How To Remove Qensvlcbymk Ransomware And Recover Infected Data
Simple Steps To Delete Qensvlcbymk Ransomware From Computer
Qensvlcbymk Ransomware is a new deadly file-locking virus that was first spotted by security researcher GrujaRS and belongs to that family of Snatch ransomware. As soon as this hazardous threat manages to assail on your work-station, it encrypts nearly all commonly used file types and renames the encoded data by appending “.qensvlcbymk” extension with the name of each of them. It has ability to compromise various file formats such as .html, .docx,.png, .jpeg,.mp3, .mp4, .pdf,.gif, .sql etc. and can make those files unusable unless they are decrypted using a private decryption tool or key. This perilous crypto-virus has been found to be using powerful encryption algorithm and instantly stores the decryption software on remote servers.
More About Qensvlcbymk Ransomware:
Once the encryption process is completed, Qensvlcbymk Ransomware displays a ransom message in a file named “HOW TO RESTORE YOUR FILES.TXT” that shows the content regarding the attack. The ransom note informs victims that their important data have been encrypted and also instructs that the infected files can only be recovered using a special software and unique decryption key that can be acquired by contacting the attackers via the email address provided with it to negotiate a deal regarding the ransom price. The size of the extortion depends on how quickly you contact the hackers but it has to be paid in BitCoins or any other digital cryptocurrency.
To prove that the decryption is possible, Qensvlcbymk Ransomware operators offer to decrypt three files for free which should be less than 1 MB in size and should not contain any valuable information like backups, large Excel spreadsheets, databases etc. Moreover, the note also warns users that renaming the infected files, turning off or restarting the NAS (Network-attached storage) equipment may cause permanent data loss. Initially upon getting into your device, this hazardous crypto-virus makes critical changes in default registry settings in order to get automatically activated with each Window reboot. After that, it performs a deep scanning of all the folders in search of the data that are in its targets list and once detected, locks them at the end.
Text Presented In The Ransom Note:
Hello!
All your files are encrypted, write to me if you want to return your files – I can do it very quickly!
Contact me by email:
[email protected] or [email protected]
The subject line must contain an encryption extension or the name of your company!
Do not rename encrypted files, you may lose them forever.
You may be a victim of fraud. Free decryption as a guarantee.
Send us up to 3 files for free decryption.
The total file size should be no more than 1 MB! (not in the archive), and the files should not contain valuable information. (databases, backups, large Excel spreadsheets, etc.)
!!! Do not turn off or restart the NAS equipment. This will lead to data loss !!!
To contact us, we recommend that you create an email address at protonmail.com or tutanota.com
Because gmail and other public email programs can block our messages!
Should You Pay The Ransom?
Qensvlcbymk Ransomware authors give you a time limit to make the payment however; you should never make any sort of payment to the hackers because you are not going to get back your crucial data. You have absolutely no guarantee that criminals will send you the alleged decryption software even after taking the ransom as their only motive is to extort illicit money from the victimized users. Moreover, even if they provide you the tool that works, the virus will still remain in the device and can strike again for further incomes. And so, never consider dealing with the hackers no matter what situation is and find any alternate way to retrieve the compromised data. But, the first thing you need to do here is to remove Qensvlcbymk Ransomware from the computer immediately before it infects your other essential files.
How To Restore The Infected Files?
This precarious Ransomware has ability to delete the shadow volume copies (temporary backup made by OS itself) of the infected files and also specific system restore points and thus, recovering those data become even more complex for the affected users. In such hazardous situation, you should use a powerful file-recovery application that you can download right here via the link provided under this article. Furthermore, you should keep making regular backups by the help of which, you can easily restore the infected or lost files if such hazardous situation occurs whenever. The longer Qensvlcbymk Ransomware stays in your work-station; it can affect many parts of the device and run in the background until you completely get rid of it.
Malevolent Files Attached to Spam Emails And Pirated Software Packages:
Ransomware infections mostly rely on silent methods to penetrate the targeted computers. Malevolent files can trigger and cause the crypto-virus attack pretty quickly without even noticed by the users. The payload delivery as well as the data encrypting process both occurs without your knowledge. Spam emails that have vicious macro-filled documents can pretend as genuine notifications from companies like eBay, Amazon, DHL or other Online shopping platforms. These types are selected because invoices, order information and other files related to financial details are mainly sent by such companies. However, such files and data sent out during pirated software installations can trigger penetration of direct ransomware or the malware that is designed to inject the crypto-virus executable file. And hence, we highly advise to stay away from pirating or torrent sites and delete questioning emails once you obtain them.
Quick Glance
Name: Qensvlcbymk Ransomware
Type: Ransomware, Crypto-virus
Description- Destructive malware that aims to encrypt users’ crucial files and then ask them to pay off for the decryption key/tool.
