How to Remove Contentlimitless.com Pop-ups
If you wish to remove Contentlimitless.com, it can be a complicated process for you if you are an inexperienced user. To eliminate this malware completely, you must uninstall all related items from your Control Panel, Registry, and system files. Additionally, you must clear your browser’s cache and cookies and reset its settings to their default state to ensure that all remnants of the infection are removed. If you lack technical skills, the easiest way to remove Contentlimitless.com is to employ a reputable anti-malware tool that can scan your system and eradicate the threat automatically.
Special Offer (For Windows)
Contentlimitless.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Contentlimitless.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
What is Contentlimitless.com?
Contentlimitless.com is a kind of malware that shows the traits of browser hijacker. Browser hijackers are a malicious program that is infamous for altering your web browser settings without your consent. This infectious program forces its victim to use a new search engine and makes it extremely difficult to navigate from page to page. In most of the cases, the hackers infiltrate this malware into the PC to generate ad revenue. In order to make higher revenue for their developer the malware redirect you to other commercially sponsored pages. After landing on these pages, you get prompted with various unwanted ads for online web games, 18+ sites, unwanted browser extensions and so on. Sometimes the uses also get prompted with fake software alerts. These alerts claims that the users needs to update their software to prevent their PC from several malware attacks. But it’s nothing more than a scam and the users should not trust these fake claims.
Threat Summary |
| Name: Contentlimitless.com |
| Category: Browser hijacker, Redirect Virus |
|
Features: The hijackers or redirect viruses are often featured with abilities to modify almost all critical browser values like Homepage, new tab, search engine, DNS, proxy, and even more. |
| Danger Level: Medium |
|
Symptoms: The PUP or hijacker if installed, can lead to several unwanted modifications on browsers or system. and these changes will probably cause frequent issues like redirects to malicious websites, eruption of commercial pop ups or banners, fake or deceptive warnings, enforcements to download rogue applications, and even more. |
|
Distribution: Fake flash player updates, malicious websites, free software installer or updater packages, hacked social media channels, free software distribution channels, and so on. |
|
Removal: To remove the threat, scan your system with powerful SpyHunter anti-malware software |
What are the potential risks and consequences of Contentlimitless.com infections?
After entering your PC browser hijackers create loop holes in your machine which makes your PC more vulnerable to other malware. But many users don’t consider it as a hazardous malware they believe that browser hijackers or adware are only responsible for minute changes in their browser settings. But it is imperative to understand that these malware are not only limited to minor browser settings. It prompts intrusive ads and these irksome ads serve as a gateway for other malware.
The intent behind infecting your browser may differ from hacker to hacker. On the basis of our research we concluded that following can be the possible reasons for infiltrating Contentlimitless.com in your PC:
- Bombard you with unnecessary advertising.
- Replace a home page or research page with the one the hijacker wants you to access
- Steal banking information and other sensitive data.
- Track and record your internet activity
Among all the above mentioned reasons data tracking is the main goal of the hackers. By hijacking your browser they monitor your online activities. The information of interest may include user IDs, passwords, finance related data and may more.
In the extreme case, browser hijackers may install ransomware in your PC which can encrypt your files and make it inaccessible. And then the attackers demand a big ransom for decrypting your file.
To summarize, once your PC is infected with this malicious program you may face serious system infections, data loss, financial losses and even identity theft as well. The scammers can access your social networking accounts by stealing your passwords and demands loans and donations from your colleagues, friends, and followers.
How do adware and browser hijackers typically enter a user’s system?
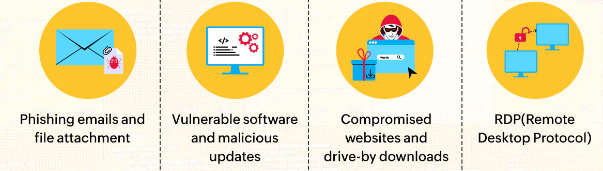
There are various ways through which adware or browser hijackers infect your PC. Here we have enlisted some common ways through which the malware gets distributed.
Social Engineering: Social Engineering is a way through which browser hijackers enters your PC. In this technique, the attackers create fake advertisement or pop-up that claims that user needs to update their software. These pop-up messages may contain a convincing message such as “Your PC is infected; Click here to remove this virus”. Once you click on this dubious link the malicious program gets installed in your PC out of your knowledge.
Malicious Websites: Malware like Contentlimitless.com also infects your PC via malicious sites. These rogue sites are designated in such a way that users get scammed by these sites. The attackers manipulate the users by sending malicious links in the email. Once the recipient click on the link provided in the email the unwanted software gets installed on the PC.
Bundled Software: One of the most common methods is software bundling. In this technique, the unwanted piece of software gets installed in your PC along with the legitimate software. It often happens when the users rely on freeware, shareware or other unverified sources to download/install program.
Contentlimitless.com Redirection Leads to Unsafe Sites
The redirection chain triggered by Contentlimitless.com may force the browser to send the user to a variety of different webpages. Nonetheless, it’s pertinent to note that most of the websites it sends people to are malicious and even dangerous and may pose a serious threat to the device and the browser. This undesired software piece may take users to following sites:
Tech Support Scam Sites

Many people are falling victim to tech support scam websites that have become increasingly widespread. These sites often imitate the appearance of legitimate operating system error messages, making it difficult for individuals to discern whether the message is genuine or a scam. As a result, users are easily fooled into giving scammers access to their personal information or paying for unnecessary and expensive services.
Unsafe Dating Website
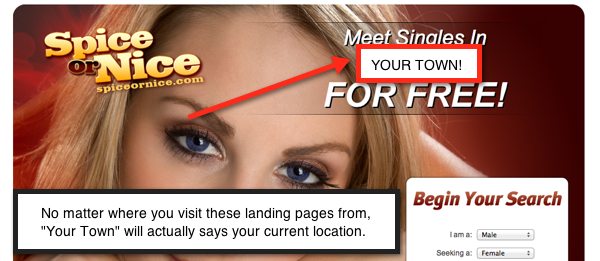
Contentlimitless.com pop-ups may lead you to dubious dating sites that are entirely controlled by robots. Such websites often display deceptive notifications and pop-ups that mislead users into believing that they have multiple chat requests or messages waiting for them. These false alerts may be designed to look convincing and may even use persuasive language to create a sense of urgency, tricking users into clicking on them. In reality, these notifications are usually a tactic employed by scammers to lure individuals into interacting with their fraudulent websites or downloading malicious software.
