Is Cacoyic.com a Scam or Legit? (Detailed Review)
Cacoyic.com pretends to be a real online store where things are super cheap, catching people’s attention with big discounts. But the truth is, it’s a fake website created by scammers. They make it look like they have great stuff for great prices, so people will buy from them. However, their real goal is to take your money and personal info without giving you what you paid for.
In reality, this means you might pay for things you never get or things that are not as good as you thought. Even worse, your private info like credit card details could end up in the hands of bad people who might use it for bad things.
Even though Cacoyic.com might seem like a good place to shop, it’s actually a trick. It’s highly significant to be careful online and only buy from websites you know are real and safe. If something seems too good to be true, it’s better to stay safe and not fall for it. Always put your safety first!
How does the Cacoyic.com scam operate?
The way Cacoyic.com works is that they show you things you really want to buy, but they make the prices seem much lower than they should be. This tricks you into buying stuff. But when you actually get the things you bought, they’re not what you wanted – they’re fake or really bad quality. This is a big lie.
Sometimes, people who buy products from this fake store don’t even get anything in return. This is a big problem because it’s like paying for something and getting nothing in exchange. This is not how real online stores should work.
In the end, Cacoyic.com is a clear example of cheating online. They use the internet’s anonymity and the fact that they can reach people from all over the world to trick them into giving them money. This is really bad because it can make people lose their money and feel very disappointed. So, when shopping online, it’s super important to be careful and check if the store is real and trustworthy before you buy anything.
Let’s review the red flags that indicate Cacoyic.com is a scam site. Moreover, we’ll provide advice on safeguarding yourself if you’ve interacted with this website.
Signs of Cacoyic.com being a scam site

As we’ve established that Cacoyic.com operates deceptively and poses risks to its customers, it’s essential to clarify the reasons behind this assessment.
The website’s domain was registered quite recently
Domain name registration is like claiming a spot on the internet with a unique name for a certain period, usually a year. Once a name is registered, everyone can see when it was made.
When we quickly checked the “Cacoyic.com” website in a special database, it showed that it’s really new. It only appeared recently.

This means that Cacoyic.com is a very new online store, probably just a few days or weeks old when you saw it. This newness makes us doubt if the website is trustworthy, like a warning sign telling us to be careful.
Our study shows that these tricky websites don’t last very long, often just a few weeks to a few months. When people start to notice their bad actions, the people behind them often leave the old website and quickly make a new one with a different name. They keep changing to hide.
In short, the fact that Cacoyic.com is so new makes us doubt if it’s real. This fits with how fake websites usually work – they don’t stay around for long, and they’re always changing to try and trick more people.
They use pictures they’ve taken from others for their products
Fake online stores like Cacoyic.com might not have real pictures of what they’re selling because they don’t actually have those things. So, they might use fake pictures made by computers or get pictures from real websites. To check if an online store is real, you can take a few picture links from the website and use tools like Tineye and Duplichecker. These tools can tell if the pictures are already on the internet, which could mean the store is trying to trick you by using images from other places.
Very low natural website visits

When we’re looking at a website to see if it’s real and trustworthy, one important thing is how many people visit it naturally, without any tricks. A good website becomes popular and shows up a lot when you search online, which means more people visit it.
But Cacoyic.com is different. When we checked using a tool called SEMrush, we saw that it only recently started getting more visitors from searches. This makes us unsure if it’s really trustworthy because it’s so new.
Although social media can also bring visitors, real websites want lots of people to come naturally. This makes it tricky to decide if Cacoyic.com is real or not because it hasn’t been around for long.
The graph shows that very few people are going to the website, and its authority on the internet is much lower than normal online stores. This means people don’t really trust it.
Looking at the Organic Keywords graph, we see that the website’s words and stuff only recently started showing up when you search on the internet. This means search engines like Google are only now starting to know about it.
When we looked more closely at the graph’s history, there’s no proof that the website existed before, had visitors, or was known by search engines. This makes us doubt if the website is real or if it’s going to last.
In brief, the website’s short history of people visiting, low internet authority, and recent notice by search engines all make us question if Cacoyic.com is reliable. These things together make us unsure if the website is real and can be trusted for a long time.
Significant price cuts that seem unbelievably attractive
Remember the saying, “If it seems too good to be true, it probably is”? Well, that’s really important when you’re shopping online. Sometimes, websites offer big discounts that seem amazing, but they’re actually trying to trick you. They might make you buy things that are not good or even not send you anything at all.
So, we’re telling you to be careful and not trust these super tempting offers too quickly. Instead, look for sales from real and trustworthy stores, or wait for special times like Black Friday when you can find real discounts.
There are good ways to save money with discounts, but websites like Cacoyic.com are not the right ones. They might look exciting, but they can actually make you lose money and be really disappointed. It’s important to be smart and cautious when you’re shopping online.
Cacoyic.com is hardly visible on social media platforms

Most online stores use social media like Facebook, Twitter, and Instagram to show people their products. But Cacoyic.com is different. It doesn’t have a strong presence on these platforms, and we can’t find much about it when we look. Even though there are a few accounts with similar names, they don’t really seem to be connected to the store we’re talking about.
This is a problem because new websites usually have trouble getting visitors from search engines. If they also don’t get many visitors from social media, they might be doing something tricky to get people to come to their site. So, it’s something to be careful about and not trust too quickly.
Lack of authentic customer feedback

We checked Cacoyic.com on the internet and found very few reviews from customers who bought their products. Normally, people read reviews from others to know if a store is good before they buy anything.
But with Cacoyic.com, there aren’t many real reviews. This lack of feedback makes us doubt if the store is trustworthy. Some positive reviews we do find might be fake, made by computers to make the store look better than it is.
Once in a while, real reviews might show up, warning people that Cacoyic.com is a scam. But it seems like the store might delete these bad reviews to trick more people into thinking it’s real.
When we put all the information together, it becomes clear that there are many signs that something is wrong with Cacoyic.com. So, it’s best to be careful and not use this website to buy anything.
What are the methods used by Cacoyic.com to deceive buyers?

Cacoyic.com tricks people who buy things on their website using many tricky methods. They focus on people who don’t know about their tricks. One big trick is that they don’t give what they promise to buyers, so buyers lose money and get nothing in return.
Our detailed look into the website and the people behind it found that they have a complex plan to fool buyers. It’s not just about not giving products; it’s about how they cheat people when they’re paying. They are very careful in tricking people when they are giving their money. This shows how smart they are at tricking and making people believe them.
Exploit your personal information and email for malicious purposes
Cacoyic.com is like a tool used by bad people to harm you. It can turn any information you give them into a weapon against you. For example, when you share your email while buying something, they secretly use it to send fake emails that try to trick you.
