How to remove Your Device Was Compromised Email Scam
Easy tips to delete Your Device Was Compromised Email Scam
Usually, scammers use sextortion based spam emails to threaten the recipients that they have their embarrassing images or videos and ask them payment for not releasing it to their contacts. Your Device Was Compromised Email Scam is one such sextortion based scam.

The scammers behind this scam claim that they have collected the information like the visited websites and sent text messages. Also, they claim to have had access to their webcam and microphone. Their main aim is to make the recipients believe that the collected information will be sent to the people in their contact if they do not pay them $1650 in Bitcoins.
Users must know these people actually do not have any such compromised or sensitive material. They are usually false claims so as to make people pay money to them. You require ignoring Your Device Was Compromised Email Scam and any such scam emails.
It is worth mentioning that such emails usually have spoofed senders’ email address. The email appears to be coming from the address of the targeted victim. This technique is used to trick people into believing that the scammers have broken their accounts or even computers.
Another technique that they use is to put the recipients’ passwords in the emails. These passwords are usually the old ones. The scammers managed to collect these passwords available on the dark web leaked after data breaches.
How do spam emails cause system infection?
Crooks may use spam emails to deliver malware. They spread malware through the suspicious links or files in them. Their main motive is to trick people into downloading and then opening/ executing these files that trigger the malware download/ installation.
These email attachments are usually presented as some documents, for example, purchasing orders or invoices. Although these attachments are malicious – they are designed to infect systems with Trojans, Ransomware or other malicious malware.
Usually, the emails used to spread malware contain malicious Microsoft Office documents, PDFs, archives, JavaScript and some executables as file attachments. The infection is caused when these files are being executed.
Text presented in Your Device Was Compromised Email Scam page:
Subject: With reference to your cloud storage
I am sorry to inform you that your device was compromised.
I’ll explain what led to all of this. I have used a Zero Day vulnerability with a special code to infect your device through a website.
This is a complicated software that requires precise skills that I have. It works as a chain with specially crafted and unique code and that’s why this type of an attack can go undetected.
You only need one not patched vulnerability to be infected, and unfortunately for you – it works that simple.
You were not targeted specifically, but just became one of the quite a few unlucky people who got hacked that day.
All of this happened a few month ago. So I’ve had time to collect information on you.
I think you already know what is going to happen next.
During that time, my software was quietly collecting c
There is more to it, but I have listed a few reasons for you to understand how serious this is.
For you to clearly understand, my software controlled your camera and microphone as well and it was impossible for you to know about it.
It was just about right timing for me to get you privacy violated.
I’ve been waiting enough and have decided that it’s time to put an end to this.
So here is my offer. Let’s name this a “consulting fee” I need to delete the media content I have been collecting.
Your privacy stays untouched, if I get the payment.
Otherwise, I will leak the most damaging content to your contacts and post it to a public tube for perverts to explore.
I understand how damaging this will be for you, and amount is not that big for you to keep your privacy.
Please dont blame me – we all have different ways of making a living.
I have no intention of destroying your reputation or life, but only if I get paid.
I don’t care about you personally, that’s why you can be sure that all files I have and software on your device will be deleted immediately after I receive the transfer.
I only care about getting paid.
My modest consulting fee is 1650 US Dollars transferred in Bitcoin. Exchange rate at the time of the transfer.
You need to send that amount to this wallet: 1C8a9b9X5vVCDNbspzxFYiJGAR5v9YMPtF
The fee is non negotiable, to be transferred within 2 business days.
We use Bitcoin to protect my identity.
Obviously do not try to ask for any help from anybody unless you want your privacy to violated.
I will monitor your every move until I get paid. If you keep your end of the agreement, you wont hear from me ever again.
Take care.
How to avoid installation of malware?
It is impotent to update and activate installed software using implemented tools/ functions from official software developers. Websites and links on any irrelevant emails should never be opened, especially the ones from unknown, suspicious senders. Furthermore, it is advised to download software through official websites.
Additionally, it is advised to scan the system for viruses regularly and to do this, use some reputable antivirus tool. To ensure that Your Device Was Compromised Email Scam didn’t make a virus entry, you should run a full system scan using such antivirus suite on system. If you find there is any, perform its removal without delay.