Websites Showing Fake Virus Alert:
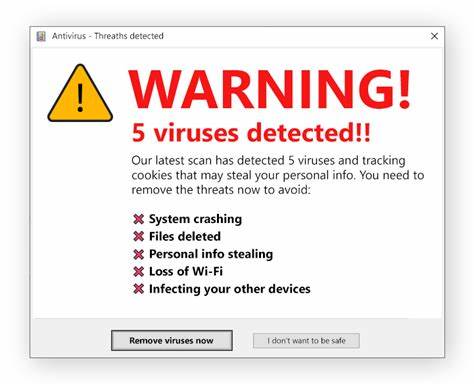
These sites tend to display fake security alerts claiming that users’ PCs are infected with several viruses. They are designed to trick visitors into believing that they are in trouble of having their computers infected and to compel them into taking immediate actions. Scammers behind these deceptions aim to mislead users into downloading and installing malicious software or extracting money from them for useless services.
Drive-by Download Malware Sites
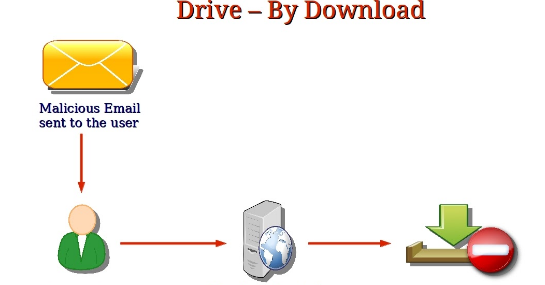
Users may also be taken to drive-by download websites, which is a type of cyberattack in which malware is automatically downloaded to a computer without the user’s knowledge or consent. Drive-by downloads are a serious security threat, as they can result in the installation of viruses, spyware, or other types of malicious software, which can compromise the security and privacy of your computer and personal data.
Fake Giveaway Survey Websites
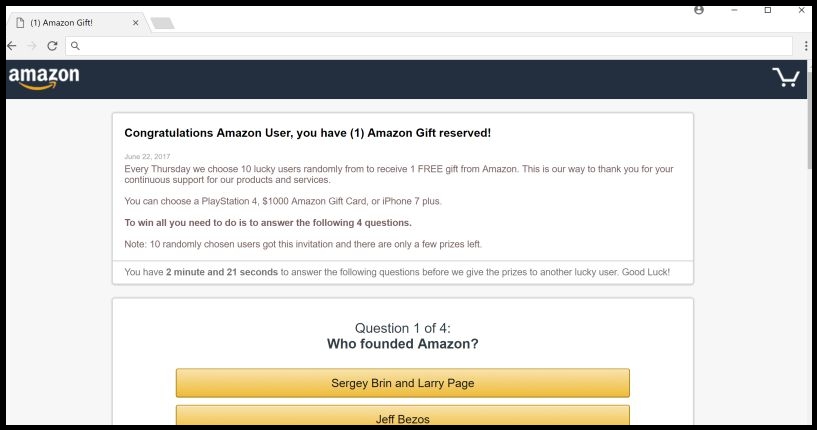
These dubious sites tend to promote bogus surveys aiming to trick users into stealing their personal information such as their credit card details, banking credentials, etc. This sort of information could later be used for various malicious purposes and may lead to a number of unpleasant issues.
Unsafe Pop-Ups Causes Online Scam

