Exposing Hiyashopsale.store: Uncovering the Alleged Scam
Hiyashopsale.store, the seemingly tempting e-commerce site offering discounted products, isn’t what it appears to be. It’s a deceptive platform created by cyber criminals to exploit unsuspecting users. This site is not here to provide you with a good deal; it’s designed to trick you and potentially harm you.
While it may look like a regular online store, Hiyashopsale.store operates with malicious intent. If you decide to make a purchase, be prepared for disappointment. The products you receive might be low-quality knockoffs, or worse, you might not receive anything at all. The site could even provide you with a fake tracking number, leaving you waiting for a package that will never arrive.
However, the deception goes beyond mere financial loss. Hiyashopsale.store is part of a more significant cyber threat. Instead of just taking your money, the main goal is to steal your valuable data. In today’s digital age, data is highly sought after by cybercriminals. Once you visit Hiyashopsale.store, your personal information is immediately at risk. The website tracks your IP address, location, and device details.
When you’re buying something on Hiyashopsale.store, they make you create an account. This might seem normal, but it’s a big problem. Your email and password become vulnerable, especially if you use the same password elsewhere. When you’re putting in your credit card details, thinking it’s a safe payment portal, it’s not. It’s like a fancy cover over a basic design – just HTML and CSS. Here’s the real shocker: there are no real payment companies involved. You’re basically giving your credit card info straight to the bad guys.
To add to the danger, the payment form asks for more than just your card details. They want your full name, home address, and phone number. Now, these cybercriminals have a ton of your info – credit card stuff, name, address, country, phone number, email, and password. That’s almost everything they need to steal your identity or do other nasty things with your data.
In essence, Hiyashopsale.store is not just an untrustworthy shopping site; it’s a dangerous platform seeking to exploit your trust and compromise your personal information. It’s crucial to be aware of such deceptive websites and prioritize your online security by avoiding them altogether.
Modus Operandi of Hiyashopsale.store Scam
The internet is a vast and interconnected space where people connect, shop, and share information. However, within this digital realm, there exists a dark side – a breeding ground for cybercrime and malware attacks. Hiyashopsale.store is one such website that serves as a starting point for a dangerous scheme, contributing to the rising tide of cyber threats.
The first step in this elaborate plot involves luring unsuspecting users through deceptive advertisements. These cybercriminals strategically promote Hiyashopsale.store on popular social media platforms like Facebook, Instagram, and TikTok. Using sponsored content, they claim to offer clearance sales or closing deals with massive discounts. Sometimes, they even mimic well-known brands to trick individuals.
Despite the dubious nature of these offers – after all, who wouldn’t be suspicious of unrealistically steep discounts – people are drawn in. The allure of saving money blinds them to the potential risks. Little do they know that these cybercriminals are setting a trap that could lead to disastrous consequences.

Once users land on Hiyashopsale.store, the real danger unfolds. Psychological tactics come into play, creating a sense of urgency with limited-time offers and countdowns. To further dispel suspicions, fake notifications claiming recent purchases pop up at the bottom of the screen. What users might not realize is that just visiting the site already logs their geolocation, IP address, and device type.
Creating an account on Hiyashopsale.store exposes even more sensitive information. This includes potential email and password combinations. If a user goes a step further and completes a purchase, their credit card number, full name, home address, and phone number become vulnerable to exploitation.
The cybercriminals’ goal isn’t just the immediate gain from scamming users on Hiyashopsale.store. Instead, they seek valuable data that can be exploited in various ways. Email receipts may come with malware-infected attachments, and tracking numbers for non-existent or substandard shipments add to the confusion.
Once the initial chaos subsides, cybercriminals move on to the next phase – using the obtained credit card details for their gain. They may order expensive items to a location where they can retrieve them undetected. The small amount scammed from Hiyashopsale.store is just a stepping stone to their larger plan.
But the danger doesn’t end there. Cybercriminals pivot to phishing messages and emails once they’ve exhausted the initial data. Armed with the information users provided to Hiyashopsale.store, these phishing attempts may appear authentic. Users are urged to verify unknown sources, avoid opening attachments, and steer clear of unfamiliar URLs to prevent falling victim to these scams.
As the cybercriminals gather more data, they turn to the dark web to sell it to third parties or exploit it for their malicious purposes. Your data becomes a commodity, accessible to various threat actors with nefarious intentions. This distribution on the internet opens the door to a multitude of potential attacks targeting you specifically.
The worst part of this cybercrime is identity fraud. The bad guys collect enough info to pretend to be you. They might take out loans or ask for money from your friends and family, pretending it’s you. This can cause big problems, not just for you, but for the people close to you too. It’s like someone stealing your identity and using it to do bad things that you’ll get blamed for.
Hiyashopsale.store is not just another website; it’s a gateway to a complex and dangerous cybercrime operation. The repercussions of falling victim to such schemes extend beyond immediate financial losses, reaching into the realm of identity theft and potential harm to one’s personal and financial well-being.
How to identify Fake Online Stores

To help users avoid future problems, we’ve compiled methods to identify fake online stores. This guidance can aid in avoiding such situations and, ideally, shield other unsuspecting users from comparable encounters down the line.
- Similar Website Designs: Bad people on the internet make fake websites like Hiyashopsale.store to trick people. They create many fake sites together to fool lots of users. Hiyashopsale.store might be one of many we haven’t found yet. Learn how to tell if a website is fake. One clue is that bad people often use the same design for all their fake sites. While many website themes are out there, these bad guys tend to use a small number of designs a lot.
- Unbelievable Discounts: If a deal seems too good to be true, it probably is, especially when shopping online. Be careful and don’t trust super cheap offers; they’re often traps to make you buy fake stuff or get nothing in return. Look for discounts at real stores during sales events like Black Friday.
- Stolen Product Images: Fake online stores like Hiyashopsale.store might not have real product images, so they use stolen pictures from other places. Check the legitimacy of an online store by using tools that can search where the product images come from. If they appear in other places online, it might be a scam.
- Lack of Customer Reviews: When we checked Hiyashopsale.store, there were almost no customer reviews about the products they sell. Usually, people read reviews to know if a store is trustworthy. If a website has very few or no reviews, it’s suspicious. Sometimes, fake stores create fake positive reviews to trick people. If you find any negative reviews, the store might be removing them to look legit.
- Check for Genuine Sales Events: Instead of falling for big discounts on fake websites, wait for real sales events from trusted stores. Legit ways to save money through discounts exist, but sites like Hiyashopsale.store are not safe. They could lead to losing money and even identity theft. Be patient and wait for genuine sales from well-known stores.
- Caution with Irresistible Offers: Be careful when online shops offer deals that are too good to resist. These are often tricks to fool people. Stay cautious and don’t trust offers that seem too amazing. Stick to well-known stores during big sales, and you won’t fall into the trap of fake discounts.
