How to remove Your MAC has been blocked due to suspicious activity! Scam from Mac
Easy tips to delete Your MAC has been blocked due to suspicious activity! Scam
Usually, tech support scams are used by scammers to offer some legit tech support services. Their pages show certain type of virus alert, or there is another problem that is to be solved immediately. Their main motive is to trick the unsuspecting users into calling into the provided number and then paying them money for some unnecessary software, services or providing them remote access to the system for the supposedly fix. Tech support scam pages get opened through shady ads, websites or installed potentially unwanted applications.
The Your MAC has been blocked due to suspicious activity! Scam page displays a fake virus notification informing its visitor that their computer has been blocked because of suspicious activity and virus infection. It urges them to call the number – 1855-948-3710 belongs to the scammers behind it to fix the issues immediately. It claims not to close this website as this may leave the computer damaged and vulnerable. As said, this is tech support scam and so you should not believe on any such claims. These are just to trick you into paying money for unnecessary and/ or fake software or services, or providing remote access to the computer.
Scammers may use the provided remote access to steal personal or financial data like credit card info, social security numbers, log-in data or infect computers with malware like Ransomware and Trojans or install other unwanted software like cryptocurrency miner, adware. It is important to note that the websites promoting such scams are often disguised as official Apple, Microsoft or other company websites. In one way or another, these pages should have to be ignored – all the viruses and error notifications that they display are not real.
As said, tech support pages and other deceptive pages are often visited not on purpose. Usually, people come to these sites via visiting other pages of this kind, deceptive ads or PUAs. PUAs can be designed to collect browsing based data and other data and generate intrusive ads as well. They target the data like:
- IP addresses,
- Search queries,
- Viewed pages,
- URLs visited and etc.
Some of the PUAs can collect personal data like credit card info and passwords as well. The collected data could be shared and/or sold to third parties or potent crooks or monetized in some other ways. Ads that these apps promote are coupons, banners, pop-ups and so on. They promote various questionable pages. Sometimes, they might run certain scripts to cause unwanted download. So, when you receive Your MAC has been blocked due to suspicious activity! Scam, you should check the system for any such virus infection for their removal.
How did PUAs infiltrate my system?
It is very common for PUAs to be distributed through bundling with other programs. In other word, these are offered with the downloaders/ installers of some other software. The offers can be declined before finishing downloads/installations. Users can do this by changing to Advanced/ Custom or other similar settings or by un-ticking the ticked checkboxes. When users download, install programs bundled with PUAs without making any of those changes, they agree to the download, install of those apps. Sometimes, users download PUAs by clicking intrusive ads that are designed to run certain scripts.
Full text on Your MAC has been blocked due to suspicious activity! Scam pop-up page:
WARNING!
Your MAC has been blocked due to suspicious activity! Please call Support Now!. Call 1855-948-3710 (Toll Free) To find right solution.
Are you sure you want to leave this page?
[Leave Page][Stage On Page]
Second pop-up of Your MAC has been blocked due to suspicious activity! Scam page says:
WARNING!
MAC OS X is infeted with Viruses and other malicious applications.
Viruses must be removed and system damage repaired.
It is necessary to run the Virus removal procedure immediately, please proceed.
**If you leave this site your Mac OS X will remain damaged and vulnerable**
Call Apple Helpline 1855-948-3710 (Toll Free)
[Back To Safe][Leave Page]
How to prevent PUAs installation?
It is not recommended to trust apps, files downloaded from unofficial websites, through torrent clients, eMule and other p2p networks via third-party downloaders or use third-party installers to install any apps. It is common that the aforementioned sources or tools are used to distribute unwanted, potentially malicious files and apps. Prefer only official websites and direct links for any download. Furthermore, downloaders/ installers with Custom/Advanced option and ticked checkboxes should have to be checked for additional apps. Ads on questionable pages should not be trusted as well. These ads can be designed to promote shady pages, potentially malicious apps.
