How To Remove Apex Enquiry email scam
Easy Guide To Delete Apex Enquiry email scam
Apex Enquiry email scam is a deceptive email scam that is mainly designed to spreads Agent Tesla RAT which is Remote Access Trojan. These letter usually target users, companies, business, and similar objects. The Apex Enquiry email appeal recipients to review the attached file which contains shipments details and provide the important information to continue with order. Opening the attached file cause the installation of Agent Tesla Trojan.
Apex Enquiry email scam states that some of the sender’s industries have been crushed and absence due to the Covid-19 pandemic. So the company provides the best pricing option and delivery time following certain condition which mentions the attached files that is a new inquiry and request recipient. The conditions are listed as quantity between 500 and 1000 pieces and with EXW (Ex Works) shipping terms. If any need for changes recipients are asked to inform the sender. Recipients are requested to specify unit weight, outer packaging measurement and production method. But all the information which provided in Enquiry letters is false. All the statement is fake and bogus. Once opening attached archived file cause the installation of Agent Tesla Trojan.
How Agent Tesla Trojan is harmful For PC:
However, Agent Tesla is a remote access Trojan which is mainly designed as a tool which connects the system with cyber-criminal and allows them to access the system remotely and control the infected PC. The main aim behind to steal user’s personal and confidential information. It has the ability to record key strokes by the key logger. But its main focus to steal login credential such as Usernames and password of various accounts. It also hijacks email, messaging, social media, social networking, online data storage, ecommerce, online money transfer, banking and other accounts which can be used by cyber-criminal to make fraudulent transactions, online purchases and so on. In this way it can lead to financial losses, severe privacy issues and identity theft.
Moreover, Agent Tesla Trojan can block your System security and privacy by the inactivate firewall, task manager, control panel and preinstalled antimalware tool and deeply hides into the PC. It makes loop holes to gets installed other harmful infection like as malware, spyware, adware and other harmful threats. It can corrupt the system files and Windows registries as well as create duplicate and infectious files and registry keys. It also connects the system with remote server to remotely access your system as well as steal your private and sensitive information like as email-id, password, bank account details, IP address, geo location etc. it also consumes huge resources of the System memory to slowdown overall performance. It can gradually decrease the System Performance and makes your PC totally useless. So it is very important to remove Agent Tesla Trojan as soon as possible from your System.
Threat Summary:
Name: Agent Tesla virus
Threat Type: Trojan, password-stealing virus, banking malware, spyware.
Attachment(s) Apex Datasheet.ppt and Important Letter.cab
Symptoms Trojans are designed to stealthily infiltrate the victim’s computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine.
Payload: Agent Tesla
Distribution methods: infected email attachments, malicious online advertisements, social engineering, software ‘cracks’.
Damage: Stolen passwords and banking information, identity theft, and the victim’s computer added to a botnet.
Removal process: we are highly recommended use the reputable automatically removal tool to remove Agent Tesla Trojan completely from system.
How Apex Enquiry email scam intrudes into the System:
Mostly, Apex Enquiry email scam is mainly designed to promote Agent tesla Trojan that usually intrudes into the System with the spam email attachments, bundling methods, Fake update the System Software; Peer to peer sharing files and other social engineering techniques. Spam email often sends by the cyber-criminal which contains malicious attachments like as word, documents, text, PDF, Java scripts and so on with the aim to someone open them. Such types of files look genuine and useful and send by the reputable organization. Opening such types of files might cause the infiltration of lots of infection. Bundling is a deceptive marketing method that promotes the third party freeware software and application with additional features and packages. Mostly users download and installed freeware program without intentionally and with careless. They also Skip to select custom or advance options as well as read their terms and license agreements. Thus this type of the installation is the main cause the infiltration of potentially unwanted program. Update System Software from unofficial or suspicious link as well as sharing files through bad network environments like as emule, torrent, and infected removal devices etc also open back doors to get enters lots of malicious threats.
How To Prevent the System from Apex Enquiry email scam:
We are highly advice be pay attentive while downloading and installing especially freeware program. Don’t try to download and installed freeware from third party site. Always use official or relevant or trustworthy site. Read the installation Guide carefully till the end and select custom or advance option before the proceeding installation process. Users must avoiding the attachments of files which send through unknown sender if seems suspicious. Firstly verify the sender name and address before attachments. Check the grammatical error and spelling mistakes. Users also must update the system from relevant address and official site. Don’t try to share any files from infected devices. Scan the removal devices with reputable antimalware tool before use it to share files. Please scan the system with genuine and powerful antimalware tool regularly. I hope these precaution tips will help you to keep the PC safe and secure forever.
How To Remove Apex Enquiry email scam Automatically:
Apex Enquiry email scam promotes Agent Tesla Trojan that is a very dangerous virus which can badly harm your system if you will not remove it completely from your system at the first detection. It copies itself and distributed into the system in every files. So it is very hard to detect and eliminate from manually as well as normal antimalware tool. Here is given two possible ways to delete Agent Tesla Trojan infection. First is Automatic Removal tool and second is manually step. As discussed above it is impossible to eliminate manually. Manual Steps is very hard to follow and time consuming process. So we are highly recommended you should use a powerful Automatic removal tool which can easily detect and remove Apex Enquiry email scam completely from your system.