Unsafe pop-ups are a common method used by online scammers to deceive unsuspecting internet users. These pop-ups can appear on users’ browser when their system is contaminated with an unwanted application; they visit a website or click on a link, and often try to convince them to take some action, such as downloading a program or providing personal information.
Once users interact with the pop-up, they can be redirected to a fraudulent website that looks legitimate, but is actually designed to steal their sensitive data or money. For example, a Contentlimitless.com pop-up might claim that users’ device is infected with a virus and prompt them to download software that is actually malware.
Other pop-ups might offer a prize or gift in exchange for the user’s personal information, such as their name, address, and credit card number. Once the scammers have this information, they can employ it to make unauthorized purchases or commit identity theft. This can lead to serious privacy issues, identity fraud, high-risk system infections, and even significant monetary losses.
Special Offer (For Windows)
Contentlimitless.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Contentlimitless.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
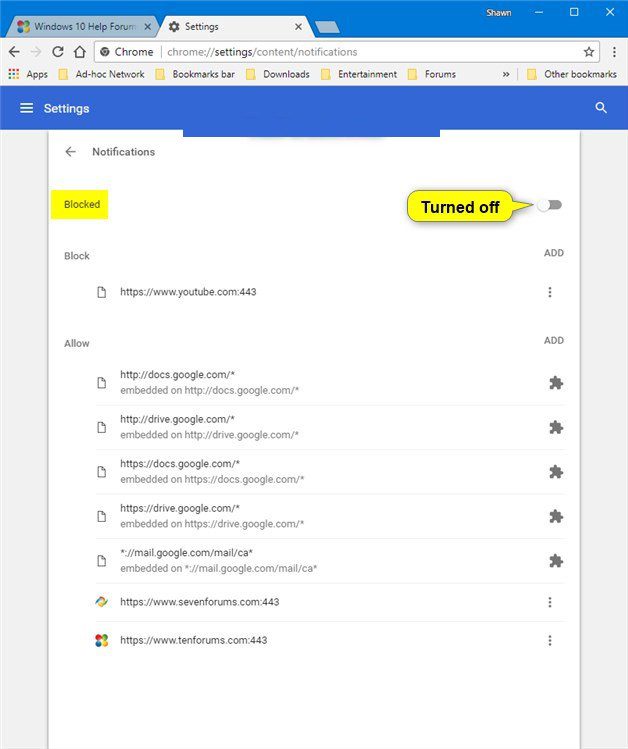
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
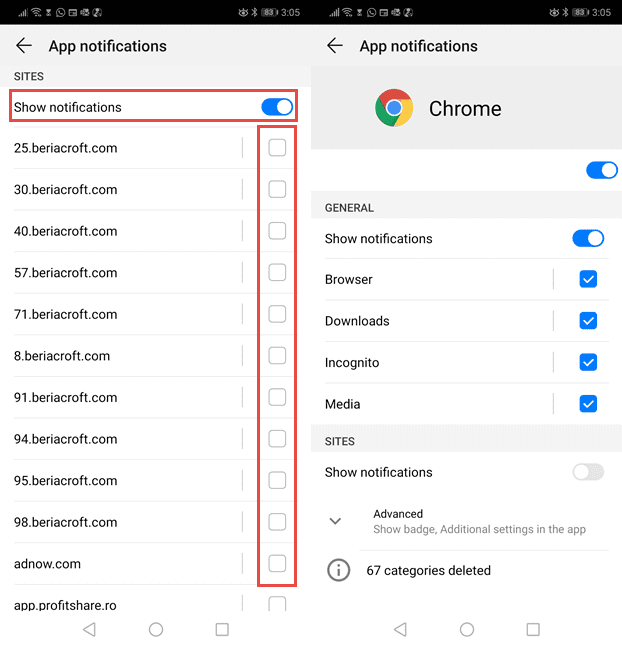
Google Chrome (Android)
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
