Beware: Uncovering the Deceptive Jeoosake.shop Scam
Jeoosake.shop is a deceitful online shopping site that pretends to offer products at incredibly low prices. Despite appearing like a great deal, it’s a scam designed to trick unsuspecting shoppers. The website showcases various items at unbelievably low costs, attracting people seeking budget-friendly deals.
Once customers place orders and make payments, Jeoosake.shop often fails to deliver the promised products. In some cases, the site may send inferior or counterfeit items that don’t match the original product’s description. The low prices act as bait to lure in customers, but in reality, it’s a ploy to collect money without providing the advertised goods.
It’s essential to be cautious when encountering online shopping deals that seem too good to be true, as they may lead to disappointment and financial loss. Before making any purchases from a new or unfamiliar website, it’s wise to research its reputation, read reviews, and verify its legitimacy. Falling for the trap of fake online shopping sites like Jeoosake.shop can result in frustration and financial setbacks, so it’s crucial to exercise caution and prioritize reputable platforms for online purchases.
How does Jeoosake.shop fraudulent online shopping site carry out its deceptive activities?
Jeoosake.shop scam typically works by deceiving unsuspecting users into making purchases for products that either do not exist or are of poor quality. Here’s a breakdown of the common steps involved in such scams:
- Attractive Offers: Scammers create fake online shopping website like Jeoosake.shop mimicking legitimate one. They often lure users with unbelievable discounts and deals on popular products, creating a sense of urgency to encourage quick purchases.
- Professional Appearance: These fraudulent websites are designed to look professional and convincing, with appealing layouts, product images, and descriptions. The scammers may also use stolen logos or design elements to make the site seem more legitimate.
- Low Prices as Bait: The primary tactic is to offer products at exceptionally low prices. This serves as bait to attract potential customers who are looking for bargains or discounts on various items, from electronics to clothing.
- Payment Methods: The scam sites typically accept payments through credit cards, debit cards, or other online payment methods. Once users provide their payment information, scammers can misuse it for unauthorized transactions or identity theft.
- Fake Reviews and Testimonials: To further deceive users, fake online shopping sites often display fabricated positive reviews and testimonials. These testimonials may feature fake customers praising the quality and reliability of the products, adding a layer of false credibility.
- Non-Delivery or Poor Quality Products: After users make payments, the scammers may either send substandard or counterfeit products that don’t match the description or fail to deliver anything at all. This leaves customers with a sense of betrayal and financial loss.
- Limited or No Customer Support: Fake sites like Jeoosake.shop may have non-existent or unresponsive customer support. When users attempt to contact the site for issues related to their purchases, they often receive no response, exacerbating the frustration and making it challenging to seek refunds.
What are the signs or indicators that can help identify a fake shopping site?

Understanding how to spot fake websites is essential in ensuring a safe and secure online shopping experience. Here’s a simplified guide to help you navigate the online marketplace and protect yourself from potential scams:
- Check the URL: Before making any online purchase, pay attention to the website’s URL. Ensure it begins with “HTTPS” rather than “HTTP.” The crucial “S” indicates a secure connection, encrypting communication between your browser and the website to safeguard your personal information.
- Watch for Red-Flag Words: Read product descriptions carefully, especially the fine print. Words like “vintage,” “refurbished,” or “close-out” may signal that the product is not in pristine condition. Be cautious and skeptical if the seller uses ambiguous terms that could mislead you about the product’s quality.
- Verify Contact Information: Legitimate online sellers provide clear and accessible contact information. Look for a contact page with a physical address and phone number. If this information is missing or hard to find, consider it a red flag. Having valid contact details is crucial for resolving issues or seeking assistance.
- Be Wary of Foreign IP Addresses: While not all websites with foreign IP addresses are scams, transactions originating from such addresses carry higher risks. According to a report, websites based in countries like China and Venezuela pose higher risks. Prioritize caution and consider researching or reading reviews before making purchases from sites with foreign IP addresses.
