How to remove Contech scam email
Easy tips to delete Contech scam email
Contech scam email refers to be a malware-spreading spam campaign. The term spam campaign defines as a large scale operation in which thousands of spam emails are designed and delivered. The letters distributed through this campaign are presented as legit purchasing order. However, the excel document attached to the emails do not contain any information about the purchases. In fact, the attachment is actually an archive executable that triggers download/ installation of Ave Maria Trojan.

The Contech scam email has the subject/ title “new purchase order document for june”. It requests the recipients to review the attached product spreadsheet which supposedly contains an order details as soon as possible so as the order is shipped before the week runs out. As said earlier in the introduction, the email attachment does not contain any stated information. Instead, when this malicious executable is clicked on – it initiates the download/ installation of malware named Ave Maria.
Ave Maria is a Trojan that primarily functions as of data theft and download/ installation of additional malware. Its keyloging capability means the ability to record keystrokes input allow it to extract the data from the web browsers, email clients. The list of the data includes log-in credentials (usernames/passwords) of various accounts, browsing and search engine histories, Internet cookies, IP addresses/ geolocations, personally identifiable details, financial information (bank account and credit card numbers), etc.
Ave Maria Trojan also spreads malicious malware on the compromised systems. It might cause system infection with ransomware, cryptocurrency miners and other malicious malware. To sum up, on trusting Contech scam email – users experience multiple system infections, device and data damage, severe privacy issues, financial loss and identity theft. If you suspect that the malware already made an entry to your system, run a full system scans using some powerful antivirus tool to perform its removal right away.
How did Contech scam email enter my system?
Scam campaigns proliferate in malware through infectious files or links for such files in them. This file can be directly attached to the emails or the letters contain the website links for such files. The virulent files can be in any forms including archives, JavaScript, Microsoft Office document, PDFs, and so on. When these files are executed, run or otherwise opened- the malware download/ installation process is triggered. For example, Microsoft office documents infect systems by executing macros commands. This process begins the moment you open the document if you are using Microsoft Office versions released before 2010. Newer versions have protective view mode in them to prevent automatic execution of macros. Instead, the users are asked to enable macros commands.
Full text presented in Contech scam email page:
Subject: new purchase order document for june
Good Morning sir,
Kindly see the attached product spreadsheet in excel, we would like the order shipped before the week runs out.
We would really appreciate your fastest response as this order is very urgent to our ongoing project.
