go to “Preferences…” window and select the “Search” tab and select the search-engine provider that you want such as “Google”.
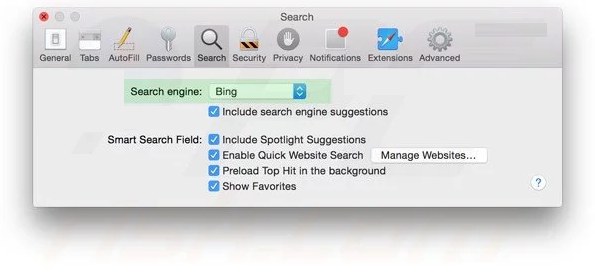
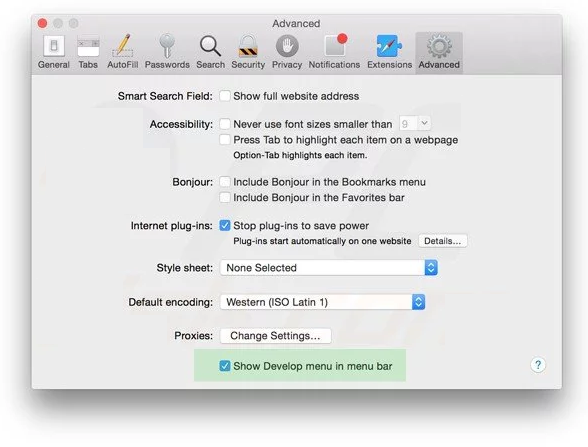
Next is to clear the Safari browser Cache- Go to “Preferences…” window and select “Advanced” tab and click on “Show develop menu in the menu bar.“
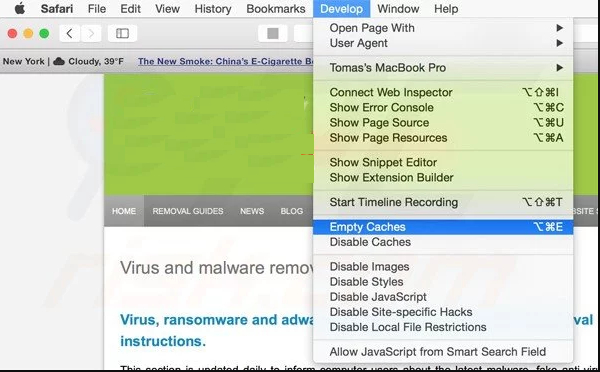
Go to “Develop” menu and select “Empty Caches”.
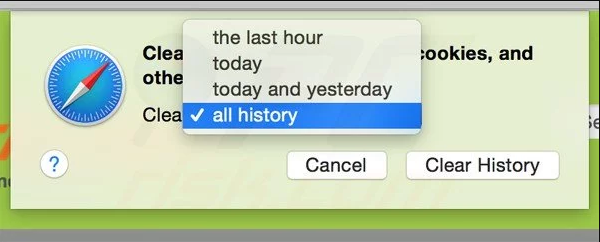
Remove website data and browsing history. Go to “Safari” menu and select “Clear History and Website Data”. Choose “all history” and then click on “Clear History”.
Remove Unwanted and Malicious Plug-ins from Mozilla Firefox
Delete Exploit.GetShell add-ons from Mozilla Firefox

Open the Firefox Mozilla browser. Click on the “Open Menu” present in the top right corner of the screen. From the newly opened menu, choose “Add-ons”.
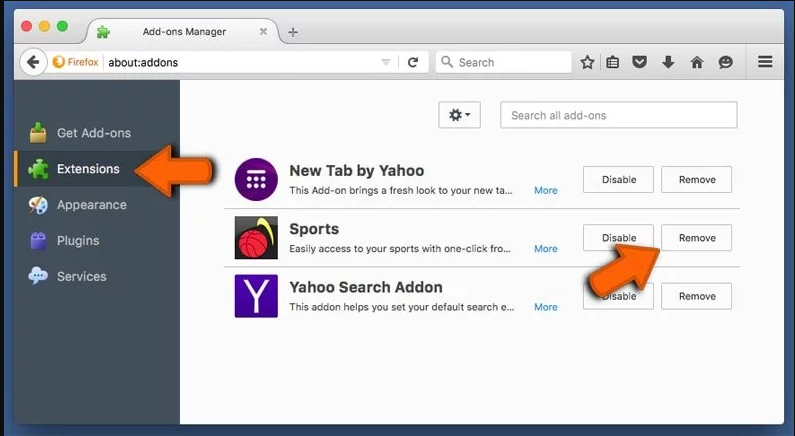
Go to “Extension” option and detect all the latest installed add-ons. Select each of the suspicious add-ons and click on “Remove” button next to them.