Special Offer (For Macintosh)
Your MAC has been blocked due to suspicious activity! Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Remove Files and Folders Related to Your MAC has been blocked due to suspicious activity! Scam
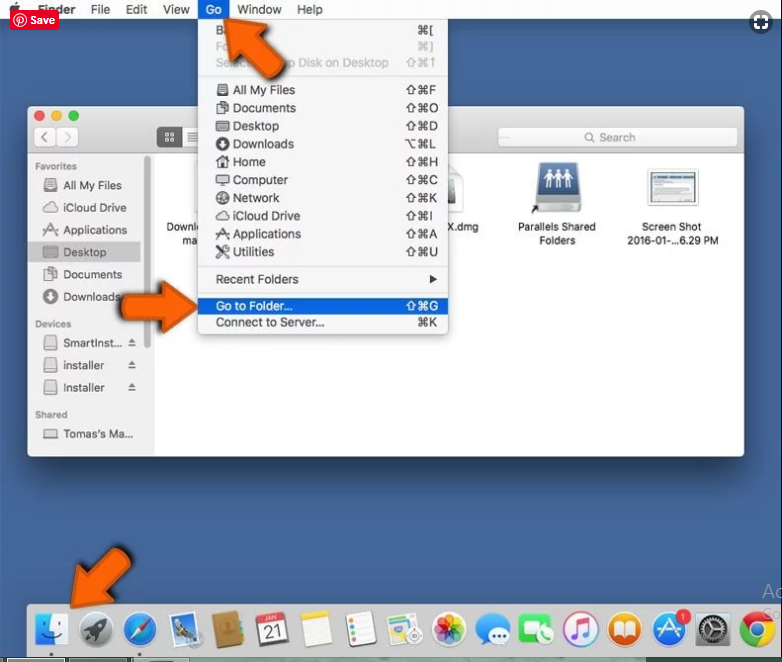
Open the “Menu” bar and click the “Finder” icon. Select “Go” and click on “Go to Folder…”
Step 1: Search the suspicious and doubtful malware generated files in /Library/LaunchAgents folder
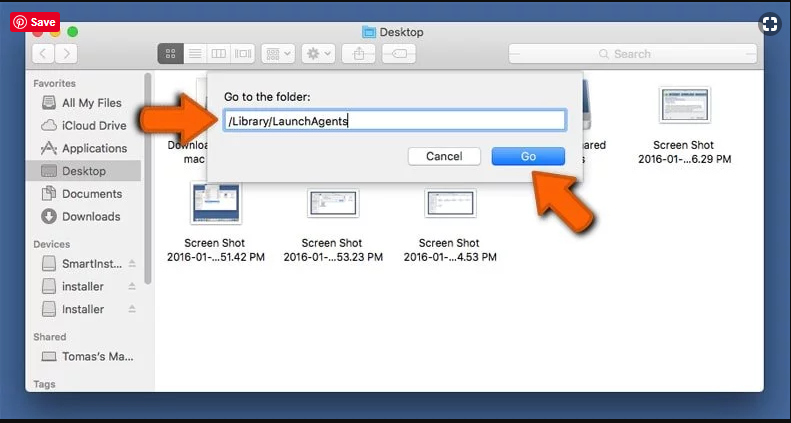
Type /Library/LaunchAgents in the “Go to Folder” option
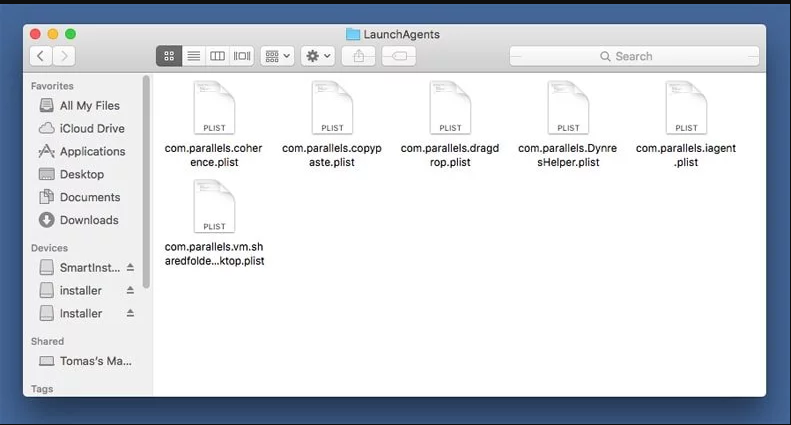
In the “Launch Agent” folder, search for all the files that you have recently downloaded and move them to “Trash”. Few of the examples of files created by browser-hijacker or adware are as follow, “myppes.download.plist”, “mykotlerino.Itvbit.plist”, installmac.AppRemoval.plist”, and “kuklorest.update.plist” and so on.