Manager(procurement)
Purchasing Management Unit
Block B170, Jebel Ali Industrial Area 2,
PO Box 5750, Dubai, UAE
Tel: +971-4-8802662
Fax: +971-4-8802622
www.contech.ae
The information in this email is confidential and may contain proprietary and/or legally privileged information. It is intended solely for the user of the individual or entity to whom it is addressed and others authorized to receive it. If you are not the intended recipient, please e-mail the sender and delete this email and any attachments from your system and note that any disclosure, copying, distribution or taking action in reliance of the contents of this email is prohibited and may be unlawful.
P No trees were harmed in the making or sending of this message. Consider the environment please don’t print this e-mail unless you really need to
How to prevent installation of malware?
To avoid infecting systems via spam email, it is advised against opening any dubious and irrelevant emails- especially any attachments or links inside them. It is recommended to use Microsoft Office versions released after 2010. However, malware can be spread through untrustworthy downloading channels such as unofficial and free file hosting sites, p2p networks and etc as well as via illegal activation tools and fake updaters. Therefore, it is crucial to download only from official and verified sources. Additionally, all programs should have to be updated/ activated using tools/ functions from official software developers.
Special Offer (For Windows)
Contech scam email can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Contech scam email has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
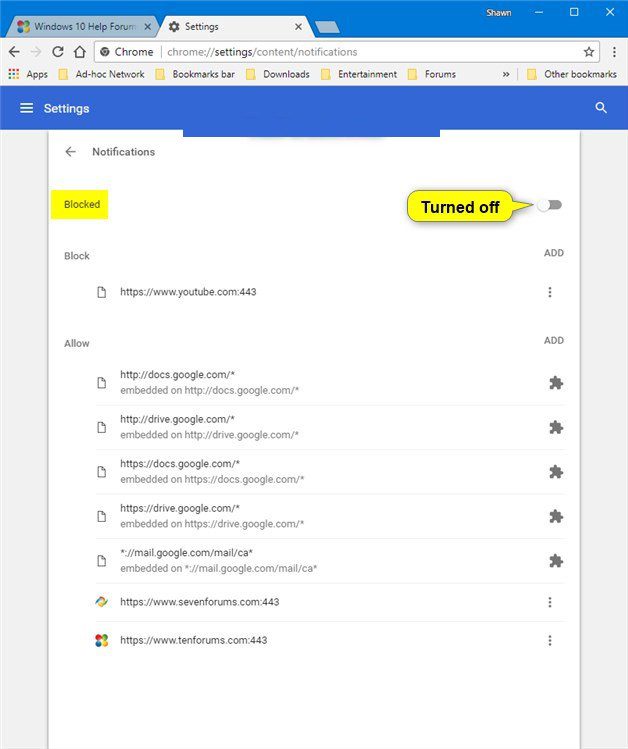
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
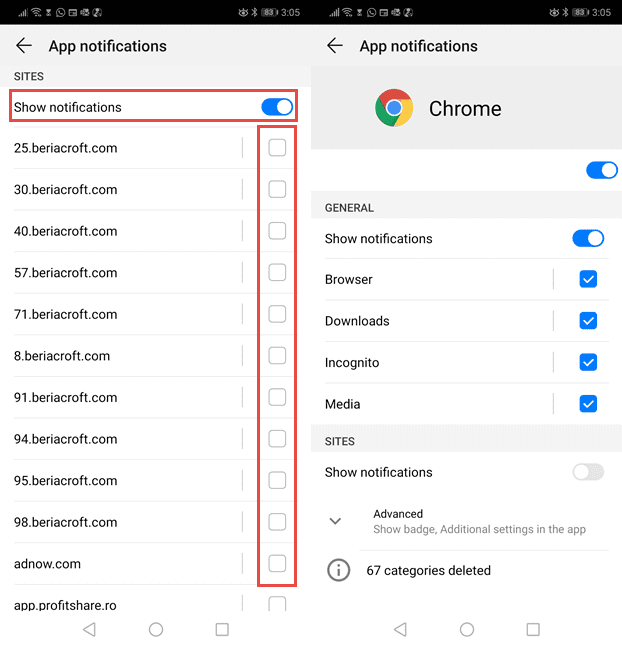
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
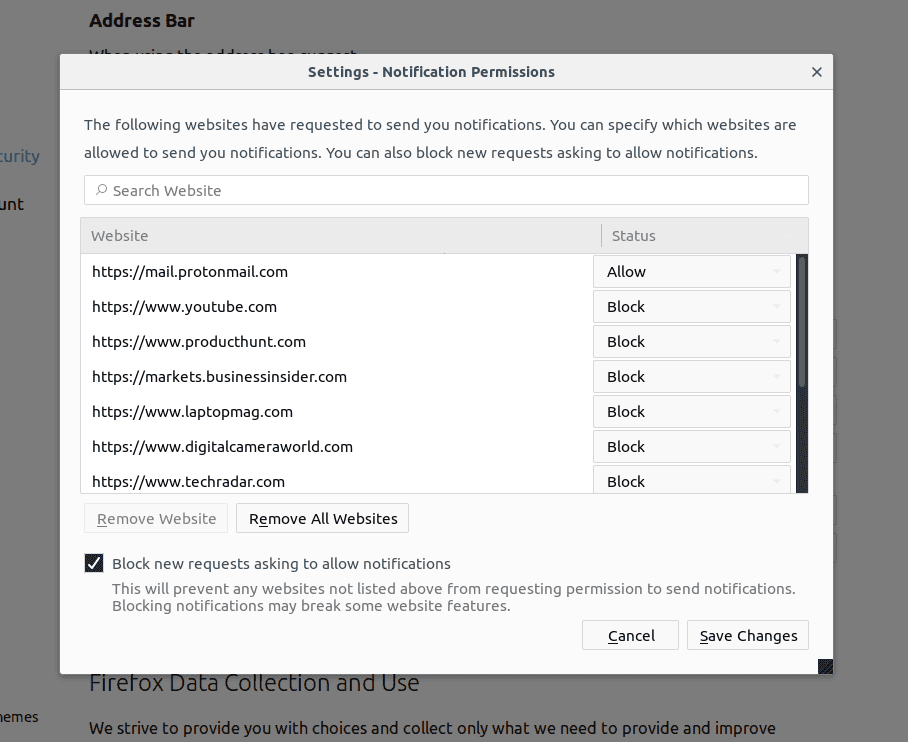
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
Internet Explorer
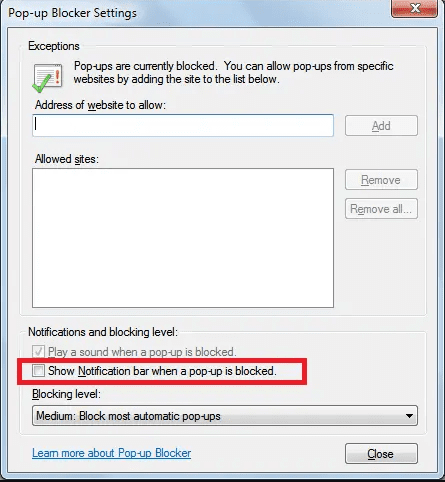
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
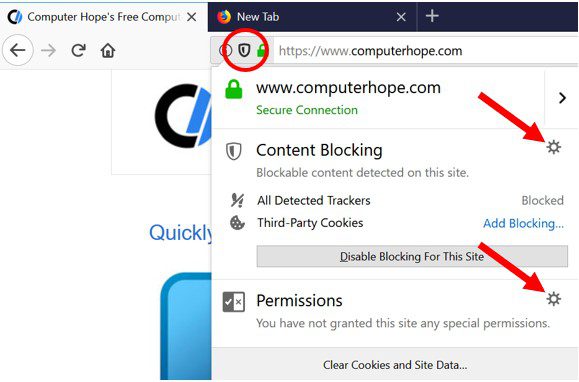
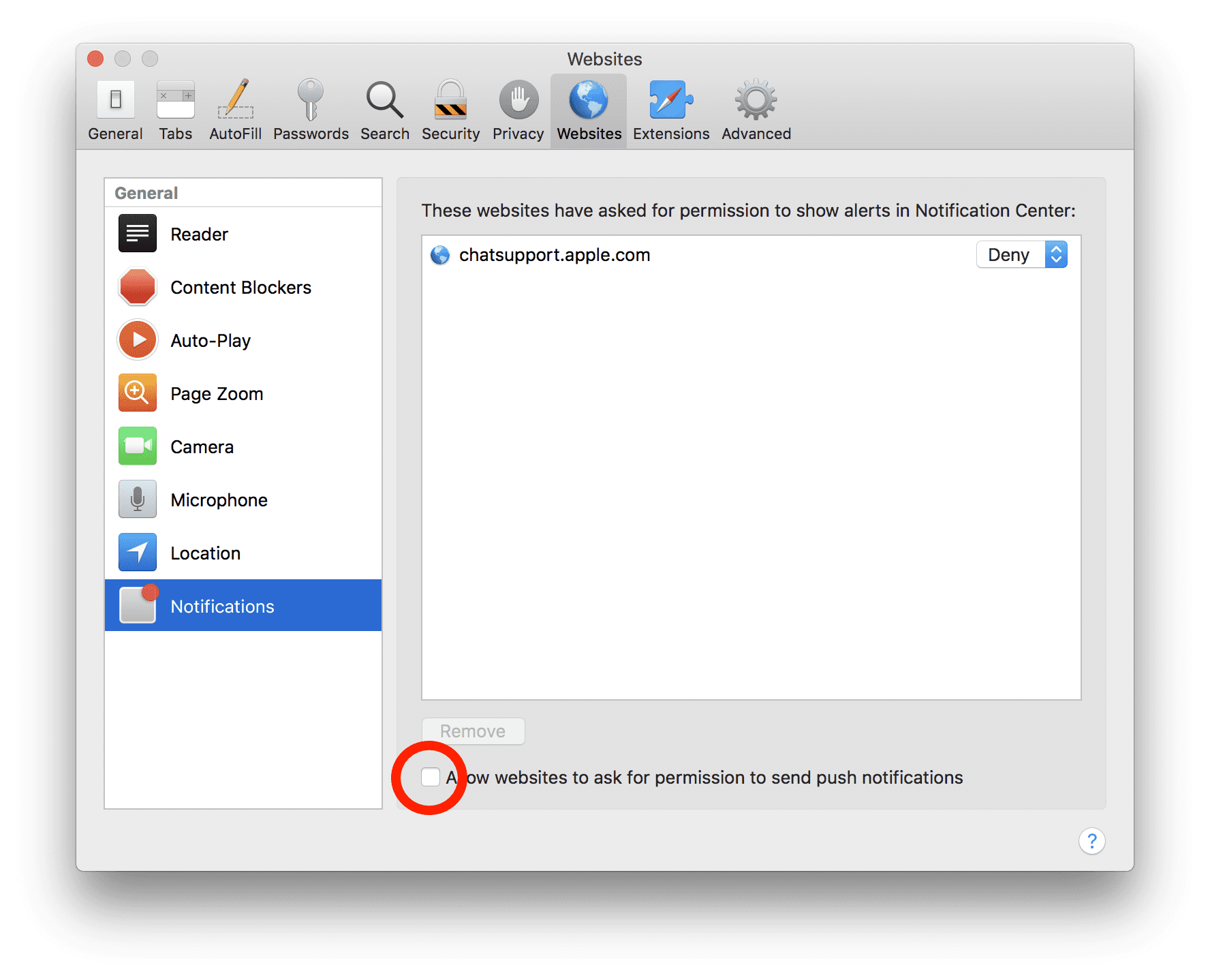
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Contech scam email:
Remove the related items of Contech scam email using Control-Panel
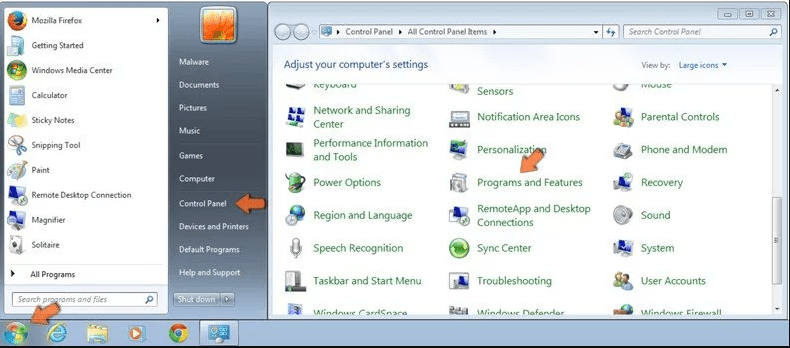
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
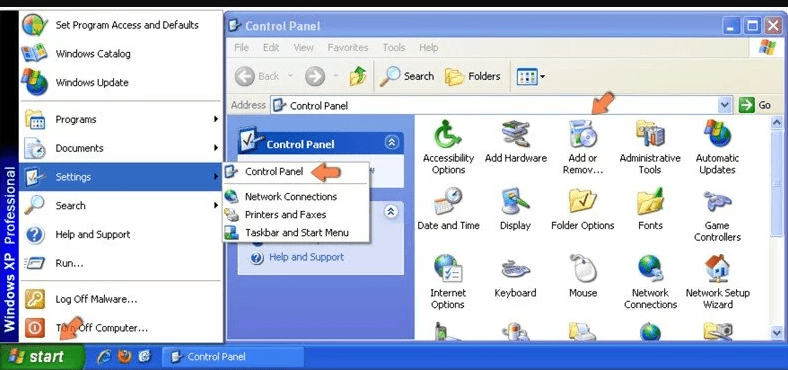
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
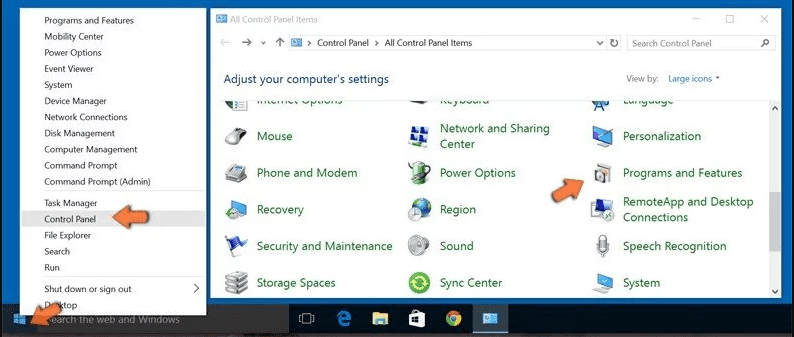
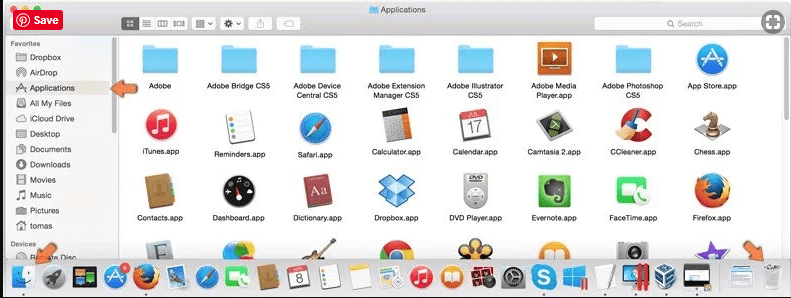
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
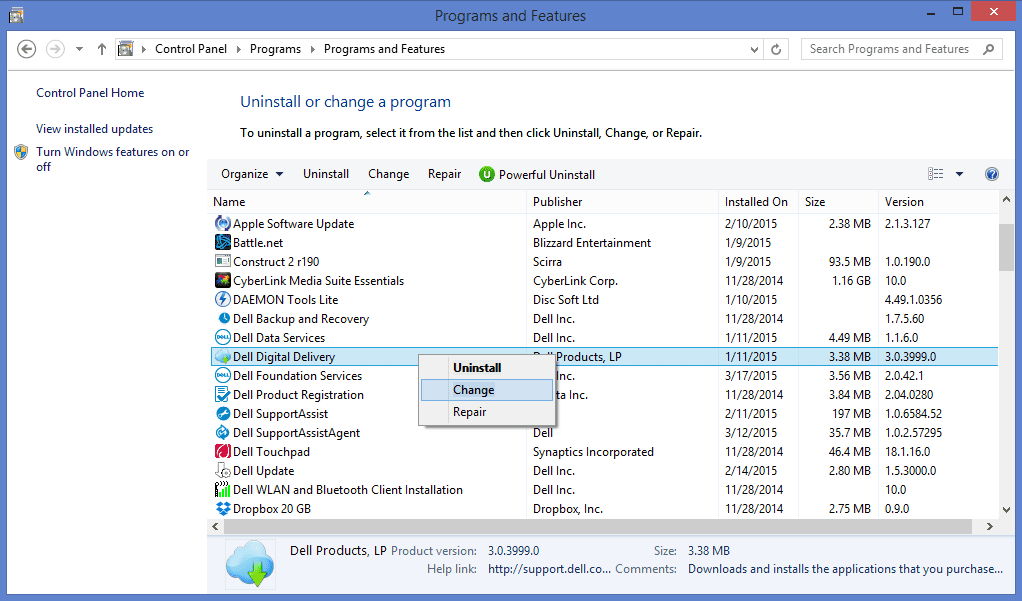
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Contech scam email issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Contech scam email can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Contech scam email has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Contech scam email) from Internet Browsers
Delete malicious add-ons and extensions from IE
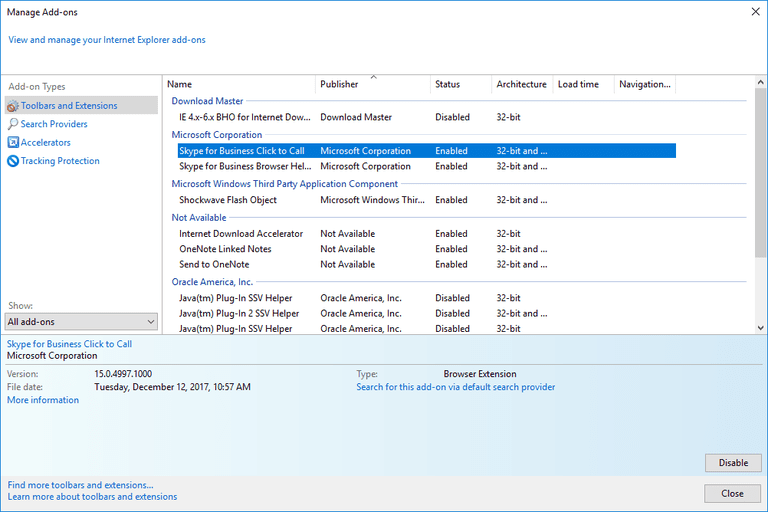
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
Additional Option
If you still face issues related to Contech scam email removal, you can reset the Internet Explorer to its default setting.