In case if you want to “reset” the Mozilla Firefox browser then follow the steps that has been mentioned below.
Reset Mozilla Firefox Settings
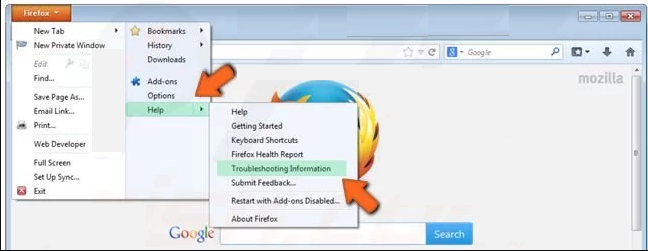
Open the Firefox Mozilla browser and click on “Firefox” button situated at the top left corner of the screen.

In the new menu, go to “Help” sub-menu and choose “Troubleshooting Information”
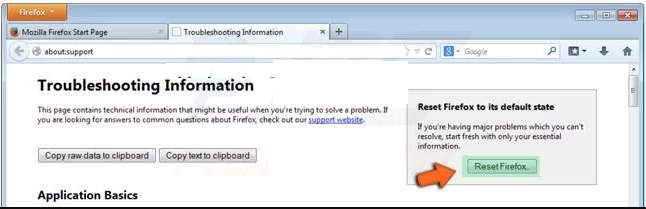
In the “Troubleshooting Information” page, click on “Reset Firefox” button.
Confirm that you want to reset the Mozilla Firefox settings to default by pressing on “Reset Firefox” option
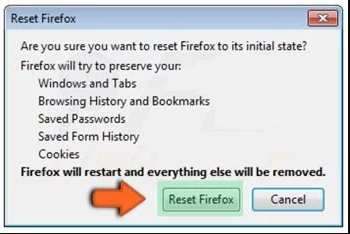
The browser will get restarted and the settings changes to factory default
Delete Unwanted and Malicious Extensions from Google Chrome
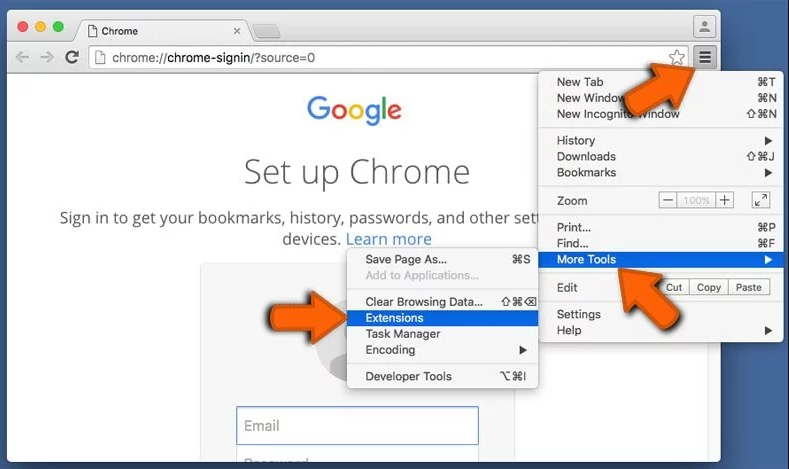
Open the chrome browser and click on “Chrome menu”. From the drop down option, choose “More Tools” and then “Extensions”.
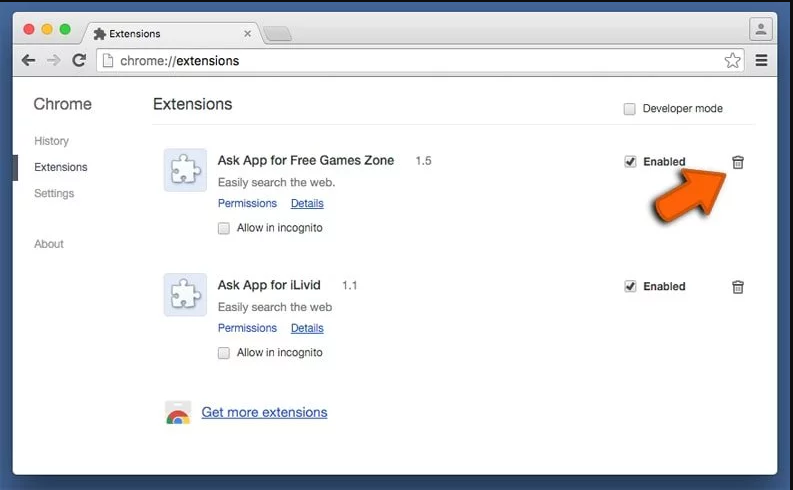
In the “Extensions” option, search for all the recently installed add-ons and extensions. Select them and choose “Trash” button. Any third-party extension is not important for the smooth functionality of the browser.