Step 2: Detect and remove the files generated by the adware in “/Library/Application” Support folder
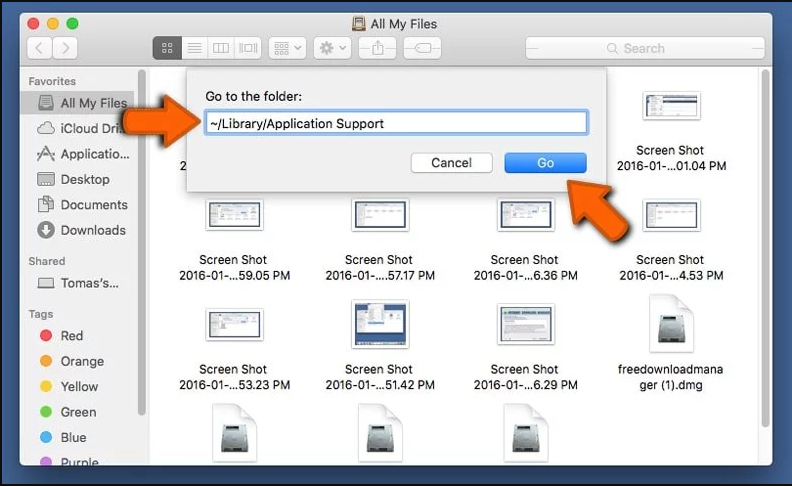
In the “Go to Folder..bar”, type “/Library/Application Support”
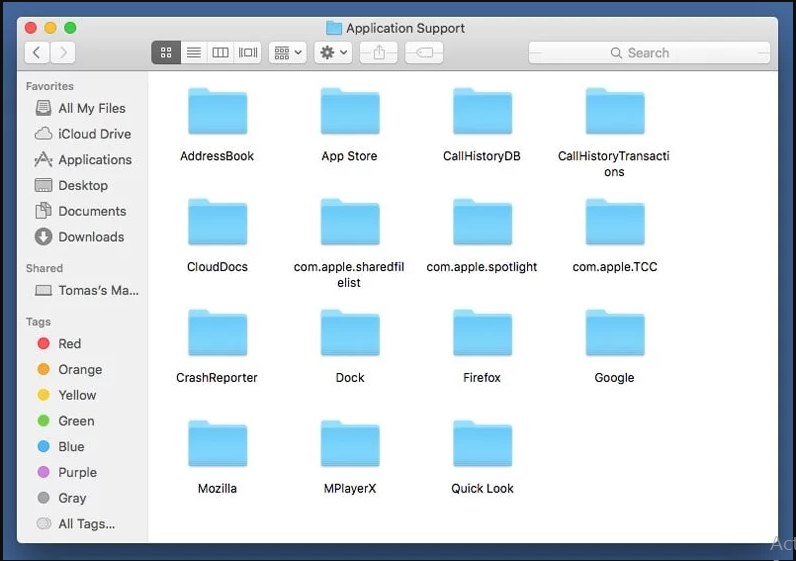
Search for any suspicious newly added folders in “Application Support” folder. If you detect any one of these like “NicePlayer” or “MPlayerX” then send them to “Trash” folder.
Step 3: Look for the files generated by malware in /Library/LaunchAgent Folder:
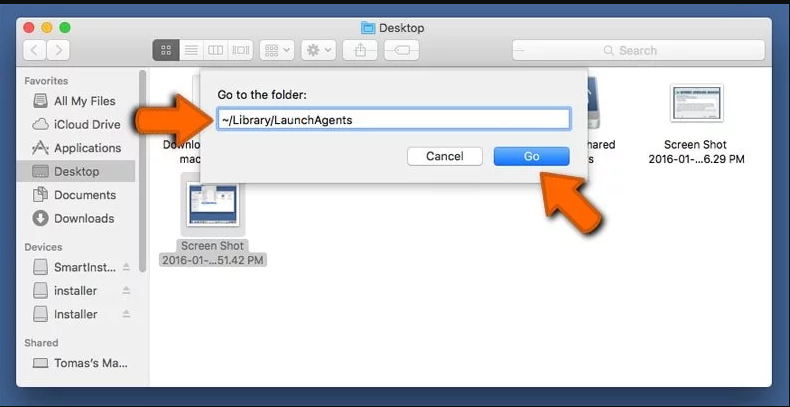
Go to Folder bar and type /Library/LaunchAgents
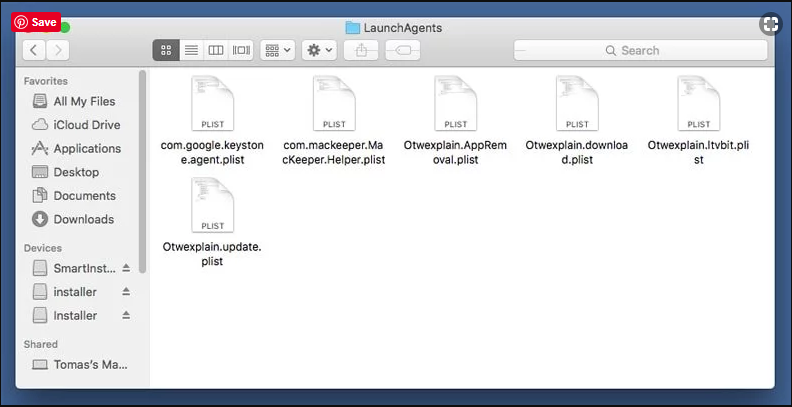
You are in the “LaunchAgents” folder. Here, you have to search for all the newly added files and move them to “Trash” if you find them suspicious. Some of the examples of suspicious files generated by malware are “myppes.download.plist”, “installmac.AppRemoved.plist”, “kuklorest.update.plist”, “mykotlerino.ltvbit.plist” and so on.