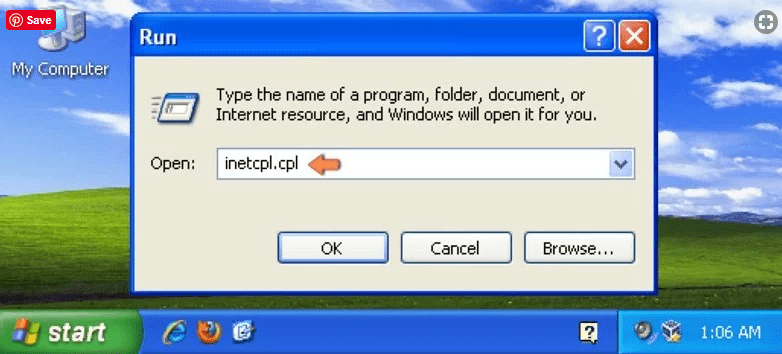
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
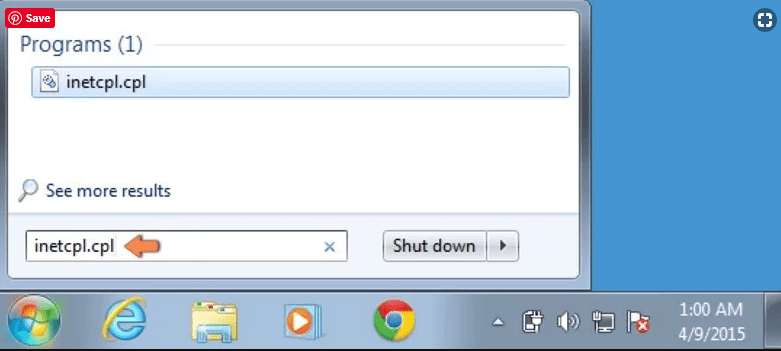
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
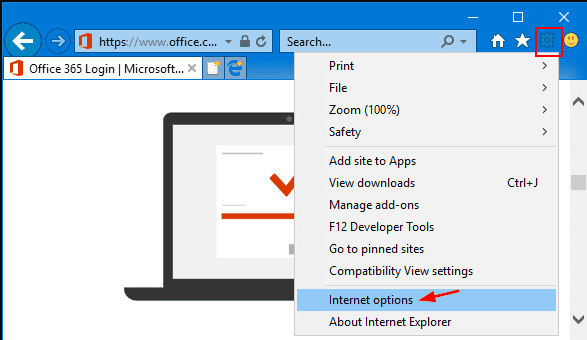
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
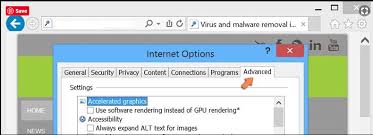
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
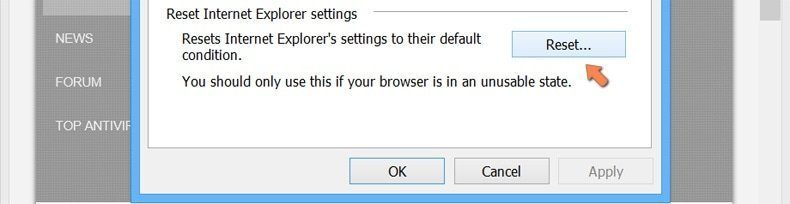
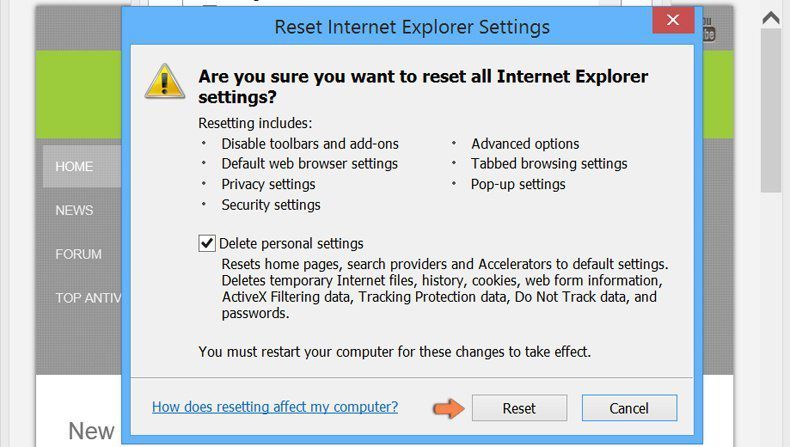
You have to press on the “Reset” button again to confirm that you really want to reset the IE