Special Offer (For Windows)
Apex Enquiry email scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Apex Enquiry email scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
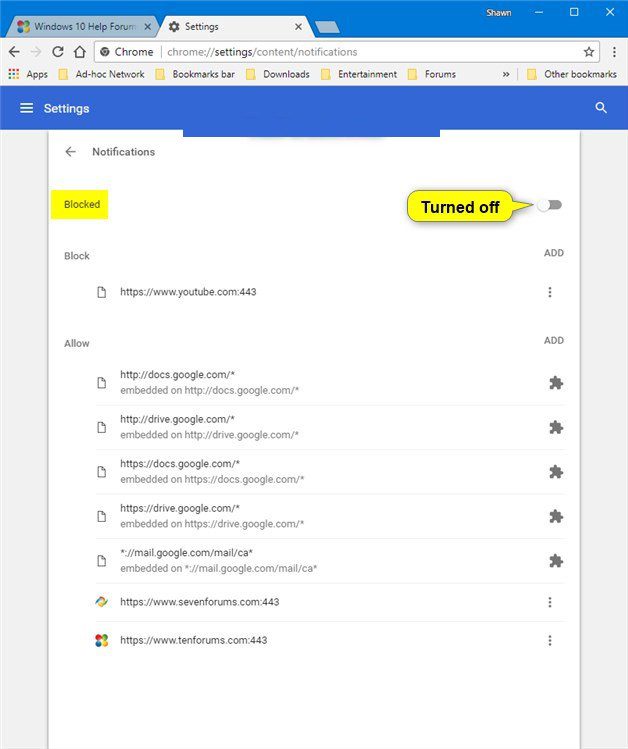
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
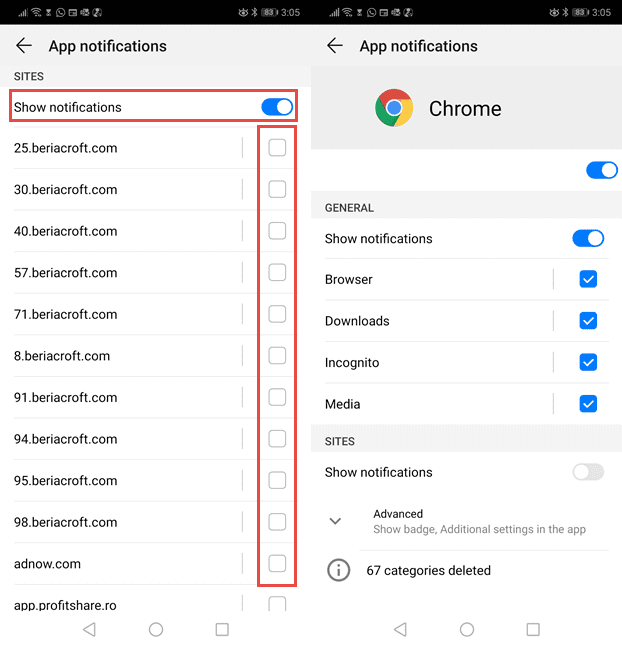
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
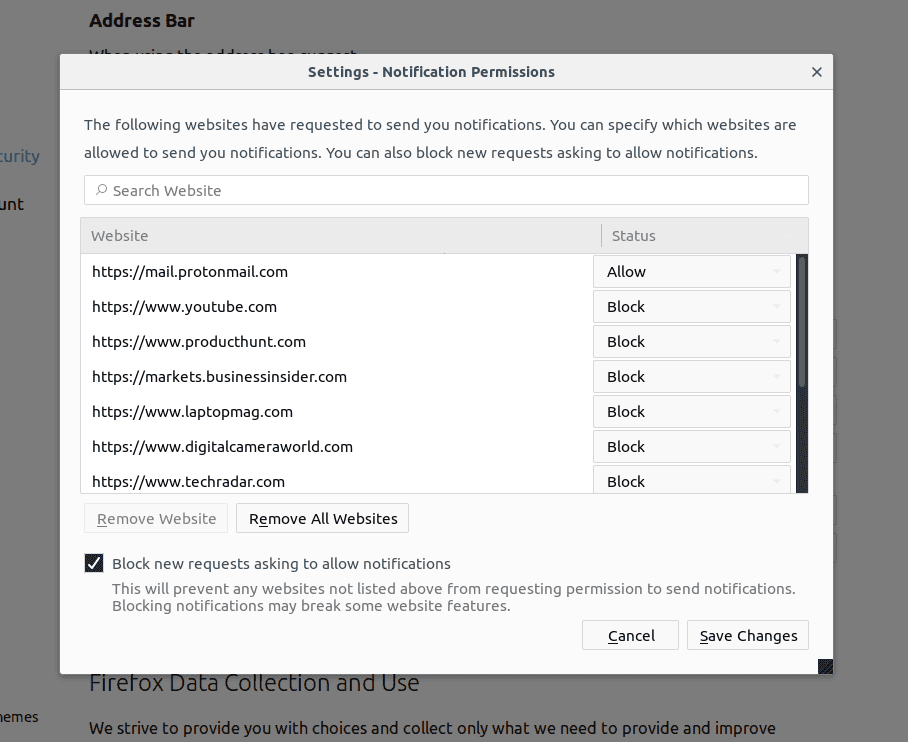
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
Internet Explorer
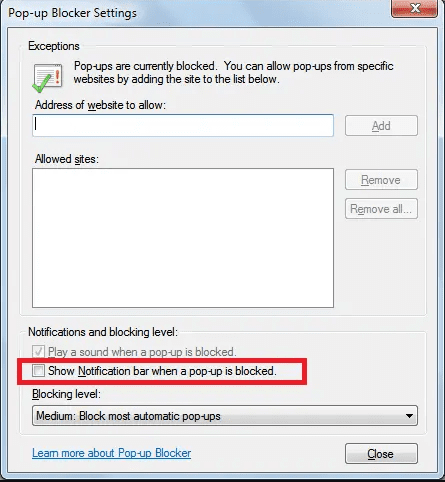
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
