How to remove [[email protected]].LX ransomware
Tips for [[email protected]].LX ransomware removal
LX or otherwise called [[email protected]].LX ransomware is a piece of malicious software, belonging to the Crisis/Dharma ransomware family. The credit of discovery of this malware goes to Jakub Kroustek. It operates by encrypting the data of infected systems, in order to demand payment for the decryption tools/software. As this malware encrypts, all affected files are renamed with some definite pattern: original filename, unique ID, cyber criminals’ email address and the “.LX”. For example, a file like “1.jpg” becomes 1.jpg.id-1E857D00.[[email protected]].LX”. Afterwards, the ransomware creates a text file – “FILES ENCRYPTED.txt” and drops it on the desktop.
The ransom note in the text file (“FILES ENCRYPTED.txt”) informs victims that their data has been “locked” and instruct that they must have to write a letter to the crooks behind [[email protected]].LX ransomware email addresses of the cyber criminals behind the infection if they want the data back. The text presented in the pop-up window provides a bit more information. Initially, it repeats the same statement that the users must initiate communication via email and then says the letter must contain the unique ID assigned to them. If no response is received within 12 hours, they are asked to use the other email address. At the end, the note alters the users that renaming the encrypted files and/or attempting to decrypt them with third party tools – may lead to permanent data loss.
Unfortunately, in most cases of ransomware infections, without the involvement of the individuals responsible – decryption is impossible. The encryption is done using some strong cipher algorithm that allows the crooks to create a unique decryption tool/key associated with each victim individually. All such keys are stored on some remote servers that only the crooks can access to them. They ask users to ransom payment exchange for providing the decryption tool. However, in most cases, the users receive no decryption tool even if they fulfil all their demands. In other word, those who follow the ransom payment instruction get scammed. They do not receive the decryptor even if they pay the ransom fee.
Due to this, you are recommended to use some data recovery alternate and avoid paying/contact to the LX developers. For the data recovery, you have existing backup, volume shadow copy and data recovery tools –you can use one of them according to the condition that suite you the best. However, before performing the data recovery process, we recommend you remove [[email protected]].LX ransomware so that you will not get any trouble during the files recovery process. The virus removal prevents further files encryptions and also avoids various other possible risks including the risk of data stealing, system/software damaging and other malicious malware intrusion. For the virus removal, use some reputable antivirus tool or follow manual malware removal guide provided below the post.
How did ransomware intrude in?
Ransomware and other malware primarily spread through Trojans, spam campaigns, illegal activation (“cracking”) tools, illegitimate updates and untrustworthy download sources. Trojans are malicious programs that are especially design to cause chain infections. After the install, such malware creates backdoor for other malware injection on the device. In scam campaigns, deceptive/scam emails sent on a mass scale. Such emails have infectious files attached to them, when are opened – the users initiate the infection process. Illegal activation tools (“cracks”) can download/install malicious software, instead of activating licensed product. Fake updaters cause infections by abusing flaws of outdated products and/or simply install malware, rather than the promised updates. Untrustworthy download channels, e.g. unofficial and free file-hosting sites, Peer-to-Peer sharing networks (BitTorrent, Gnutella, eMule, etc.) and other third party updaters spread malware by presenting it as legit software.
How to prevent ransomware infection?
It is not advised to open suspicious and/or irrelevant emails, especially any attachments (or links) present in them – can result in a high-risk infection. You should download software from official and verified sources. Also, It is just as important to activate and update software with tools/functions, provided by legitimate developers. Further, it is crucial to have a dependable anti-virus/anti-spyware installed and kept updated. Such tools provide regular update to the installed apps and OS. Also, they provide the adequate protection to the device by preventing any malicious executables from being launched.
Text presented in [[email protected]].LX ransomware‘s pop-up window:
YOUR FILES ARE ENCRYPTED
Don’t worry,you can return all your files!
If you want to restore them, follow this link:email [email protected] YOUR ID 1E857D00
If you have not been answered via the link within 12 hours, write to us by e-mail:[email protected]
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Remove [[email protected]].LX ransomware
Manual malware removal guide is provided below in step by step manner. Follow it so that you will not find any trouble during removal process. You can use some reputable antivirus tool to automatically remove [[email protected]].LX ransomware from the device.