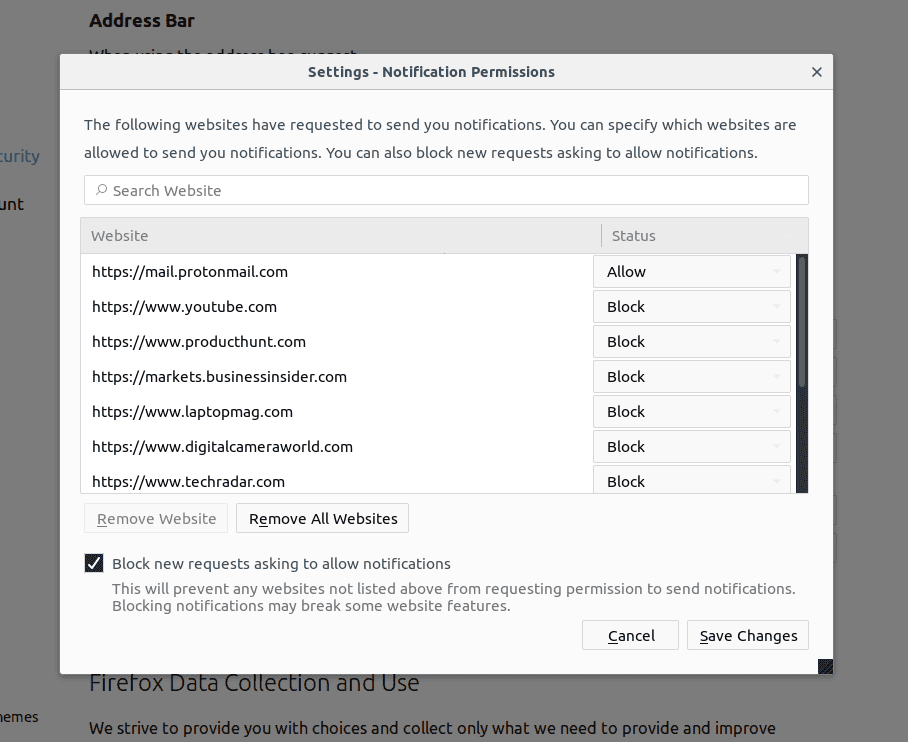
Mozilla Firefox
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
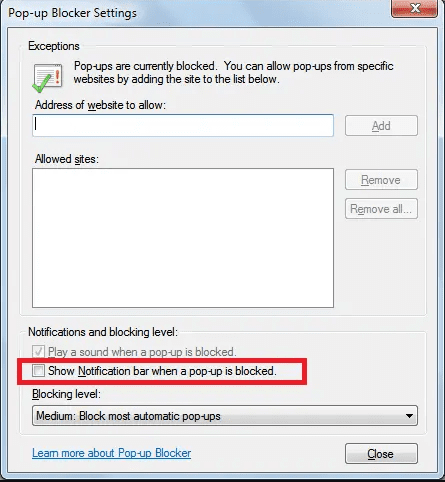
Internet Explorer
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
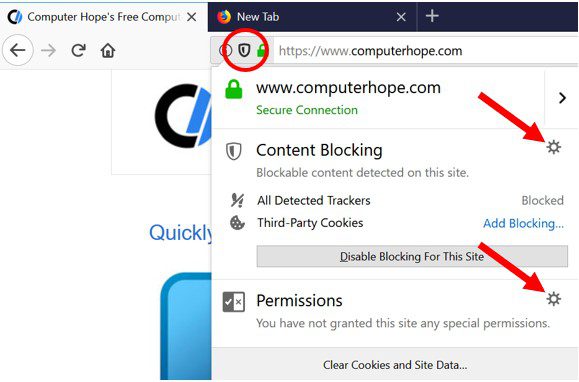
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
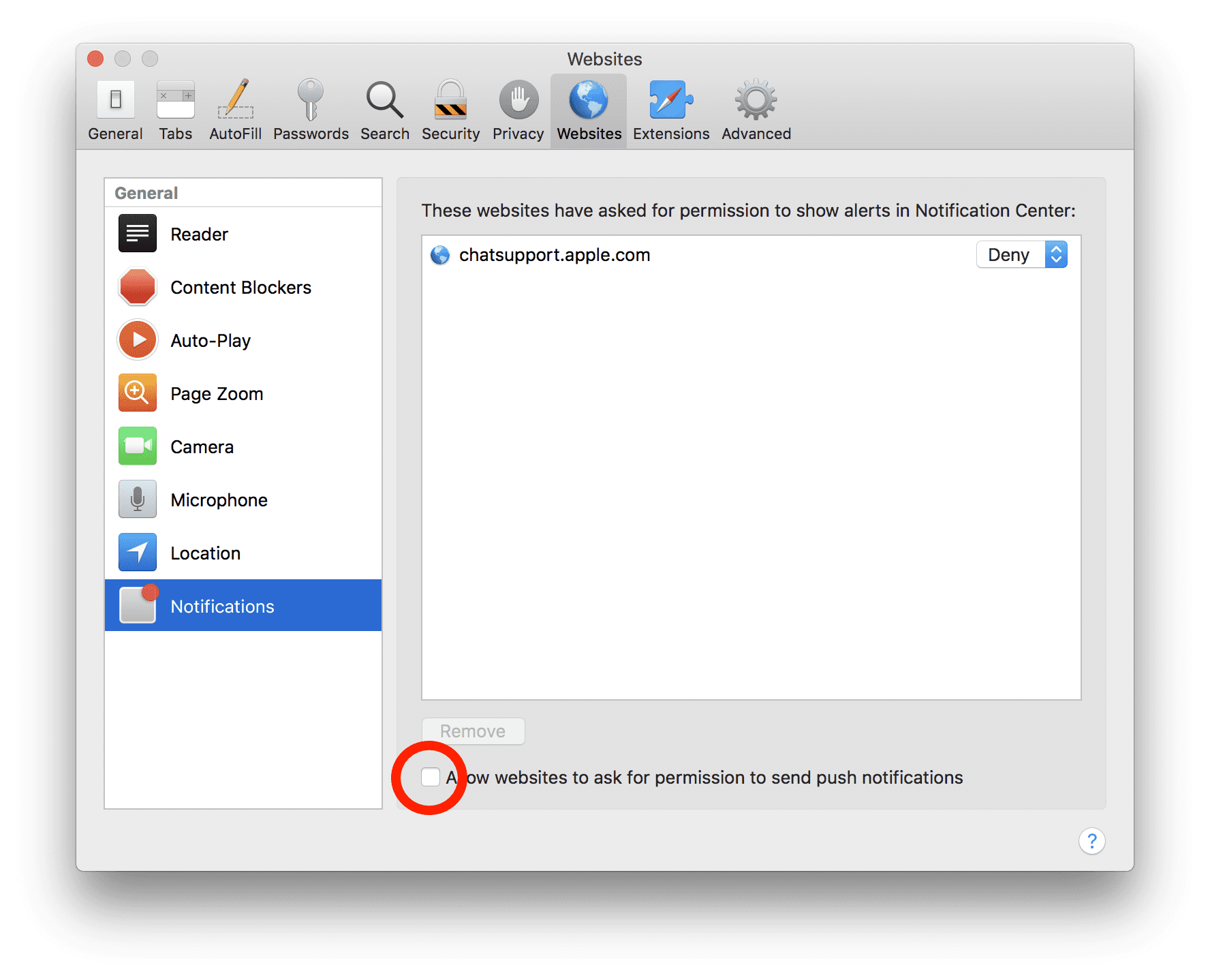
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Contentlimitless.com:
Remove the related items of Contentlimitless.com using Control-Panel
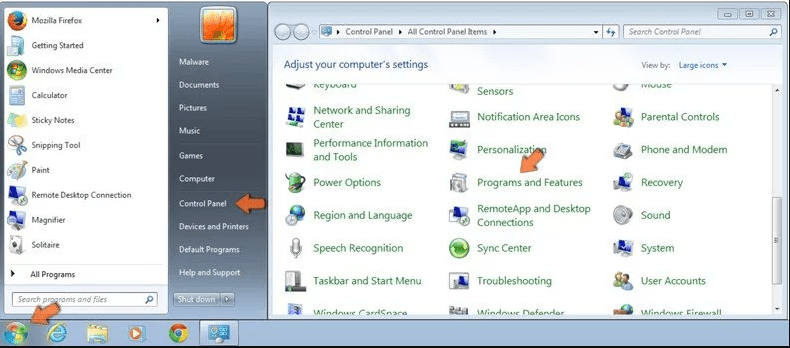
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
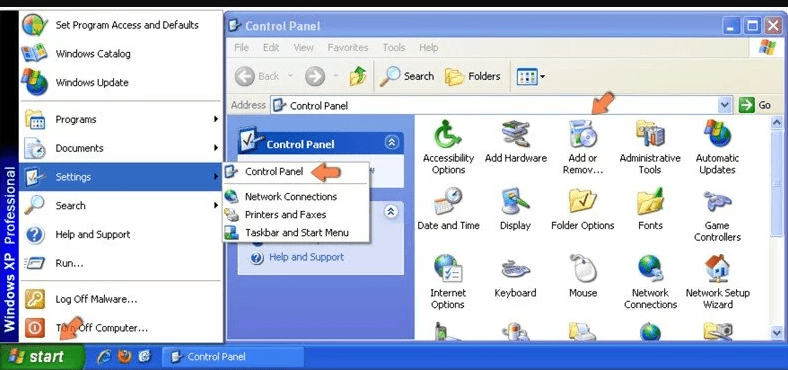
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
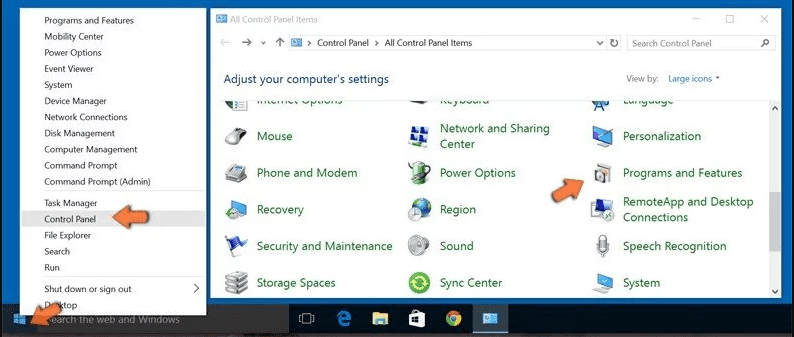
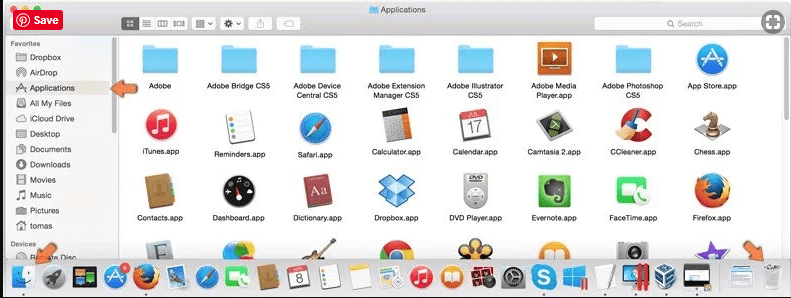
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
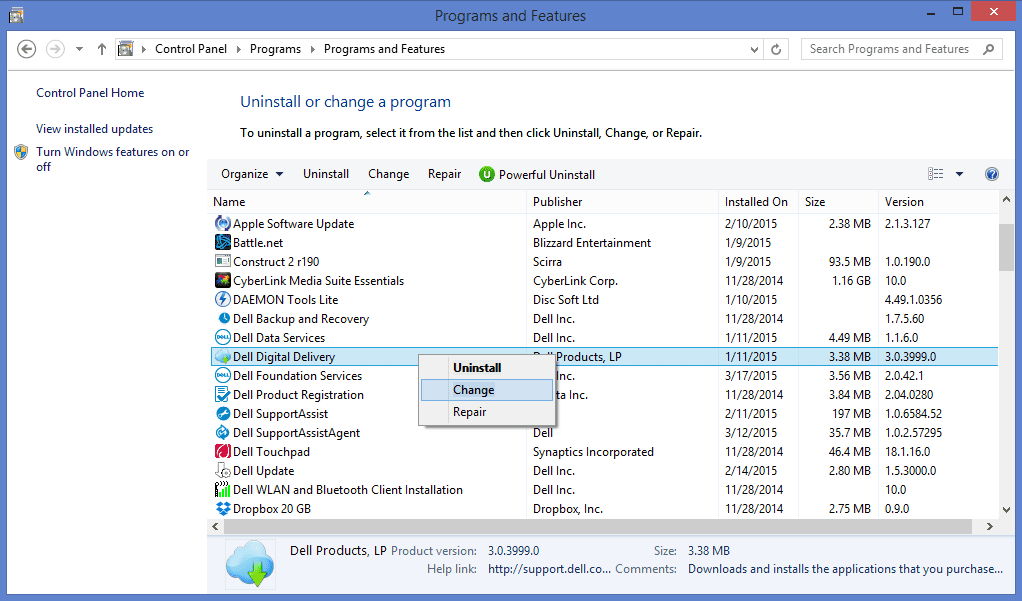
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Contentlimitless.com issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Contentlimitless.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Contentlimitless.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Contentlimitless.com) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
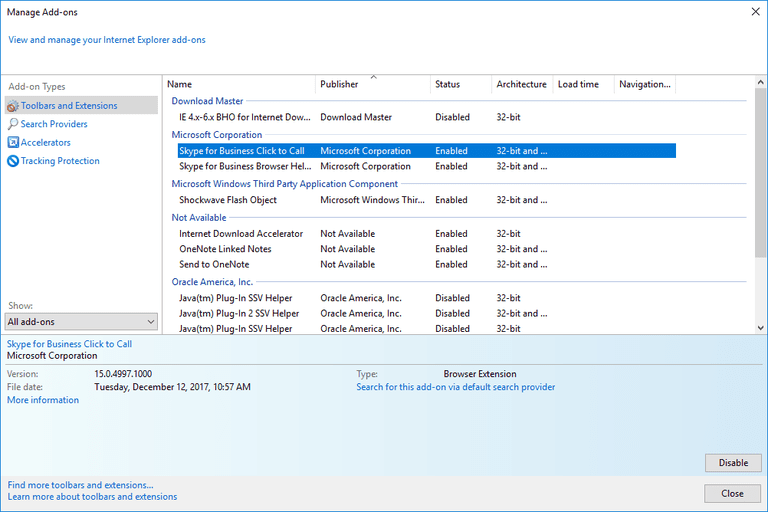
Additional Option
If you still face issues related to Contentlimitless.com removal, you can reset the Internet Explorer to its default setting.