Step4: Go to /Library/LaunchDaemons Folder and search for the files created by malware
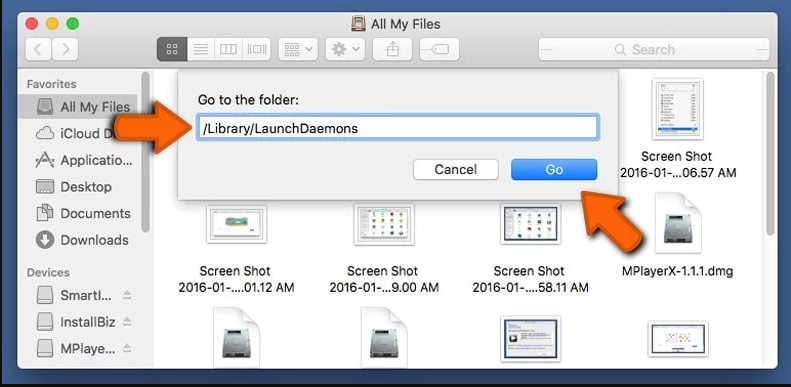
Type /Library/LaunchDaemons in the “Go To Folder” option
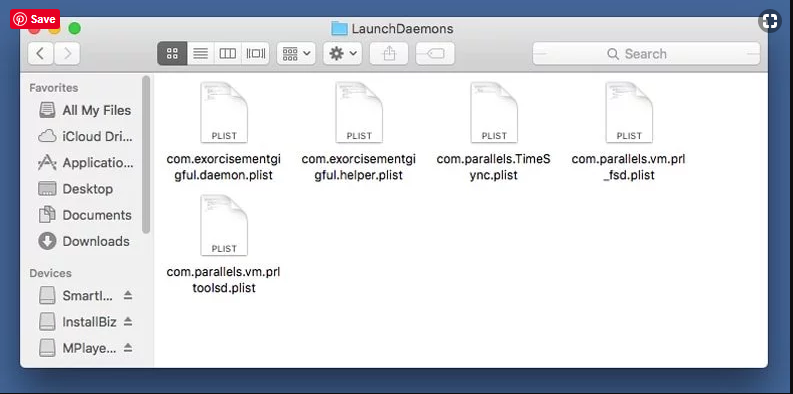
In the newly opened “LaunchDaemons” folder, search for any recently added suspicious files and move them to “Trash”. Examples of some of the suspicious files are “com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, “com.myppes.net-preference.plist”, “com.aoudad.net-preferences.plist” and so on.
Step 5: Use Combo Cleaner Anti-Malware and Scan your Mac PC
The malware infections could be removed from the Mac PC if you execute all the steps mentioned above in the correct way. However, it is always advised to be sure that your PC is not infected. It is suggested to scan the work-station with “Combo Cleaner Anti-virus”.
Special Offer (For Macintosh)
Your MAC has been blocked due to suspicious activity! Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Once the file gets downloaded, double click on combocleaner.dmg installer in the newly opened window. Next is to open the “Launchpad” and press on “Combo Cleaner” icon. It is advised to wait until “Combo Cleaner” updates the latest definition for malware detection. Click on “Start Combo Scan” button.
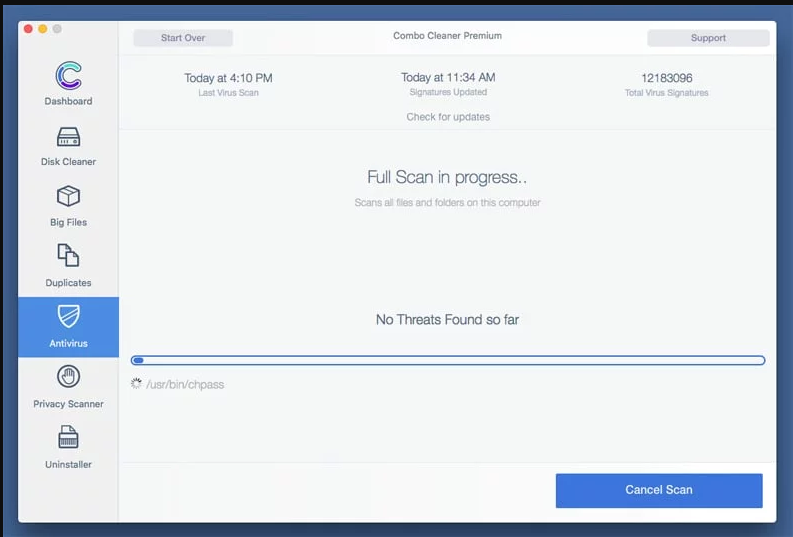
A depth scan of your Mac PC will be executed in order to detect malware. If the Anti-virus scan report says “no threat found” then you can continue with guide further. On the other hand, it is recommended to delete the detected malware infection before continuing.
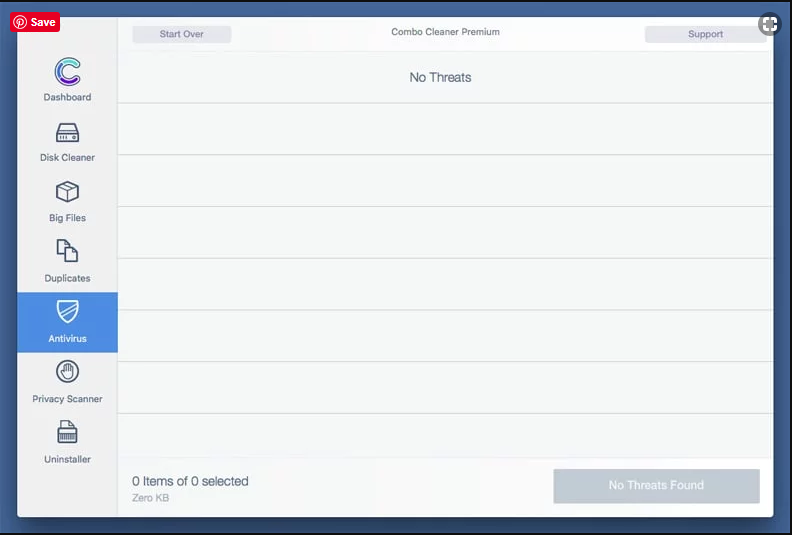
Now the files and folders created by the adware is removed, you have to remove the rogue extensions from the browsers.