These fake emails want you to click on them, making you more involved in their lies. Also, if you use the same email and password for other websites, they might use that to get into your other accounts.
The information they collect might be sold to others who want to show you ads or even to people who do bad things on the internet. This shows how serious the danger from Cacoyic.com is. It’s important to be very careful and protect yourself online.
Fraudsters may manipulate your credit card to make unauthorized transactions

When customers try to pay for their purchases, they see a system that doesn’t keep their card information private. The website only lets people use credit/debit cards because they’re harder for scammers to misuse. PayPal is safer with extra security.
Scammers secretly get real credit card numbers, dates, and codes. Then they buy expensive things using those stolen details.
To hide, scammers change where products go after buying. People who got tricked end up with huge credit card bills for things they didn’t buy. The scammers’ tricky plan uses how payments work and where things are sent, making victims lose money and trust.
Steps to take if fallen prey to the Cacoyic.com
Keeping your information safe is our top priority. If you’ve given your details or shopped on the website, don’t worry. We’ve put together important steps to protect you from potential risks coming from the fake Cacoyic.com website.
Revise your login information and activate two-step verification for security
Using the same login details on Cacoyic.com as you do on other websites can be risky. Scammers can use your email and password from the fake website to try and get into your other accounts. If they match, they might get into those accounts too. To be safer, it’s a good idea to use two-factor authentication and change your passwords.
Two-factor authentication means you need an extra step to log in, like a special code sent to your phone. This makes sure only you can get in. If you get a message asking for this code when you didn’t try to log in, it shows scammers are trying to get into your account. If they don’t have the right code, it means they can’t get in, and your account stays secure.
Get in touch with your bank to reclaim funds and block dubious transactions