- Use Reverse Image Search Tools: To check if a website is lying, use tools that look for where the pictures come from. Copy and paste product images into tools like Duplichecker and Tineye. If the images are used elsewhere, it might be a scam.
- Look for Genuine Customer Reviews: Real customer reviews help you decide if a store is good. Hiyashopsale.store had very few reviews, making it suspicious. If a website lacks reviews or only has a few, be careful. Fake stores might create fake positive reviews. If you find any bad reviews, the store could be hiding them.
- Beware of Genuine-Looking Scams: Sometimes, fake stores seem real, but they’re scams. They might look like they have good deals, but it’s all a trick. Always double-check. Don’t be fooled by how real a site looks. Follow the steps mentioned to make sure it’s safe before buying anything.
In a nutshell, be smart online. Don’t trust everything you see, especially if it seems too good to be true. Use tools and common sense to avoid falling into the traps set by cybercriminals.
What are the methods used by Hiyashopsale.store to deceive buyers?

Hiyashopsale.store tricks people who buy things on their website using many tricky methods. They focus on people who don’t know about their tricks. One big trick is that they don’t give what they promise to buyers, so buyers lose money and get nothing in return.
Our detailed look into the website and the people behind it found that they have a complex plan to fool buyers. It’s not just about not giving products; it’s about how they cheat people when they’re paying. They are very careful in tricking people when they are giving their money. This shows how smart they are at tricking and making people believe them.
Exploit your personal information and email for malicious purposes
Hiyashopsale.store is like a tool used by bad people to harm you. It can turn any information you give them into a weapon against you. For example, when you share your email while buying something, they secretly use it to send fake emails that try to trick you.
These fake emails want you to click on them, making you more involved in their lies. Also, if you use the same email and password for other websites, they might use that to get into your other accounts.
The information they collect might be sold to others who want to show you ads or even to people who do bad things on the internet. This shows how serious the danger from Hiyashopsale.store is. It’s important to be very careful and protect yourself online.
Fraudsters may manipulate your credit card to make unauthorized transactions

When customers try to pay for their purchases, they see a system that doesn’t keep their card information private. The website only lets people use credit/debit cards because they’re harder for scammers to misuse. PayPal is safer with extra security.
Scammers secretly get real credit card numbers, dates, and codes. Then they buy expensive things using those stolen details.
To hide, scammers change where products go after buying. People who got tricked end up with huge credit card bills for things they didn’t buy. The scammers’ tricky plan uses how payments work and where things are sent, making victims lose money and trust.
What to do if Fallen Victim to the Hiyashopsale.store Scam

If you’ve found yourself ensnared by the Hiyashopsale.store scam, fear not. In this guide, we’ll walk you through practical steps to mitigate the damage and safeguard your online presence.
Report to Authorities
Your first line of defense is to report Hiyashopsale.store to the appropriate authorities. By doing so, you contribute to the collective effort in bringing down malicious websites. Use the following links to submit detailed reports:
Fill out the forms with specific details to facilitate a swift investigation by the authorities.
Contact Your Bank for a Refund and Transaction Stop
Swift action is crucial after making a purchase on Hiyashopsale.store. Contact your credit card issuer immediately, informing them about the unauthorized purchase. Provide details such as the specific product(s) bought and where the transaction occurred. Initiate a chargeback, a process allowed by card networks and the Electronic Fund Transfer Act (EFTA). This enables you to dispute the transaction and request your bank to cancel the payment to the fraudulent website.
Moreover, ask your your bank to prevent any future transactions on your credit card. Additionally, contemplate activating either a fraud alert or a credit card freeze, providing an additional safeguard against potential financial losses.
Update Login Details and Enable Two-Factor Authentication
To prevent further security breaches, it’s crucial to update your login details. Since Hiyashopsale.store has access to your email address and password used during registration, using the same credentials on other sites poses a risk. Enhance security across all your accounts by enabling two-factor authentication and regularly resetting passwords.
Two-factor authentication requires a verification step before logging in, such as entering a code sent to your phone number. This added layer ensures that only you, with access to the code, can log in to your accounts. Unexpected two-factor verification requests indicate potential unauthorized access attempts.
Protect Against Future Cyberattacks with Antivirus Software
Given that Hiyashopsale.store is a creation of cybercriminals, there’s a risk of receiving fake receipts infected with malware. To prevent such threats, investing in a reliable antivirus program is crucial. Consider using SpyHunter, which offers real-time protection against malware threats from various sources.
This becomes especially important for those using computers for work and mobile devices like Android phones, which are susceptible to spyware, Trojans, and malware infections. A standout feature of SpyHunter is its real-time protection, ensuring continuous safety from malware threats.
Understanding the Importance of Antivirus Programs
Antivirus programs, like SpyHunter, play a vital role in safeguarding your digital life. They act as a shield against malware, which can come in various forms, from fake receipts to phishing emails. With your email and other data compromised, cybercriminals can create targeted phishing emails with harmful attachments and links leading to dangerous websites.
The key to preventing malware infections is proactive defense. SpyHunter’s real-time protection acts as a vigilant guardian, constantly scanning for potential threats and neutralizing them before they can harm your system. This is particularly crucial for those using their computers for work, where sensitive information is at stake.
How can malicious websites (browser-hijackers) exploit vulnerabilities in web browsers?
Malicious websites such as fake online stores can take advantage of weaknesses in web browsers to harm your computer. They might use these weaknesses to deceive you into purchasing counterfeit products, install harmful software without your knowledge, steal your personal information, or trick you into downloading harmful files.
