How to Remove Cuckoo Malware (Mac)
In order to remove Cuckoo threat from your Mac OS X, it is very important that all its related entries and associated items are removed completely. It is strongly recommended to get rid of this malware as soon as possible. The manual removal process has been broadly discussed here. However, novice users are recommended to scan their PC with a powerful anti-malware tool and get rid of Cuckoo automatically.
Special Offer (For Macintosh)
Cuckoo can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Proper Guide For Advertising App Elimination
Cuckoo is a nasty kind of malware specifically made to target Mac computers. It’s like a spy that sneaks into your device and steals all sorts of important information. This malware has been around since at least 2024 and it’s been causing trouble by pretending to be something innocent, like a tool for downloading music from streaming sites.
Here’s how it works: Cuckoo malware hides inside what seems to be harmless software, like a Spotify music converter. When you install that software, you’re actually letting Cuckoo into your Mac. Usually, you’d just drag software into a folder to install it, but with Cuckoo, it tricks you into right-clicking and opening it instead.
Once it’s in, Cuckoo starts doing all kinds of bad stuff. It might ask you for your password, pretending it needs it for something innocent, but really, it’s just checking if your password works. If it does, that’s bad news because it means Cuckoo can do even more damage by getting more control over your Mac.
But that’s not all – Cuckoo malware is really sneaky. It checks where your Mac is located, and if it’s in certain places like Ukraine or Russia, it won’t do anything. But if you’re in a different location, it starts gathering information about your Mac, like what kind of hardware you have, what software you’re running, and even your username.
Once it has all that info, Cuckoo gets to work stealing things from your Mac. It can grab files from different folders, like your desktop or your downloads folder. It’s not picky – it’ll take anything it can find, like documents, pictures, or spreadsheets.
But it doesn’t stop there. Cuckoo malware can also dig into specific apps on your Mac, like your web browser or your email program. It looks for things like your browsing history, your saved passwords, and even your credit card details. That’s really scary because it means the hackers behind Cuckoo could steal your identity or your money.
And it gets worse – Cuckoo can even take screenshots of what’s on your screen, so it’s like someone is looking over your shoulder all the time. And because it can mute your computer’s volume, you won’t even hear it happening.
The problem with Cuckoo is that it’s always changing. The people who make it are always finding new ways to make it sneakier and more dangerous. So even if you think you’re safe now, there might be a new version of Cuckoo out there that’s even harder to spot.
So what can you do to protect yourself from Cuckoo? It’s a good idea to keep your Mac’s software up to date. That way, you’ll have the latest security patches to help keep Cuckoo out. And if you ever think your Mac might be infected with Cuckoo or any other kind of malware, don’t wait – get help from a professional right away.
In the end, dealing with malware like Cuckoo is a serious business. It can cause all kinds of problems, from stealing your personal information to messing up your computer. So stay vigilant and keep your Mac safe from harm.
Quick Glance |
| Name: Cuckoo |
| Class: Mac virus, Browser hijacker, adware |
|
Features: Alters the user’s browsing experience by changing the default search engine and homepage, displays unwanted ads, and redirects the user to malicious websites. |
| Danger level: Medium |
| Symptoms: The unwanted application can cause several adverse effects, such as displaying intrusive pop-up ads and slowing down internet browsing. The threat can manipulate the settings of an internet browser. This manipulation forces users to visit the hijacker’s website and conduct internet searches using their search engine. |
| Distribution: Browser hijackers or adware such as Cuckoo can spread through deceptive pop-up ads, free software installers that are bundled with malware, and fake Flash Player installers. |
| Removal: To remove the threat, scan your system with powerful Combo Cleaner anti-malware software |
What harms Cuckoo can cause?
Cuckoo is a type of malicious software that can take control of your web browser and modify its settings without your consent. Such apps are typically designed to redirect your web traffic to other sites, display unwanted advertisements, and collect your personal information. Browser hijackers can be very harmful, and can cause a wide range of problems for your computer and your privacy. Below, we will discuss some of the harms that Cuckoo can cause.
- Modify Your Browser Settings: It can modify your browser settings, such as your homepage, default search engine, and new tab page. This can be very frustrating, as it can take a long time to reset these settings back to their original state.
- Display Annoying Ads: This hijacking app often displays unwanted ads, pop-ups, and banners on your screen. These ads can be very annoying, and can even lead to more harmful content if you click on them. In some cases, the ads may even be used to trick you into downloading more malware.
- Redirect Your Web Traffic: It can redirect your web traffic to other sites, even if you didn’t intend to visit those sites. This can be very dangerous, as the sites you are redirected to may contain harmful content, such as malware, phishing scams, or other types of scams.
- Slow Down Your Computer: One of the most obvious harms of hijackers or adware like Cuckoo is that they can slow down your computer. This is because they are constantly running in the background, using up valuable system resources. This can cause your device to become sluggish, unresponsive, and even crash.
- Cause Browser Crashes: Cuckoo can also cause your browser to crash or freeze. This can be very frustrating, as it can cause you to lose any work you were doing, or even cause you to lose important data if you haven’t saved your work.
- Decrease Your Online Privacy: This undesired software piece can decrease your online privacy by tracking your browsing habits, collecting your personal information, and displaying unwanted ads. This can be very harmful, as it can expose you to identity theft, fraud, and other types of cybercrime.
In short, Cuckoo can cause a wide range of harms to your device and your privacy. Therefore, it is important to take steps to protect your computer from this hijacking application, such as using antivirus software, keeping your browser and operating system up to date.
Is Cuckoo a dangerous virus?
Cuckoo is a type of malware that can cause a lot of unkind issues inside the compromised systems. While many don’t consider it as a destructive virus in the sense that it is not intended to damage the device, it can be a nuisance and potentially compromise the user’s online security. Additionally, it may indirectly expose their system to more dangerous form of viruses and malware.
Browser hijackers or adware can make your computer more vulnerable to other types of attacks. This is because they often disable your antivirus software, firewall, and other security measures that are designed to protect your system from malware and other types of attacks.
Cuckoo can also be used to install other types of malware on your computer, such as adware, spyware, and even ransomware. These types of malware can cause even more harm, such as stealing your files, encrypting them, and demanding a ransom to unlock them.
In addition to that, such browser-based infections are often designed to collect users’ personal data, such as their browsing history, search queries, and even their login credentials. This information can be used for identity theft, fraud, and other malicious activities.