- Evaluate Reviews: Check for reviews of the website or the business owner. Be cautious if reviews seem suspicious or don’t make sense. Fake reviews may use non-standard English or generic usernames composed of random letters and numbers. A plethora of overly positive reviews can also be a warning sign, as they might be fabricated.
- Trust Your Instincts: If an offer seems too good to be true, it probably is. Exercise caution if you come across prices significantly lower than those on other reputable sites. Scammers often use unbelievably low prices to lure unsuspecting shoppers into making impulsive purchases.
- Avoid Providing Financial Information Unprompted: Legitimate companies never ask for your financial information via pop-up messages or emails while you’re browsing. If you receive such requests, do not reply or click on any links. Close the window immediately by clicking the “X” on your navigation bar.
- Scrutinize the Domain Name: Take a close look at the website’s domain name to ensure it matches your expectations. Scammers may create fake sites with names slightly altered from reputable ones. Check for signs of imitations, such as bad grammar in the website’s copy and the absence of encryption during the purchase process.
- Examine the Return Policy: A clear and reasonable return policy is indicative of a trustworthy online seller. If the return policy appears vague, convoluted, or unfavorable, consider it a warning sign. Inability to return items for a full refund may suggest an unreliable platform.
What steps should be taken if you have become a victim of a fake online store?

Discovering that you’ve fallen victim to a fake online shopping site like Jeoosake.shop can be distressing, but taking prompt and strategic actions can help mitigate the impact of the scam. Here are actionable tips on what to do after being scammed online:
Contact Your Bank or Credit Card Company Immediately:
If you notice unauthorized charges, swiftly contact your bank or credit card company. Inform them about the scam so that they can take immediate actions to protect your finances. Your bank may put a hold on your account, debit card, or checks, while credit card companies can freeze your card. Additionally, inquire about fraud protection policies that may cover certain unauthorized charges.
File a Complaint (If Purchased from a Marketplace):
If the scam occurred through a reputable online marketplace like eBay or Amazon, file a complaint with them. Most online marketplaces have mechanisms in place to investigate and address fraudulent activities. Reporting the incident allows them to take corrective actions, potentially recovering your money or ensuring the delivery of the purchased product.
Utilize Freelancing Site Protections (If Applicable):
For purchases made on freelancing sites like Fiverr, utilize the platform’s policies to protect users from fraud. Report the incident to the platform, providing details of the fraudulent transaction. These platforms often conduct investigations and may take actions against the scammer, such as account suspension or removal.
Contact Regulatory Authorities and Consumer Protection Agencies:
- FTC (Federal Trade Commission): File a complaint with the FTC, providing details of the scam.
- State Attorney General: Contact your state Attorney General using the contact information at the National Association of Attorney Generals.
- Consumer Protection Agency: Reach out to your county or state consumer protection agency. Check the blue pages of the phone book under county and state government, or visit consumeraction.gov for guidance on where to file a complaint.
- Better Business Bureau (BBB): Lodge a complaint with the BBB, detailing the fraudulent online shopping experience.
Explore Options to Get Your Money Back:
- PayPal Buyer Protection: If you used PayPal for the transaction and haven’t received the ordered product, PayPal Buyer Protection may offer coverage. However, be aware of the limits, and ensure the legitimacy of the payment form to avoid potential scams.
- Credit Card Protections: Credit cards can act as a buffer against fraudulent charges. If fraud occurs, credit card companies often have protections in place, and many cards offer purchase protection. This provides an additional layer of security between the fraudulent charge and your actual payment.
Be Vigilant and Learn from the Experience:
- Review Transactions Regularly: Keep a close eye on your bank and credit card statements for any suspicious activities. Regularly reviewing transactions helps you detect and address potential issues promptly.
- Educate Yourself on Scam Warning Signs: Familiarize yourself with common signs of online scams. This knowledge can help you make informed decisions and avoid falling victim to similar fraudulent activities in the future.
While it might be challenging to recover all your losses, taking these steps can increase the chances of minimizing the impact of the scam and prevent future incidents. Remember to stay vigilant, report scams promptly, and leverage the protective measures offered by financial institutions and online platforms to safeguard your online transactions.