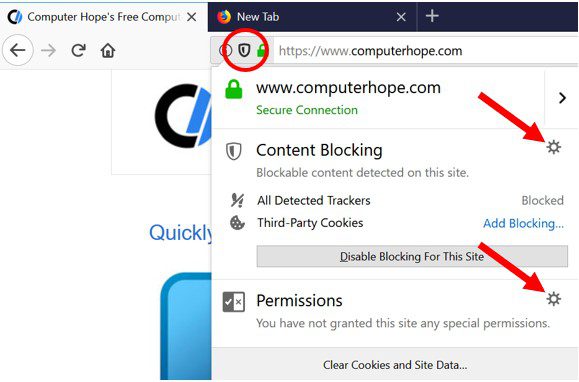
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
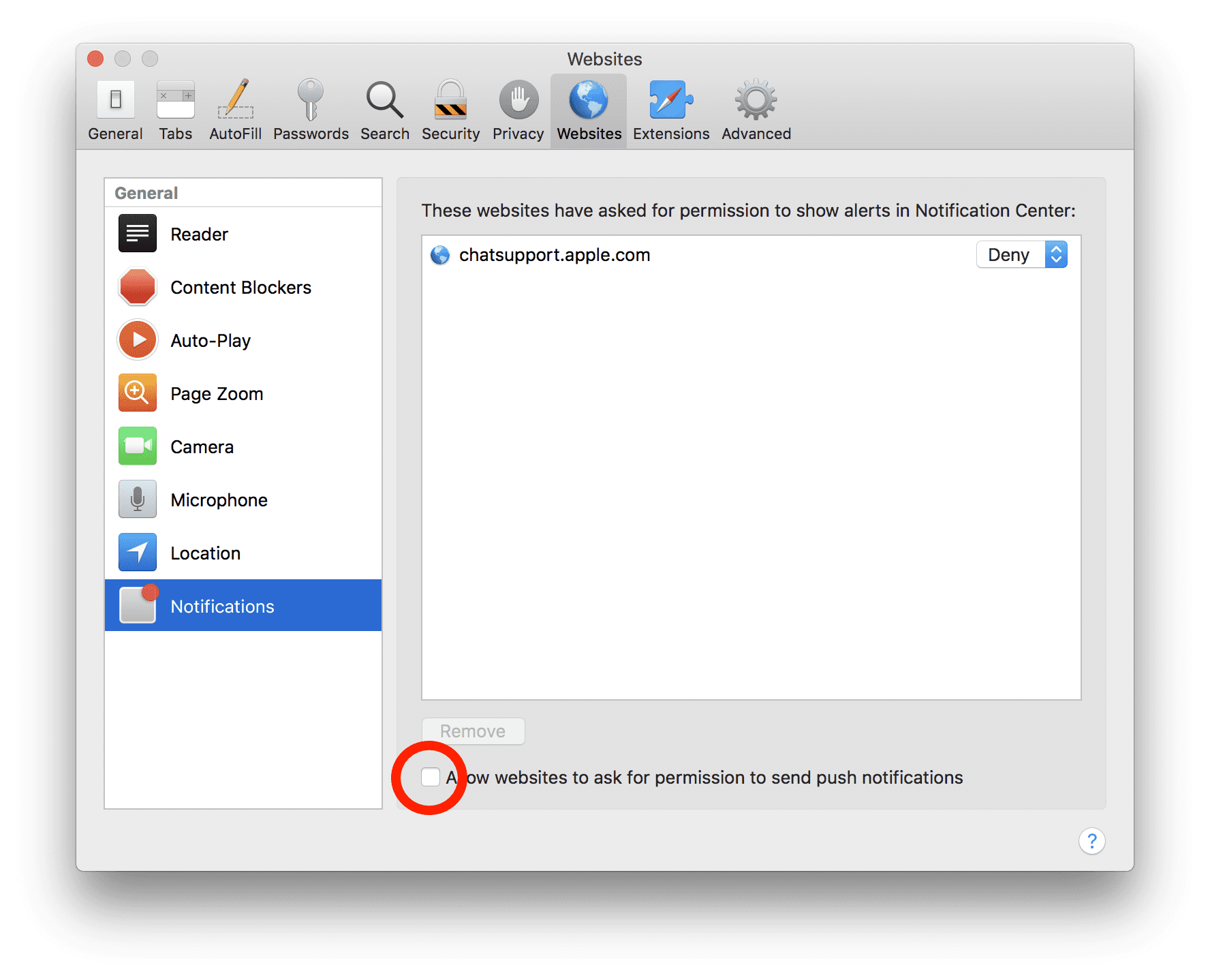
Manual Steps to Remove Apex Enquiry email scam:
Remove the related items of Apex Enquiry email scam using Control-Panel
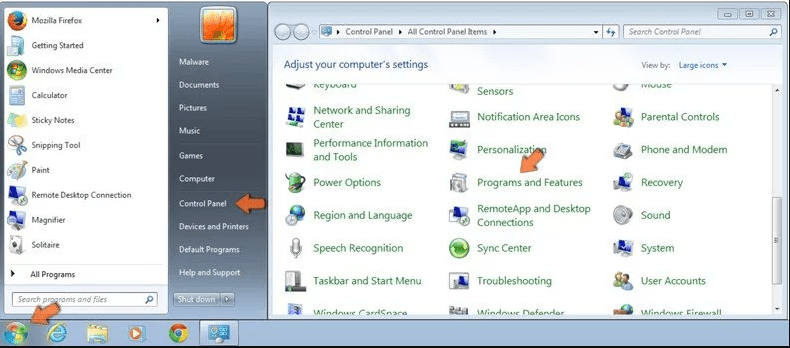
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
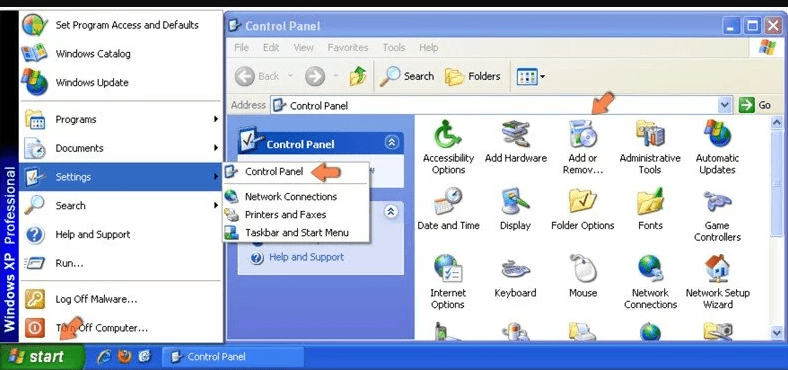
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
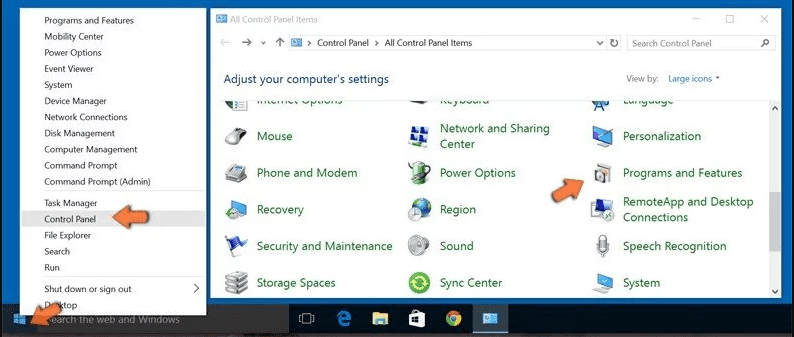
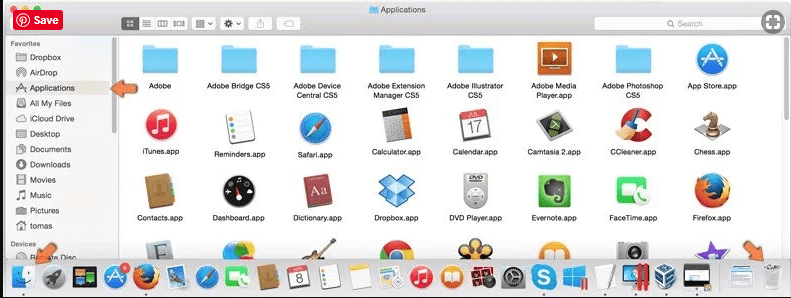
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