Special Offer (For Windows)
[[email protected]].LX ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
Antimalware Details And User Guide
Step 1: Remove [[email protected]].LX ransomware through “Safe Mode with Networking”
Step 2: Delete [[email protected]].LX ransomware using “System Restore”
Step 1: Remove [[email protected]].LX ransomware through “Safe Mode with Networking”
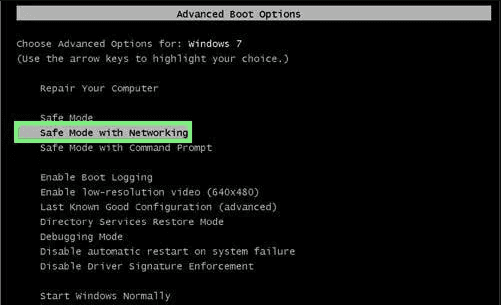
For Windows XP and Windows 7 users: Boot the PC in “Safe Mode”. Click on “Start” option and continuously press on F8 during the start process until the “Windows Advanced Option” menu appears on the screen. Choose “Safe Mode with Networking” from the list.
Now, a windows homescreen appears on the desktop and work-station is now working on “Safe mode with networking”.
For Windows 8 Users: Go to the “Start Screen”. In the search results select settings, type “Advanced”. In the “General PC Settings” option, choose “Advanced startup” option. Again, click on the “Restart Now” option. The work-station boots to “Advanced Startup Option Menu”. Press on “Troubleshoot” and then “Advanced options” button. In the “Advanced Option Screen”, press on “Startup Settings”. Again, click on “Restart” button. The work-station will now restart in to the “Startup Setting” screen. Next is to press F5 to boot in Safe Mode in Networking.
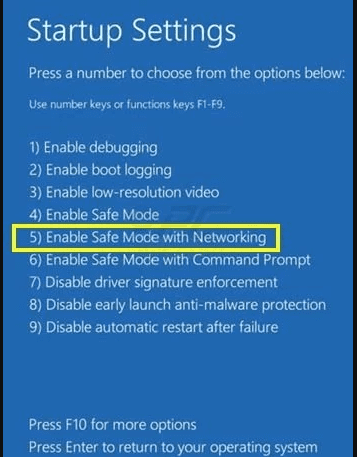
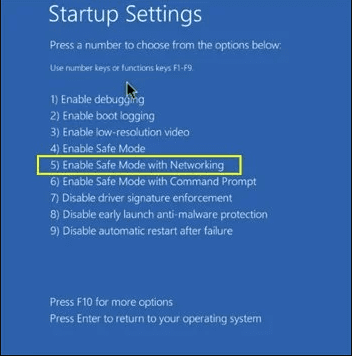
For Windows 10 Users: Press on Windows logo and on the “Power” icon. In the newly opened menu, choose “Restart” while continuously holding “Shift” button on the keyboard. In the new open “Choose an option” window, click on “Troubleshoot” and then on the “Advanced Options”. Select “Startup Settings” and press on “Restart”. In the next window, click on “F5” button on the key-board.
Step 2: Delete [[email protected]].LX ransomware using “System Restore”
Log-in to the account infected with [[email protected]].LX ransomware. Open the browser and download a legitimate anti-malware tool. Do a full System scanning. Remove all the malicious detected entries.
Special Offer (For Windows)
[[email protected]].LX ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.
In case if you cannot start the PC in “Safe Mode with Networking”, Try using “System Restore”
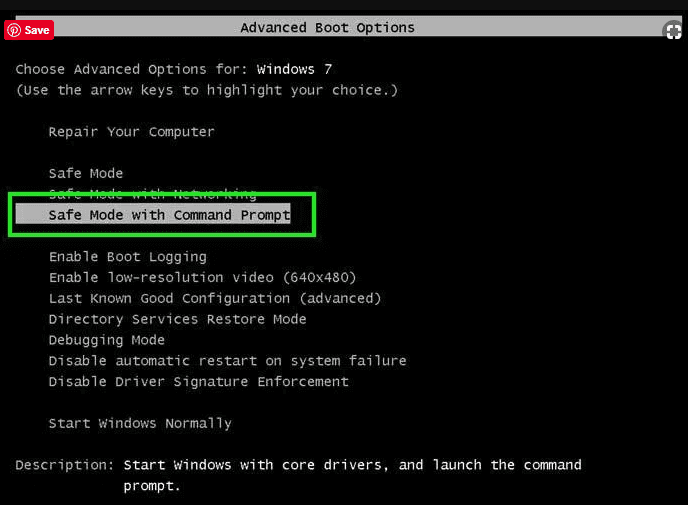
- During the “Startup”, continuously press on F8 key until the “Advanced Option” menu appears. From the list, choose “Safe Mode with Command Prompt” and then press “Enter”
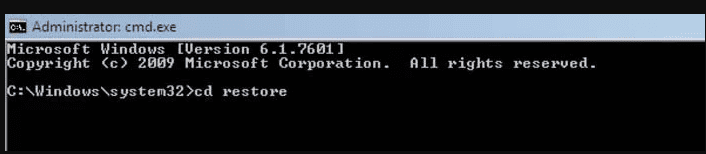
- In the new opened command prompt, enter “cd restore” and then press “Enter”.