For these reasons, Cuckoo can still be considered a dangerous computer virus, and must be eliminated from the system as early as possible.
Cuckoo Redirection Leads to Unsafe Sites
The redirection chain triggered by Cuckoo may force the browser to send the user to a variety of different webpages. Nonetheless, it’s pertinent to note that most of the websites it sends people to are malicious and even dangerous and may pose a serious threat to the device and the browser. This undesired software piece may take users to following sites:
Tech Support Scam Sites

Many people are falling victim to tech support scam websites that have become increasingly widespread. These sites often imitate the appearance of legitimate operating system error messages, making it difficult for individuals to discern whether the message is genuine or a scam. As a result, users are easily fooled into giving scammers access to their personal information or paying for unnecessary and expensive services.
Unsafe Dating Website
Cuckoo pop-ups may lead you to dubious dating sites that are entirely controlled by robots. Such websites often display deceptive notifications and pop-ups that mislead users into believing that they have multiple chat requests or messages waiting for them. These false alerts may be designed to look convincing and may even use persuasive language to create a sense of urgency, tricking users into clicking on them. In reality, these notifications are usually a tactic employed by scammers to lure individuals into interacting with their fraudulent websites or downloading malicious software.
Websites Showing Fake Virus Alert:
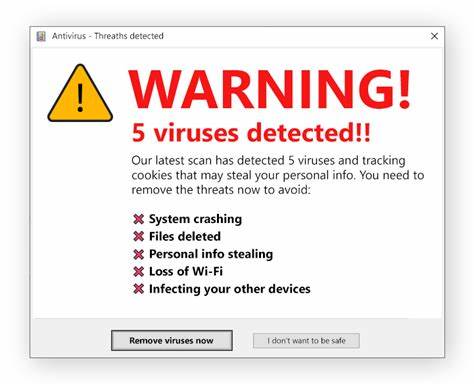
These sites tend to display fake security alerts claiming that users’ PCs are infected with several viruses. They are designed to trick visitors into believing that they are in trouble of having their computers infected and to compel them into taking immediate actions. Scammers behind these deceptions aim to mislead users into downloading and installing malicious software or extracting money from them for useless services.
Drive-by Download Malware Sites
Users may also be taken to drive-by download websites, which is a type of cyberattack in which malware is automatically downloaded to a computer without the user’s knowledge or consent. Drive-by downloads are a serious security threat, as they can result in the installation of viruses, spyware, or other types of malicious software, which can compromise the security and privacy of your computer and personal data.
Fake Giveaway Survey Websites
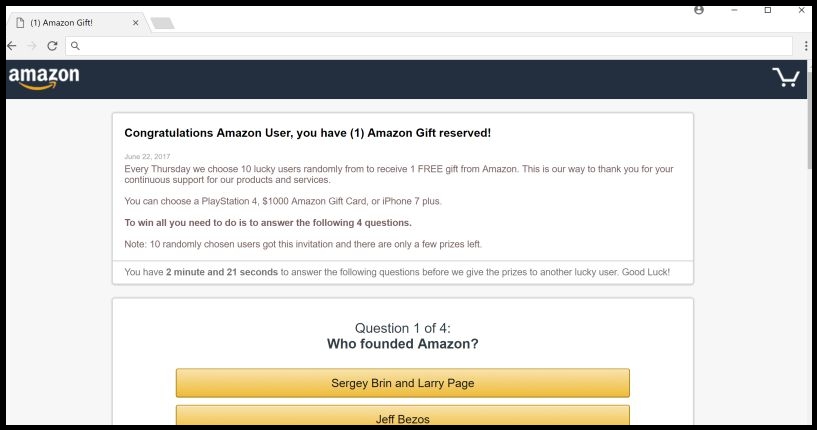
These dubious sites tend to promote bogus surveys aiming to trick users into stealing their personal information such as their credit card details, banking credentials, etc. This sort of information could later be used for various malicious purposes and may lead to a number of unpleasant issues.
Unsafe Pop-Ups Causes Online Scam

Unsafe pop-ups are a common method used by online scammers to deceive unsuspecting internet users. These pop-ups can appear on users’ browser when their system is contaminated with an unwanted application; they visit a website or click on a link, and often try to convince them to take some action, such as downloading a program or providing personal information.
Once users interact with the pop-up, they can be redirected to a fraudulent website that looks legitimate, but is actually designed to steal their sensitive data or money. For example, a Cuckoo pop-up might claim that users’ device is infected with a virus and prompt them to download software that is actually malware.
Other pop-ups might offer a prize or gift in exchange for the user’s personal information, such as their name, address, and credit card number. Once the scammers have this information, they can employ it to make unauthorized purchases or commit identity theft. This can lead to serious privacy issues, identity fraud, high-risk system infections, and even significant monetary losses.
How did Cuckoo Attack my device?
Browser-based parasites like Cuckoo can infect PC systems through a number of deceptive ways. Below are some key points on how these types of malware can sneak into the targeted devices:
-
- Bundled Software: Adware and browser hijackers are often bundled with legitimate software that users download from the internet. This could be a free utility or game that is made available for download from a website. The site may offer the program for free, but it will be bundled with additional software that the user may not be aware of. When the user download and installs the program, the bundled software will also be installed on their system without their knowledge or consent. This bundled software may include a browser hijacker or adware that will modify the user’s web browser settings.
- Malicious Websites: Cuckoo can also spread through malicious websites. These sites are designed to trick users into downloading and installing software or visiting other harmful web places. People visit a malicious website often by clicking on a link in a spam email, a social post, or a search engine result. The site contains code that automatically downloads and installs the undesired software piece onto the users’ computer without their knowledge or approval.
- Exploits: Other way through which PUPs like Cuckoo can enter the computer systems is exploits. Exploits are vulnerabilities in software that can be exploited by attackers to gain unauthorized access to a computer system or to install malware or adware. Threat actors find a vulnerability in the user’s web browser, operating system, or a plugin, such as Java or Flash. After that, they create a website that contains code that exploits the vulnerability when the user visits the site. The exploit downloads and installs the parasite onto the PC without users’ awareness or consent.
- Social Engineering: Cuckoo can make its way into the device through social engineering as well, which is a technique used by hackers to trick users into downloading and installing malware. These internet criminals create a fake advertisement or pop-up message that claims the user needs to update their software or install a new plugin to view content on a website. The pop-up message may contain a convincing message, such as “Your Flash Player is out of date, please click here to update it” or “Your computer is infected, click here to remove the virus.” When users click on the pop-up message, they end up downloading and installing the unwanted program without realizing it.