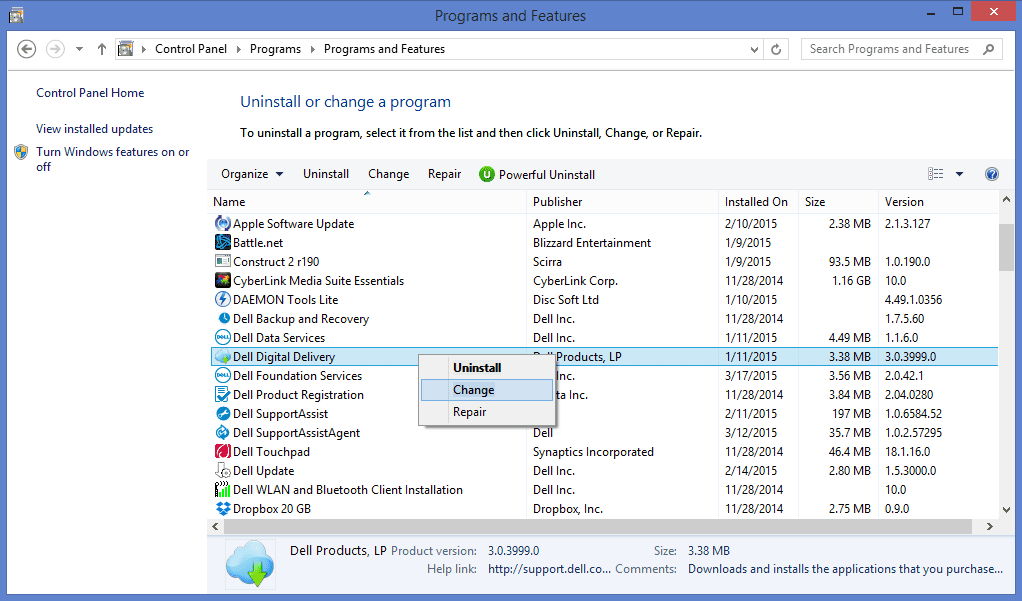
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Apex Enquiry email scam issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Apex Enquiry email scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Apex Enquiry email scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Apex Enquiry email scam) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
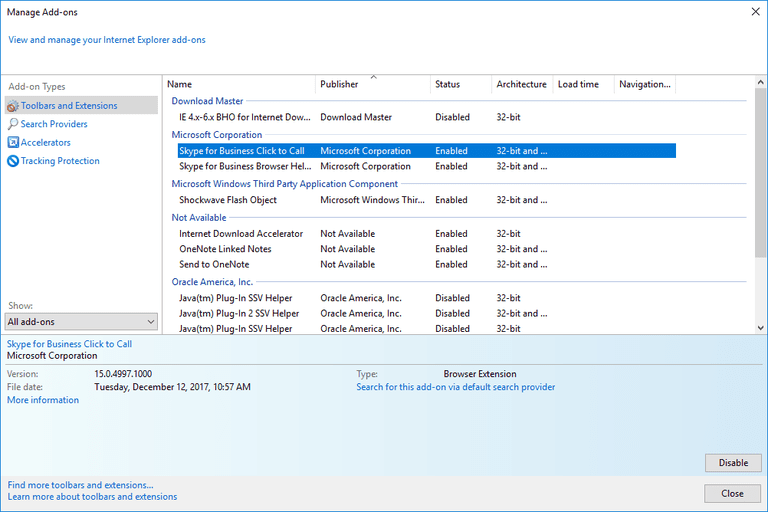
Additional Option
If you still face issues related to Apex Enquiry email scam removal, you can reset the Internet Explorer to its default setting.