Special Offer (For Windows)
Your Device Was Compromised Email Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Your Device Was Compromised Email Scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
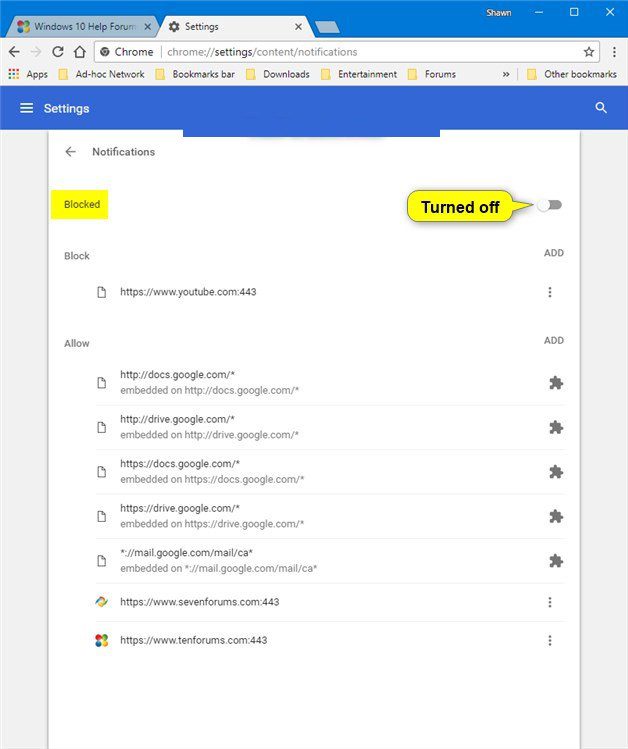
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
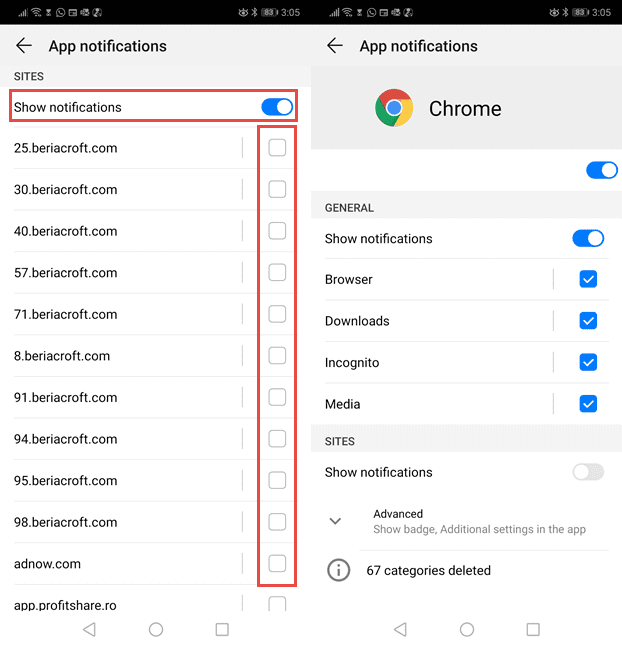
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
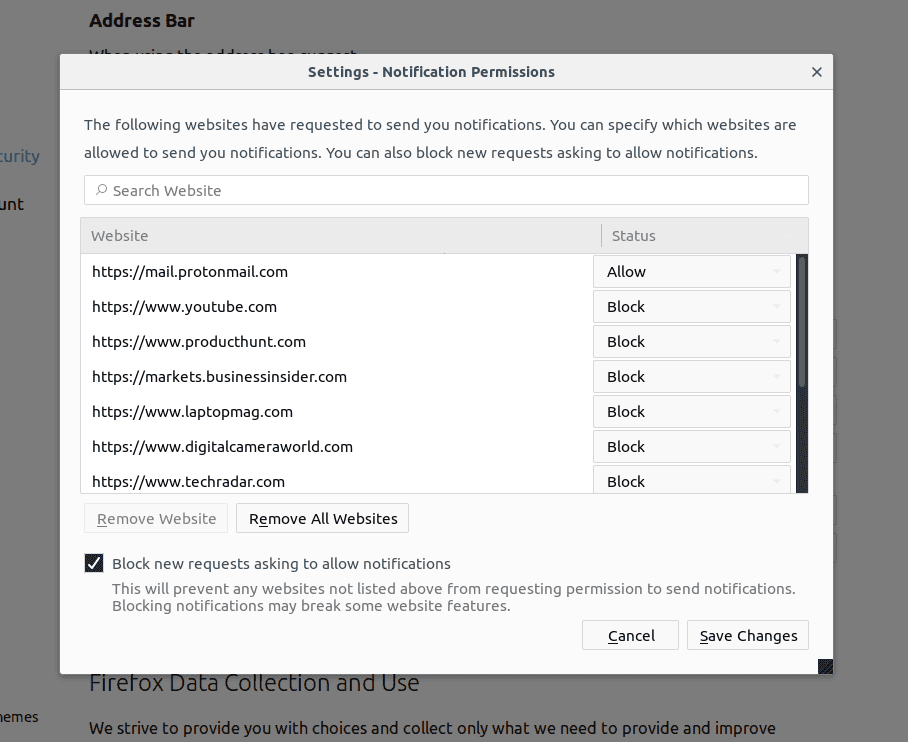
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
Internet Explorer
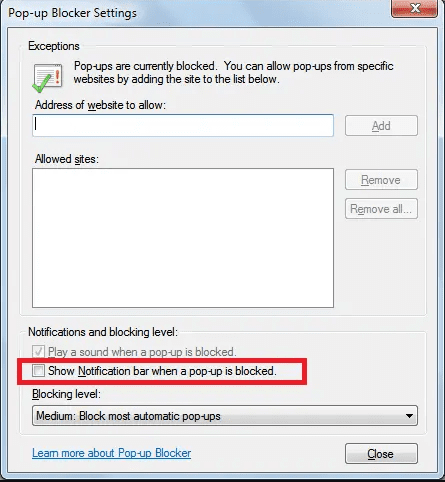
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
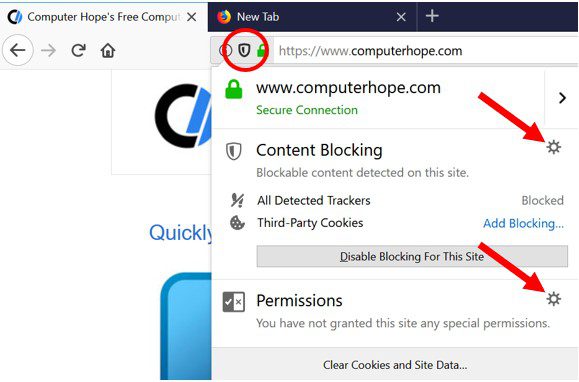