Special Offer (For Macintosh)
Cuckoo can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Remove Files and Folders Related to Cuckoo
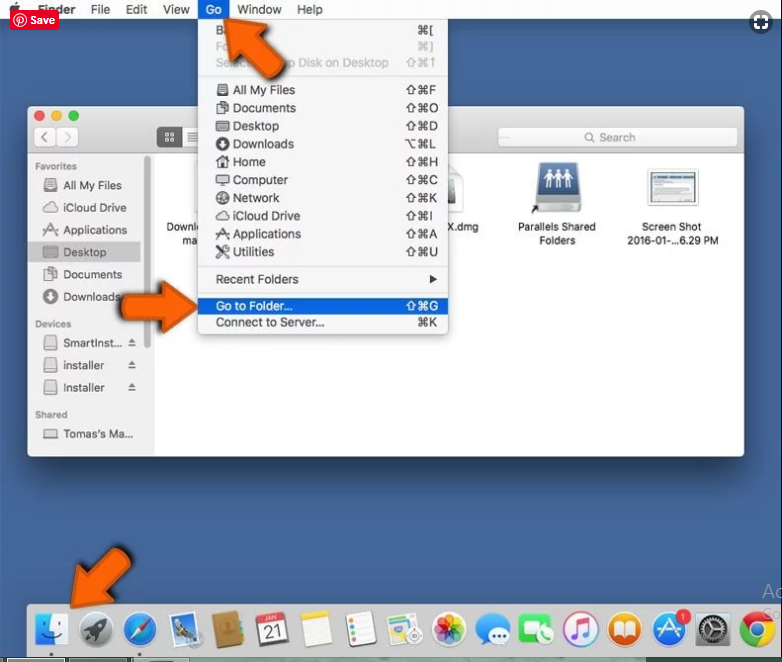
Open the “Menu” bar and click the “Finder” icon. Select “Go” and click on “Go to Folder…”
Step 1: Search the suspicious and doubtful malware generated files in /Library/LaunchAgents folder
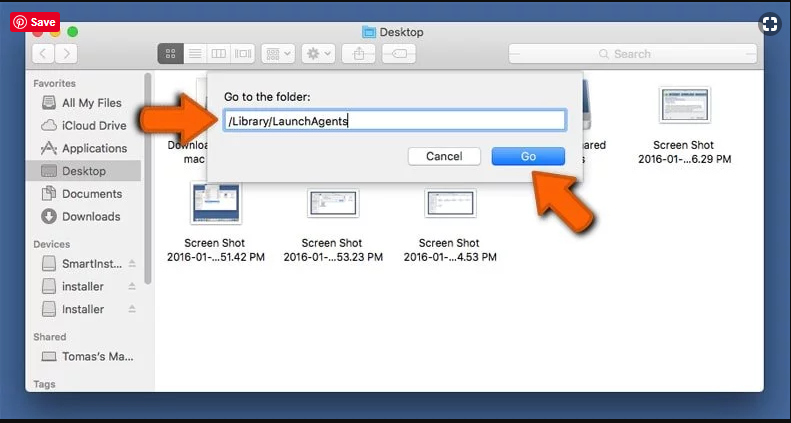
Type /Library/LaunchAgents in the “Go to Folder” option
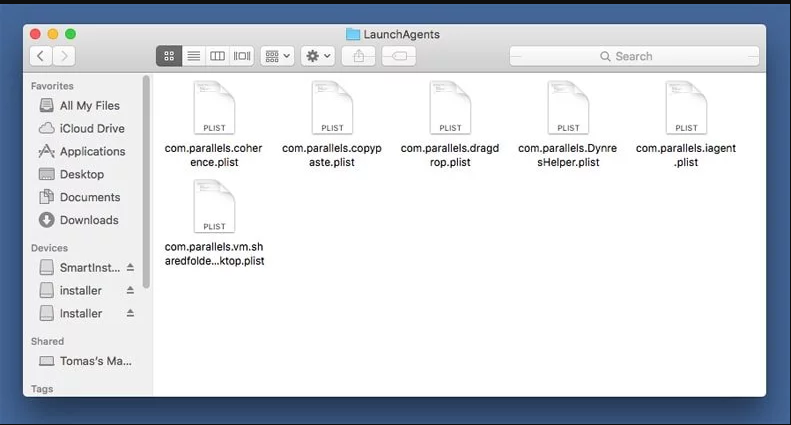
In the “Launch Agent” folder, search for all the files that you have recently downloaded and move them to “Trash”. Few of the examples of files created by browser-hijacker or adware are as follow, “myppes.download.plist”, “mykotlerino.Itvbit.plist”, installmac.AppRemoval.plist”, and “kuklorest.update.plist” and so on.