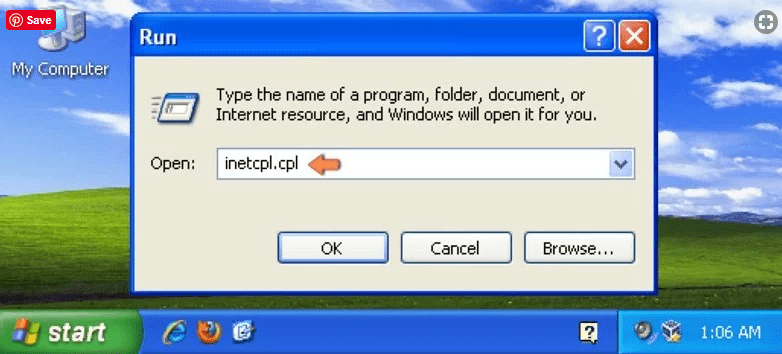
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
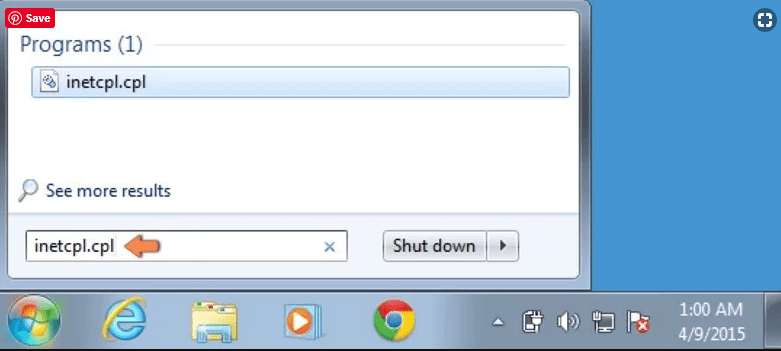
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
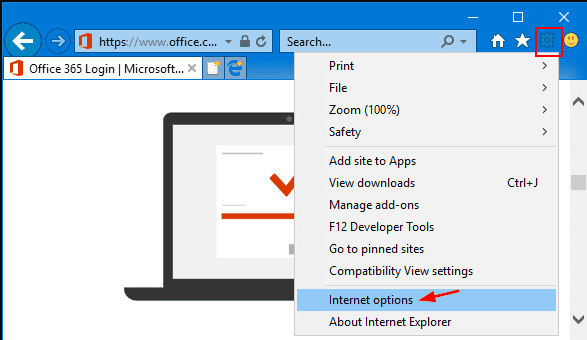
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
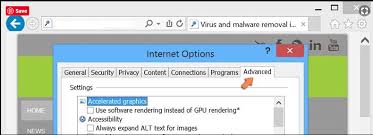
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
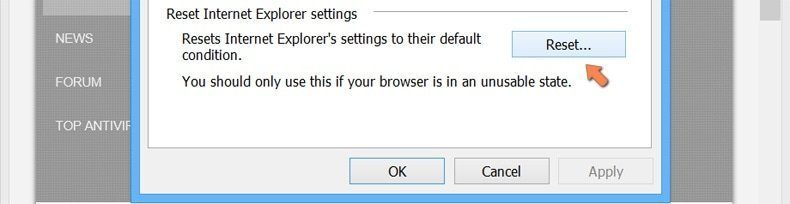
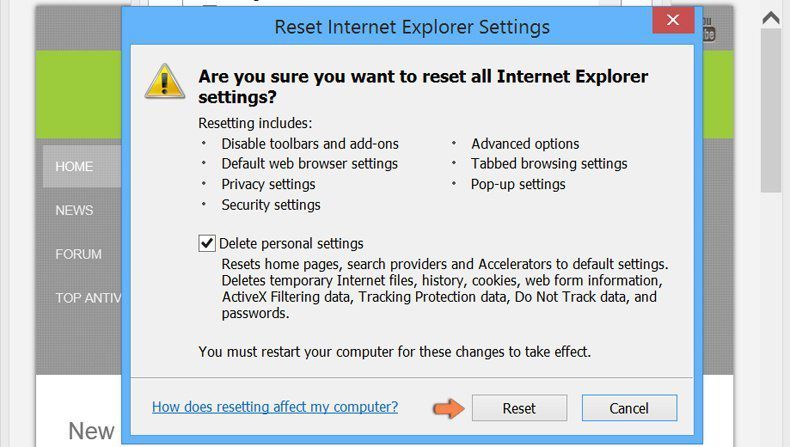
You have to press on the “Reset” button again to confirm that you really want to reset the IE