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
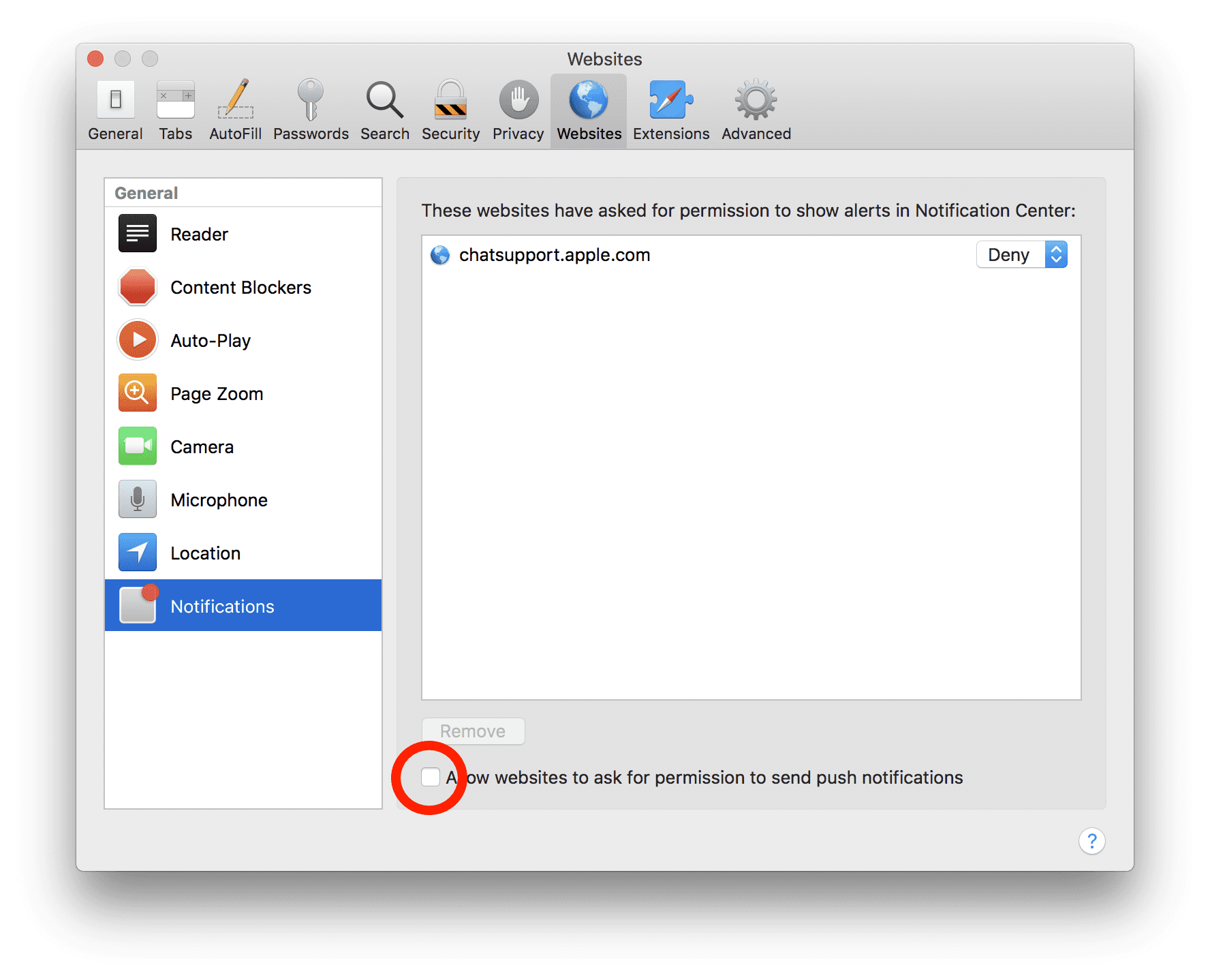
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Your Device Was Compromised Email Scam:
Remove the related items of Your Device Was Compromised Email Scam using Control-Panel
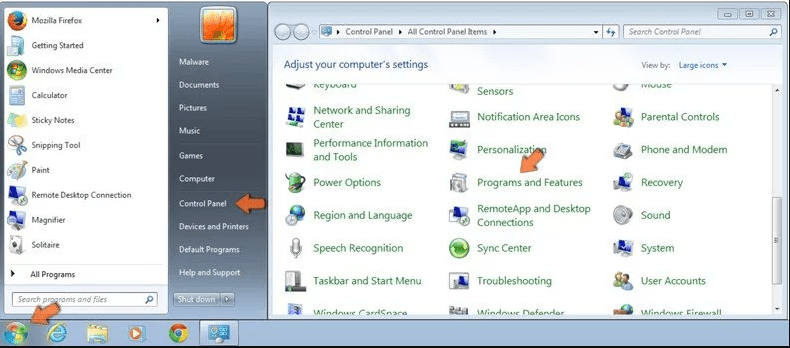
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
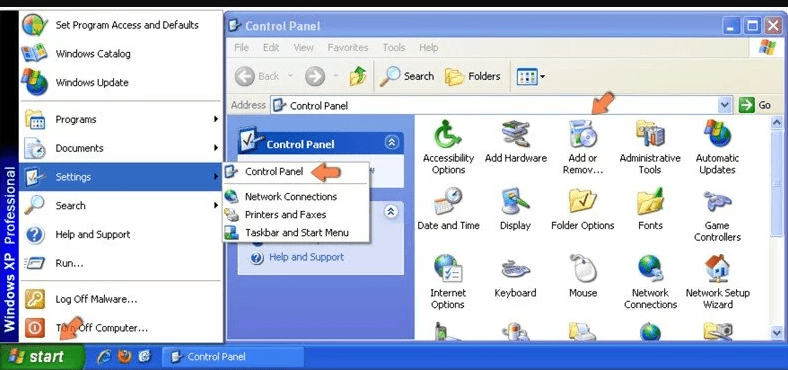
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
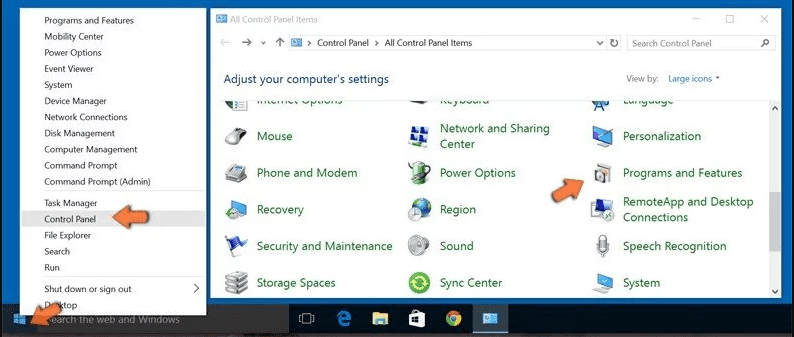
Mac OSX Users
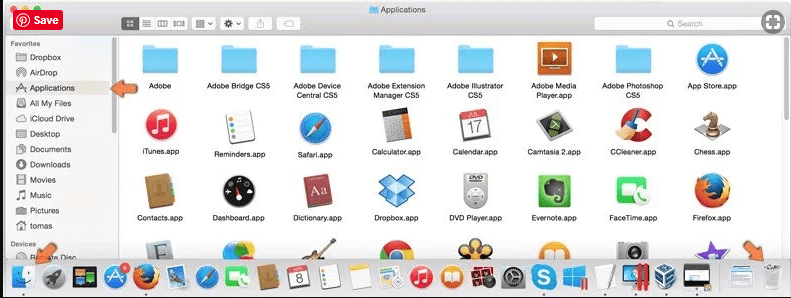
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
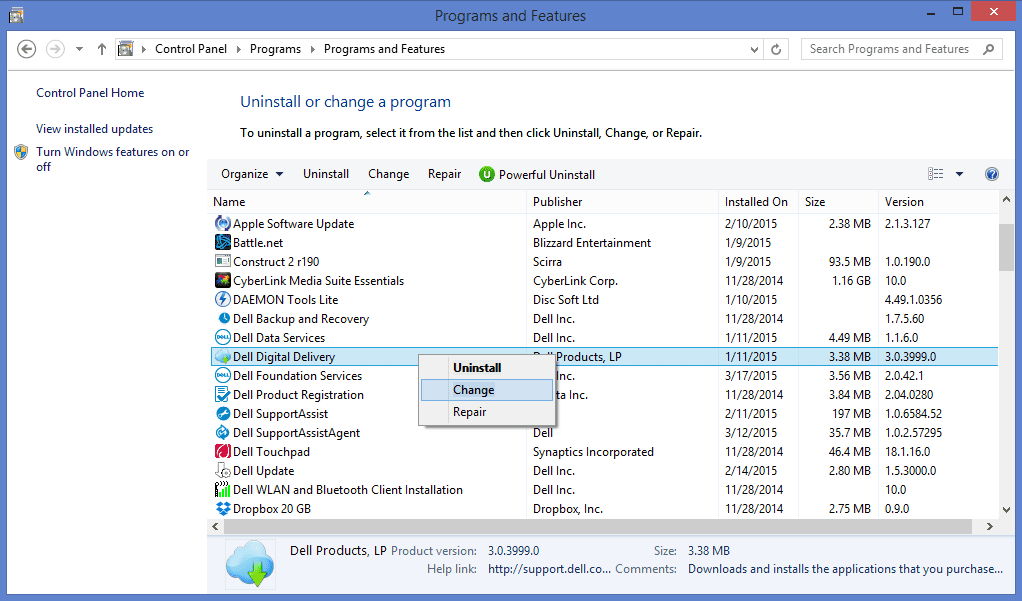