Step 2: Detect and remove the files generated by the adware in “/Library/Application” Support folder
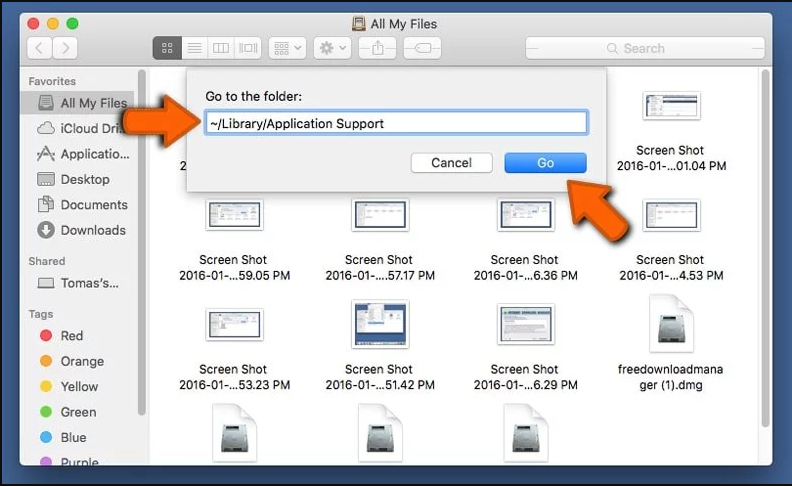
In the “Go to Folder..bar”, type “/Library/Application Support”
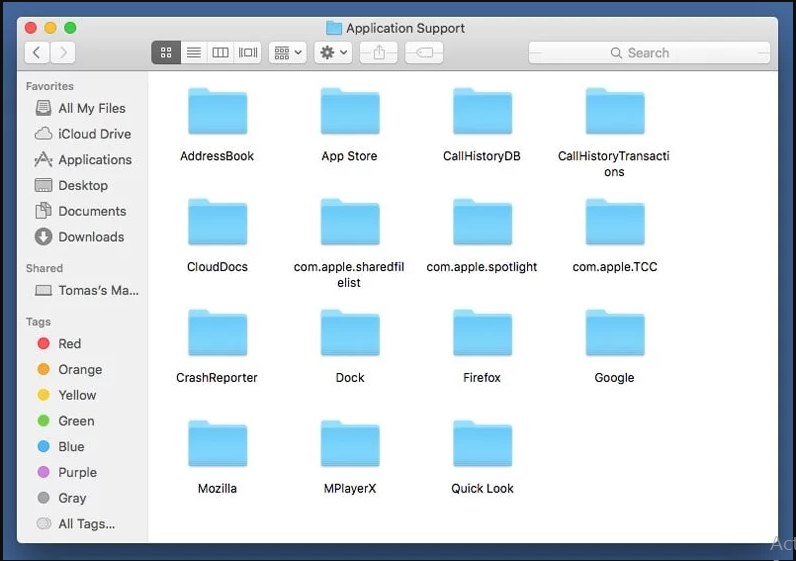
Search for any suspicious newly added folders in “Application Support” folder. If you detect any one of these like “NicePlayer” or “MPlayerX” then send them to “Trash” folder.
Step 3: Look for the files generated by malware in /Library/LaunchAgent Folder:
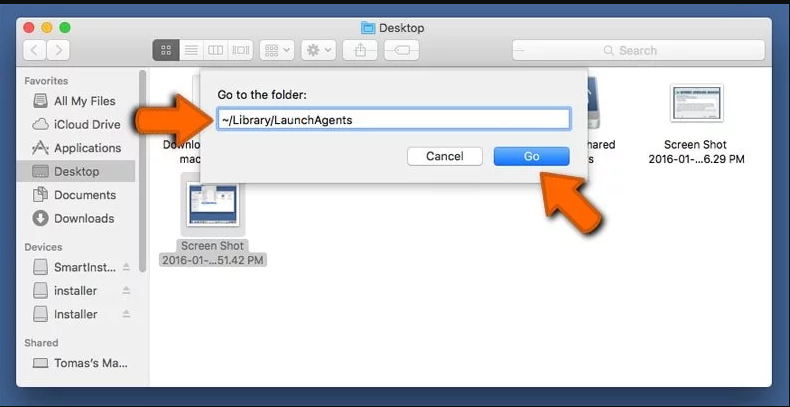
Go to Folder bar and type /Library/LaunchAgents
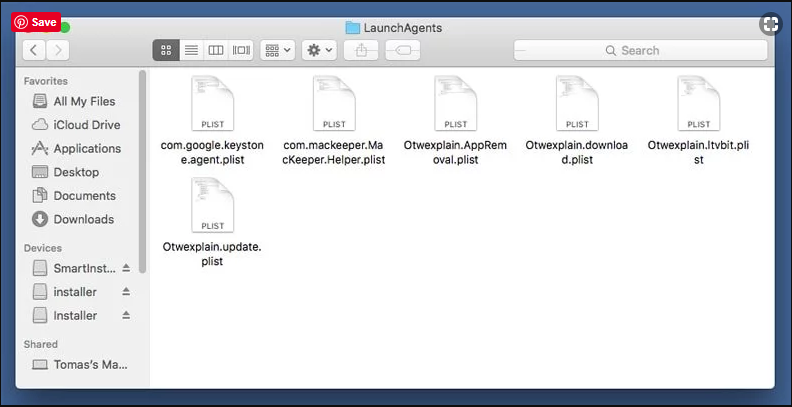
You are in the “LaunchAgents” folder. Here, you have to search for all the newly added files and move them to “Trash” if you find them suspicious. Some of the examples of suspicious files generated by malware are “myppes.download.plist”, “installmac.AppRemoved.plist”, “kuklorest.update.plist”, “mykotlerino.ltvbit.plist” and so on.
Step4: Go to /Library/LaunchDaemons Folder and search for the files created by malware
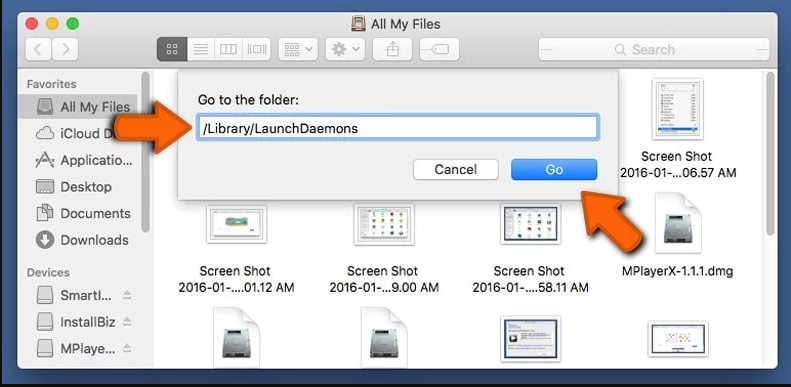
Type /Library/LaunchDaemons in the “Go To Folder” option
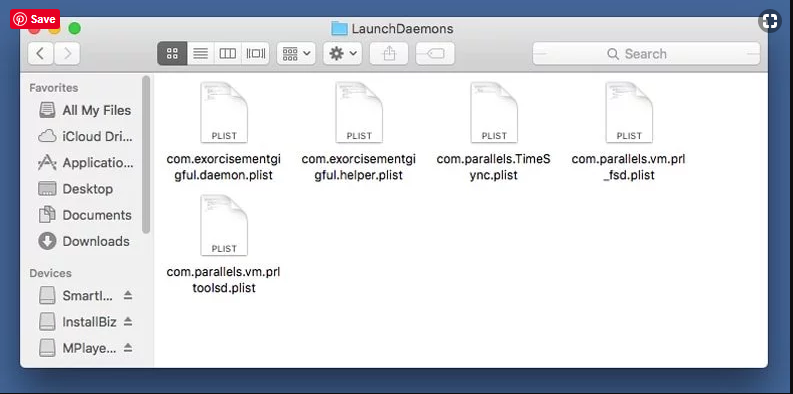
In the newly opened “LaunchDaemons” folder, search for any recently added suspicious files and move them to “Trash”. Examples of some of the suspicious files are “com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, “com.myppes.net-preference.plist”, “com.aoudad.net-preferences.plist” and so on.