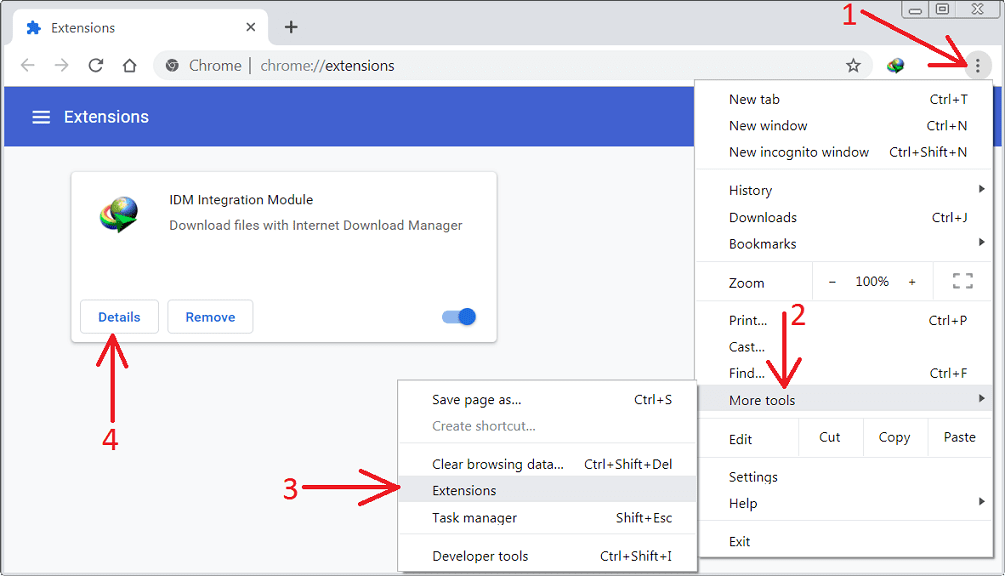
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
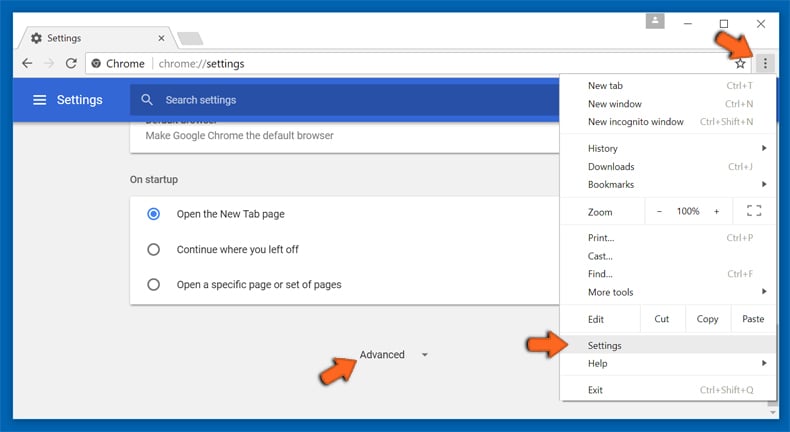
Optional Method
If the problems related to Apex Enquiry email scam still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
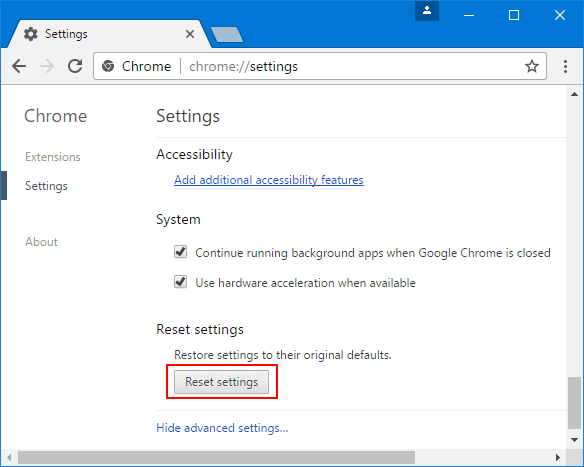
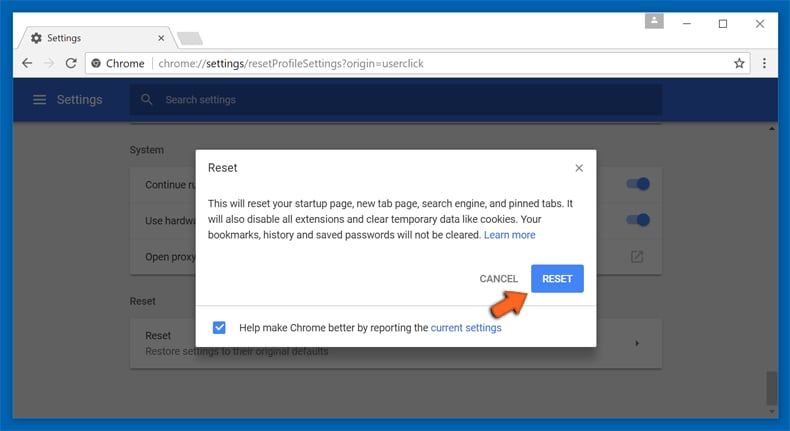
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove Apex Enquiry email scam plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Apex Enquiry email scam removal then you have the option to rese the settings of Mozilla Firefox.