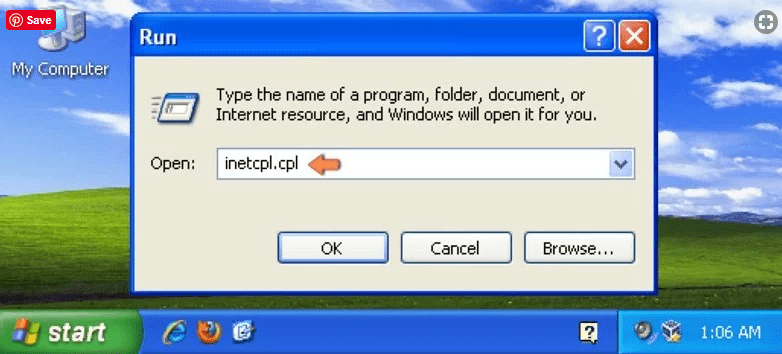
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
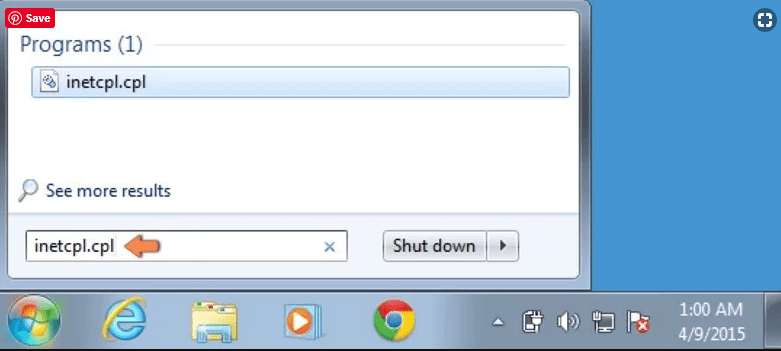
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
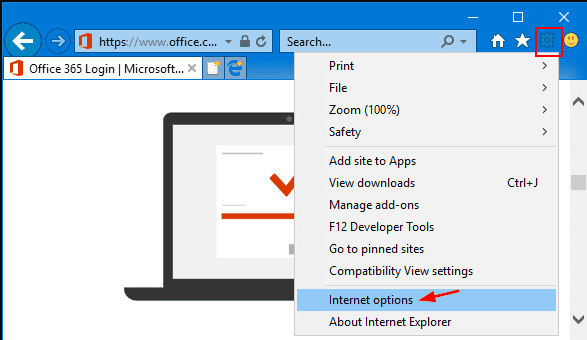
Select the “Advanced” tab in the newly opened window
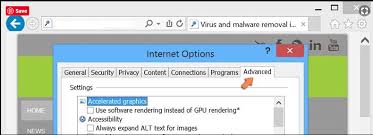
Press on “Reset” option
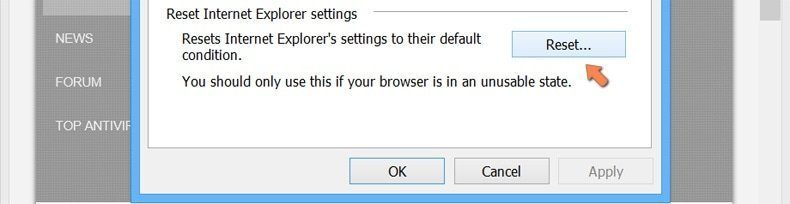
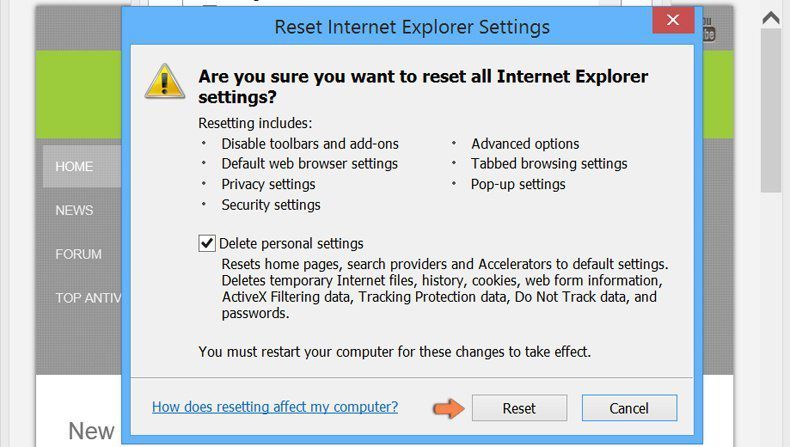
You have to press on the “Reset” button again to confirm that you really want to reset the IE
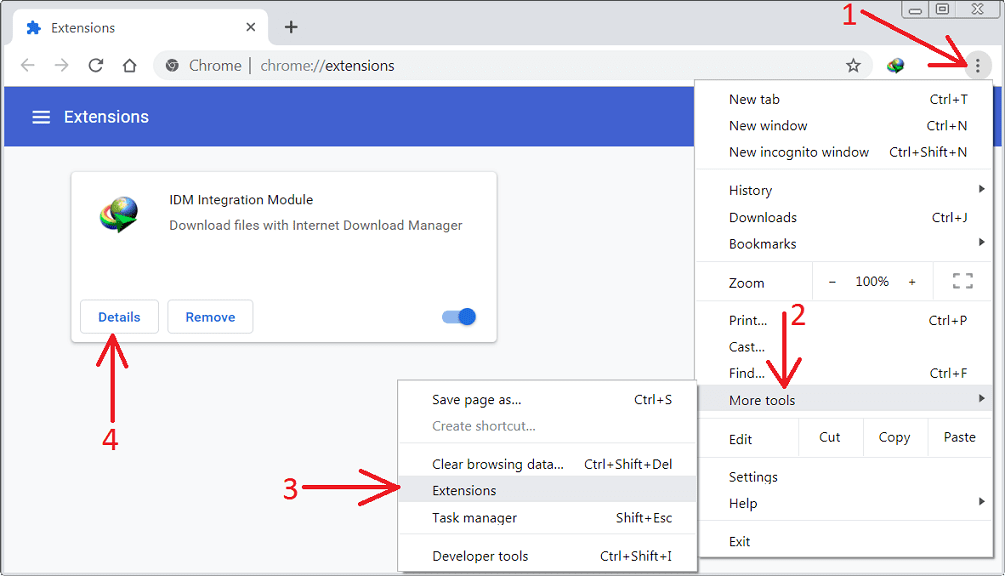
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