Step 5: Use Combo Cleaner Anti-Malware and Scan your Mac PC
The malware infections could be removed from the Mac PC if you execute all the steps mentioned above in the correct way. However, it is always advised to be sure that your PC is not infected. It is suggested to scan the work-station with “Combo Cleaner Anti-virus”.
Special Offer (For Macintosh)
Cuckoo can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Once the file gets downloaded, double click on combocleaner.dmg installer in the newly opened window. Next is to open the “Launchpad” and press on “Combo Cleaner” icon. It is advised to wait until “Combo Cleaner” updates the latest definition for malware detection. Click on “Start Combo Scan” button.
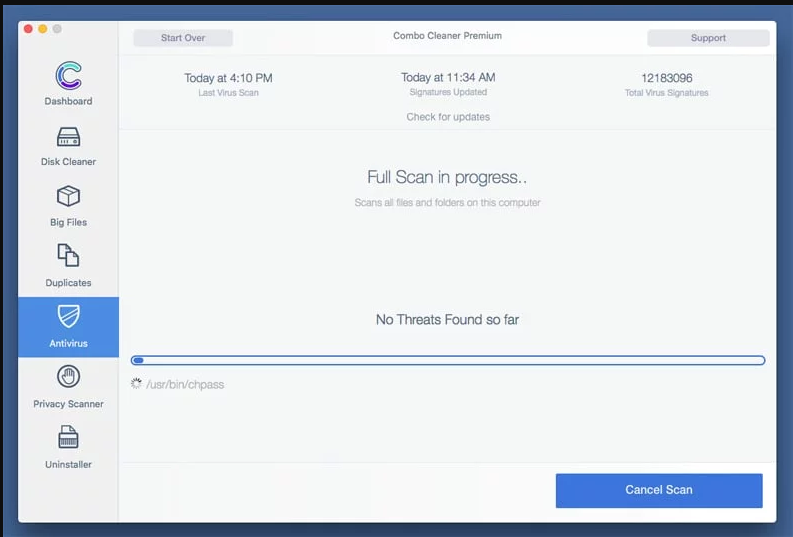
A depth scan of your Mac PC will be executed in order to detect malware. If the Anti-virus scan report says “no threat found” then you can continue with guide further. On the other hand, it is recommended to delete the detected malware infection before continuing.
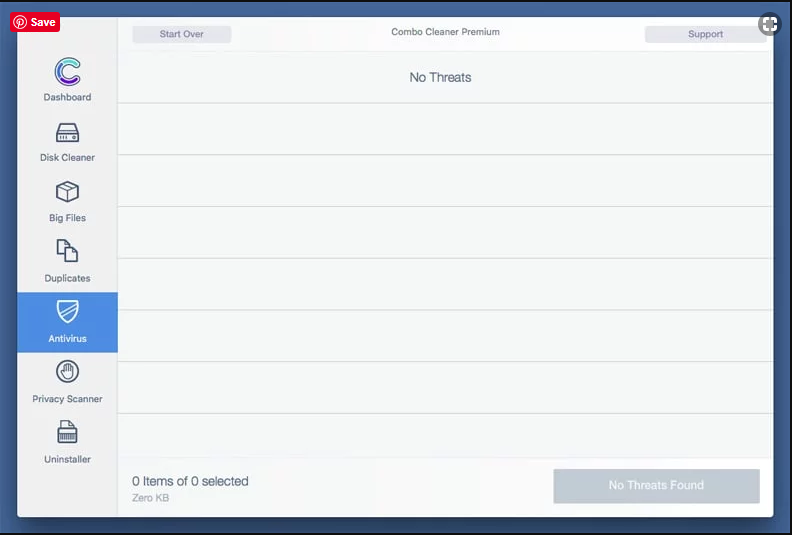
Now the files and folders created by the adware is removed, you have to remove the rogue extensions from the browsers.
Remove Cuckoo from Internet Browsers
Delete Doubtful and Malicious Extension from Safari
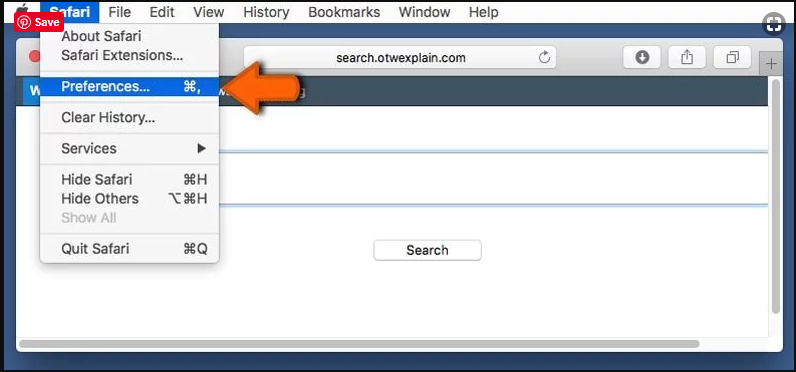
Go to “Menu Bar” and open “Safari” browser. Select “Safari” and then “Preferences”
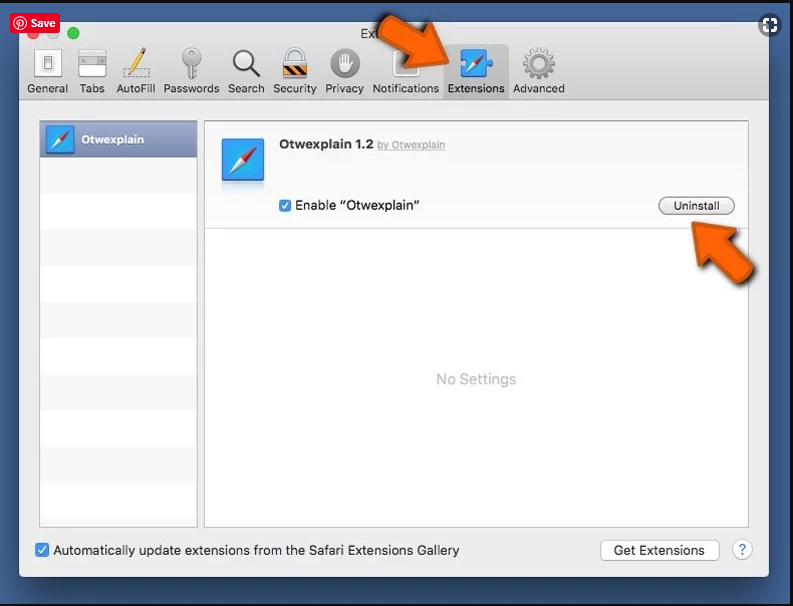
In the opened “preferences” window, select “Extensions” that you have recently installed. All such extensions should be detected and click the “Uninstall” button next to it. If you are doubtful then you can remove all the extensions from “Safari” browser as none of them are important for smooth functionality of the browser.