- Type: rstrui.exe and Press “ENTER”
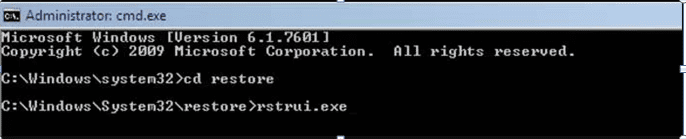
- Click “Next” on the new windows
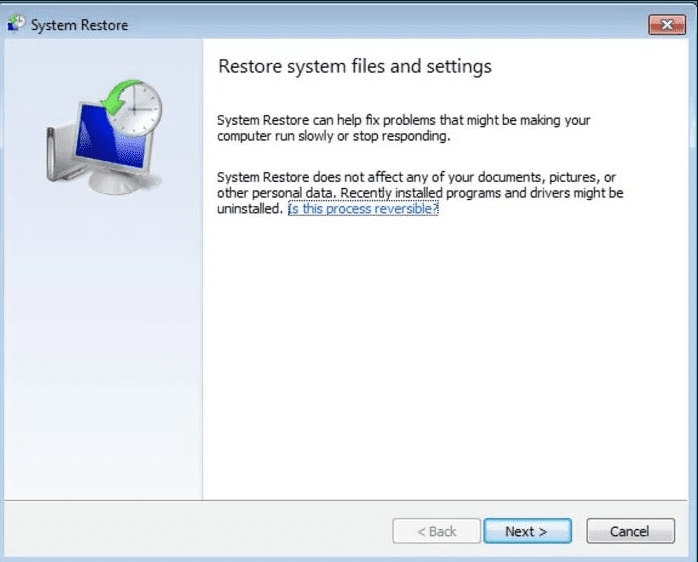
- Choose any of the “Restore Points” and click on “Next”. (This step will restore the work-station to its earlier time and date prior to [[email protected]].LX ransomware infiltration in the PC.
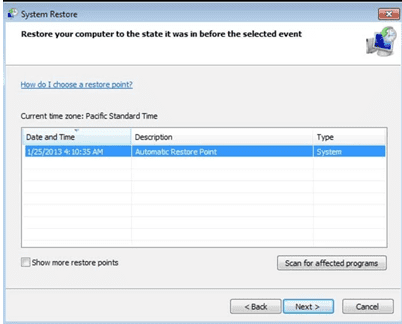
- In the newly opened windows, press on “Yes”.
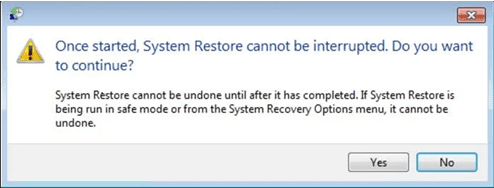
Once your PC gets restored to its previous date and time, download the recommended anti-malware tool and perform a deep scanning in order to remove [[email protected]].LX ransomware files if they left in the work-station.
In order to restore the each (separate) file by this ransomware, use “Windows Previous Version” feature. This method is effective when “System Restore Function” is enabled in the work-station.
Important Note: Some variants of [[email protected]].LX ransomware delete the “Shadow Volume Copies” as well hence this feature may not work all the time and is applicable for selective computers only.
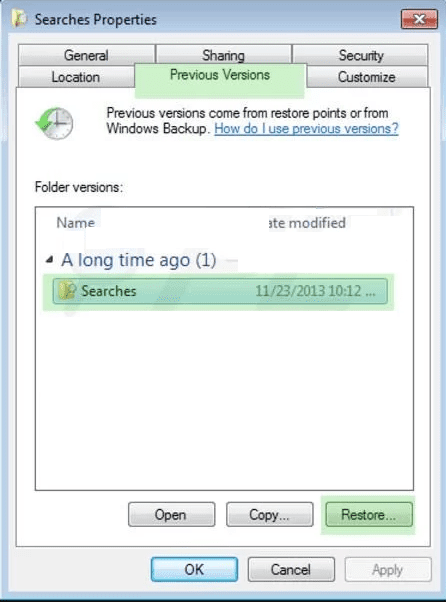
How to Restore Individual Encrypted File:
In order to restore a single file, right click on it and go to “Properties”. Select “Previous Version” tab. Select a “Restore Point” and click on “Restore” option.