These websites could use clever tricks or codes that the browser doesn’t fully understand, allowing them to take control and do bad things. It’s important to keep your browser updated and be cautious of unfamiliar websites to stay safe from these sneaky tricks. In case, you’ve got misled into installing harmful app which changed the way your browser works, follow the steps below to remove the infection and revert the browser settings:
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
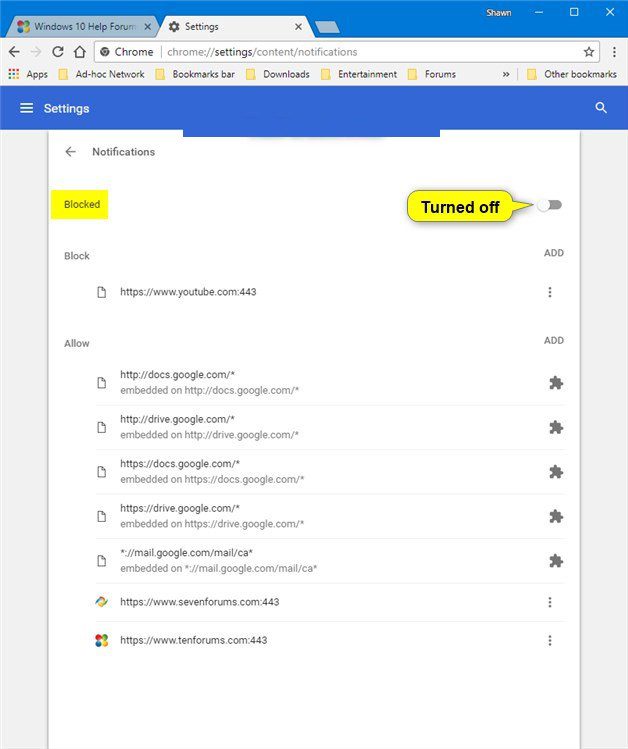
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
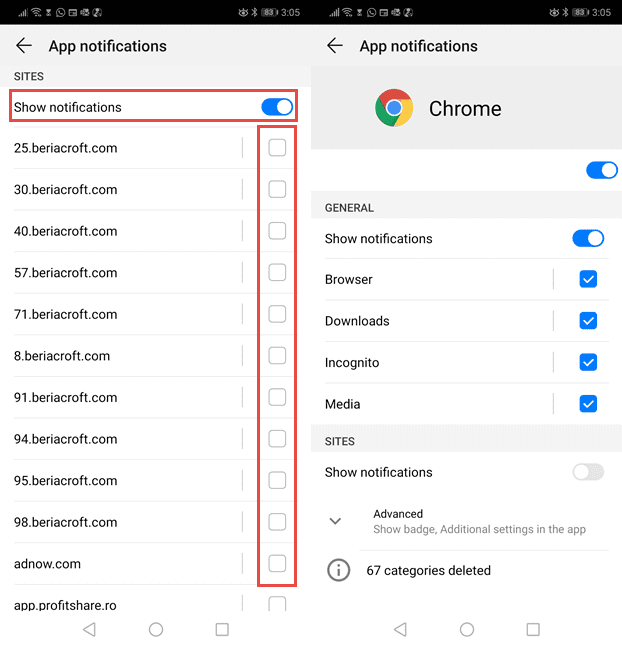
Google Chrome (Android)
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
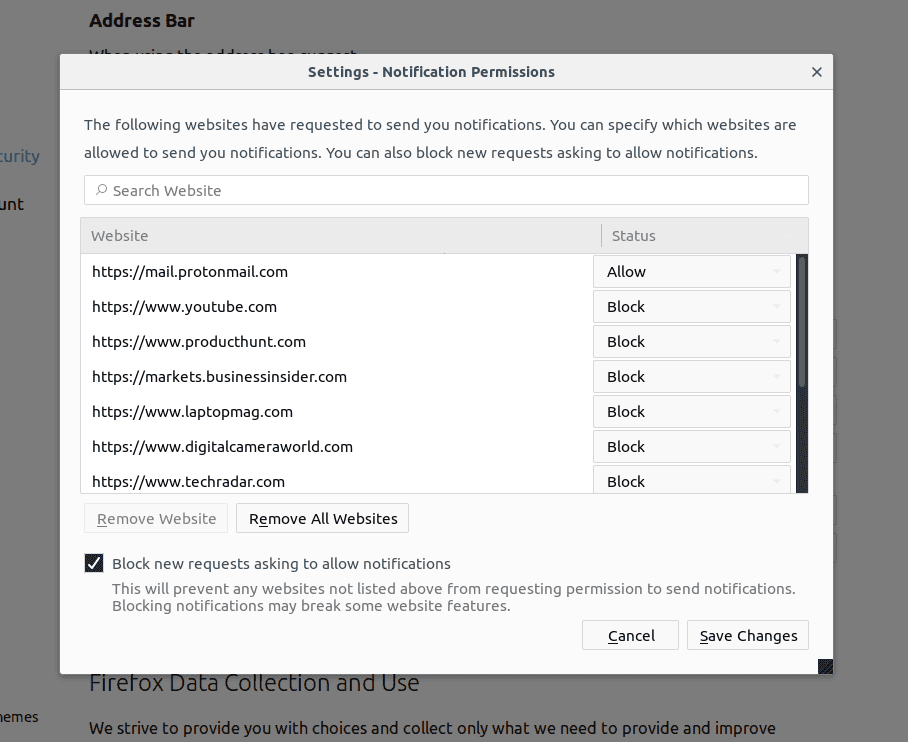
Internet Explorer
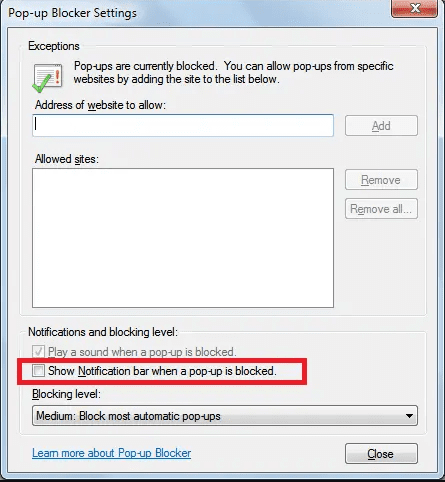