In case if you continue facing unwanted webpage redirections or aggressive advertisements bombarding, you can reset the “Safari” browser.
“Reset Safari”
Open the Safari menu and choose “preferences…” from the drop-down menu.
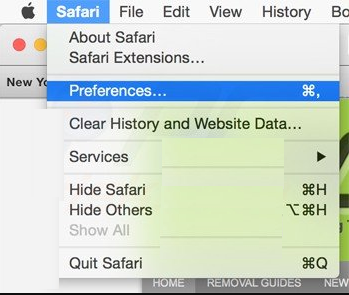
Go to the “Extension” tab and set the extension slider to “Off” position. This disables all the installed extensions in the Safari browser
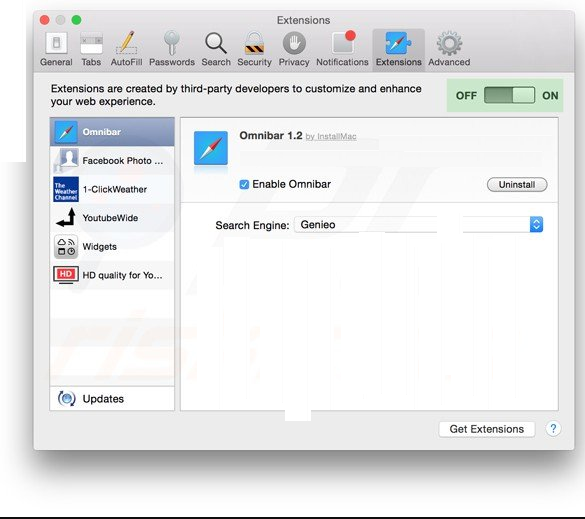
Next step is to check the homepage. Go to “Preferences…” option and choose “General” tab. Change the homepage to your preferred URL.
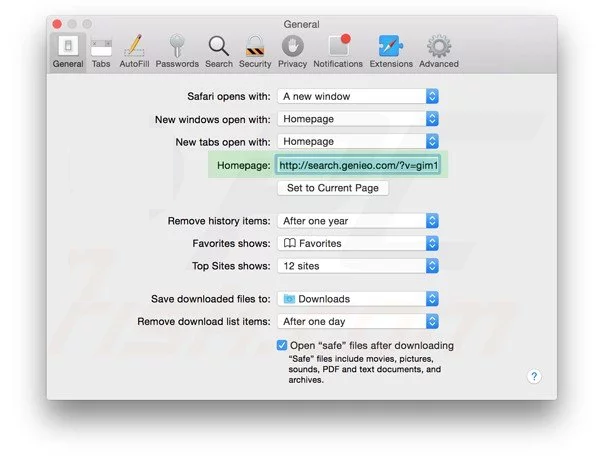
Also check the default search-engine provider settings. Go to “Preferences…” window and select the “Search” tab and select the search-engine provider that you want such as “Google”.
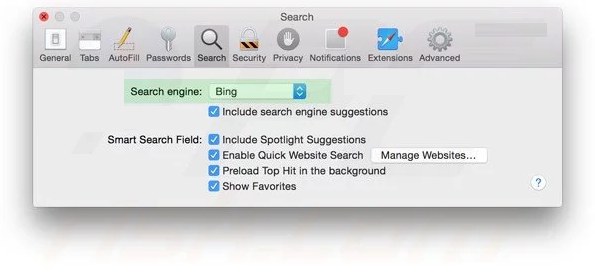
Next is to clear the Safari browser Cache- Go to “Preferences…” window and select “Advanced” tab and click on “Show develop menu in the menu bar.“
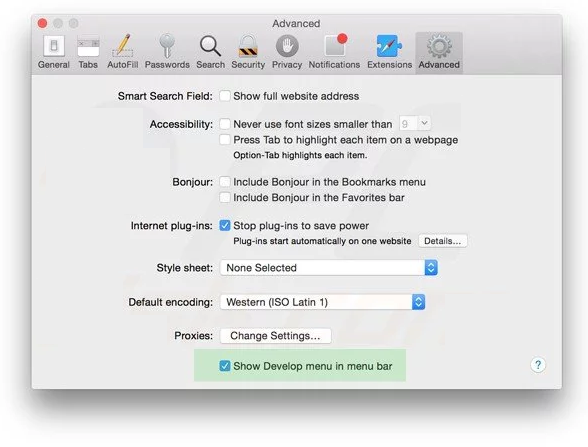
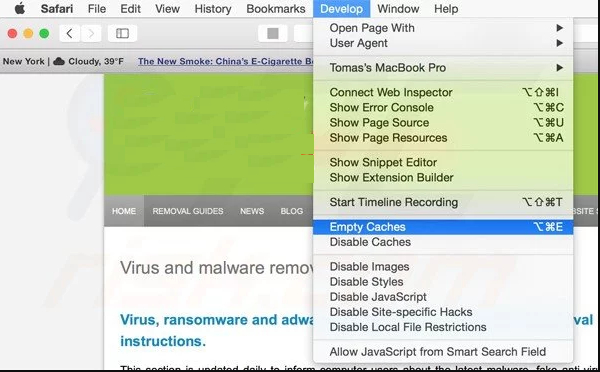
Go to “Develop” menu and select “Empty Caches”.
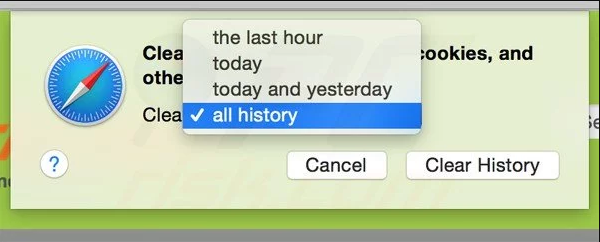
Remove website data and browsing history. Go to “Safari” menu and select “Clear History and Website Data”. Choose “all history” and then click on “Clear History”.