Once you’ve bought something on Cacoyic.com, it’s really important to quickly contact your credit card’s issuing bank. Tell them about the purchase that you didn’t make and give them all the details like what you bought and where you got it from.
This is called a chargeback, where you ask the bank to cancel a payment you made to a fake website. It’s a protection for you, and it follows rules from big credit card companies like MasterCard and Visa, and also the Electronic Fund Transfer Act (EFTA), which keeps your digital money transfers safe.
You can also ask your bank to stop any future transactions on your credit card, so scammers can’t use it. You can do this by setting up a fraud alert or freezing your credit card. This makes it harder for them to mess with your money.
When you do this, you’re stopping scammers from using your credit card and trying to make new accounts in your name. Fraud alerts work kind of like when you have to verify your identity with a code before you can buy something, giving you more safety for your money.
Verify if your personal information has been exposed online
One of the top priorities is to prevent your email and password from being exposed on the internet. Sometimes, breaches in well-known websites have led to logins being leaked on the hidden parts of the internet, causing data leaks.
The information you shared on Cacoyic.com isn’t safe from the start. To make sure you’re fully protected, it’s important to actively look for any possible breaches that involve your accounts.
Using a tool that checks for leaked data is a really good way to find out if your personal information has been leaked. These tools search for any leaks that might have your email or password, which helps you be proactive in keeping your information safe.
There are several tools available that do this job, such as Dehashed.com, Intelx.io, and Haveibeenpwned.com. These websites collect data from big databases of leaks.
If your personal information was taken by the fake Cacoyic.com, these leak detection sites might show if it’s out there. Using these tools helps you take action to protect your data and make your online security stronger.
How can malicious websites (browser-hijackers) exploit vulnerabilities in web browsers?