Reset Google Chrome Settings
Open the browser and click on three line bar at the top right side corner of the window.
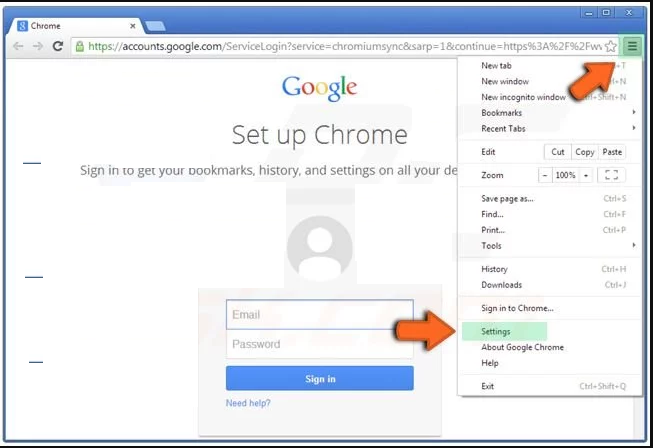
Go to the bottom of the newly opened window and select “Show advanced settings”.
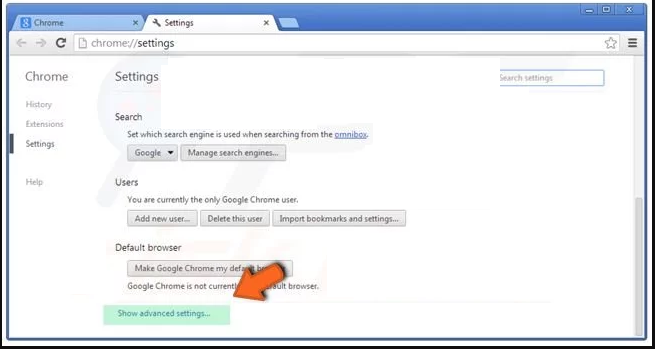
In the newly opened window, scroll down to the bottom and choose “Reset browser settings”
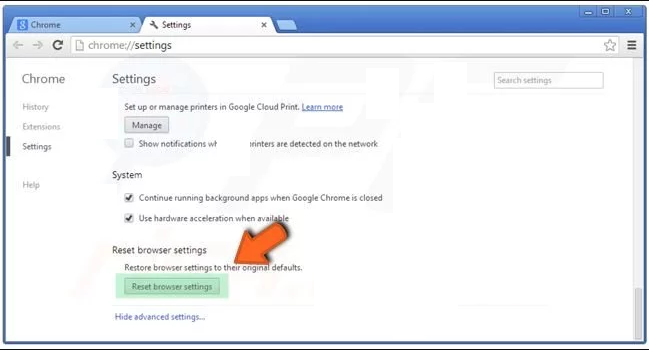
Click on the “Reset” button on the opened “Reset browser settings” window
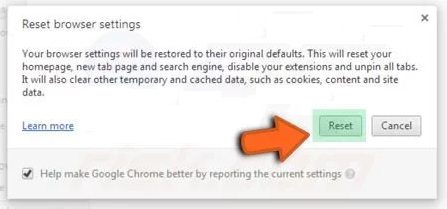
Restart the browser and the changes you get will be applied
The above mentioned manual process should be executed as it is mentioned. It is a cumbersome process and requires a lot of technical expertise. And hence it is advised for technical experts only. To be sure that your PC is free from malware, it is better that you scan the work-station with a powerful anti-malware tool. The automatic malware removal application is preferred because it doesn’t requires any additional technical skills and expertise.
Special Offer (For Macintosh)
Exploit.GetShell can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Download the application and execute it on the PC to begin the depth scanning. Once the scanning gets completed, it shows the list of all the files related to Exploit.GetShell. You can select such harmful files and folders and remove them immediately.