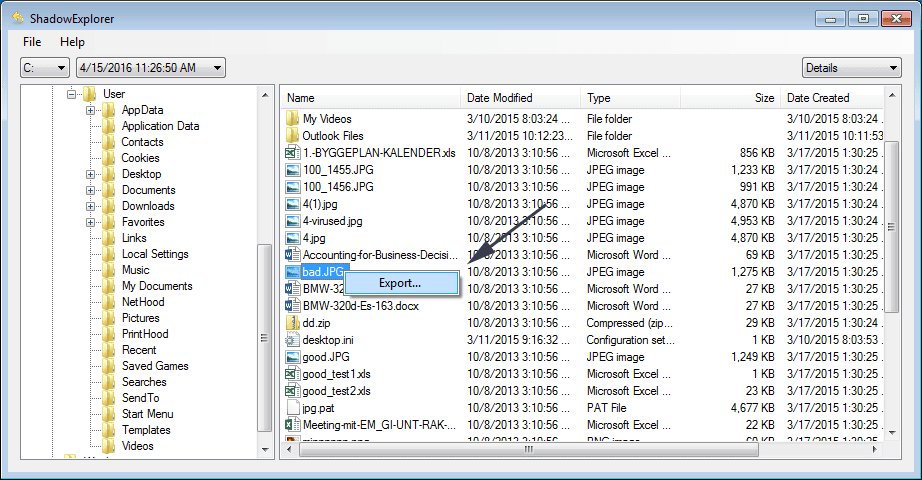
In order to access the files encrypted by [[email protected]].LX ransomware, you can also try using “Shadow Explorer”. In order to get more information on this application, press here.
Important: Data Encryption Ransomware are highly dangerous and it is always better that you take precautions to avoid its attack on your work-station. It is advised to use a powerful anti-malware tool in order to get protection in real-time. With this help of “SpyHunter”, “group policy objects” are implanted in the registries in order to block harmful infections like [[email protected]].LX ransomware.
Also, In Windows 10, you get a very unique feature called “Fall Creators Update” that offer “Controlled Folder Access” feature in order to block any kind of encryption to the files. With the help of this feature, any files stored in the locations such as “Documents”, “Pictures”, “Music”, “Videos”, “Favorites” and “Desktop” folders are safe by default.
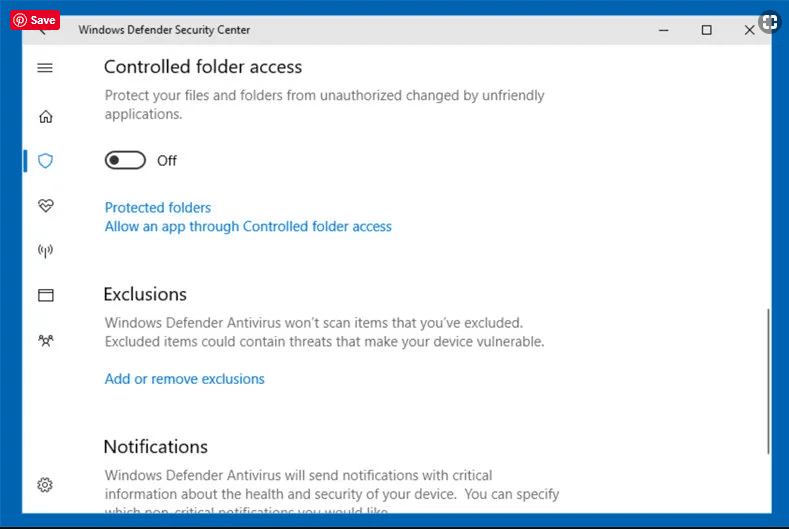
It is very important that you install this “Windows 10 Fall Creators Update” in your PC to protect your important files and data from ransomware encryption. The more information on how to get this update and add an additional protection form rnasomware attack has been discussed here.
How to Recover the Files Encrypted by [[email protected]].LX ransomware?
Till now, you would have understood that what had happed to your personal files that got encrypted and how you can remove the scripts and payloads associated with [[email protected]].LX ransomware in order to protect your personal files that has not been damaged or encrypted until now. In order to retrieve the locked files, the depth information related to “System Restore” and “Shadow Volume Copies” has already been discussed earlier. However, in case if you are still unable to access the encrypted files then you can try using a data recovery tool.