Malicious websites such as fake online stores can take advantage of weaknesses in web browsers to harm your computer. They might use these weaknesses to deceive you into purchasing counterfeit products, install harmful software without your knowledge, steal your personal information, or trick you into downloading harmful files.
These websites could use clever tricks or codes that the browser doesn’t fully understand, allowing them to take control and do bad things. It’s important to keep your browser updated and be cautious of unfamiliar websites to stay safe from these sneaky tricks. In case, you’ve got misled into installing harmful app which changed the way your browser works, follow the steps below to remove the infection and revert the browser settings:
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
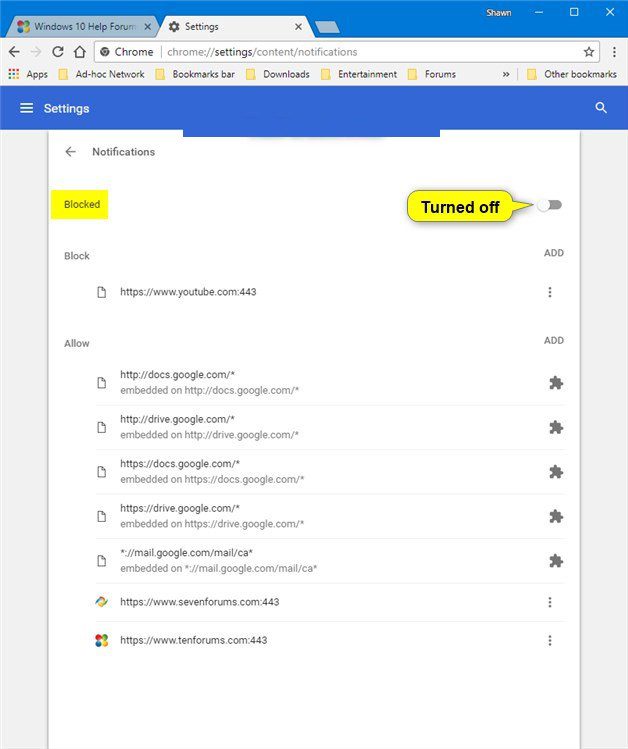
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
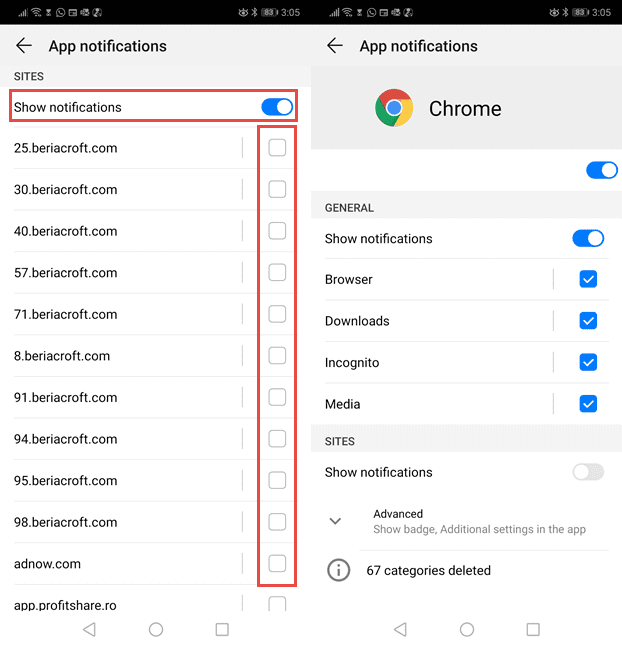
Google Chrome (Android)
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
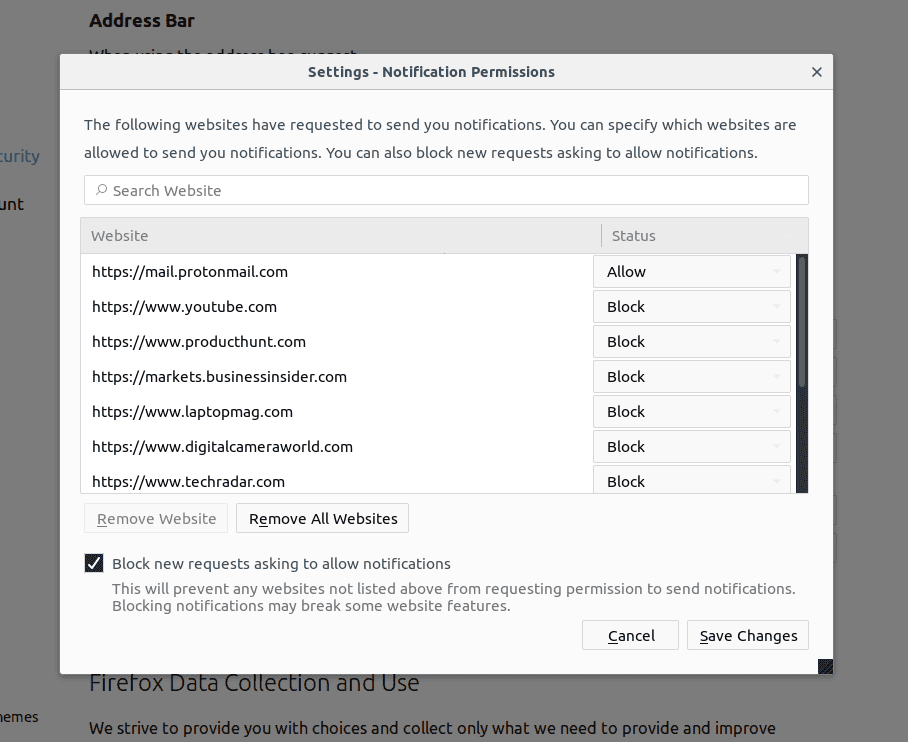
Mozilla Firefox
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
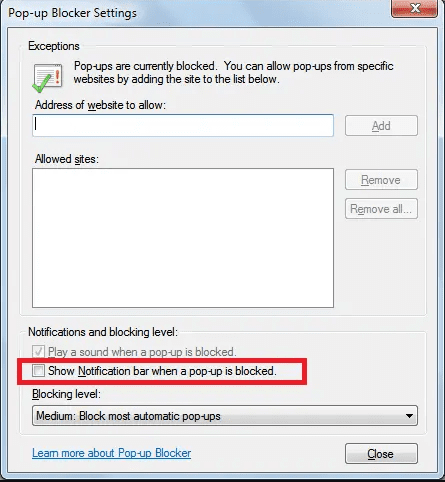
Internet Explorer
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
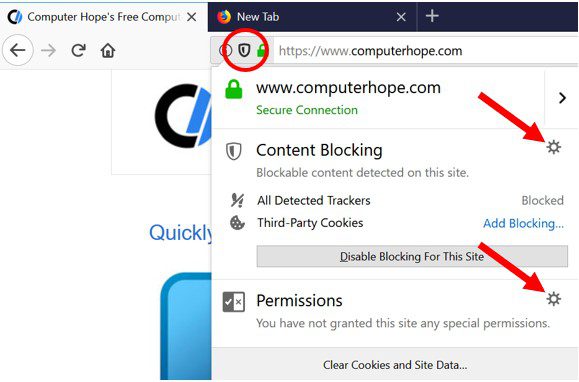
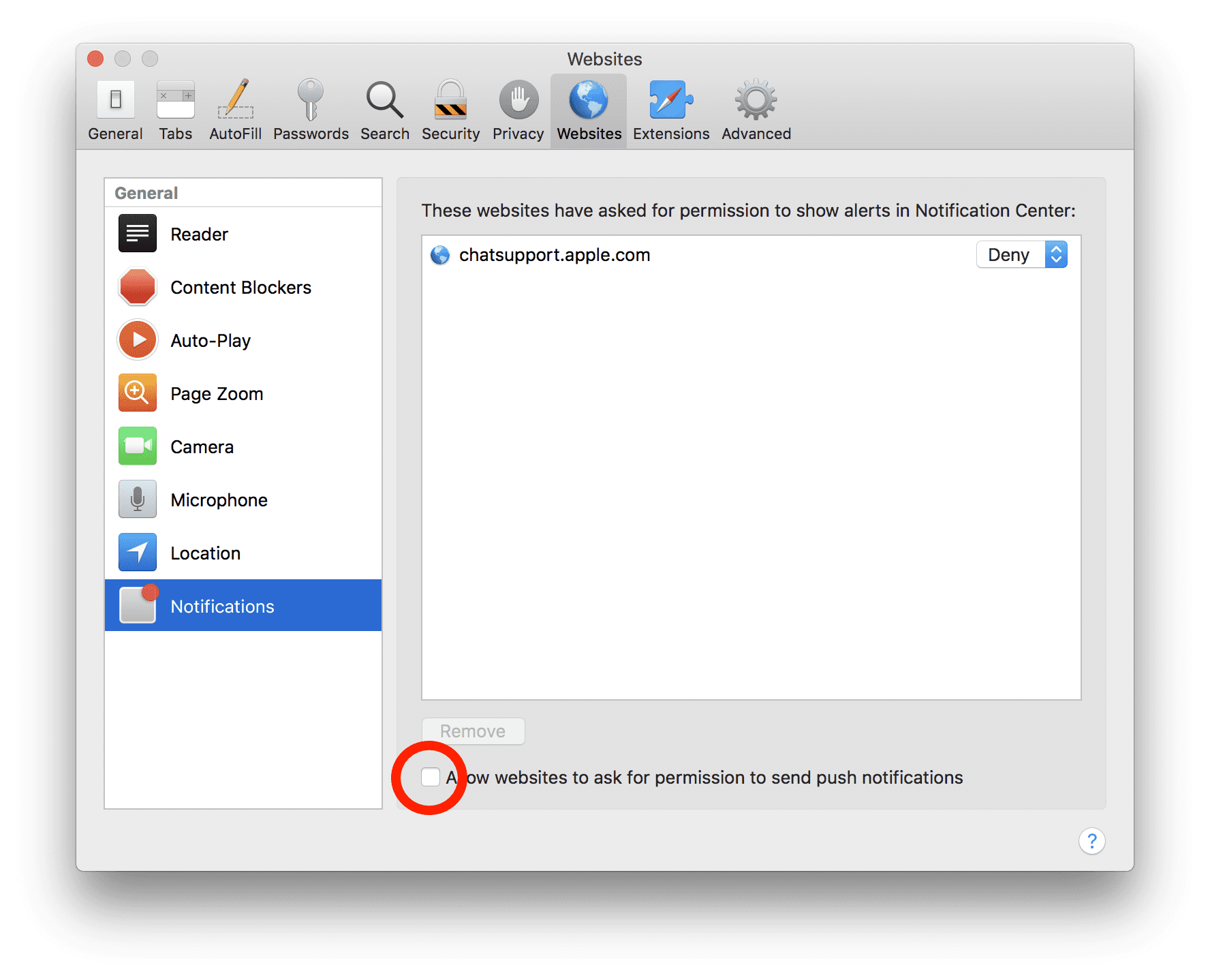
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove browser-hijacker:
Remove the related items of browser-hijacker using Control-Panel
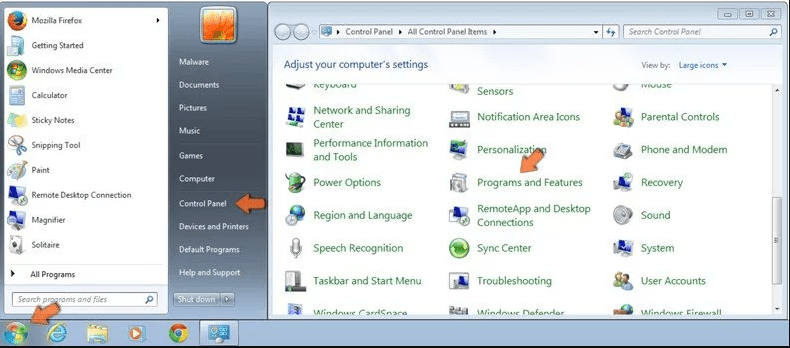
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
Windows XP Users
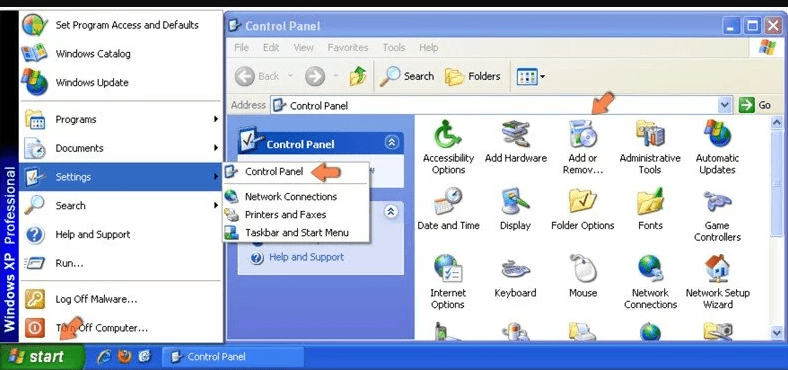
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
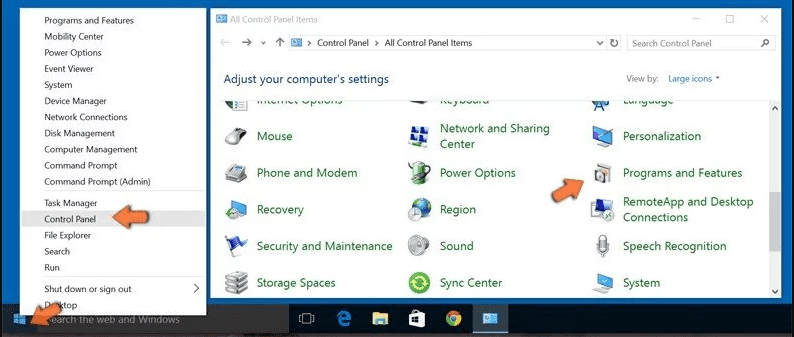
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
Mac OSX Users
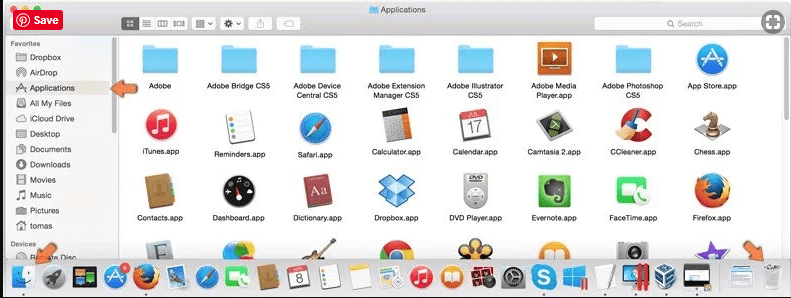
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
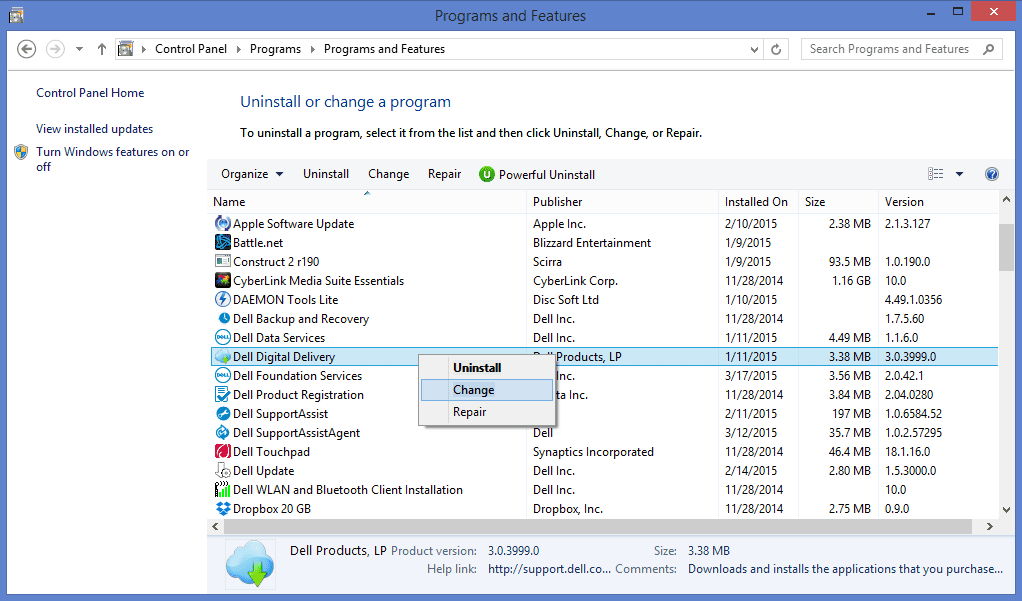
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing browser-hijacker issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (browser-hijacker) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
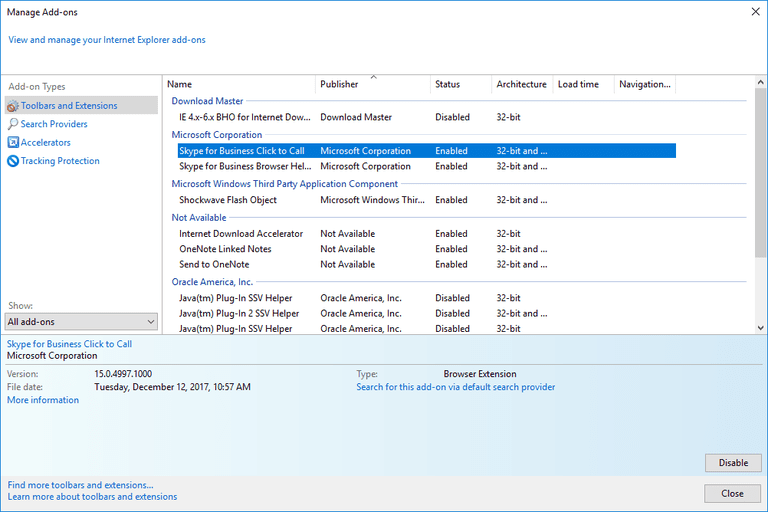
Additional Option
If you still face issues related to browser-hijacker removal, you can reset the Internet Explorer to its default setting.