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Your Device Was Compromised Email Scam issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Your Device Was Compromised Email Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Your Device Was Compromised Email Scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Your Device Was Compromised Email Scam) from Internet Browsers
Delete malicious add-ons and extensions from IE
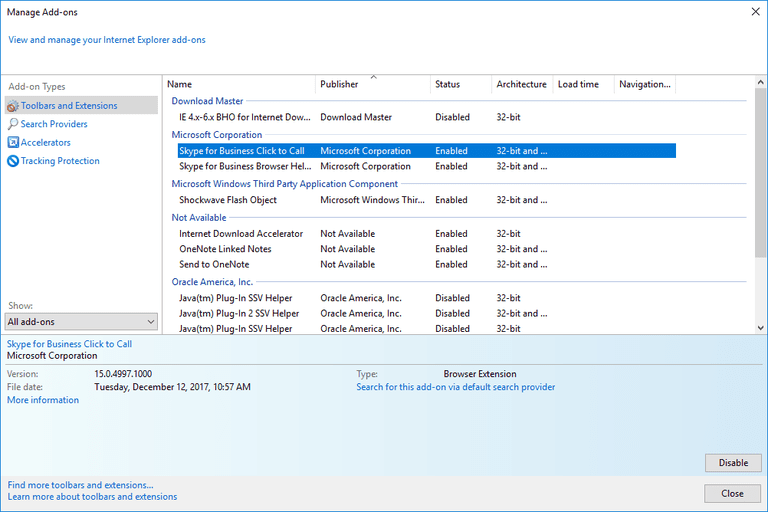
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
Additional Option
If you still face issues related to Your Device Was Compromised Email Scam removal, you can reset the Internet Explorer to its default setting.