Extension- “.qensvlcbymk”
Ransom message- “HOW TO RESTORE YOUR FILES.TXT”
Attackers’ Contact- [email protected] and [email protected]
Symptoms: Users can not open files available on their desktop, previously functional files now have different extensions, A ransom demanding message is displayed on the desktop screen. Users are asked to pay an amount of ransom to unlock their encoded data and files.
Distribution methods: Spam emails, Torrent websites, peer to peer network sharing, unofficial activation and updating tools.
Damage: All files are encrypted and cannot be accessed without paying ransom, Additional password stealing Trojans and malware infections can be installed along with ransomware infections and other malware.
Removal: To remove this virus from the system, we advise you to use a reliable anti-malware tool. Once malware gets removed, you can recover your files by using existing backup or data-recovery software.
Other Common Symptoms of Qensvlcbymk Ransomware:
Qensvlcbymk Ransomware downgrades the overall computer performance severely as it consumes huge amount of memory resources and increases the usage of CPU. It ruins vital system files which assure efficient device functioning and prevents many running apps as well as drivers from working in a proper manner. This notorious infection has ability to deactivate all the running security programs and Windows Firewalls and allow other Online parasites such as spyware, adware, worms, rootkits, Trojans etc. to sneak into your machine as well and cause more damages inside. This nasty parasite causes several other hazardous issues in the PC such as application malfunctioning, frequent system crash, boot errors, hard drive failure and so on. And therefore, looking at all these hazards, you are strongly recommended to remove Qensvlcbymk Ransomware from the computer without wasting any time.
Special Offer (For Windows)
Qensvlcbymk Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove Qensvlcbymk Ransomware through “Safe Mode with Networking”
Step 2: Delete Qensvlcbymk Ransomware using “System Restore”
Step 1: Remove Qensvlcbymk Ransomware through “Safe Mode with Networking”
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
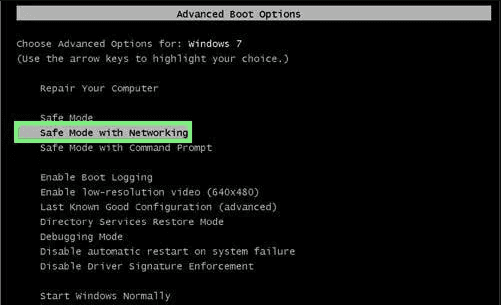
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
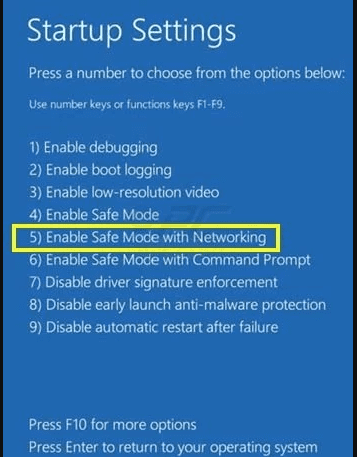
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
Step 2: Delete Qensvlcbymk Ransomware using “System Restore”
Log-in to the account infected with Qensvlcbymk Ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
Qensvlcbymk Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
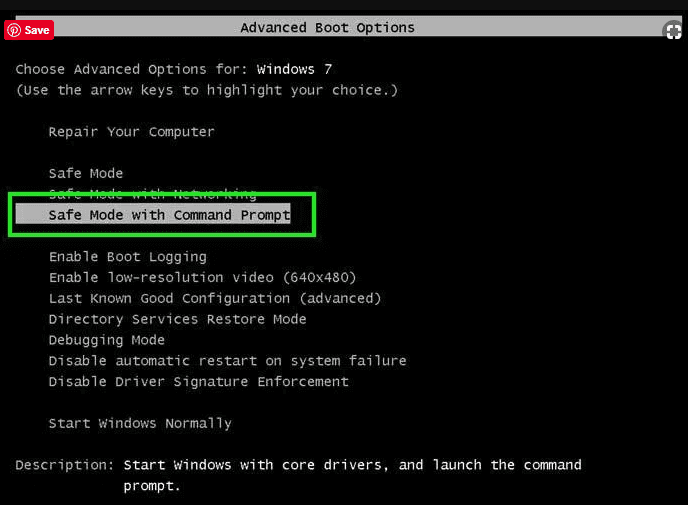
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
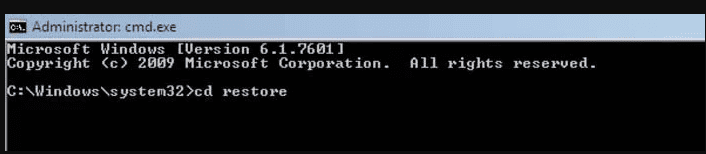
- Type: rstrui.exe and Press “ENTER”
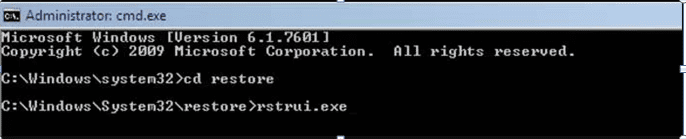