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
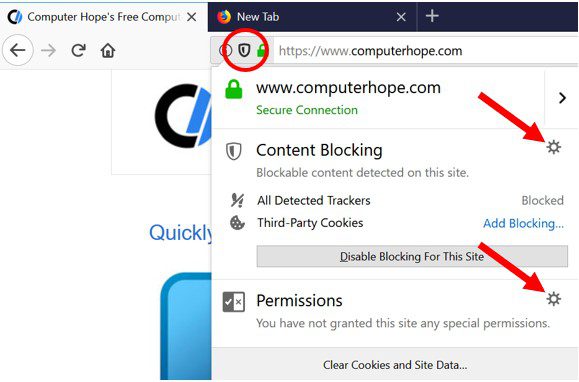
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
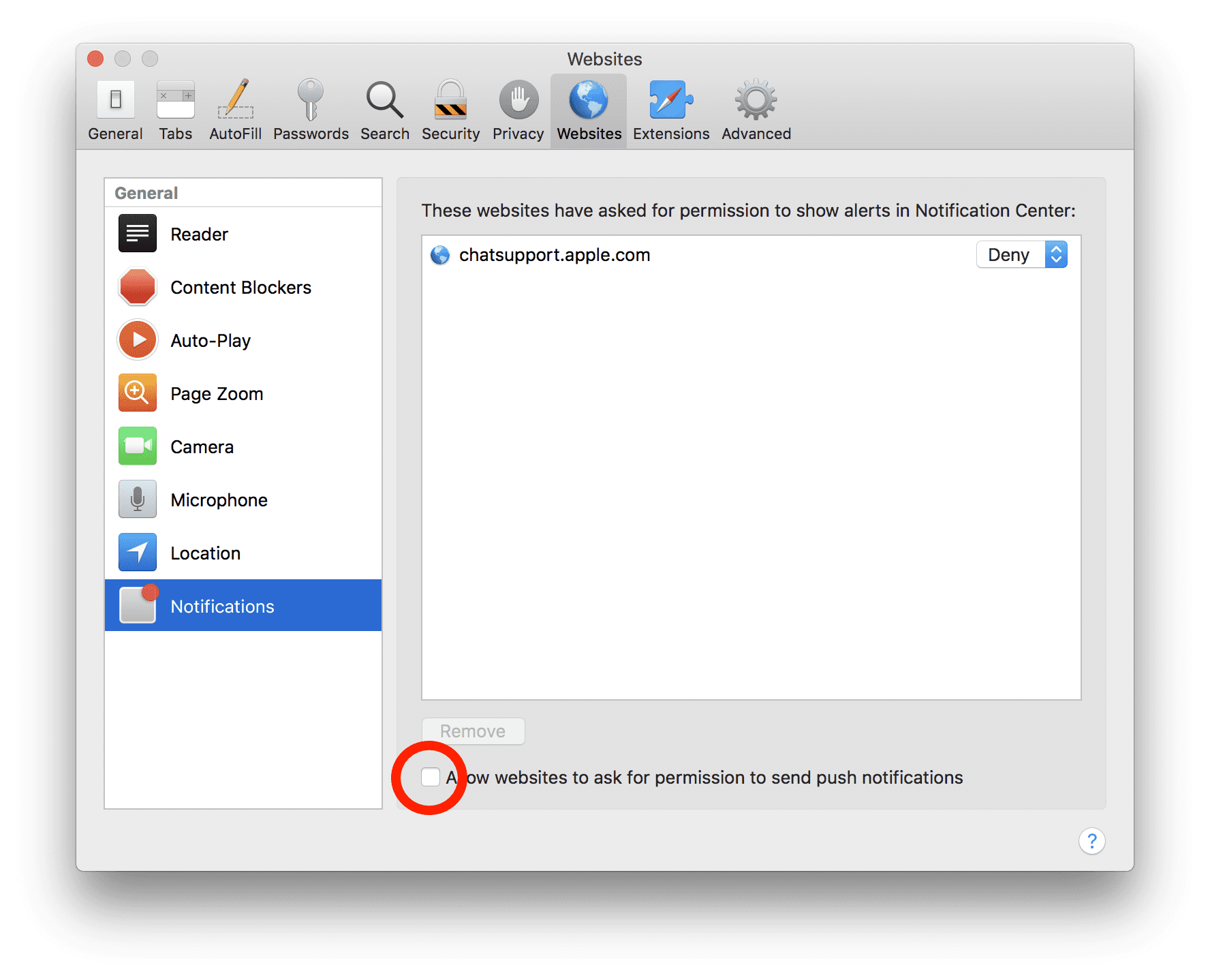
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove browser-hijacker:
Remove the related items of browser-hijacker using Control-Panel
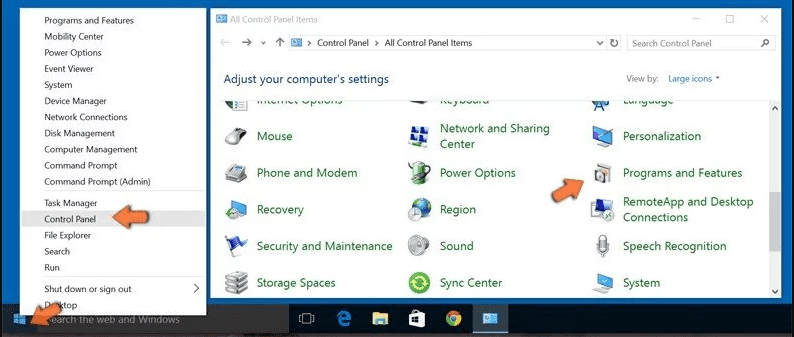
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
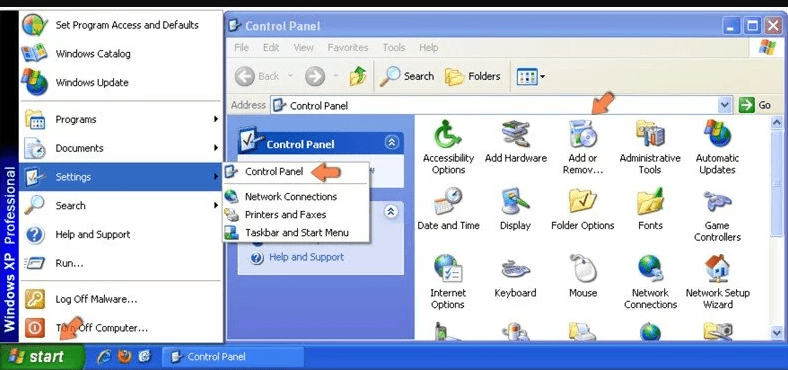
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
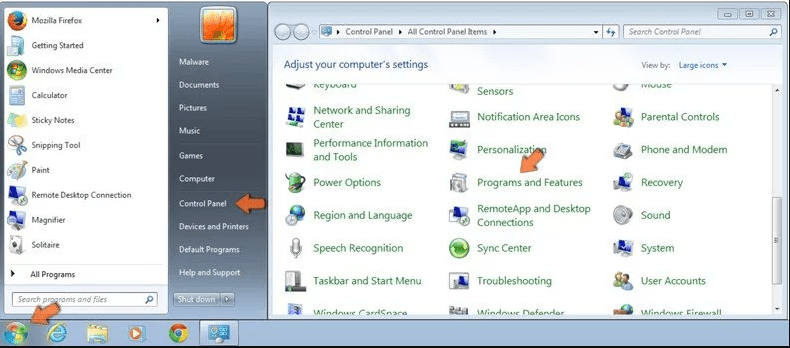
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
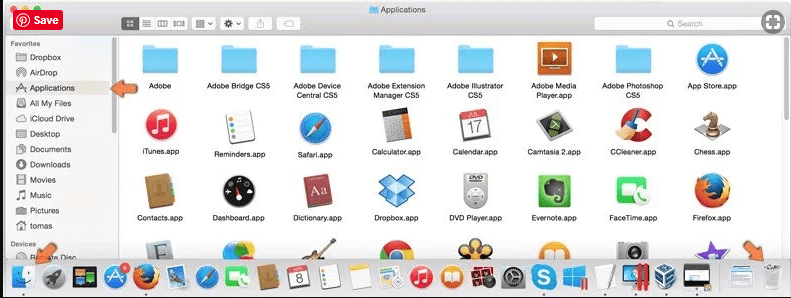
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
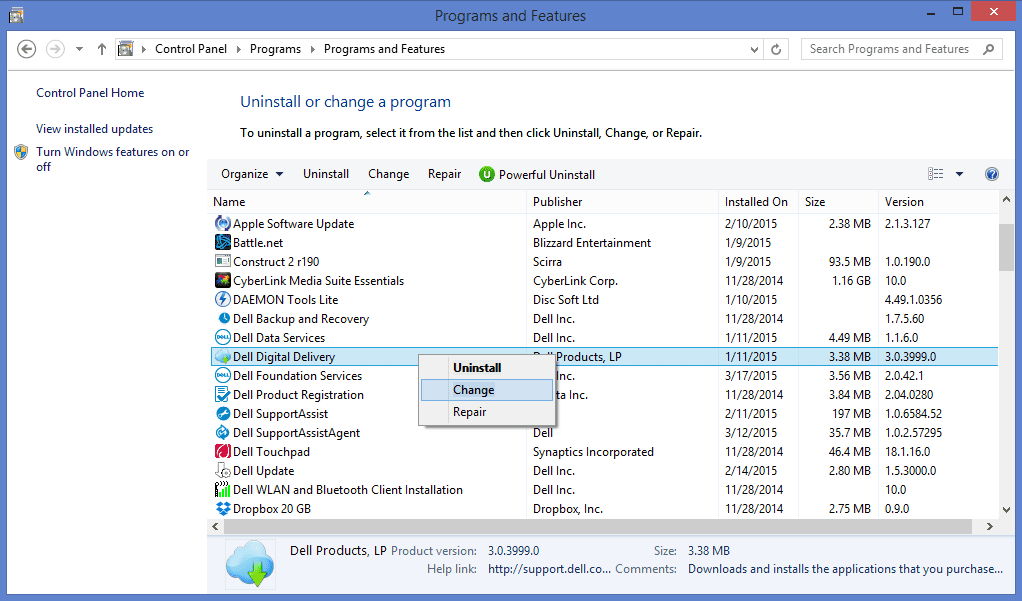