Scan your device for malware: If you suspect that your device may have been infected with malware as a result of your interaction with Jeoosake.shop, it is advisable to run a thorough scan using reputable security software like SpyHunter 5. This will help detect and remove Jeoosake.shop infection or any malicious file that may have been downloaded onto your system, ensuring the safety of your device and personal data.
Download Spyhunter 5 Free Scanner
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Taking these proactive measures will help safeguard your financial data, protect your online accounts, and mitigate potential risks associated with engaging with a fraudulent website like Jeoosake.shop. Stay vigilant, prioritize your online security, and report any suspicious activities to the appropriate authorities or organizations.
What steps can I take to verify the legitimacy of an online store before making a purchase?
Before making a purchase from an online store, there are several steps you can take to verify its legitimacy. Start by conducting thorough research on the store, looking for customer reviews and feedback from reliable sources. Check if the store provides clear contact information, including a physical address and phone number, and confirm their authenticity by reaching out directly.
Examine the website’s design and content for professionalism and accuracy. Verify if the website uses a secure connection by looking for “https://” in the URL and a padlock symbol in the browser’s address bar. Additionally, search for the store’s presence on social media platforms and trust your instincts if a deal appears too good to be true. By following these steps, you can increase your confidence in the legitimacy of the online store and make more informed purchasing decisions.
What are some common tactics used by fake online stores to deceive customers with low-priced products?
Fake online stores like Jeoosake.shop employ various tactics to deceive customers with low-priced products. Some common tactics include:
- Counterfeit or inferior products: These stores may advertise popular branded products at significantly reduced prices but deliver counterfeit or substandard items that don’t meet expectations.
- Bait-and-switch: They may lure customers with enticing deals on certain products, only to switch them with different, lower-quality items upon purchase.
- Hidden fees and charges: Fake online stores may hide additional fees or charges during the checkout process, resulting in customers paying more than expected.
- Non-delivery or delayed shipping: Customers may never receive the products they ordered, or experience significant delays in shipping, leaving them frustrated and out of pocket.
- Poor customer service: Fake online stores often provide inadequate customer support, making it challenging for customers to seek assistance, request funds, or resolve issues.
- Data theft: Some fake stores may collect personal and financial information during the purchase process, leading to identity theft or fraudulent transactions.
- Fake reviews and testimonials: They may post fabricated positive reviews and testimonials to create a false sense of trust and credibility, influencing customers’ purchasing decisions.
How can I protect myself from falling victim to a fake online store and potentially losing my money?
To protect yourself from falling victim to a fake online store like Jeoosake.shop and potentially losing your money, there are several steps you can take. First, conduct thorough research on the store, checking for customer reviews and ratings from trusted sources. Verify the store’s contact information and ensure they provide secure payment options. Look for signs of professionalism in website design and content. Be cautious of deals that seem too good to be true. Use secure online connections and keep your devices and antivirus software up to date. Finally, trust your instincts and if something feels suspicious, refrain from making a purchase and explore other reputable alternatives.
How can Jeoosake.shop affect browsers?
Scam online shopping sites, such as Jeoosake.shop can affect browsers as well by spreading malware, infecting devices with viruses, and stealing personal information. Clicking on malicious links or downloading files from these sites can lead to harmful software infiltrating a user’s browser and system.
Additionally, these sites may use deceptive tactics to capture sensitive data like credit card details, login credentials, and personal information, leading to identity theft and financial loss. To detect and eliminate concealed risks, adhere to the following instructions for identifying and eradicating threats.