Remove Unwanted and Malicious Plug-ins from Mozilla Firefox
Delete Cuckoo add-ons from Mozilla Firefox

Open the Firefox Mozilla browser. Click on the “Open Menu” present in the top right corner of the screen. From the newly opened menu, choose “Add-ons”.
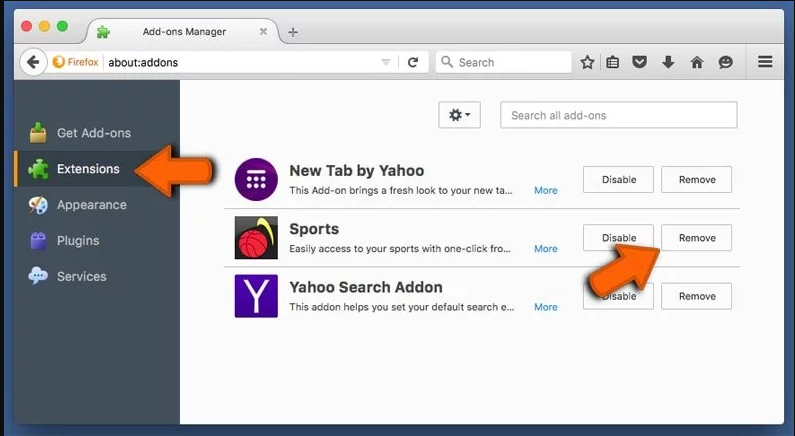
Go to “Extension” option and detect all the latest installed add-ons. Select each of the suspicious add-ons and click on “Remove” button next to them.
In case if you want to “reset” the Mozilla Firefox browser then follow the steps that has been mentioned below.
Reset Mozilla Firefox Settings
Open the Firefox Mozilla browser and click on “Firefox” button situated at the top left corner of the screen.

In the new menu, go to “Help” sub-menu and choose “Troubleshooting Information”
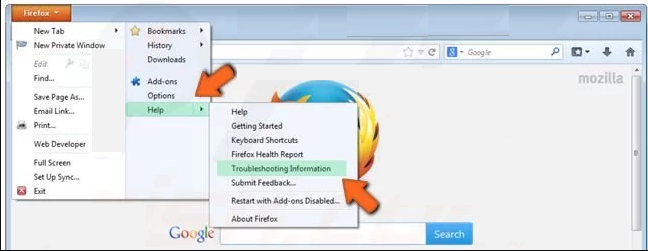
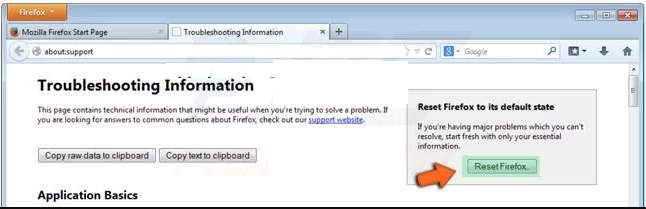
In the “Troubleshooting Information” page, click on “Reset Firefox” button.
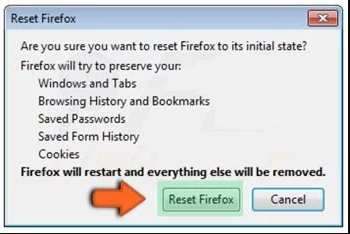
Confirm that you want to reset the Mozilla Firefox settings to default by pressing on “Reset Firefox” option
The browser will get restarted and the settings changes to factory default
Delete Unwanted and Malicious Extensions from Google Chrome
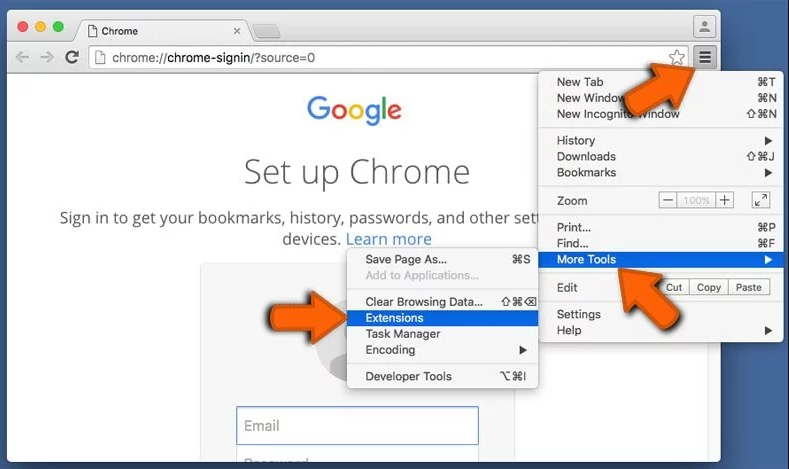
Open the chrome browser and click on “Chrome menu”. From the drop down option, choose “More Tools” and then “Extensions”.
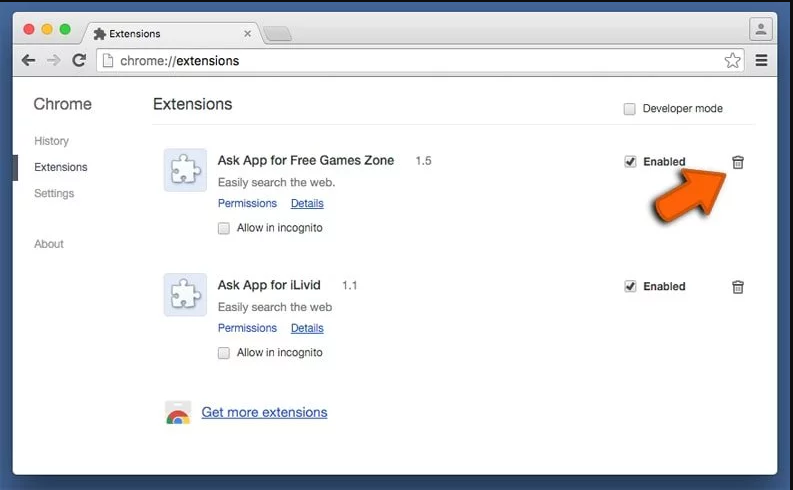
In the “Extensions” option, search for all the recently installed add-ons and extensions. Select them and choose “Trash” button. Any third-party extension is not important for the smooth functionality of the browser.