After you uninstall all the potentially unwanted program causing browser-hijacker issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (browser-hijacker) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
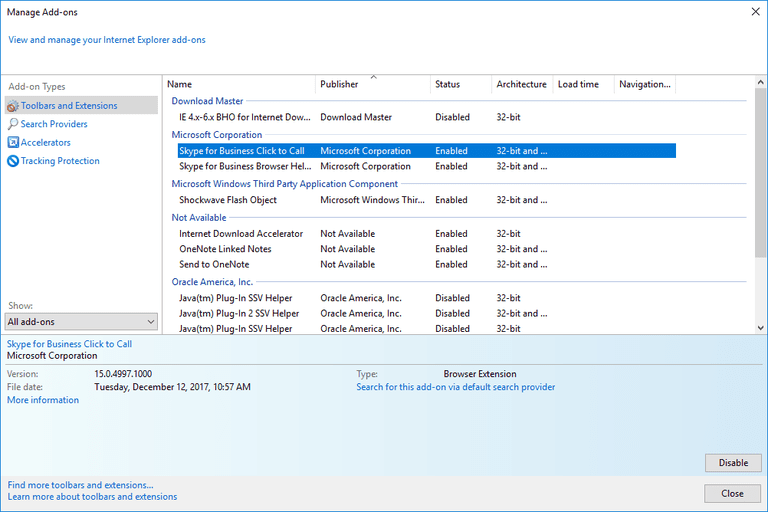
Additional Option
If you still face issues related to browser-hijacker removal, you can reset the Internet Explorer to its default setting.
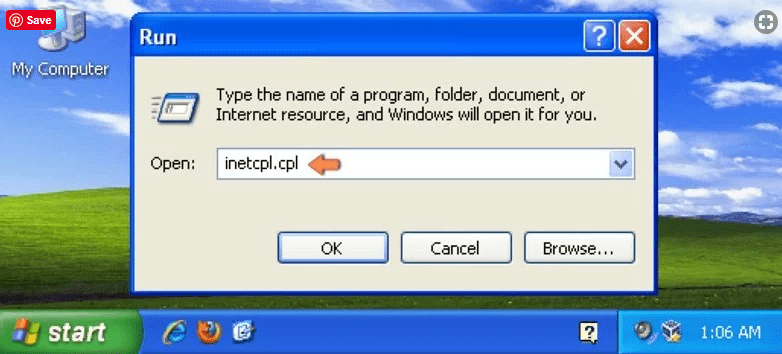
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
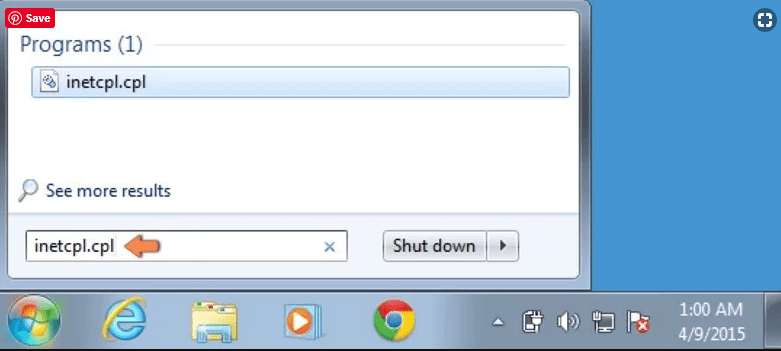
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
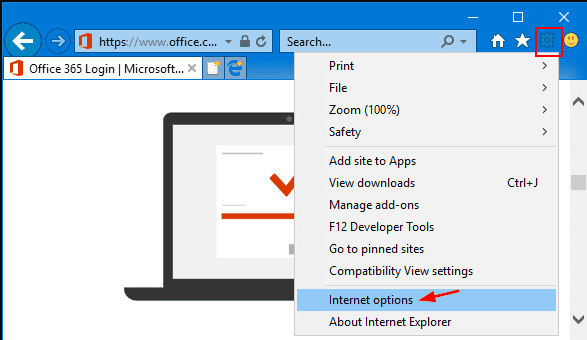
Select the “Advanced” tab in the newly opened window
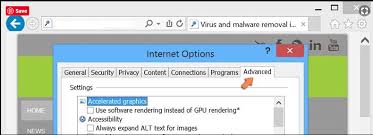
Press on “Reset” option
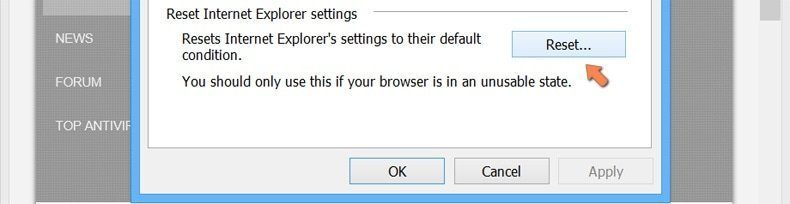
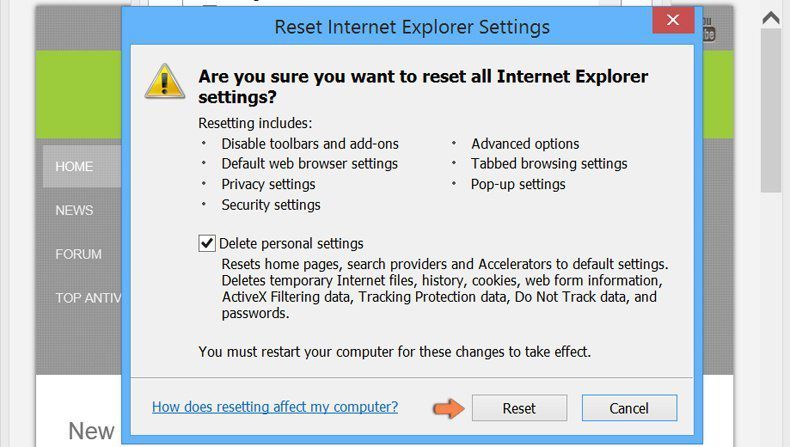