Remove Your MAC has been blocked due to suspicious activity! Scam from Internet Browsers
Delete Doubtful and Malicious Extension from Safari
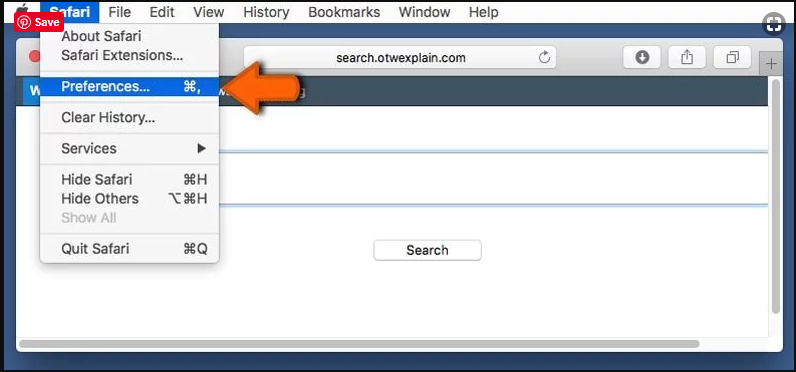
Go to “Menu Bar” and open “Safari” browser. Select “Safari” and then “Preferences”
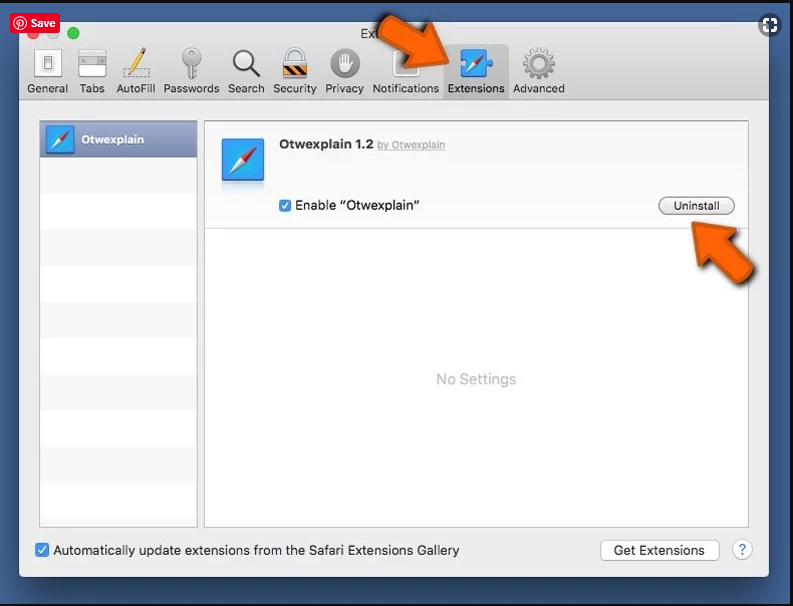
In the opened “preferences” window, select “Extensions” that you have recently installed. All such extensions should be detected and click the “Uninstall” button next to it. If you are doubtful then you can remove all the extensions from “Safari” browser as none of them are important for smooth functionality of the browser.
In case if you continue facing unwanted webpage redirections or aggressive advertisements bombarding, you can reset the “Safari” browser.
“Reset Safari”
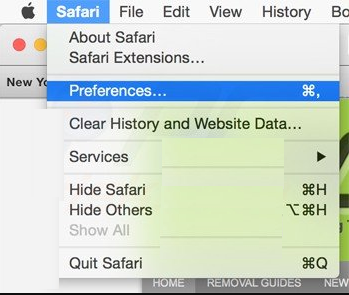
Open the Safari menu and choose “preferences…” from the drop-down menu.