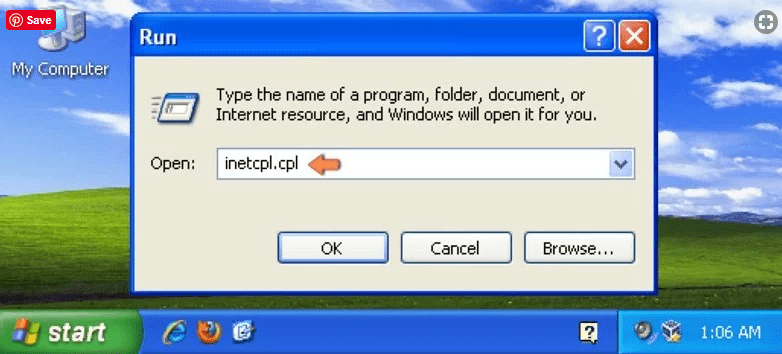
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
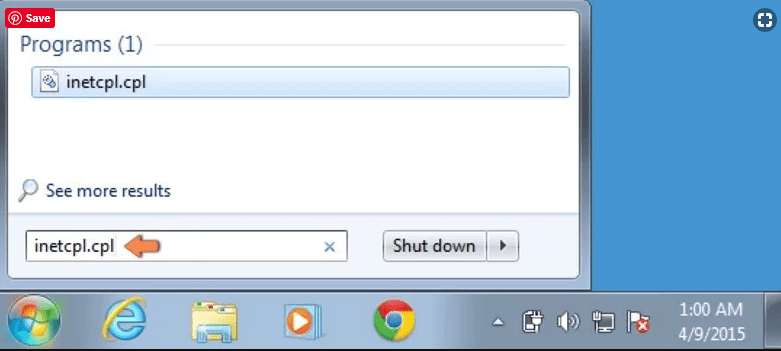
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
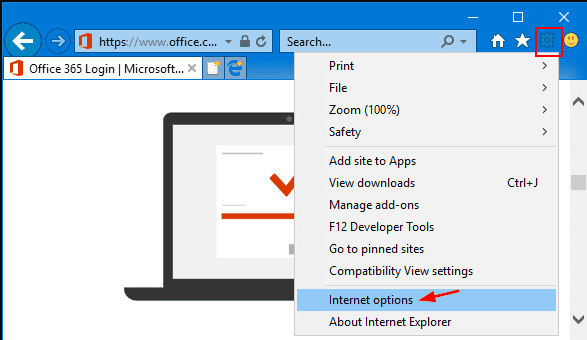
Select the “Advanced” tab in the newly opened window
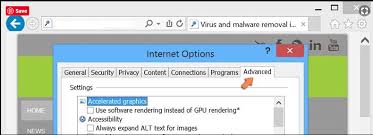
Press on “Reset” option
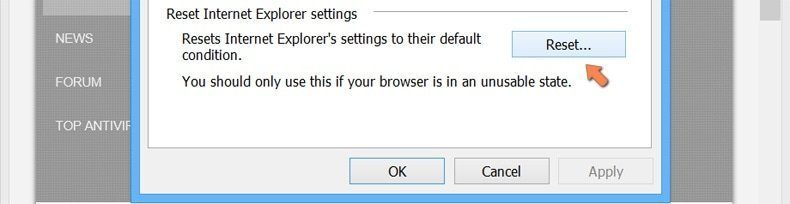
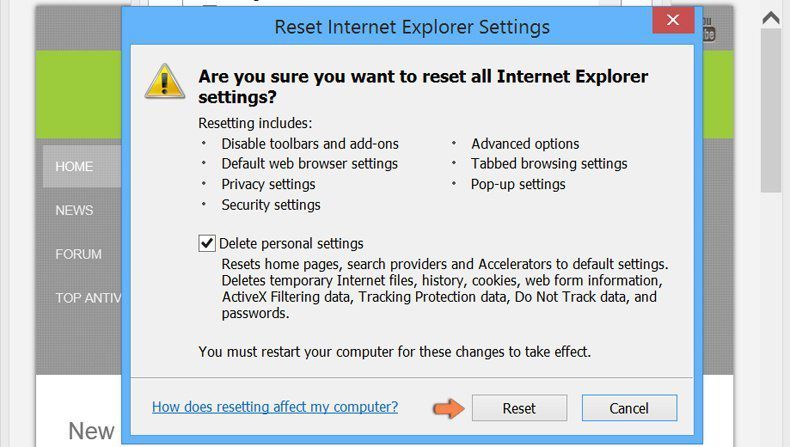
You have to press on the “Reset” button again to confirm that you really want to reset the IE
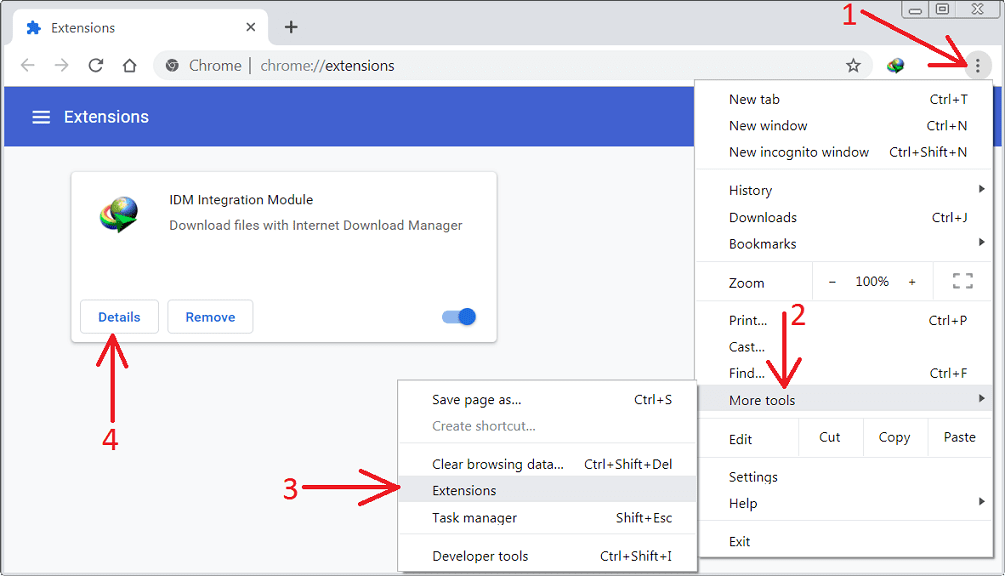
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