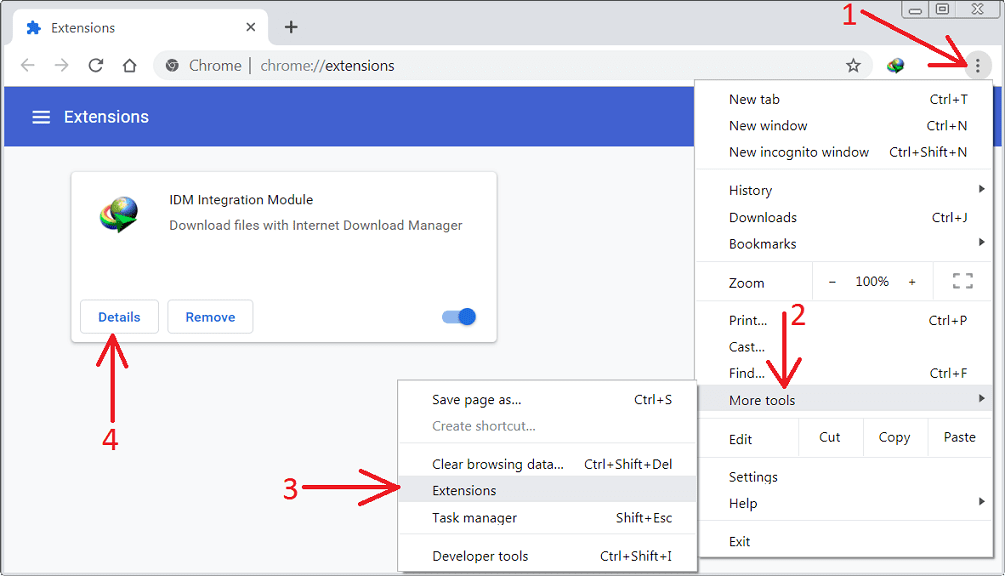
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
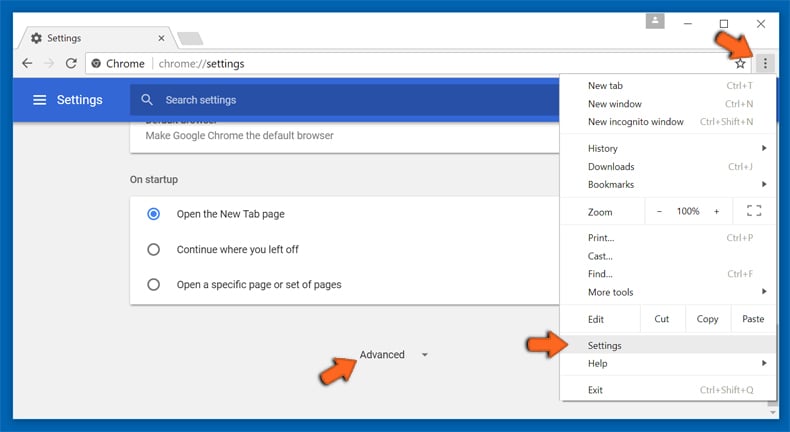
Optional Method
If the problems related to Contech scam email still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
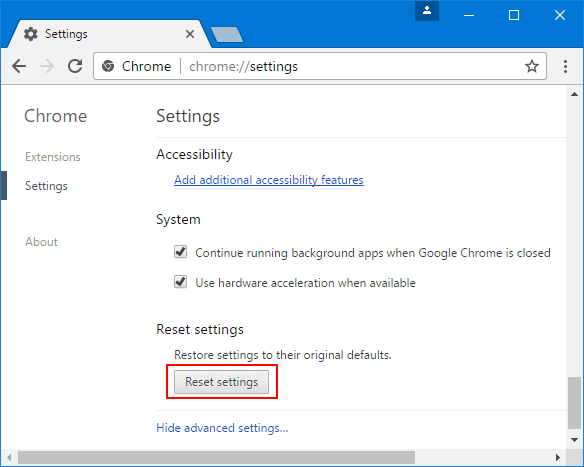
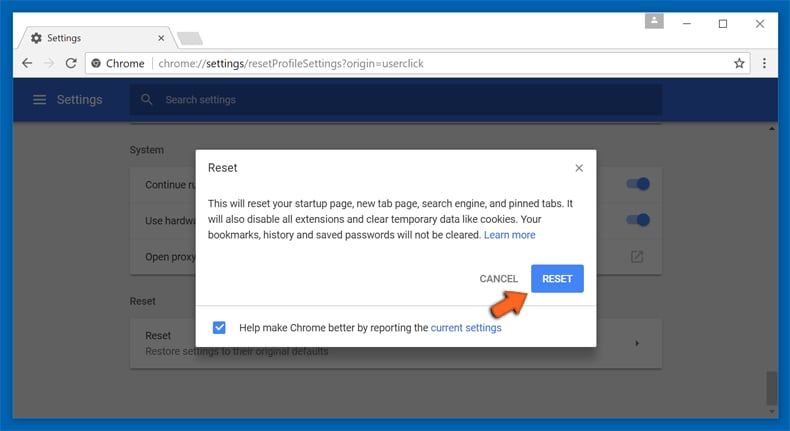
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove Contech scam email plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Contech scam email removal then you have the option to rese the settings of Mozilla Firefox.