- Click “Next” on the new windows
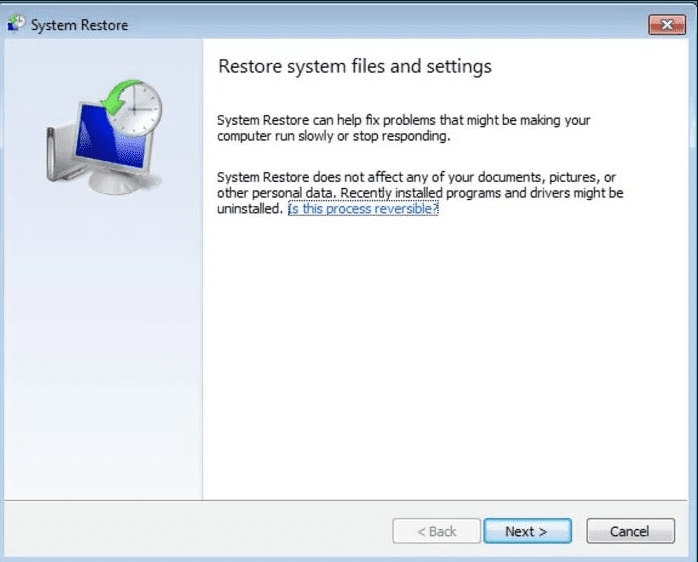
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to Qensvlcbymk Ransomware infiltration in the PC.
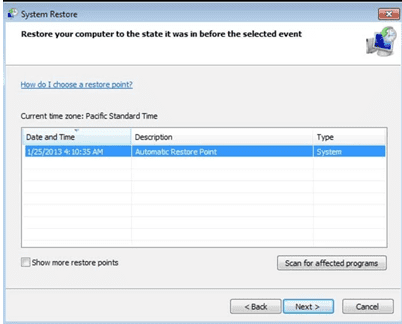
- In the newly opened windows, press on “Yes”.
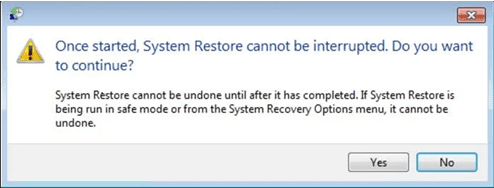
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove Qensvlcbymk Ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of Qensvlcbymk Ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
How to Restore Individual Encrypted File:
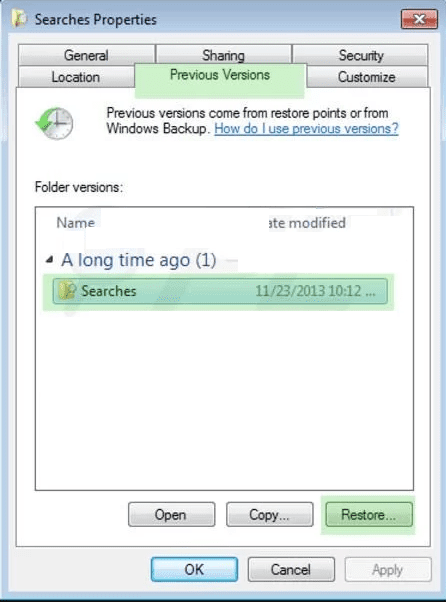
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
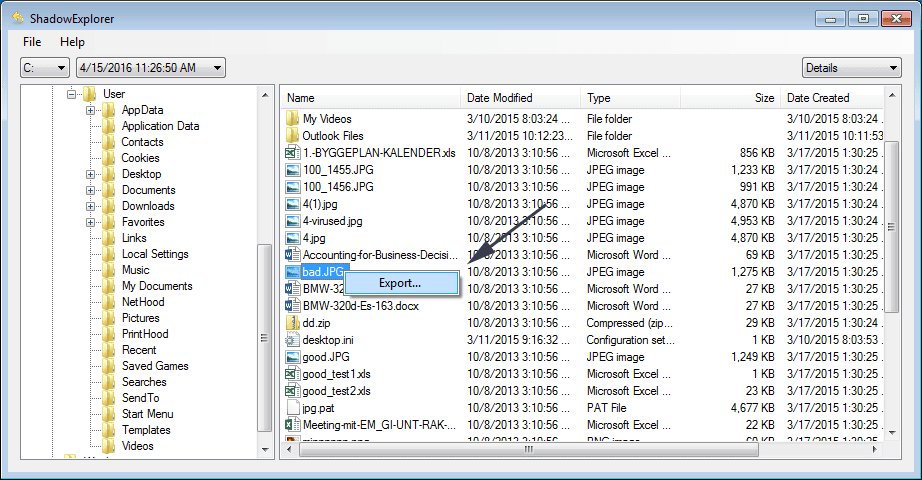
In order to access the files encrypted by Qensvlcbymk Ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like Qensvlcbymk Ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
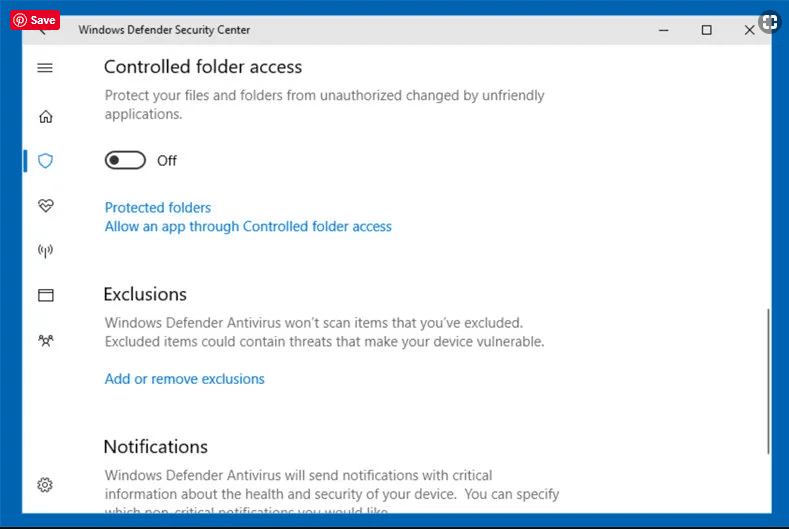
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by Qensvlcbymk Ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with Qensvlcbymk Ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove Qensvlcbymk Ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

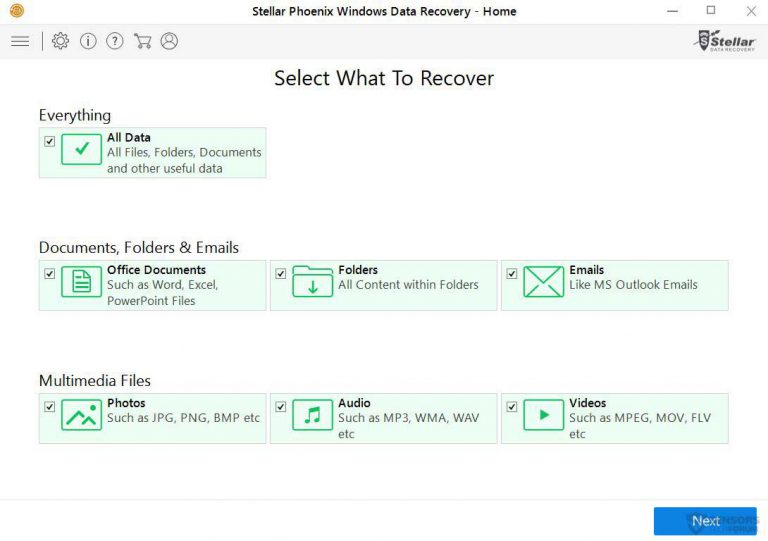
Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
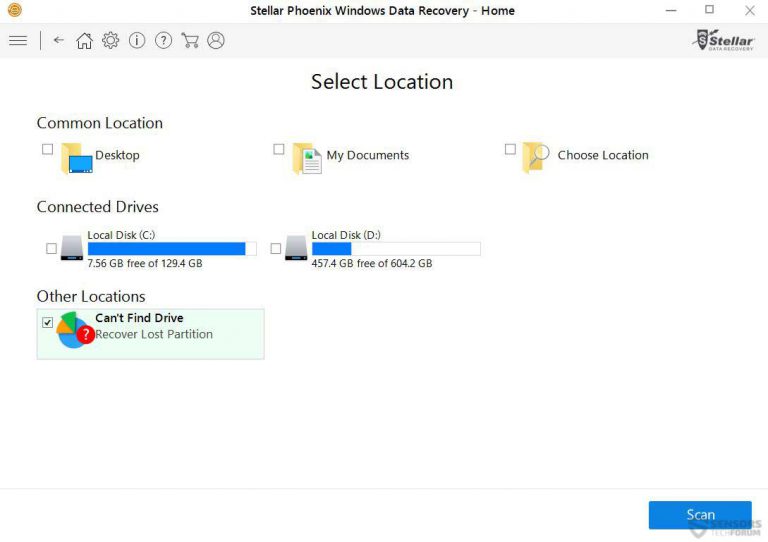
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
Qensvlcbymk Ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.