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
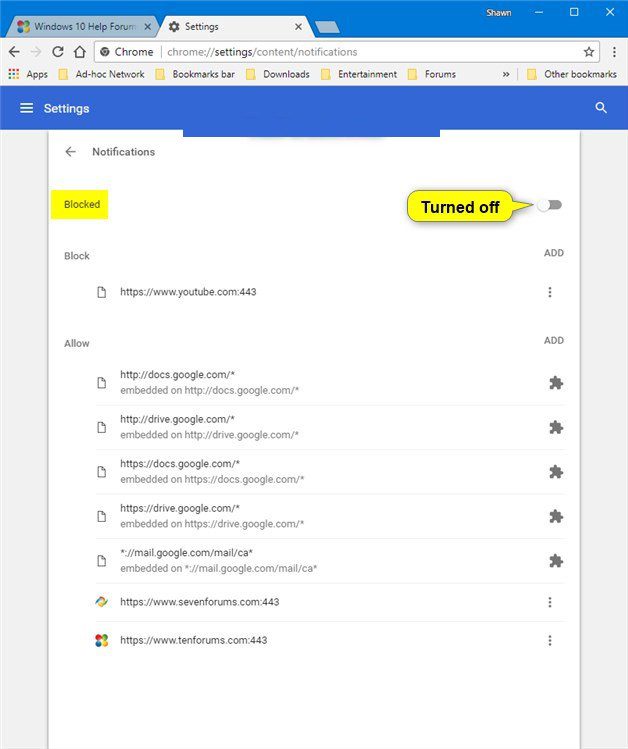
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
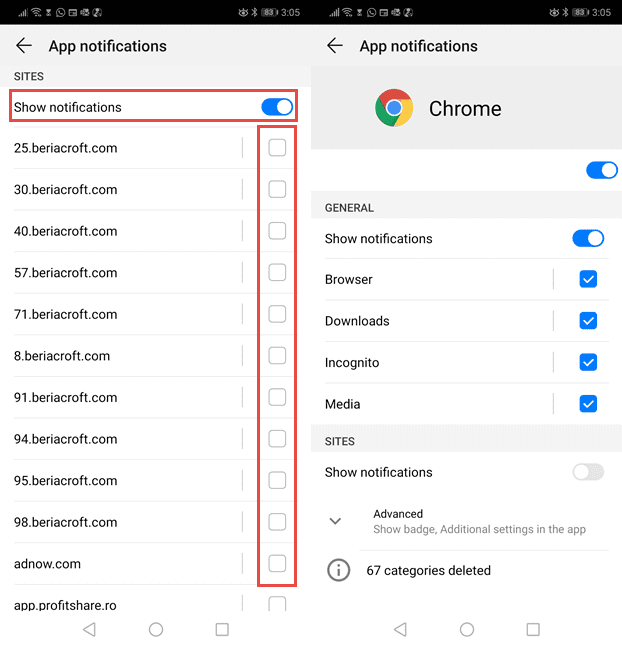
Google Chrome (Android)
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
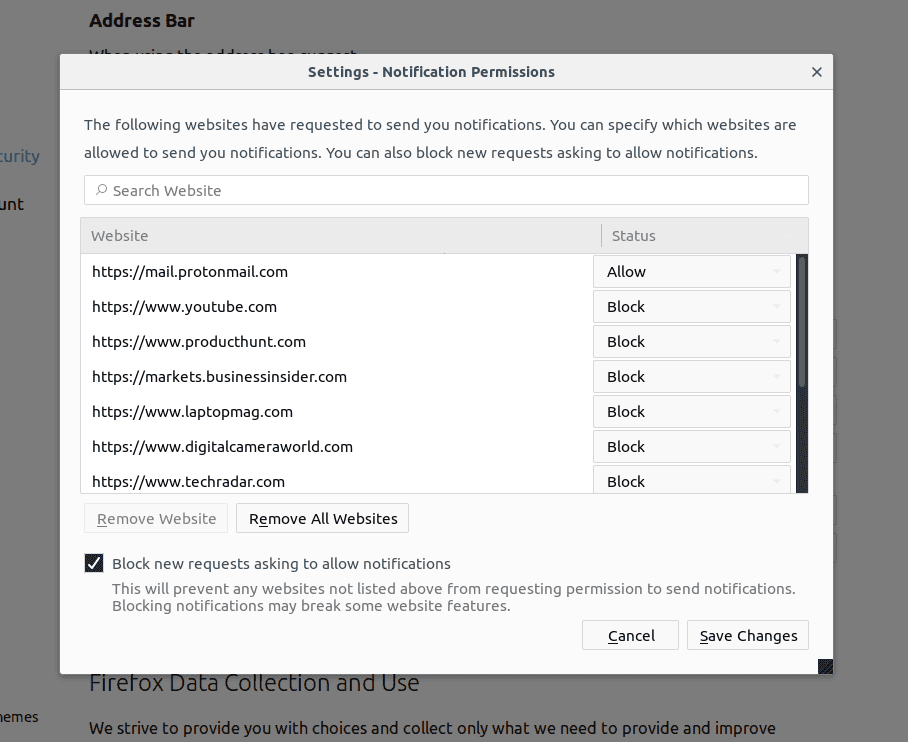
Mozilla Firefox