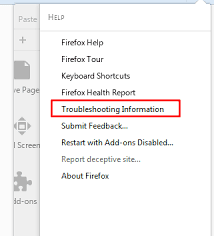
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
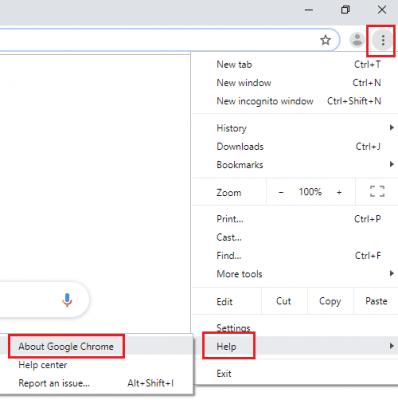
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
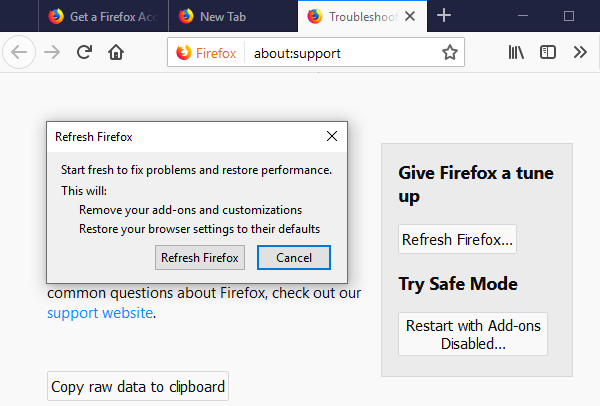
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
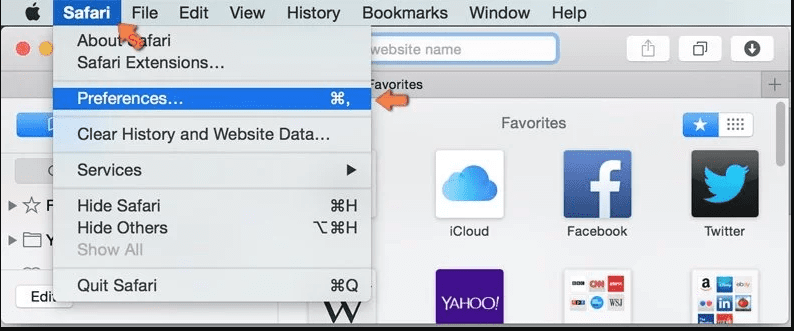
Open the Safari and go to its “Menu” and select “Preferences”.
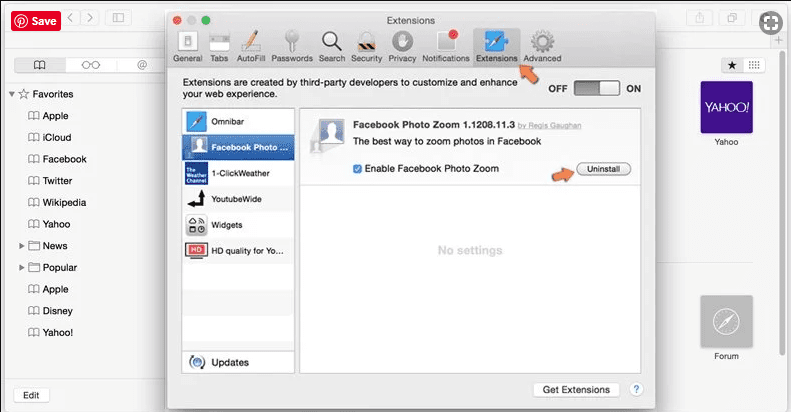
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
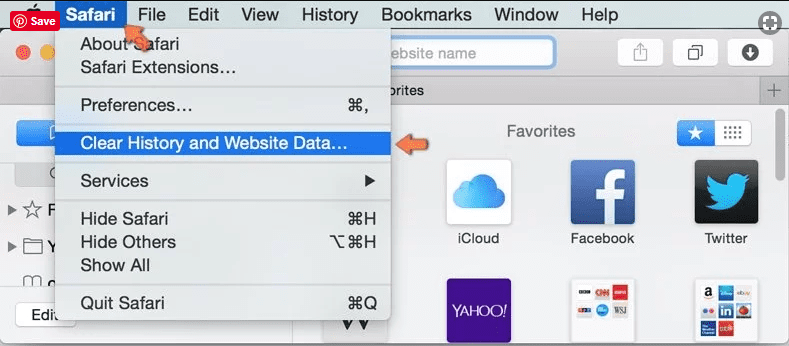
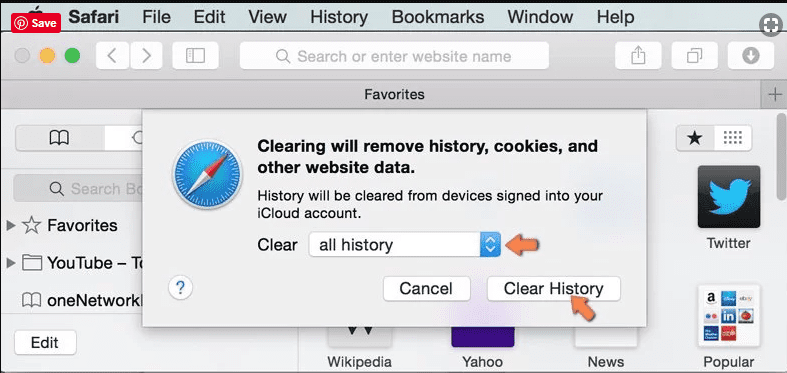
In the newly opened window, select “All History” and then press on “Clear History” option.