Optional Method
If the problems related to browser-hijacker still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
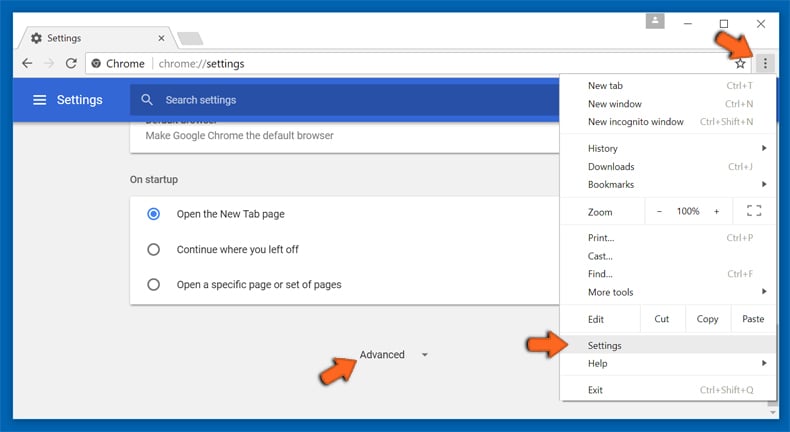
At the bottom, notice the “Reset” option and click on it.
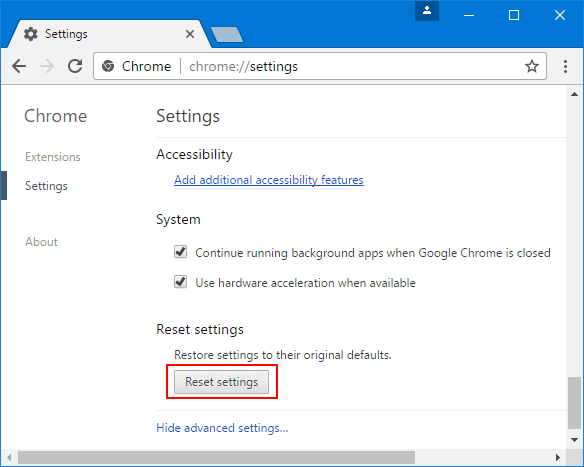
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
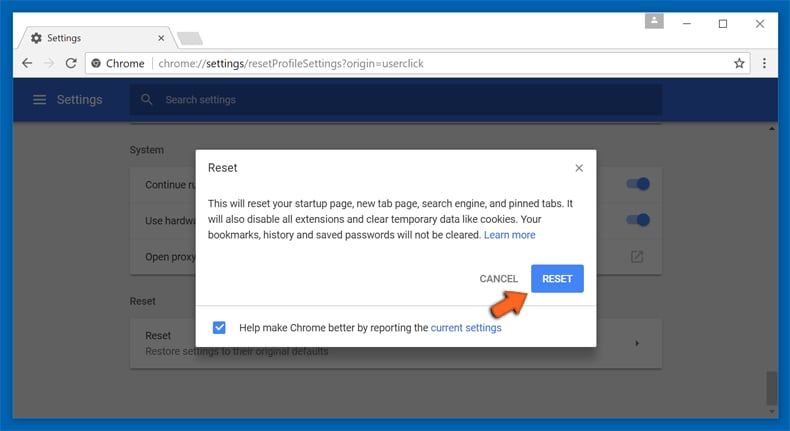
Remove browser-hijacker plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
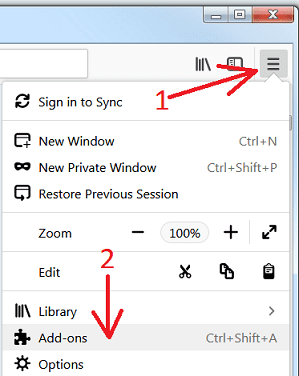
Optional Method
If you face problems in browser-hijacker removal then you have the option to rese the settings of Mozilla Firefox.