Optional Method
If the problems related to Contentlimitless.com still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
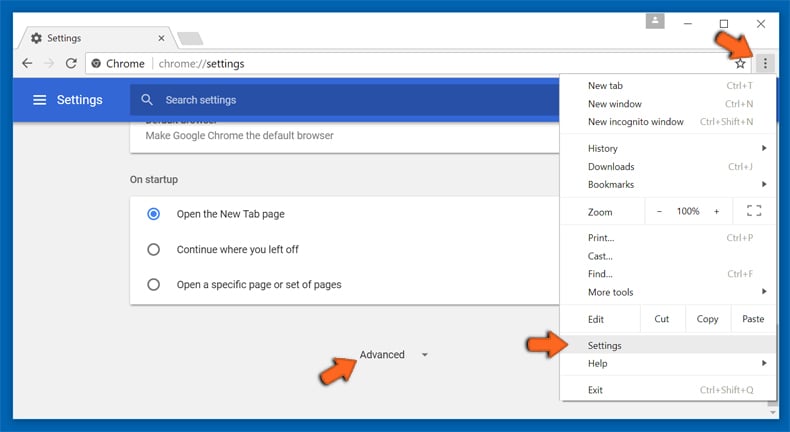
At the bottom, notice the “Reset” option and click on it.
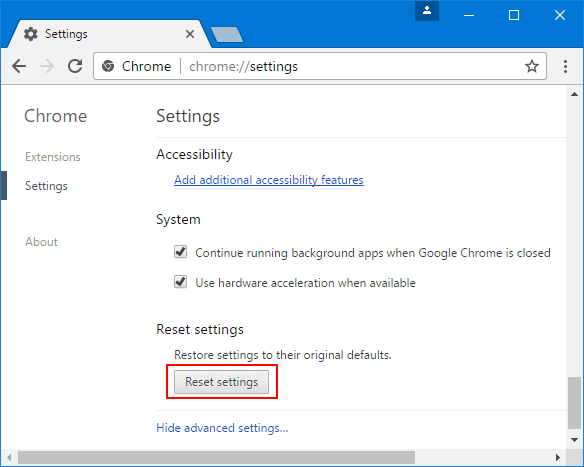
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
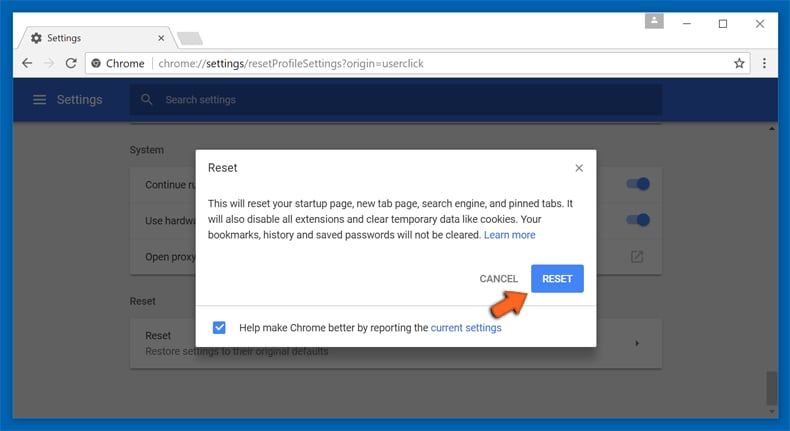
Remove Contentlimitless.com plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
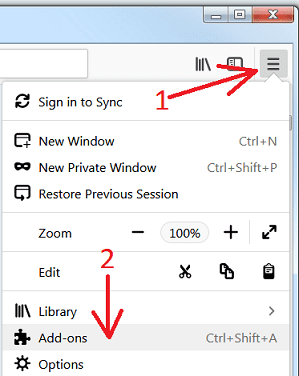
Optional Method
If you face problems in Contentlimitless.com removal then you have the option to rese the settings of Mozilla Firefox.