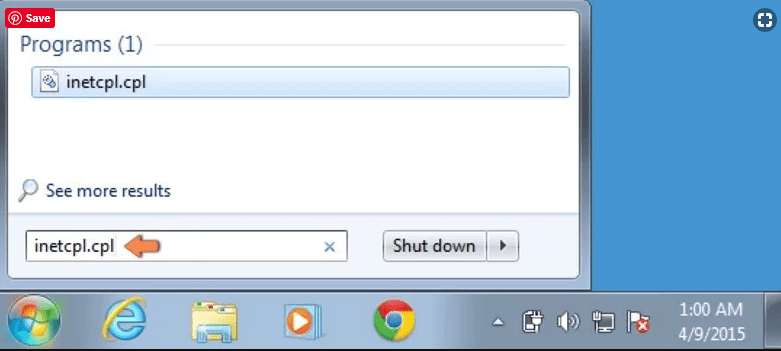
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
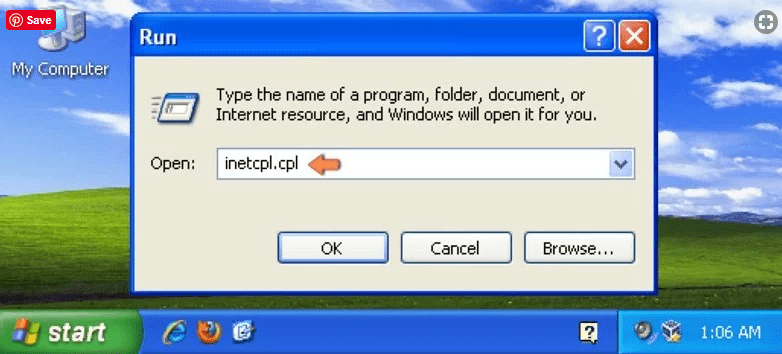
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
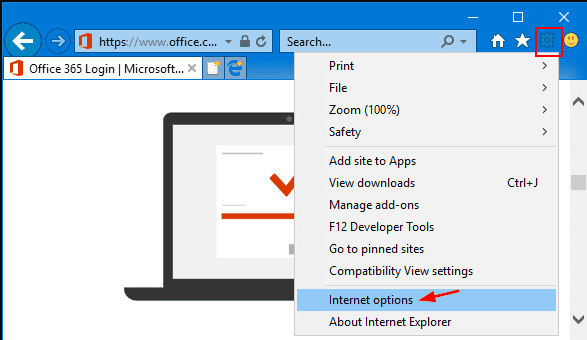
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
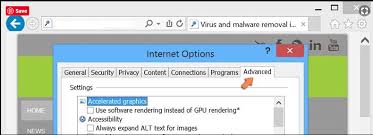
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
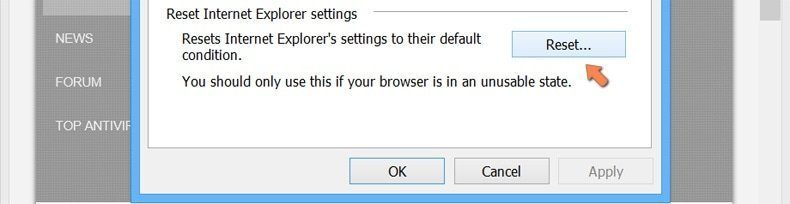
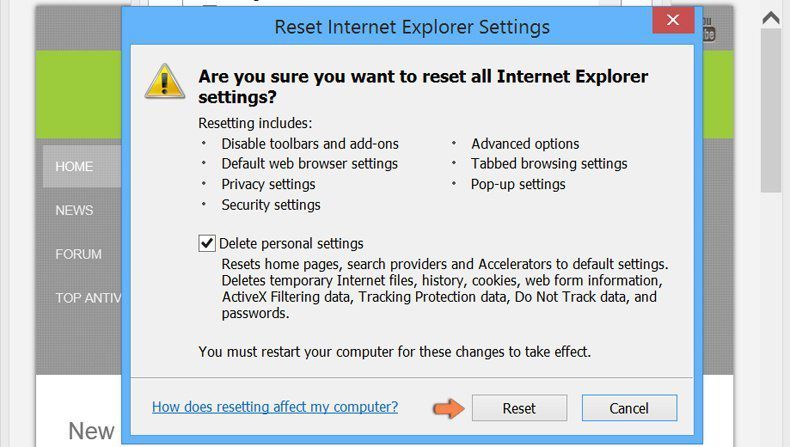
You have to press on the “Reset” button again to confirm that you really want to reset the IE
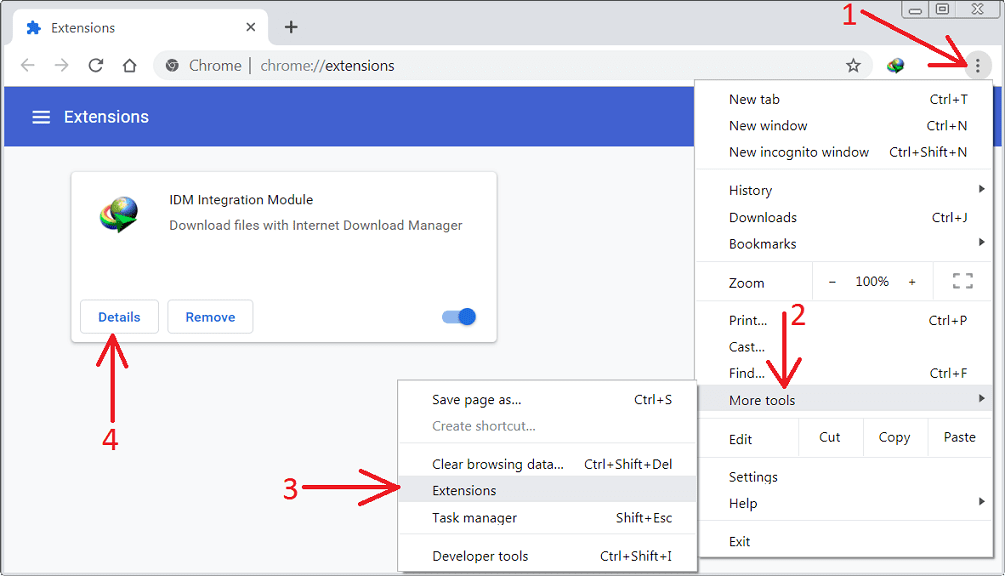