You have to press on the “Reset” button again to confirm that you really want to reset the IE
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
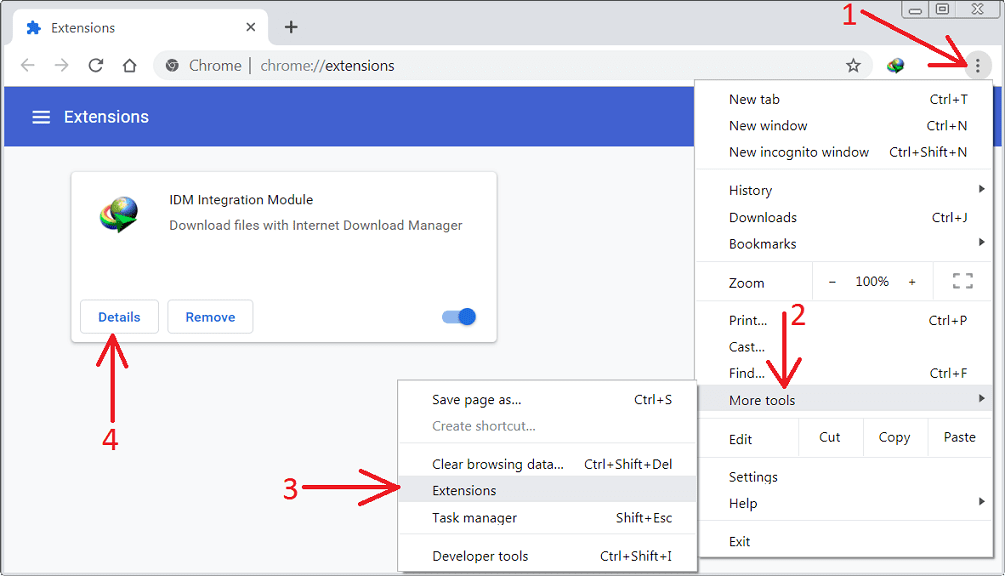
Optional Method
If the problems related to browser-hijacker still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
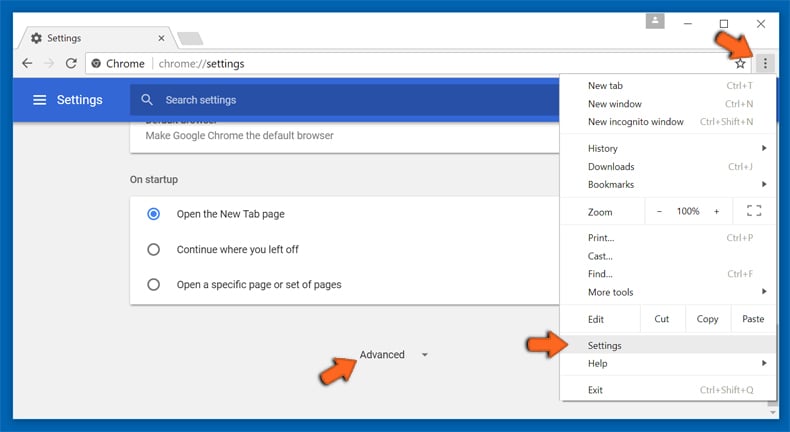
At the bottom, notice the “Reset” option and click on it.
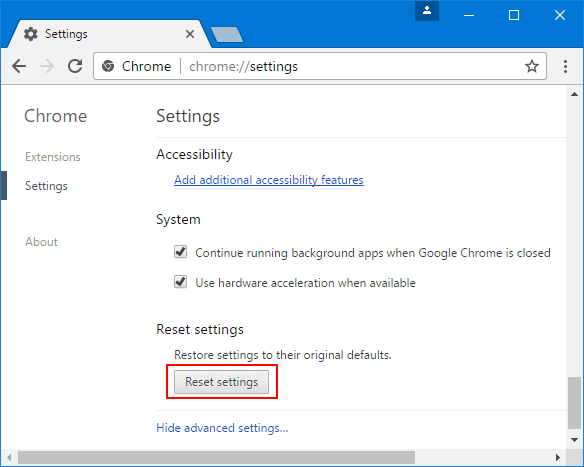
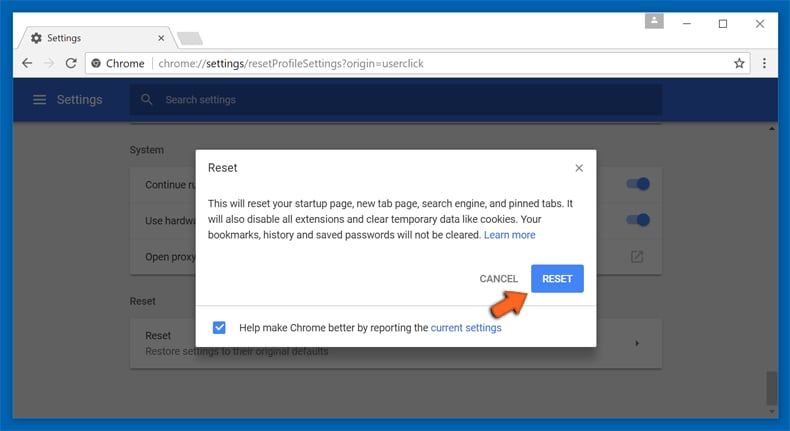
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove browser-hijacker plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
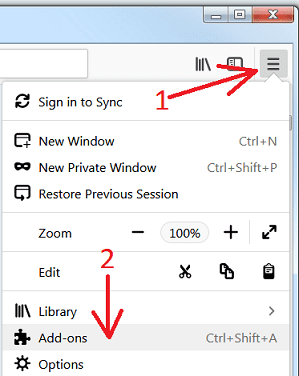
Optional Method
If you face problems in browser-hijacker removal then you have the option to rese the settings of Mozilla Firefox.