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
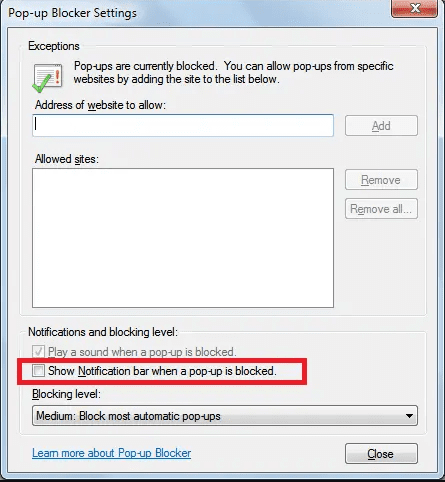
Internet Explorer
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
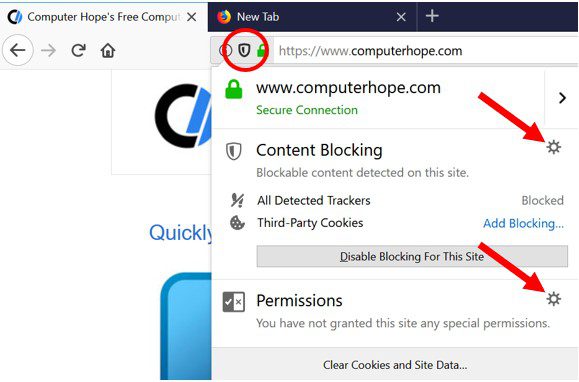
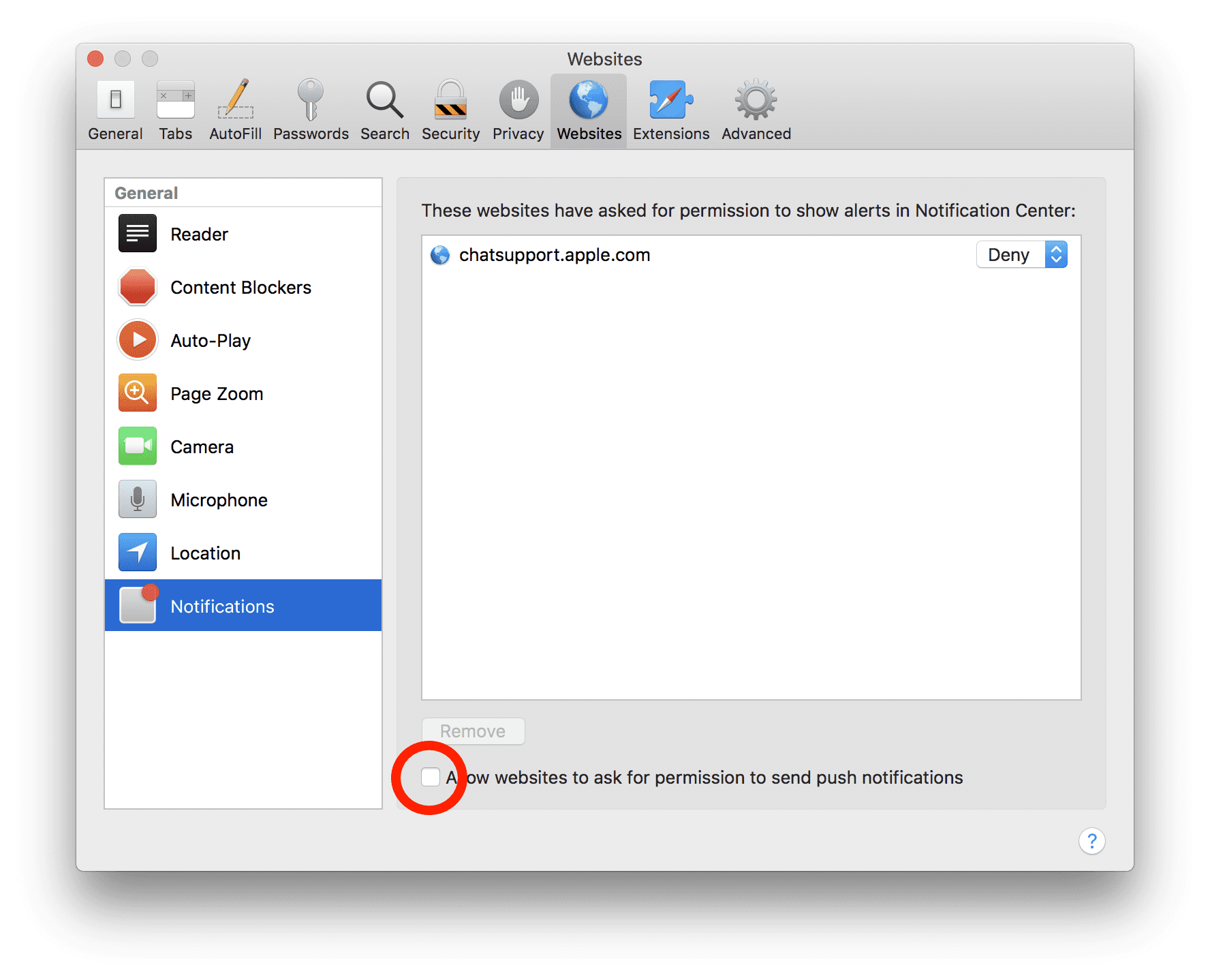
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove browser-hijacker:
Remove the related items of browser-hijacker using Control-Panel