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
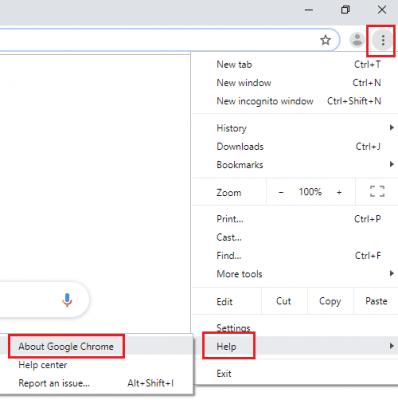
Choose “Troubleshooting Information”
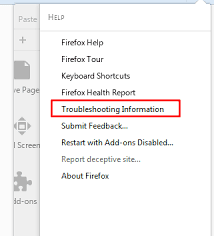
In the newly opened pop-up window, click “Refresh Firefox” button
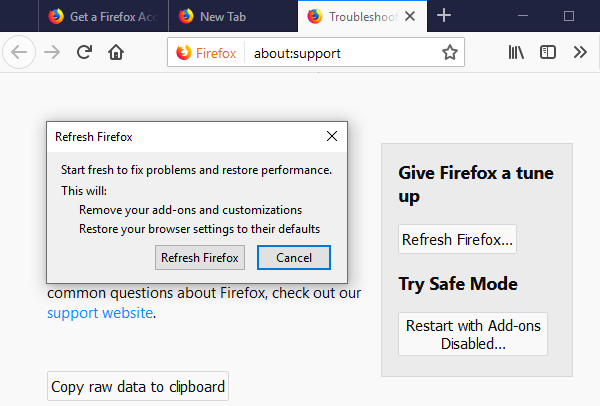
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
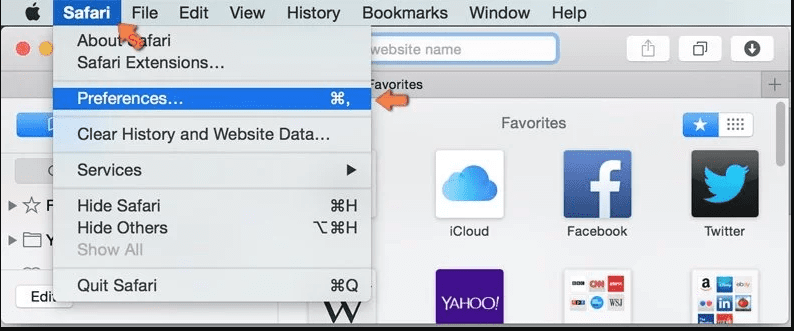
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
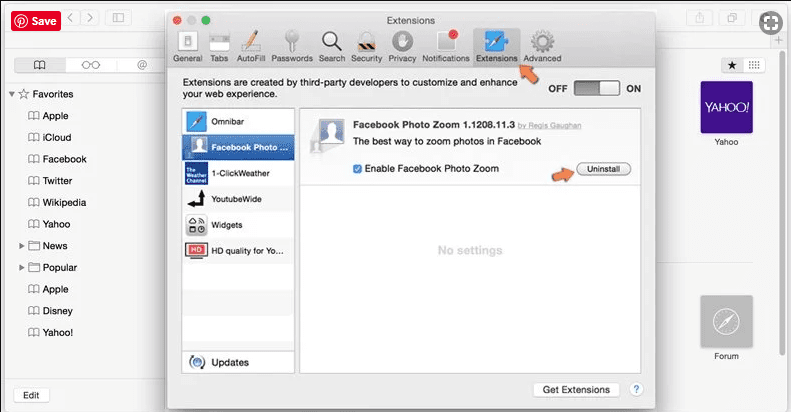
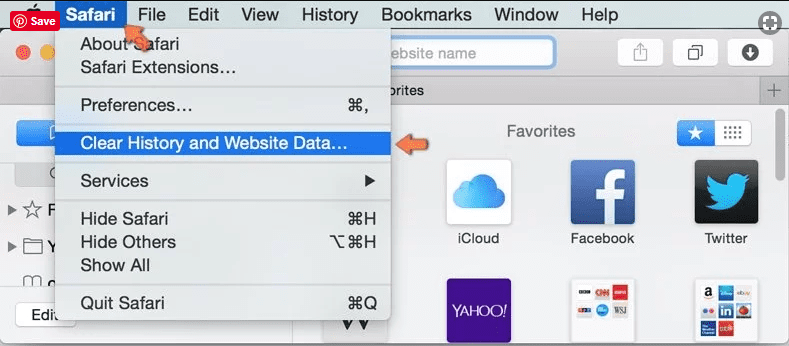
Optional Method
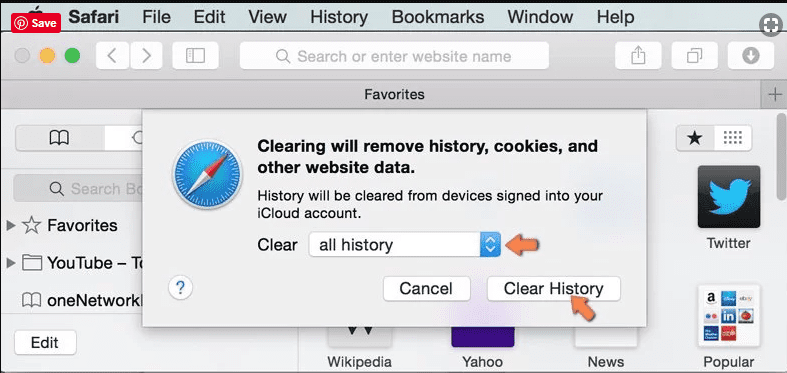
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
In the newly opened window, select “All History” and then press on “Clear History” option.
Delete browser-hijacker (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
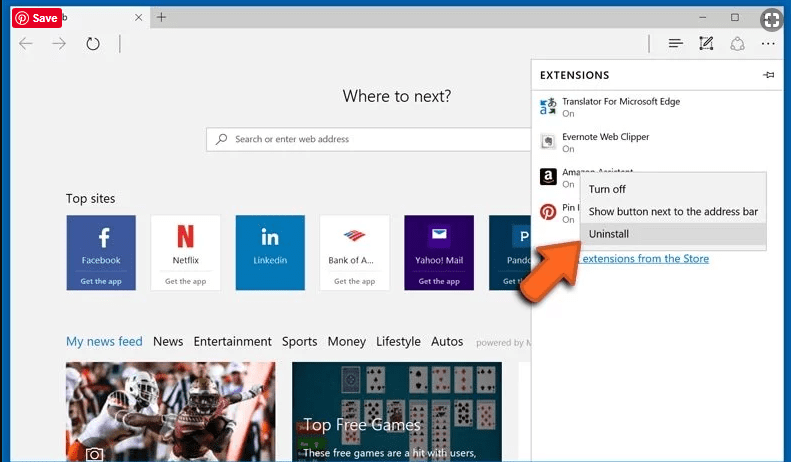
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
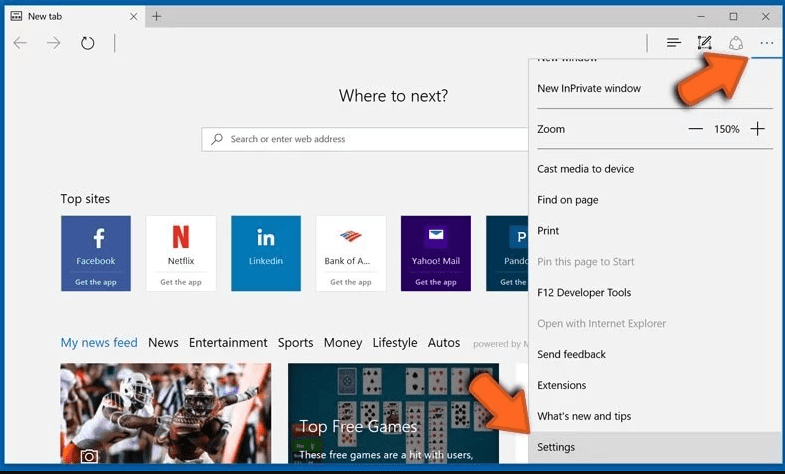
Next steps is to click on “Choose what to clear” button
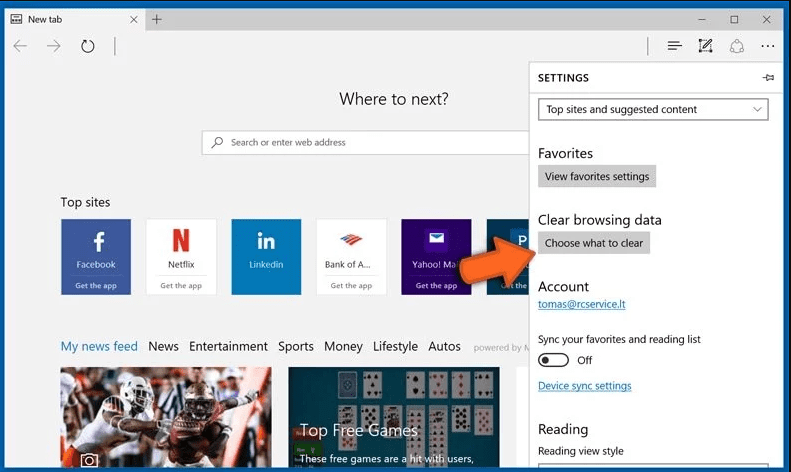
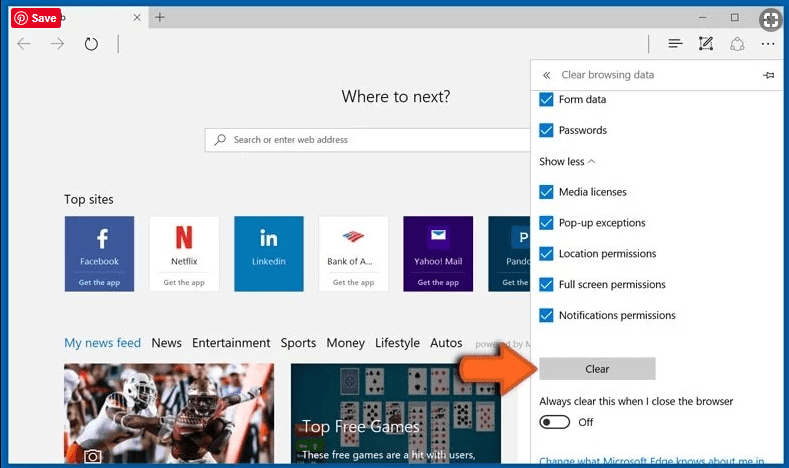
Click on “show more” and then select everything and then press on “Clear” button.
Recommended online habits you should acquire?
As soon as browser-hijacker infiltrates the PC system, it starts carrying out malicious activities in the background and may lead to a number of unpleasant issues. To avoid getting infected with such browser-based pests, below are some steps you can take:
- Download software from reputable sources: Only download software from reputable websites, such as the official page of the software vendor or well-known download portals. Avoid downloading software from third-party websites or peer-to-peer networks, as these are often sources of bundled adware.
- Pay attention during the installation process: When installing software, pay attention to each step of the installation process. Look for the checkboxes that may indicate the installation of additional software, such as adware or browser extensions. Uncheck these boxes if you don’t want to install the additional software.
- Choose custom installation: During the installation process, choose the custom installation option instead of the default or express installation. This will allow you to select which components to install and to opt-out of installing any bundled adware or other unwanted software.
- Read the End User License Agreement (EULA): Read the EULA carefully before installing any software. Look for clauses that may allow the installation of additional software or adware like browser-hijacker. If EULA contains such clauses, reconsider installing the software.
- Use a reputable web browser: Choose a reputable web browser, such as Google Chrome or Mozilla Firefox, and keep it up-to-date with the latest security patches.
- Install ad-blockers and pop-up blockers: You should use ad-blockers and pop-up blockers to prevent unwanted ads and pop-ups from appearing on your computer screen. Some web browsers have built-in ad-blocker and pop-up blockers, or you can install browser extensions that provide this functionality.