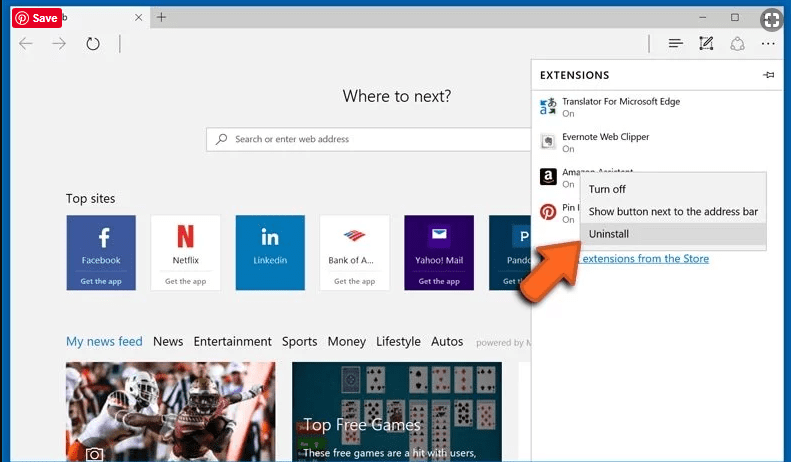
Delete Apex Enquiry email scam (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
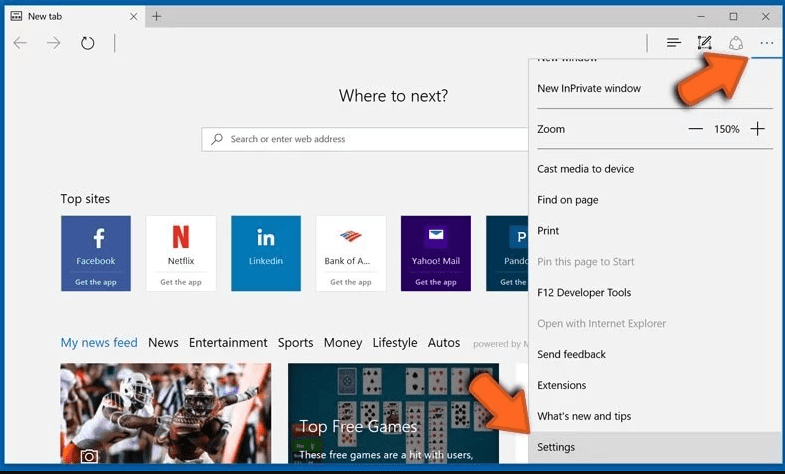
Next steps is to click on “Choose what to clear” button
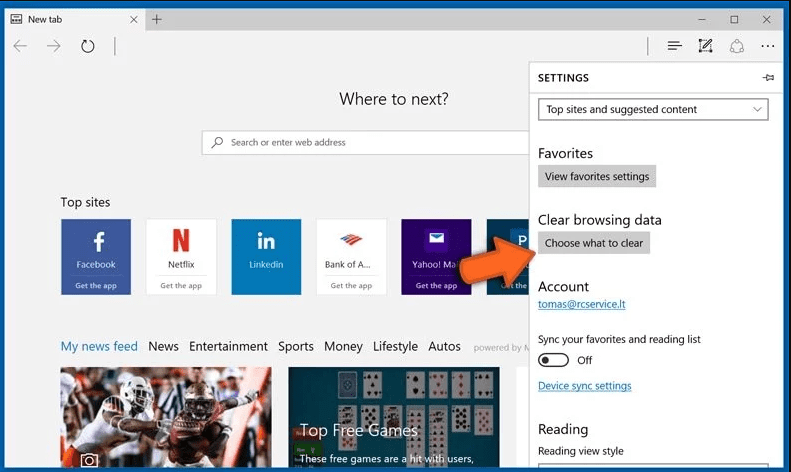
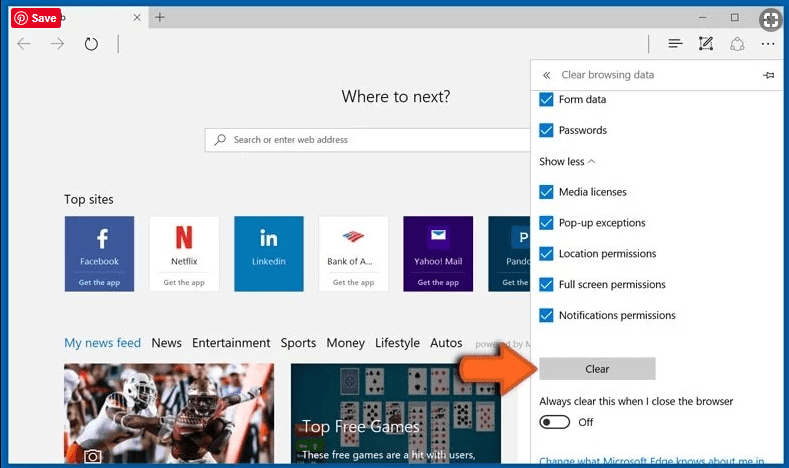
Click on “show more” and then select everything and then press on “Clear” button.
Conclusion
In most cases, the PUPs and adware gets inside the marked PC through unsafe freeware downloads. It is advised that you should only choose developers website only while downloading any kind of free applications. Choose custom or advanced installation process so that you can trace the additional PUPs listed for installation along with the main program.
Special Offer (For Windows)
Apex Enquiry email scam can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wiat for next 48 hours. If you intend to remove detected therats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Apex Enquiry email scam has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.