Reset Google Chrome Settings
Open the browser and click on three line bar at the top right side corner of the window.
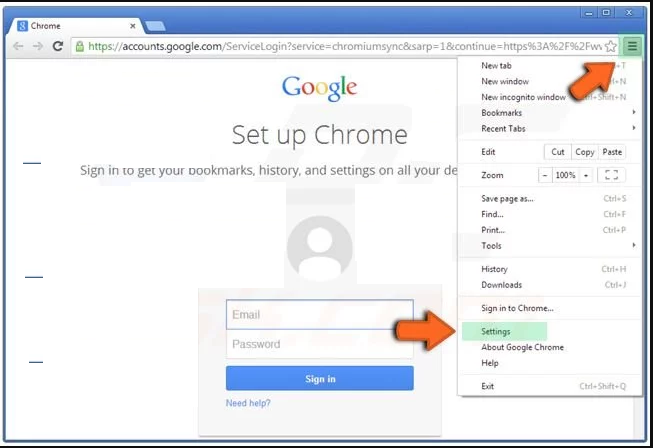
Go to the bottom of the newly opened window and select “Show advanced settings”.
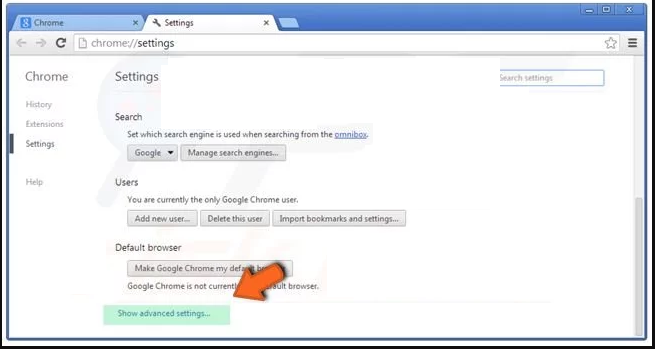
In the newly opened window, scroll down to the bottom and choose “Reset browser settings”
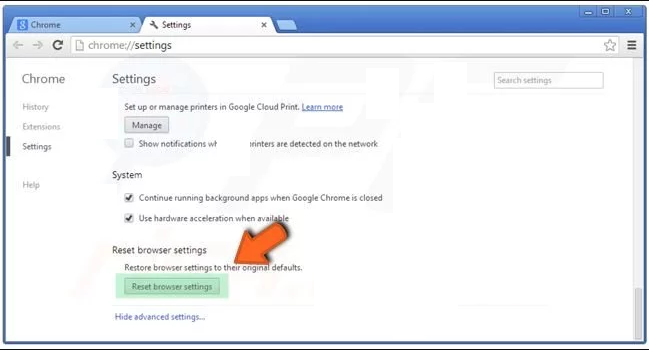
Click on the “Reset” button on the opened “Reset browser settings” window
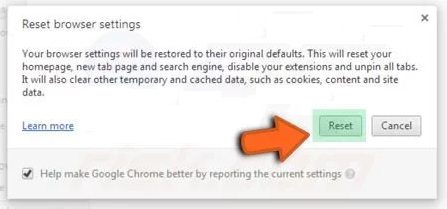
Restart the browser and the changes you get will be applied
The above mentioned manual process should be executed as it is mentioned. It is a cumbersome process and requires a lot of technical expertise. And hence it is advised for technical experts only. To be sure that your PC is free from malware, it is better that you scan the work-station with a powerful anti-malware tool. The automatic malware removal application is preferred because it doesn’t requires any additional technical skills and expertise.
Special Offer (For Macintosh)
Cuckoo can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Download the application and execute it on the PC to begin the depth scanning. Once the scanning gets completed, it shows the list of all the files related to Cuckoo. You can select such harmful files and folders and remove them immediately.
How to prevent Cuckoo infection?
As soon as Cuckoo infiltrates the PC system, it starts carrying out malicious activities in the background and may lead to a number of unpleasant issues. To avoid getting infected with such browser-based pests, below are some steps you can take:
- Download software from reputable sources: Only download software from reputable websites, such as the official page of the software vendor or well-known download portals. Avoid downloading software from third-party websites or peer-to-peer networks, as these are often sources of bundled adware.
- Pay attention during the installation process: When installing software, pay attention to each step of the installation process. Look for the checkboxes that may indicate the installation of additional software, such as adware or browser extensions. Uncheck these boxes if you don’t want to install the additional software.
- Choose custom installation: During the installation process, choose the custom installation option instead of the default or express installation. This will allow you to select which components to install and to opt-out of installing any bundled adware or other unwanted software.
- Read the End User License Agreement (EULA): Read the EULA carefully before installing any software. Look for clauses that may allow the installation of additional software or adware like Cuckoo. If EULA contains such clauses, reconsider installing the software.
- Use a reputable web browser: Choose a reputable web browser, such as Google Chrome or Mozilla Firefox, and keep it up-to-date with the latest security patches.
- Install ad-blockers and pop-up blockers: You should use ad-blockers and pop-up blockers to prevent unwanted ads and pop-ups from appearing on your computer screen. Some web browsers have built-in ad-blocker and pop-up blockers, or you can install browser extensions that provide this functionality.
- Be careful when clicking on links: Don’t click on links in emails or on websites unless you are sure they are legitimate. Check the URL and ensure it is spelled correctly and is the correct website. Be wary of shortened URLs or URLs that lead to suspicious or unknown websites.
- Keep your web browser and operating system up-to-date: Regularly install software updates and security patches for your web browser and operating system. This will help to close any security vulnerabilities that adware, hijacker and other malware may exploit.
- Use a reputable antivirus program: A good antivirus program can detect and block infections like Cuckoo and other malware before they can infect your computer. Make sure you choose a reliable antivirus suite and keep it up-to-date with the latest virus definitions.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your Mac safe and secure.
Conclusion:
To sum up, Cuckoo can cause significant problems for Mac users, including unwanted browser redirects, changes to homepage and search engine settings, and even the installation of additional malware. These infections typically result from downloading and installing software from untrusted sources or clicking on suspicious links. To prevent browser hijackers or adware, it is important to be cautious when downloading and installing software, use reputable antivirus tool, and keep browsers and operating systems updated with the latest security patches.