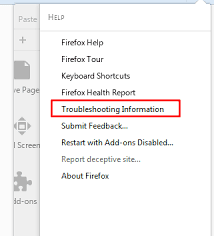
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
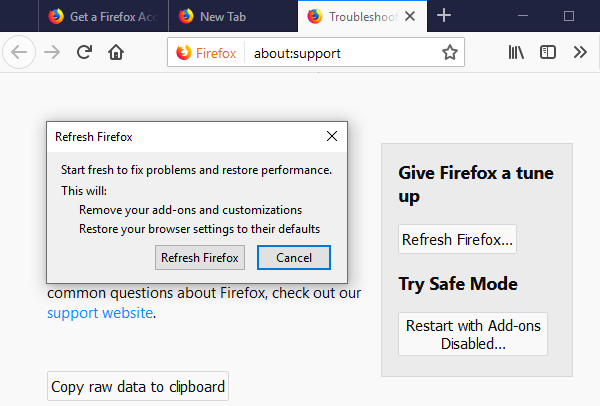
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
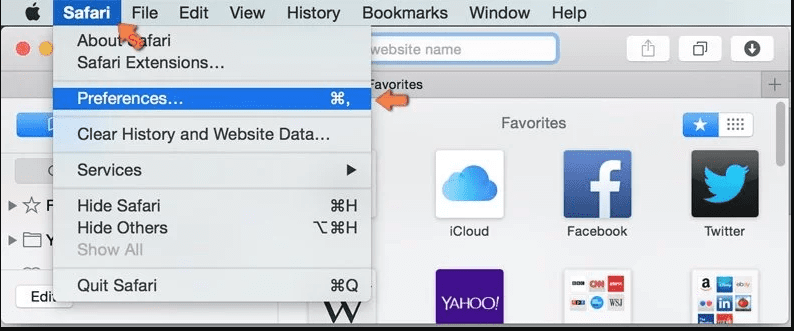
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
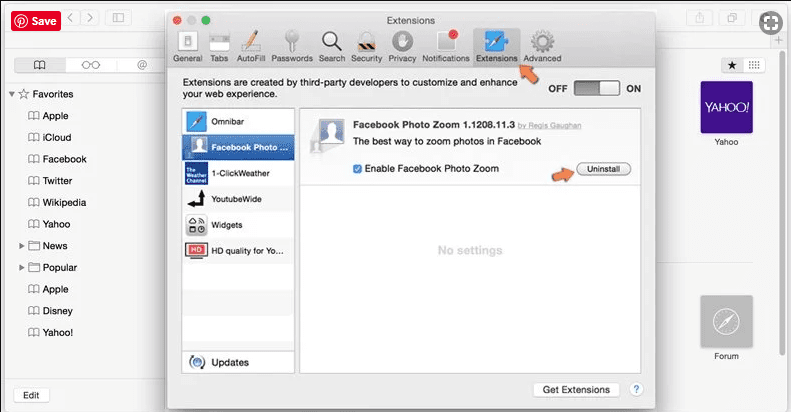
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
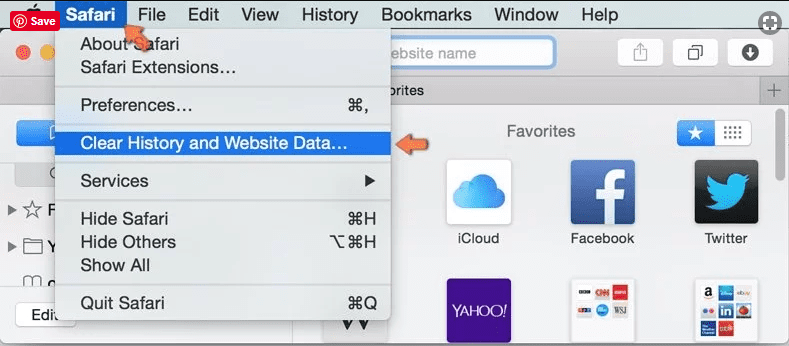
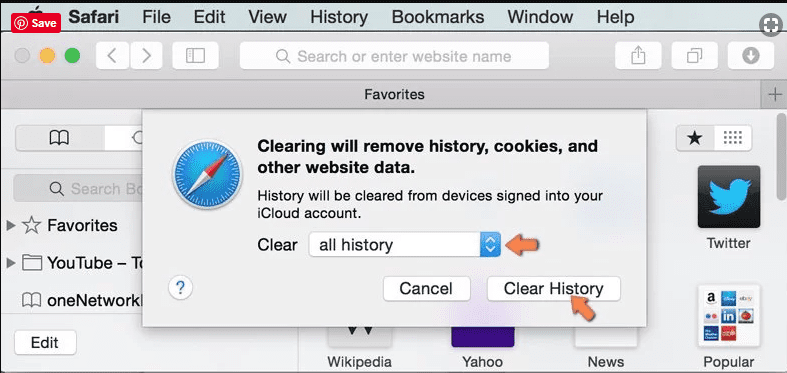
In the newly opened window, select “All History” and then press on “Clear History” option.