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
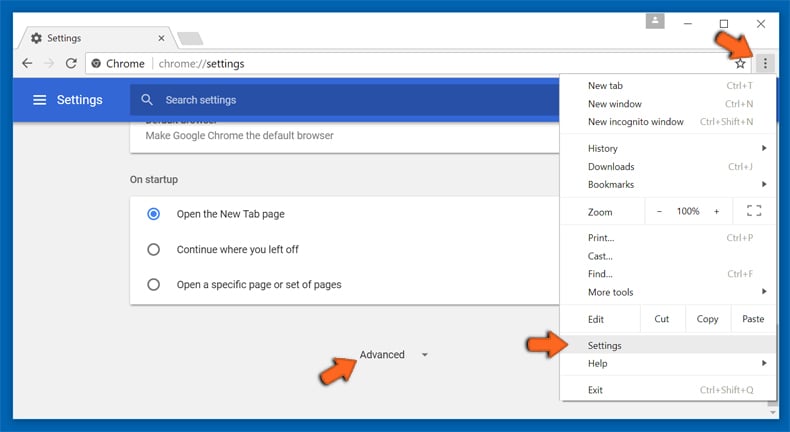
Optional Method
If the problems related to Your Device Was Compromised Email Scam still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
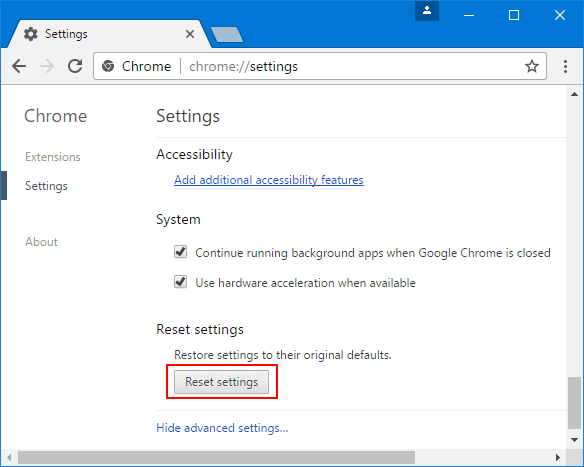
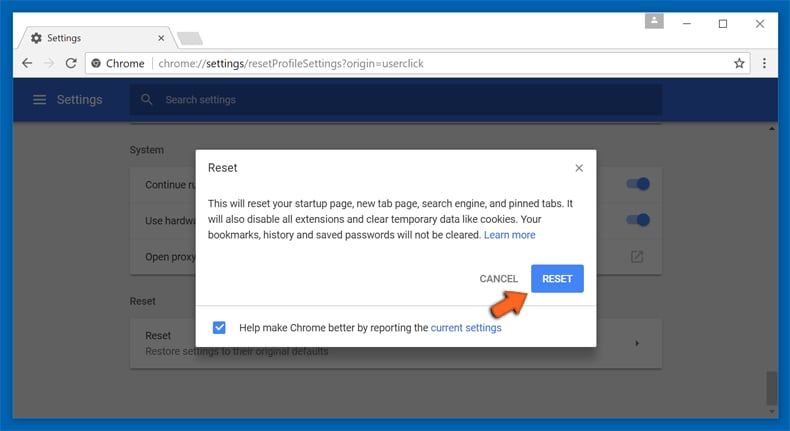
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
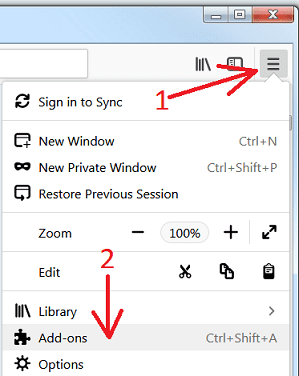
Remove Your Device Was Compromised Email Scam plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Your Device Was Compromised Email Scam removal then you have the option to rese the settings of Mozilla Firefox.