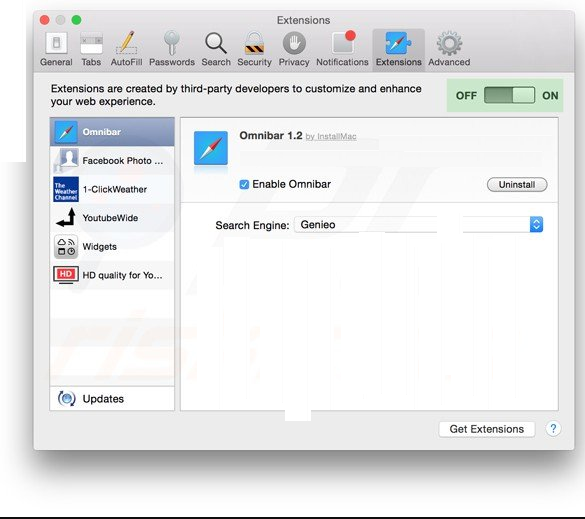
Go to the “Extension” tab and set the extension slider to “Off” position. This disables all the installed extensions in the Safari browser
Next step is to check the homepage. Go to “Preferences…” option and choose “General” tab. Change the homepage to your preferred URL.
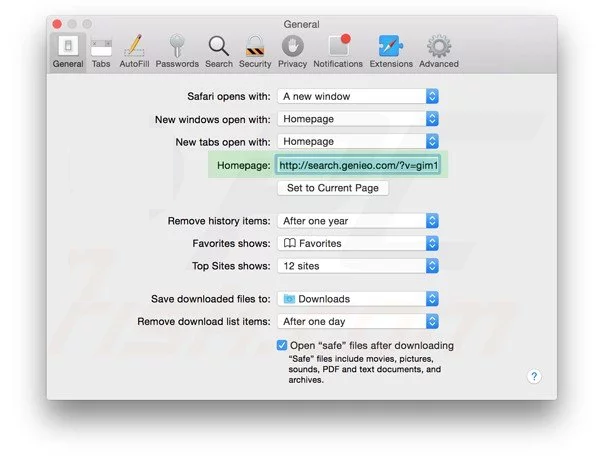
Also check the default search-engine provider settings. Go to “Preferences…” window and select the “Search” tab and select the search-engine provider that you want such as “Google”.
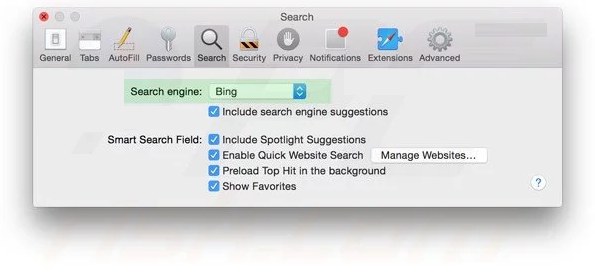
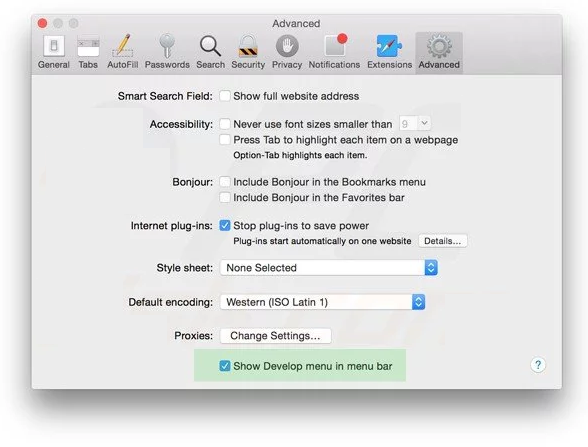
Next is to clear the Safari browser Cache- Go to “Preferences…” window and select “Advanced” tab and click on “Show develop menu in the menu bar.“
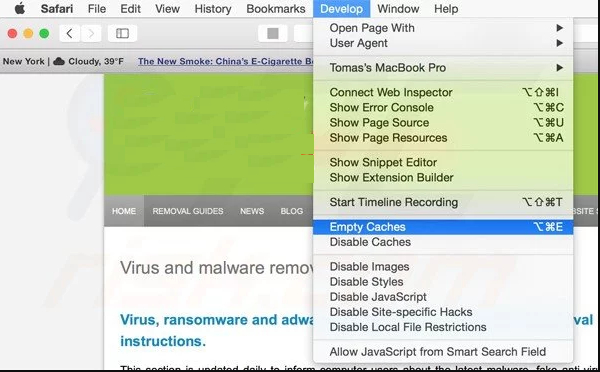
Go to “Develop” menu and select “Empty Caches”.
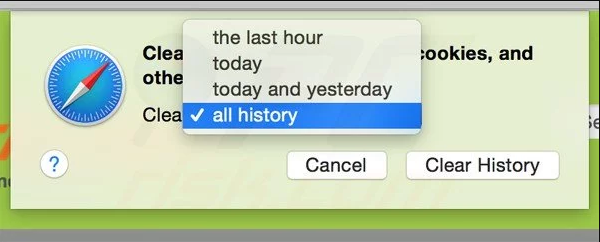
Remove website data and browsing history. Go to “Safari” menu and select “Clear History and Website Data”. Choose “all history” and then click on “Clear History”.
Remove Unwanted and Malicious Plug-ins from Mozilla Firefox
Delete Your MAC has been blocked due to suspicious activity! Scam add-ons from Mozilla Firefox

Open the Firefox Mozilla browser. Click on the “Open Menu” present in the top right corner of the screen. From the newly opened menu, choose “Add-ons”.