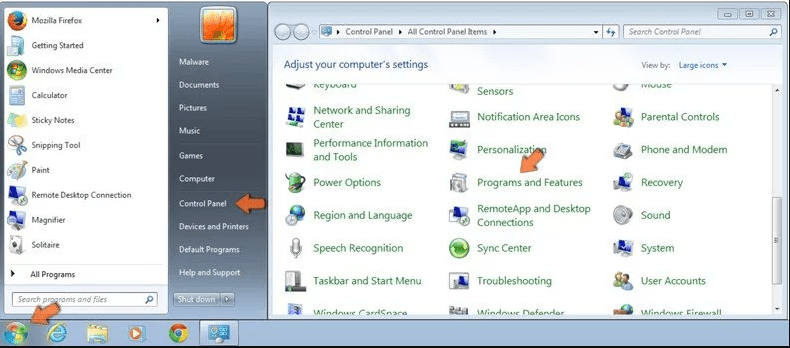
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
Windows XP Users
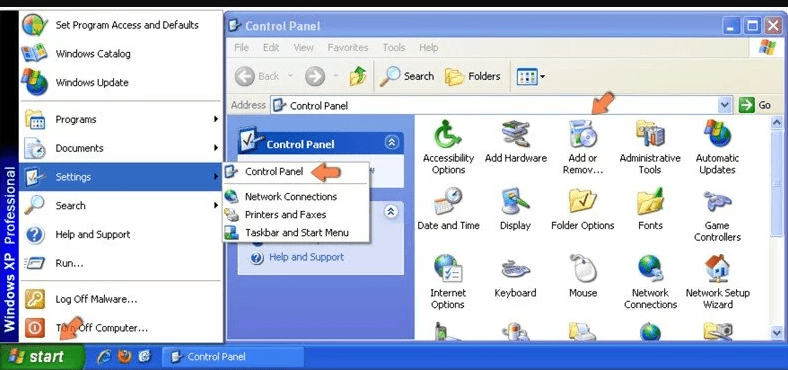
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
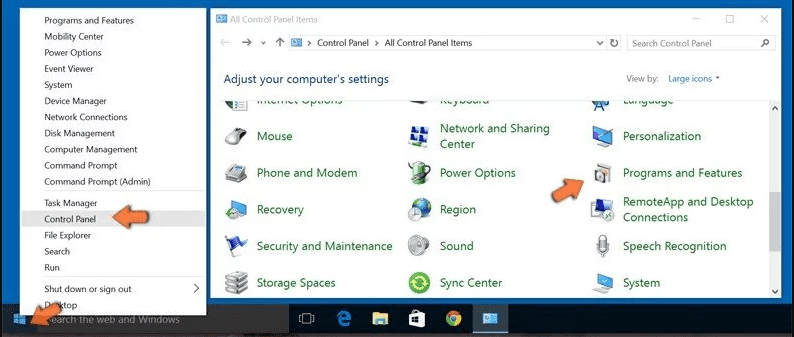
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
Mac OSX Users