- Be careful when clicking on links: Don’t click on links in emails or on websites unless you are sure they are legitimate. Check the URL and ensure it is spelled correctly and is the correct website. Be wary of shortened URLs or URLs that lead to suspicious or unknown websites.
- Keep your web browser and operating system up-to-date: Regularly install software updates and security patches for your web browser and operating system. This will help to close any security vulnerabilities that adware, hijacker and other malware may exploit.
- Use a reputable antivirus program: A good antivirus program can detect and block infections like browser-hijacker and other malware before they can infect your computer. Make sure you choose a reliable antivirus suite and keep it up-to-date with the latest virus definitions.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your PC system safe and secure.
Conclusion:
To sum up, browser-hijacker can cause significant problems for computer users, including unwanted browser redirects, changes to homepage and search engine settings, and even the installation of additional malware. These infections typically result from downloading and installing software from untrusted sources or clicking on suspicious links. To prevent browser hijackers or adware, it is important to be cautious when downloading and installing software, use reputable antivirus tool, and keep browsers and operating systems updated with the latest security patches.
Related FAQs about browser-hijacker
What are the Symptoms of Browser-hijacker ?
The common symptoms of browser-hijacker infection include changes to the default homepage and search engine, unwanted toolbars and extensions, pop-up ads, and redirects to unfamiliar websites. Additionally, the browser may slow down or crash frequently, and search results may be manipulated or irrelevant to the query.
What Should I do if my PC gets infected with virus like browser-hijacker?
If your computer is infected with this browser-based threat, you should immediately run a virus scan using reputable antivirus software. If the software detects the malware, you should follow the removal instructions provided by it to eliminate the infection and restore your browser settings to default.
How can I protect my password and other personal credentials from browser-hijacker?
To protect your password and other sensitive information from browser-hijacker, you should employ reputable antivirus suite, enable two-factor authentication on all accounts, and use strong and unique passwords for each account. Also, you should avoid clicking on suspicious links or downloading software from untrusted sources.
Why I should trust your research conducted on browser-hijacker?
It’s important to mention that our research is conducted independently and with the assistance of unbiased security experts, who provide us with daily updates on the latest definitions and threats related to malware, adware, and browser hijackers. Moreover, our study on the browser-hijacker threat is supported by VirusTotal.
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.