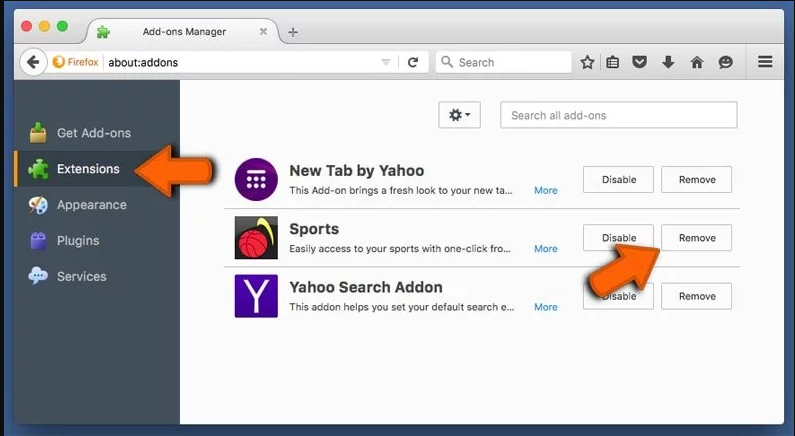
Go to “Extension” option and detect all the latest installed add-ons. Select each of the suspicious add-ons and click on “Remove” button next to them.
In case if you want to “reset” the Mozilla Firefox browser then follow the steps that has been mentioned below.
Reset Mozilla Firefox Settings
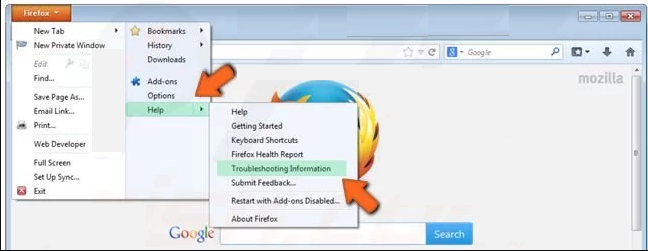
Open the Firefox Mozilla browser and click on “Firefox” button situated at the top left corner of the screen.

In the new menu, go to “Help” sub-menu and choose “Troubleshooting Information”
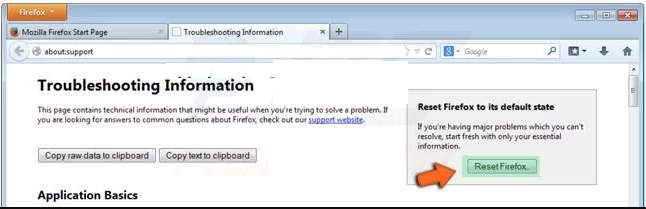
In the “Troubleshooting Information” page, click on “Reset Firefox” button.
Confirm that you want to reset the Mozilla Firefox settings to default by pressing on “Reset Firefox” option
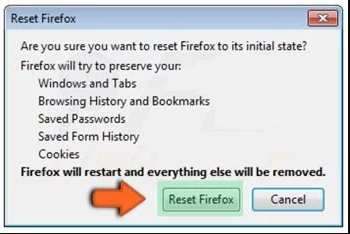
The browser will get restarted and the settings changes to factory default
Delete Unwanted and Malicious Extensions from Google Chrome
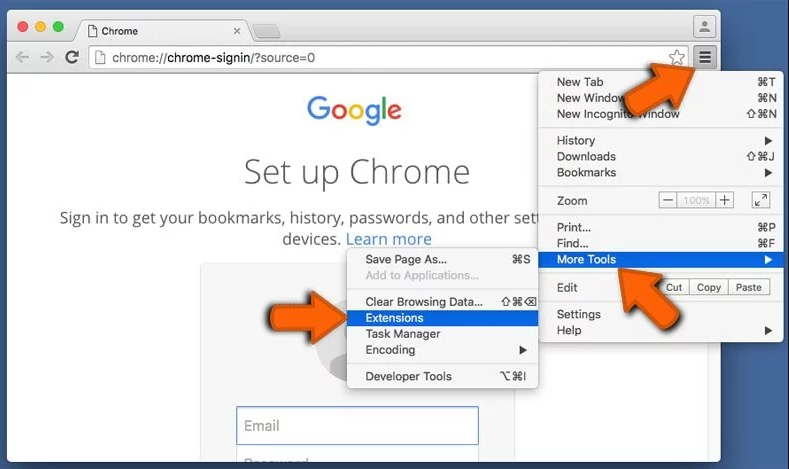
Open the chrome browser and click on “Chrome menu”. From the drop down option, choose “More Tools” and then “Extensions”.