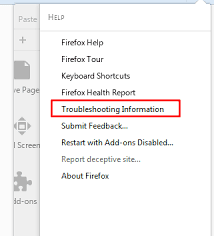
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
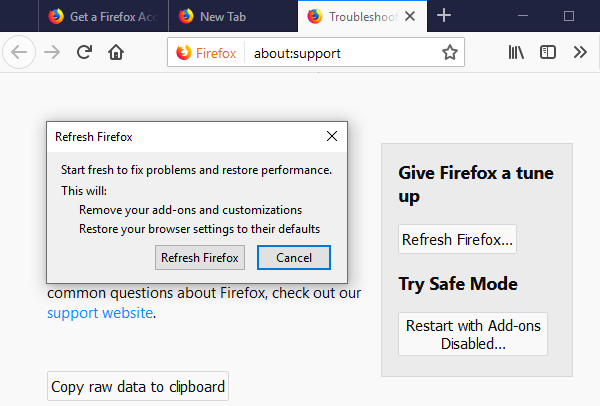
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
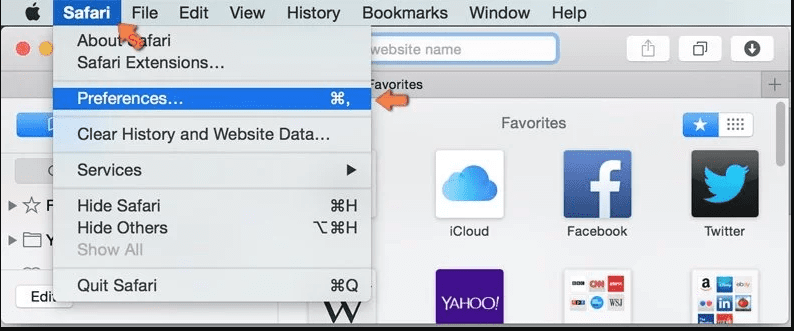
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
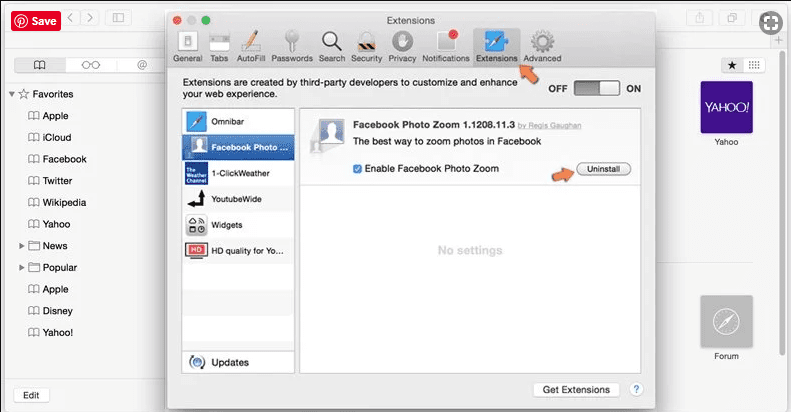
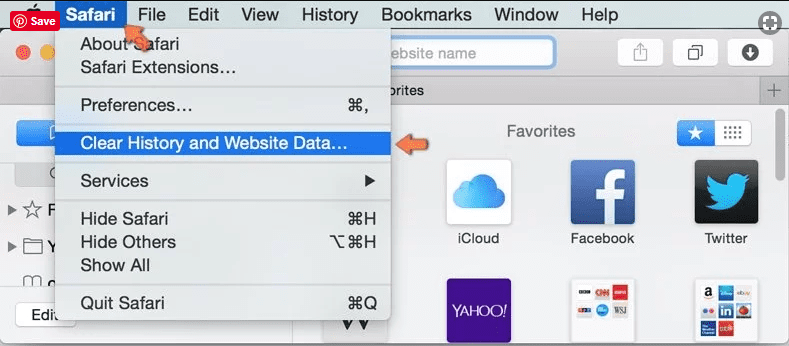
Optional Method
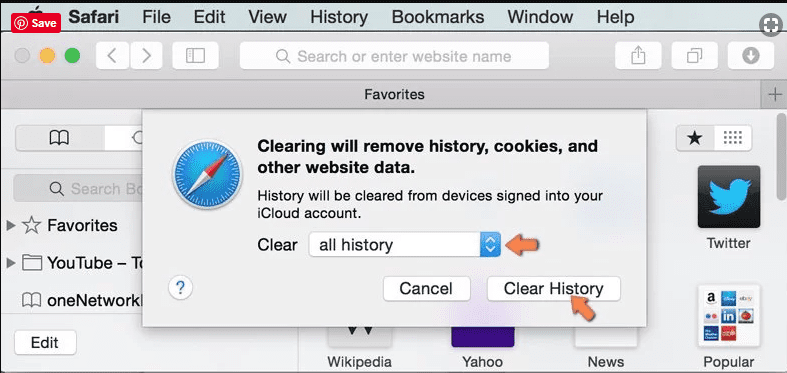
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
In the newly opened window, select “All History” and then press on “Clear History” option.