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
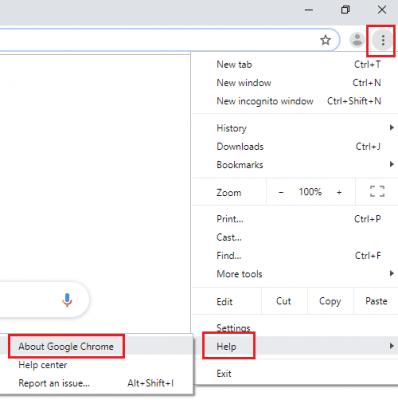
Choose “Troubleshooting Information”
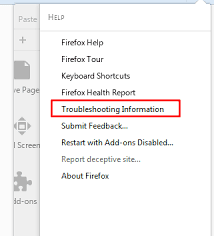
In the newly opened pop-up window, click “Refresh Firefox” button
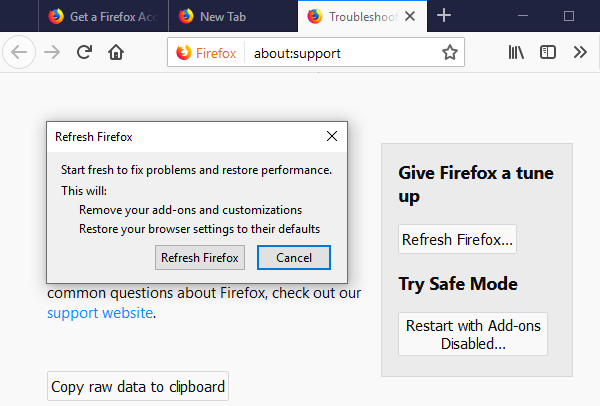
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
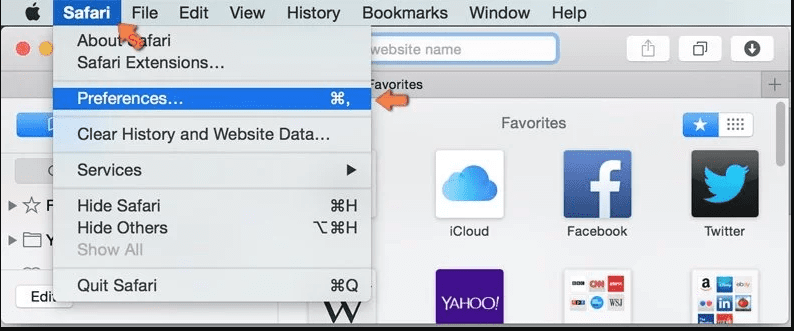
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
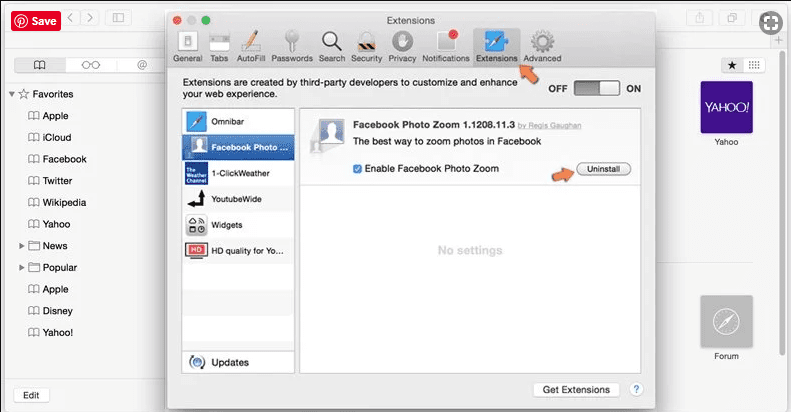
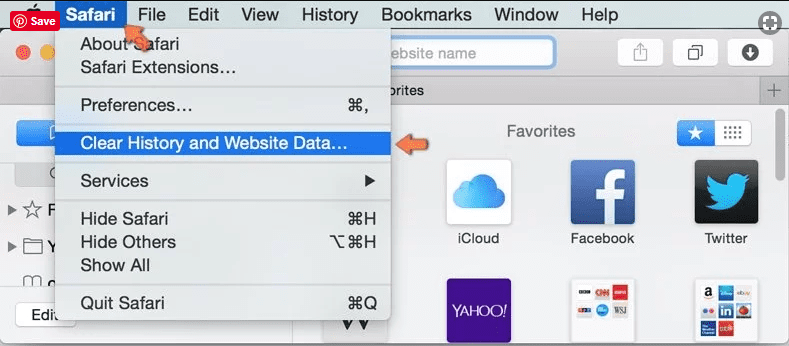
Optional Method
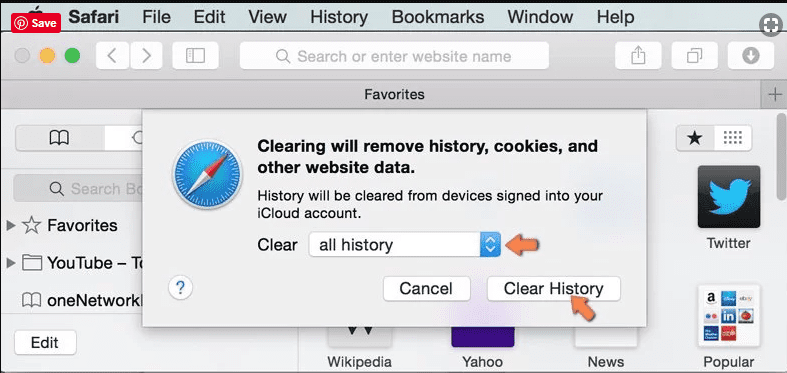
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
In the newly opened window, select “All History” and then press on “Clear History” option.
Delete Contentlimitless.com (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
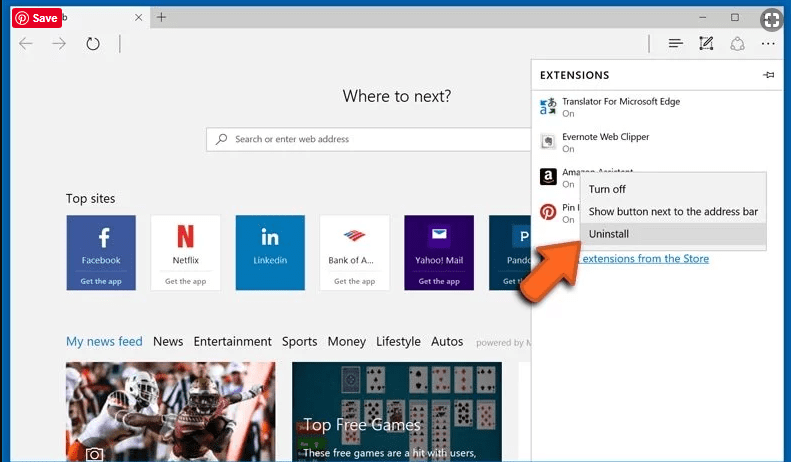
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
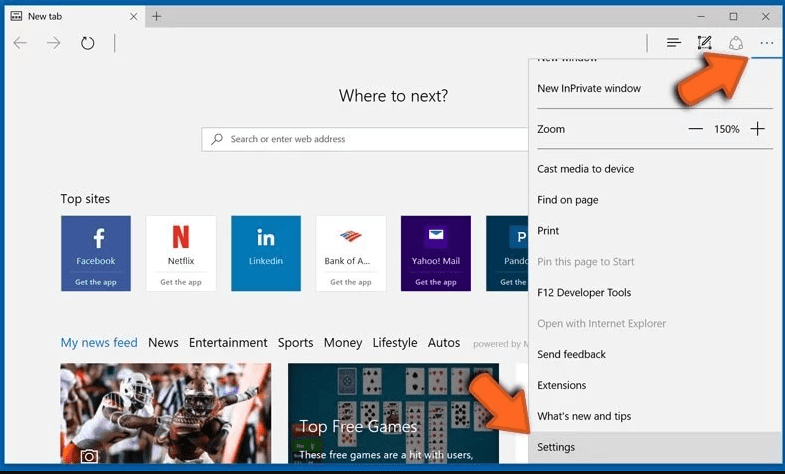
Next steps is to click on “Choose what to clear” button
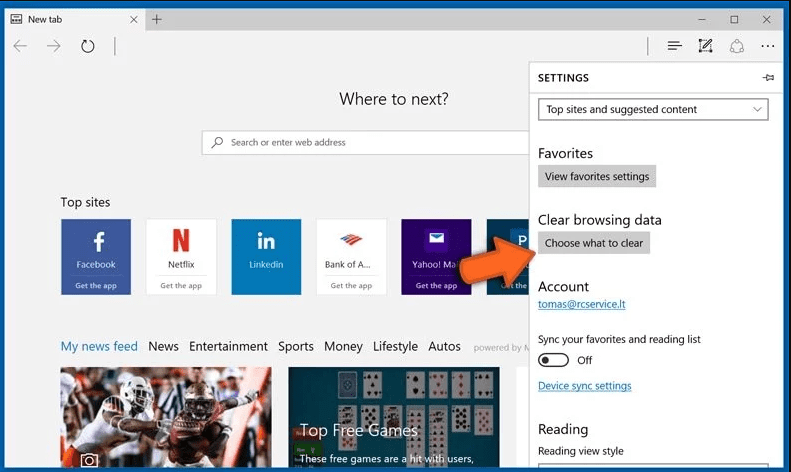
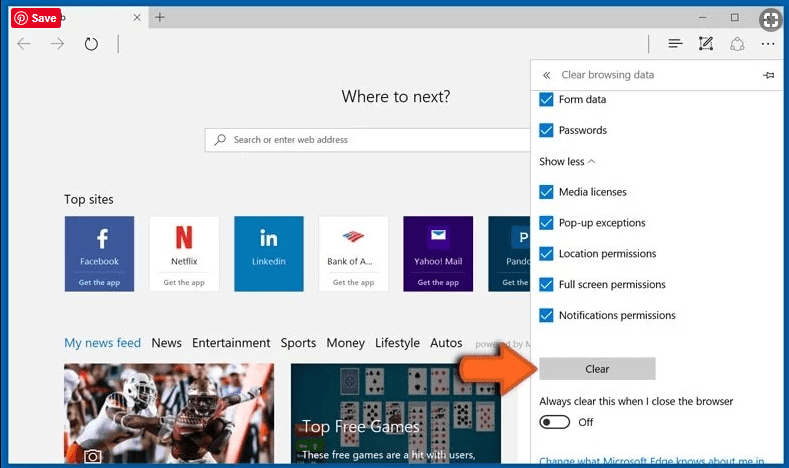
Click on “show more” and then select everything and then press on “Clear” button.
Are there any specific websites or download sources that are more likely to distribute unwanted programs?
Nowadays there are numerous download sources that avails free utility or games to the users for grabbing their attention and make them download the freebies. This technique is called software bundling. The scammer uses torrent sites and shareware to distribute malware. The software downloaded from these sites are bundled with the malware like browser hijackers or adware. When you install/download the malicious program gets installed in your PC along with the legitimate software. some examples of such sites that promotes the distribution of malware are download.com, Softpedia etc.
Can unwanted application compromise my personal information or online privacy?
The primary goal of the attackers is to make illicit money either by manipulating the user to subscribe their unwanted software/products or by misusing their data. Once this malicious program entered your PC you cannot claim yourself safe on the web.
Tracking the user’s data is one of the main motives of the hackers. And the information of interest may include visited URLs, viewed pages, searched queries, usernames/passwords, personally identifiable details, finance related information and so forth. The collected data can be further misuse by the cyber criminals for performing malicious activities such as frauds, unauthorized purchase and identity theft. Browser hijackers are a security invader and it may lead to the data loss. In fact not only browser hijackers other malware are also a privacy threat ad may create deep troubles for you by stealing your personal data.
Can adware or browser hijackers affect different web browsers equally, or are some more vulnerable than others?
Browser hijackers or adware are potentially unwanted programs and it can be incorporated into Google Chrome, Firefox, Edge, Safari, Opera and others as well. Such malware can alters the browser’s settings and it is quite difficult for the user to reset the settings to its original state. Once the malware gets settled down in your machine it starts performing all sorts of malicious activities. However, you need to know that browser hijackers or adware are generally considered as potentially unsafe, they are not mostly highly destructive but that doesn’t means that they are totally harmless.