Use of Data Recovery Tool
This step is for all those victims who have already tries all the above mentioned process but didn’t find any solution. Also it is important that you are able to access the PC and can install any software. The data recovery tool works on the basis of System scanning and recovery algorithm. It searches the System partitions in order to locate the original files which were deleted, corrupted or damaged by the malware. Remember that you must not re-install the Windows OS otherwise the “previous” copies will get deleted permanently. You have to clean the work-station at first and remove [[email protected]].LX ransomware infection. Leave the locked files as it is and follow the steps mentioned below.
Step1: Download the software in the work-station by clicking on the “Download” button below.
Step2: Execute the installer by clicking on downloaded files.
Step3: A license agreement page appears on the screen. Click on “Accept” to agree with its terms and use. Follow the on-screen instruction as mentioned and click on “Finish” button.

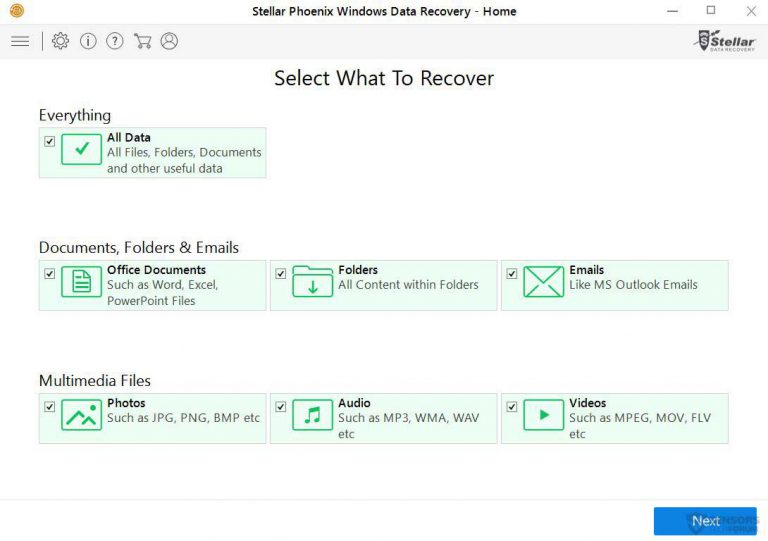
Step4: Once the installation gets completed, the program gets executed automatically. In the newly opened interface, select the file types that you want to recover and click on “Next”.
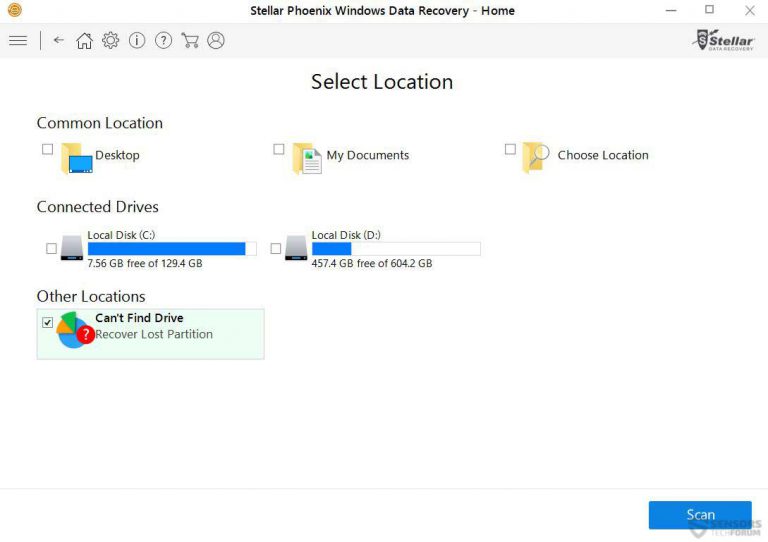
Step5: You can select the “Drives” on which you want the software to run and execute the recovery process. Next is to click on the “Scan” button.
Step6: Based on drive you select for scanning, the restore process begins. The whole process may take time depending on the volume of the selected drive and number of files. Once the process gets completed, a data explorer appears on the screen with preview of that data that is to be recovered. Select the files that you want to restore.

Step7. Next is to locate the location where you want to saver the recovered files.

Special Offer (For Windows)
[[email protected]].LX ransomware can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Data Recovery Offer
We Suggest you to choose your lately created backup files in order to restore your encrypted files, however in case if you don’t have any such backups, you can try a data recovery tool to check if you can restore your lost data.