Delete browser-hijacker (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
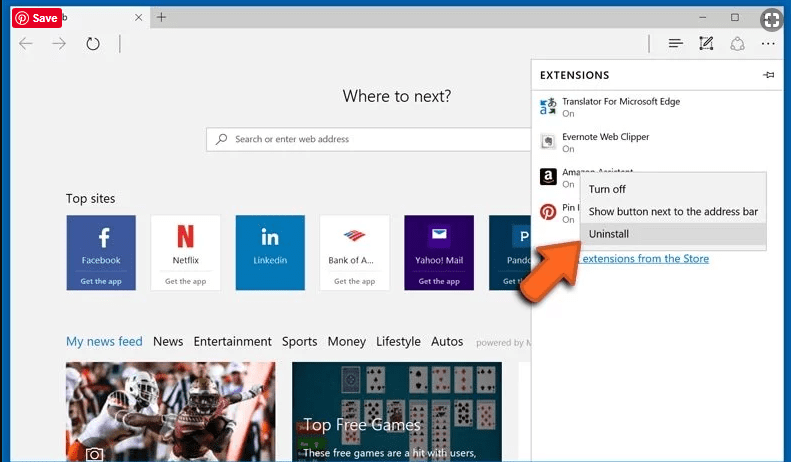
Optional Method
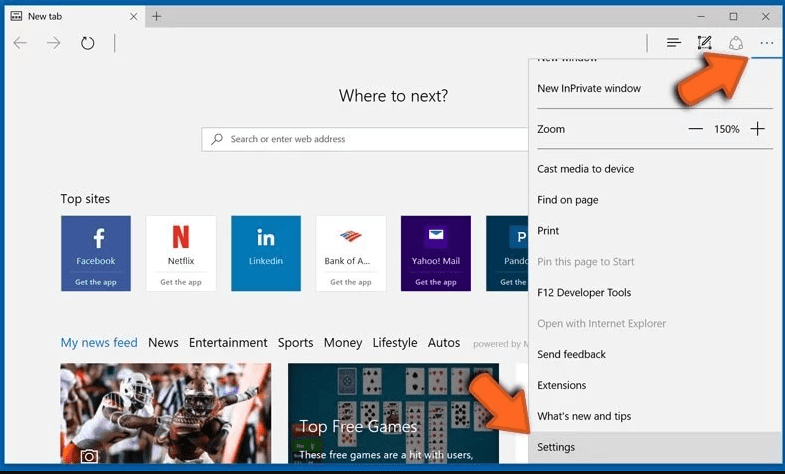
Open the browser (Microsoft Edge) and select “Settings”
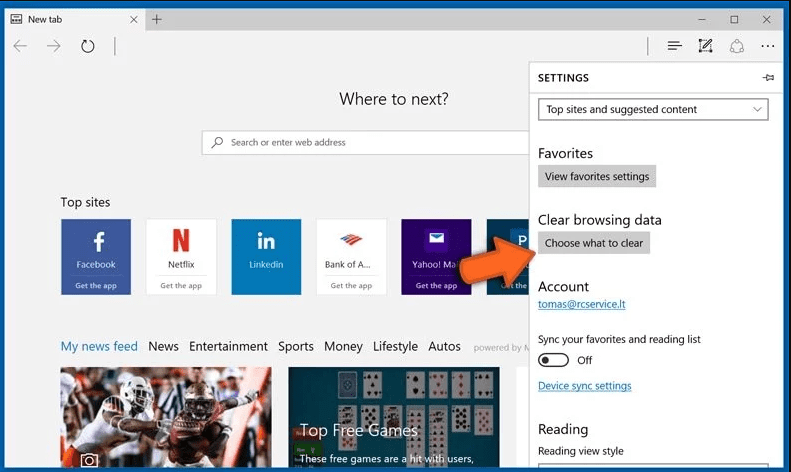
Next steps is to click on “Choose what to clear” button
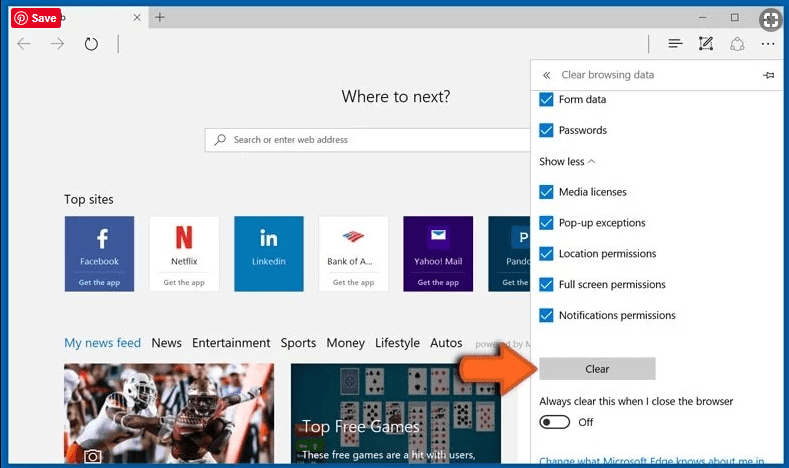
Click on “show more” and then select everything and then press on “Clear” button.
Recommended online habits you should acquire?
As soon as browser-hijacker infiltrates the PC system, it starts carrying out malicious activities in the background and may lead to a number of unpleasant issues. To avoid getting infected with such browser-based pests, below are some steps you can take:
- Download software from reputable sources: Only download software from reputable websites, such as the official page of the software vendor or well-known download portals. Avoid downloading software from third-party websites or peer-to-peer networks, as these are often sources of bundled adware.
- Pay attention during the installation process: When installing software, pay attention to each step of the installation process. Look for the checkboxes that may indicate the installation of additional software, such as adware or browser extensions. Uncheck these boxes if you don’t want to install the additional software.
- Choose custom installation: During the installation process, choose the custom installation option instead of the default or express installation. This will allow you to select which components to install and to opt-out of installing any bundled adware or other unwanted software.
- Read the End User License Agreement (EULA): Read the EULA carefully before installing any software. Look for clauses that may allow the installation of additional software or adware like browser-hijacker. If EULA contains such clauses, reconsider installing the software.
- Use a reputable web browser: Choose a reputable web browser, such as Google Chrome or Mozilla Firefox, and keep it up-to-date with the latest security patches.
- Install ad-blockers and pop-up blockers: You should use ad-blockers and pop-up blockers to prevent unwanted ads and pop-ups from appearing on your computer screen. Some web browsers have built-in ad-blocker and pop-up blockers, or you can install browser extensions that provide this functionality.
- Be careful when clicking on links: Don’t click on links in emails or on websites unless you are sure they are legitimate. Check the URL and ensure it is spelled correctly and is the correct website. Be wary of shortened URLs or URLs that lead to suspicious or unknown websites.
- Keep your web browser and operating system up-to-date: Regularly install software updates and security patches for your web browser and operating system. This will help to close any security vulnerabilities that adware, hijacker and other malware may exploit.
- Use a reputable antivirus program: A good antivirus program can detect and block infections like browser-hijacker and other malware before they can infect your computer. Make sure you choose a reliable antivirus suite and keep it up-to-date with the latest virus definitions.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your PC system safe and secure.
Conclusion:
To sum up, browser-hijacker can cause significant problems for computer users, including unwanted browser redirects, changes to homepage and search engine settings, and even the installation of additional malware. These infections typically result from downloading and installing software from untrusted sources or clicking on suspicious links. To prevent browser hijackers or adware, it is important to be cautious when downloading and installing software, use reputable antivirus tool, and keep browsers and operating systems updated with the latest security patches.
Related FAQs about browser-hijacker
What are the Symptoms of Browser-hijacker ?
The common symptoms of browser-hijacker infection include changes to the default homepage and search engine, unwanted toolbars and extensions, pop-up ads, and redirects to unfamiliar websites. Additionally, the browser may slow down or crash frequently, and search results may be manipulated or irrelevant to the query.
What Should I do if my PC gets infected with virus like browser-hijacker?
If your computer is infected with this browser-based threat, you should immediately run a virus scan using reputable antivirus software. If the software detects the malware, you should follow the removal instructions provided by it to eliminate the infection and restore your browser settings to default.
How can I protect my password and other personal credentials from browser-hijacker?
To protect your password and other sensitive information from browser-hijacker, you should employ reputable antivirus suite, enable two-factor authentication on all accounts, and use strong and unique passwords for each account. Also, you should avoid clicking on suspicious links or downloading software from untrusted sources.
Why I should trust your research conducted on browser-hijacker?
It’s important to mention that our research is conducted independently and with the assistance of unbiased security experts, who provide us with daily updates on the latest definitions and threats related to malware, adware, and browser hijackers. Moreover, our study on the browser-hijacker threat is supported by VirusTotal.
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.