On the basis of our research on the browser hijackers we concluded that some of the hijacking apps are extremely dangerous and may install more hazardous malware to your machine. These malware may include spyware, Trojan, ransomware and botnet malware as well. Botnet malware and Trojans are highly vicious programs that can manipulate your system settings and get complete access to your device. That’s why we recommend user not to browser hijackers any change to inject chain malware in your PC. Once you detected any changes in your browser behavior immediately take action to prevent yourself from severe damages.
Can PUP affect mobile devices such as Smartphones or tablets?
Potentially Unwanted Programs can also infect mobile devices such as Smartphone or tablets. Like typical Pc malware mobile malware also attacks the devices to generate ad revenue or hey steal the user’s data for making illicit profit. Like PC Malware mobile malware also targets the user’s personal data and send it to the remote server. Not only PUP but there are other malicious programs that are designated to attack the mobile devices. These infectious programs may include mobile bots, mobile phishing, ransomware, spyware and Trojans.
What should I do if I suspect my computer or browser has been infected with adware or a browser hijacker?
Browser hijackers or adware are designated in such a way that they can disable your Antivirus Program to stay long in your machine. But if you find any kind of changes in your browser settings you should not ignore this. Browser hijackers not only alter browser settings to result in redirections or pop-ups but it is also capable for tracking your data and steals your personal information for performing malicious activities. So in such scenario all you need to do is just discontinue using the infected browser and immediately run an antimalware tool to remove this malware from your PC.
Are there any preventive measures I can take to avoid adware or browser hijacker infections?

Browser hijackers or adware are quite dangerous for your PC health and a privacy invader so that’s why it is always suggested to use preventive measures to keep your PC infection free. To do the same you can use the following prevention tips.
- Always keep your Operating System and browser updated. Updates software can defend malware from entering your machine.
- Be very cautious while opening emails if they are from suspicious senders. Avoid clicking on links or attachments in emails if you are not sure they are legitimate.
- Always choose a verified Antivirus Software to prevent your PC from malware attacks and don’t forget to keep it updated with the latest virus definitions.
- Make sure you download software or programs from legitimate or verified sites only. Avoid downloading program from freeware, shareware or other suspected sources. While installing the program pay attention to the installation process and look for the checkboxes that may indicate the installation of additional software. All you need to do is uncheck those boxes and avoid installing the additional software.
Special Offer (For Windows)
Contentlimitless.com can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Contentlimitless.com has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.