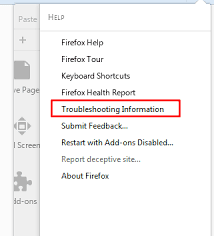
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
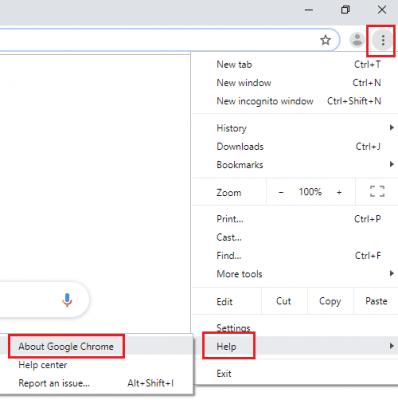
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
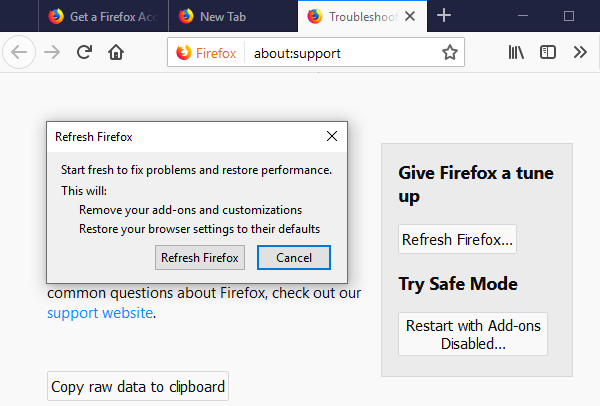
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
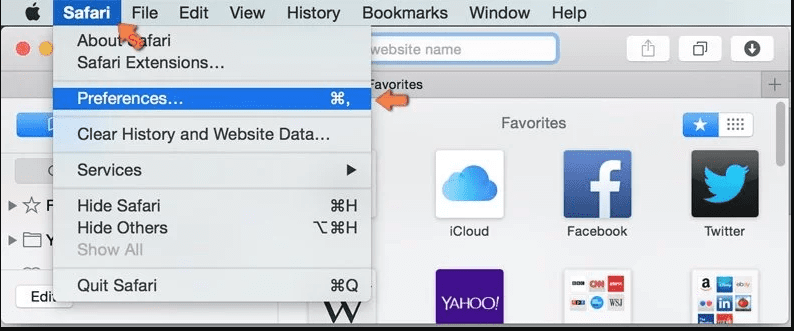
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
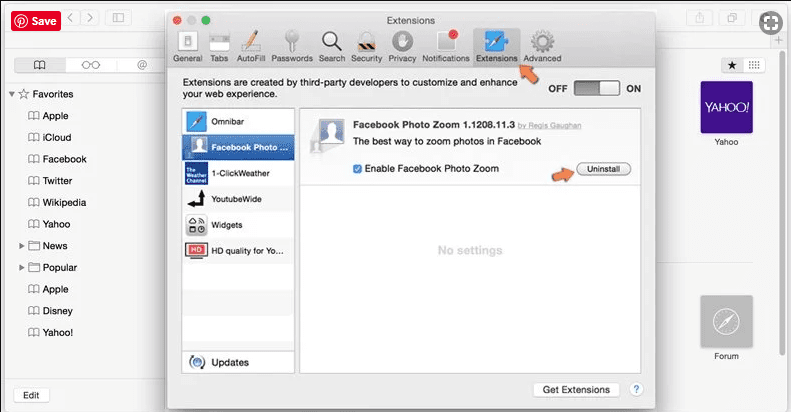
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
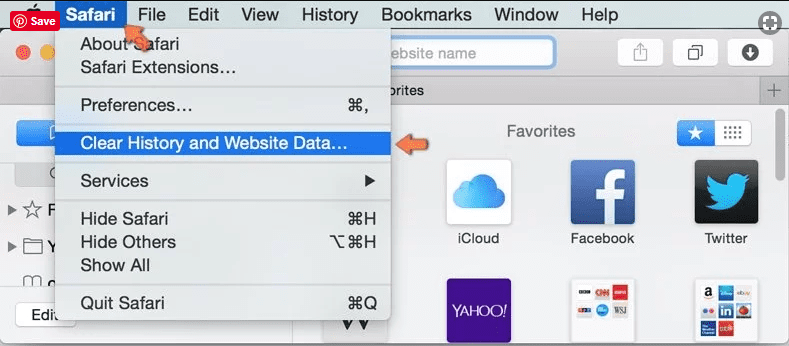
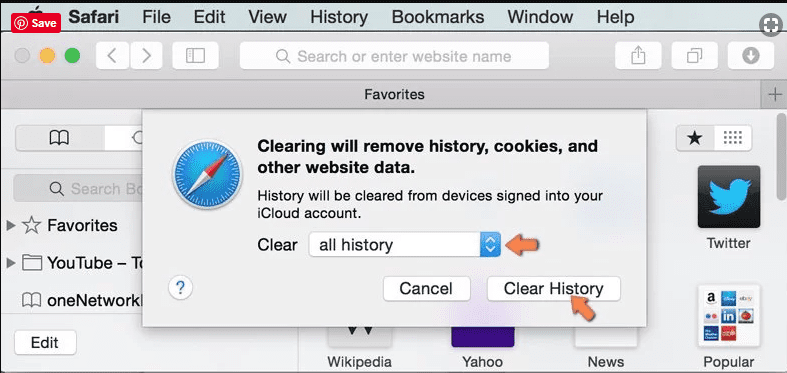
In the newly opened window, select “All History” and then press on “Clear History” option.