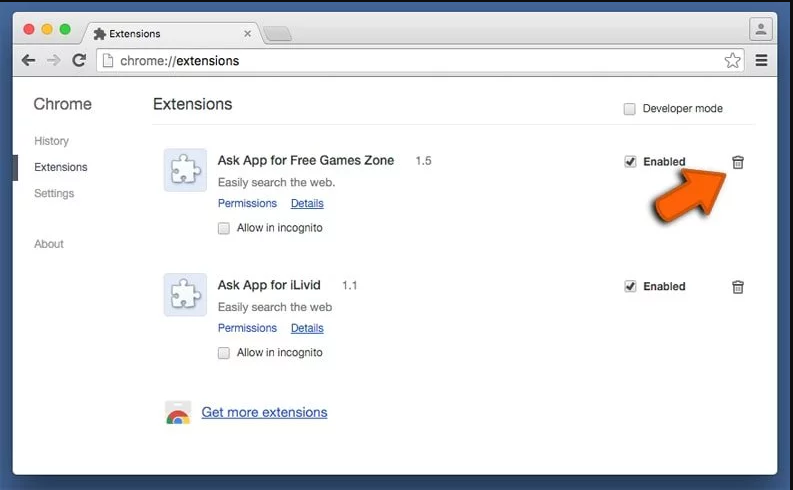
In the “Extensions” option, search for all the recently installed add-ons and extensions. Select them and choose “Trash” button. Any third-party extension is not important for the smooth functionality of the browser.
Reset Google Chrome Settings
Open the browser and click on three line bar at the top right side corner of the window.
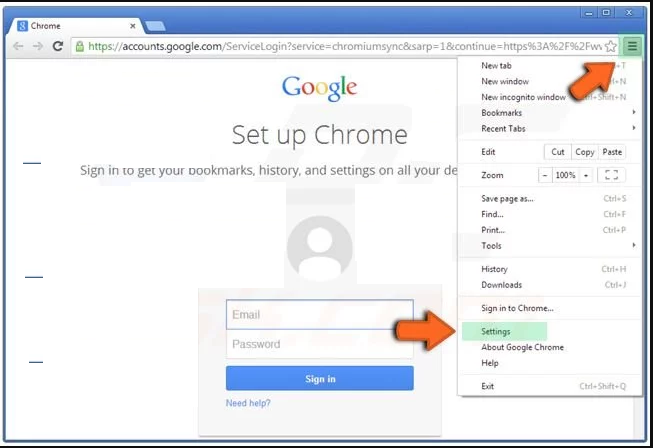
Go to the bottom of the newly opened window and select “Show advanced settings”.
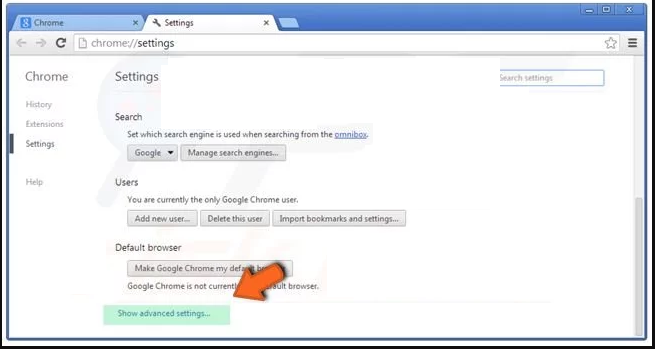
In the newly opened window, scroll down to the bottom and choose “Reset browser settings”
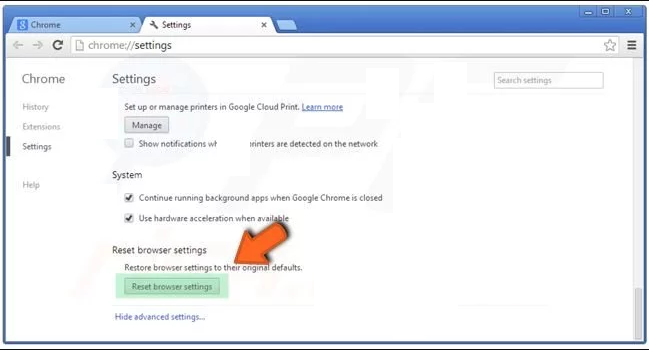
Click on the “Reset” button on the opened “Reset browser settings” window
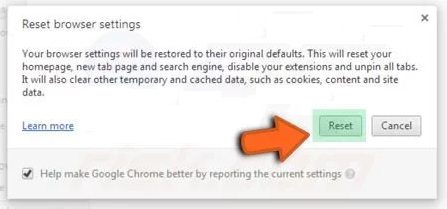
Restart the browser and the changes you get will be applied
The above mentioned manual process should be executed as it is mentioned. It is a cumbersome process and requires a lot of technical expertise. And hence it is advised for technical experts only. To be sure that your PC is free from malware, it is better that you scan the work-station with a powerful anti-malware tool. The automatic malware removal application is preferred because it doesn’t requires any additional technical skills and expertise.
Special Offer (For Macintosh)
Your MAC has been blocked due to suspicious activity! Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful antimalware scanner to help you getting rid of this virus
Download the application and execute it on the PC to begin the depth scanning. Once the scanning gets completed, it shows the list of all the files related to Your MAC has been blocked due to suspicious activity! Scam. You can select such harmful files and folders and remove them immediately.