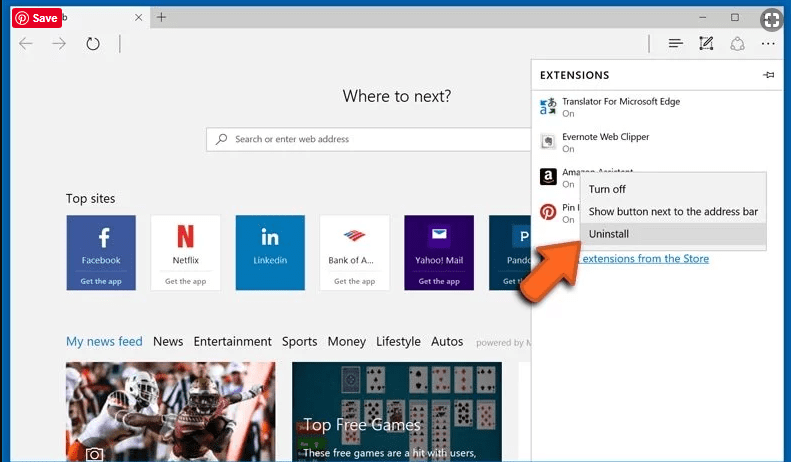
Delete Contech scam email (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
Optional Method
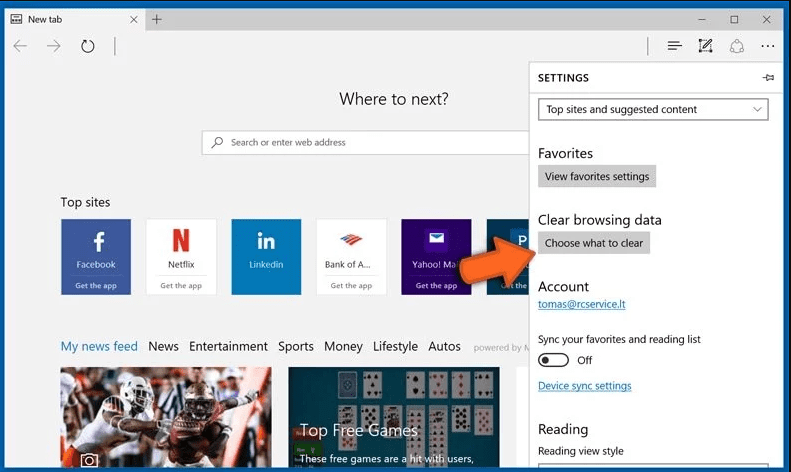
Open the browser (Microsoft Edge) and select “Settings”
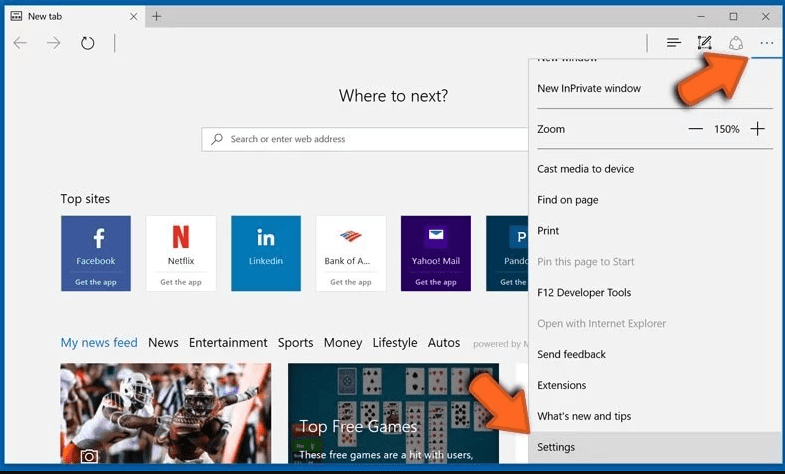
Next steps is to click on “Choose what to clear” button
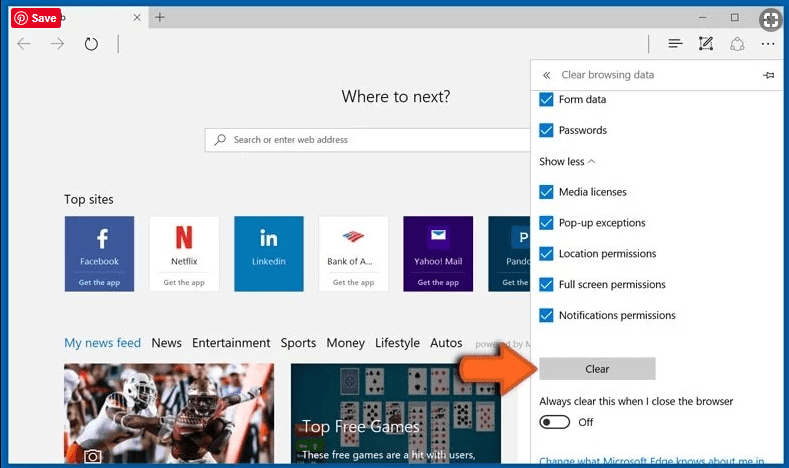
Click on “show more” and then select everything and then press on “Clear” button.
Conclusion
In most cases, the PUPs and adware gets inside the marked PC through unsafe freeware downloads. It is advised that you should only choose developers website only while downloading any kind of free applications. Choose custom or advanced installation process so that you can trace the additional PUPs listed for installation along with the main program.
Special Offer (For Windows)
Contech scam email can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Contech scam email has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.