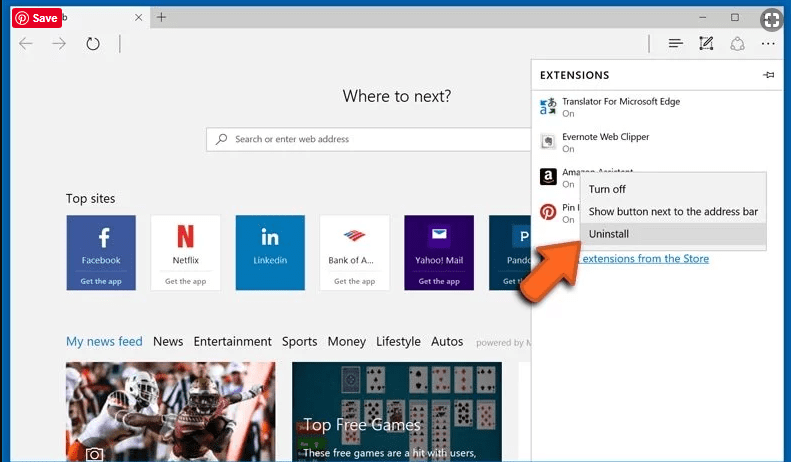
Delete Your Device Was Compromised Email Scam (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
Optional Method
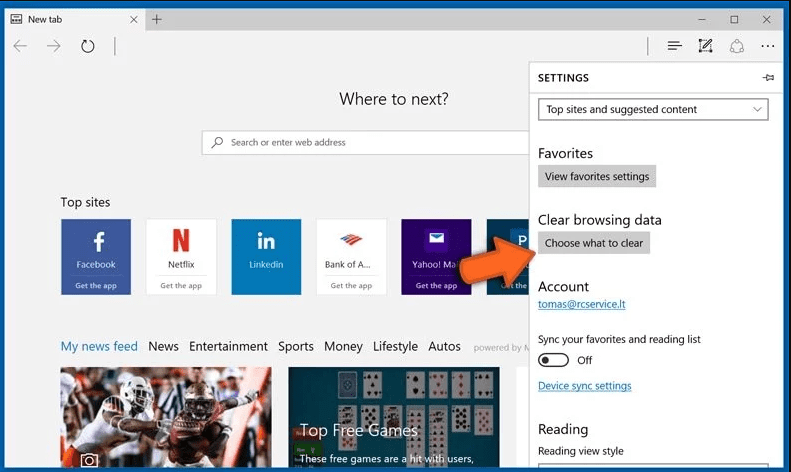
Open the browser (Microsoft Edge) and select “Settings”
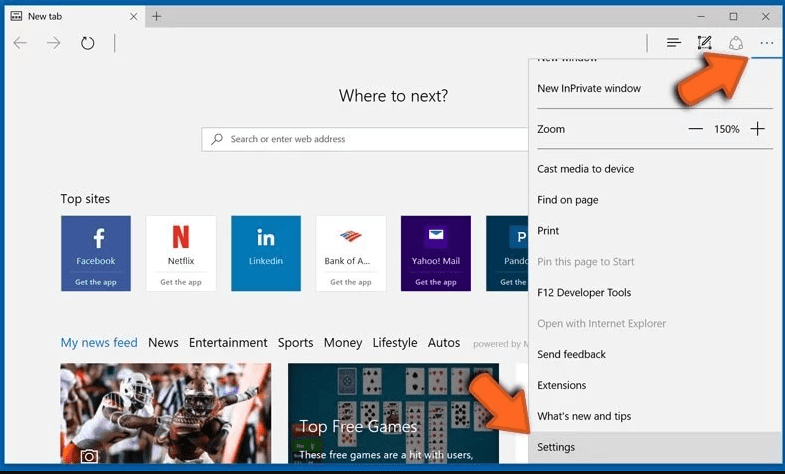
Next steps is to click on “Choose what to clear” button
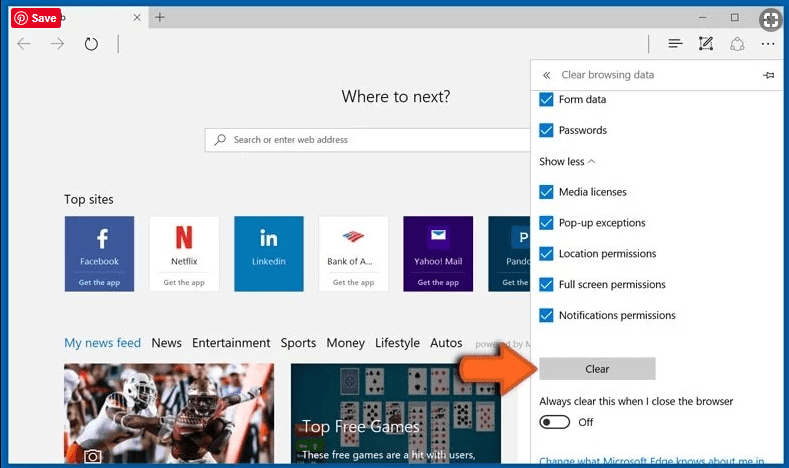
Click on “show more” and then select everything and then press on “Clear” button.
Conclusion
In most cases, the PUPs and adware gets inside the marked PC through unsafe freeware downloads. It is advised that you should only choose developers website only while downloading any kind of free applications. Choose custom or advanced installation process so that you can trace the additional PUPs listed for installation along with the main program.
Special Offer (For Windows)
Your Device Was Compromised Email Scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Your Device Was Compromised Email Scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.