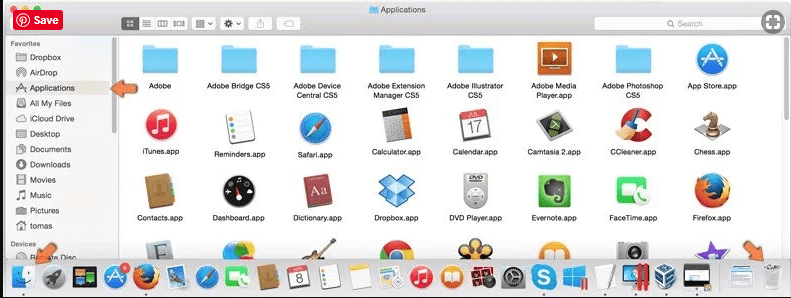
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
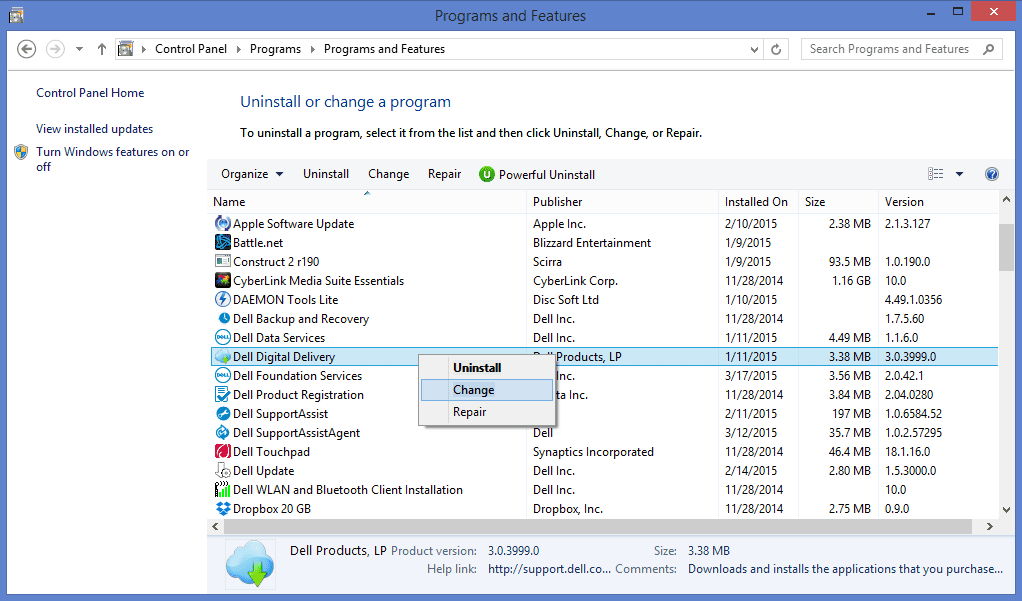
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing browser-hijacker issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (browser-hijacker) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
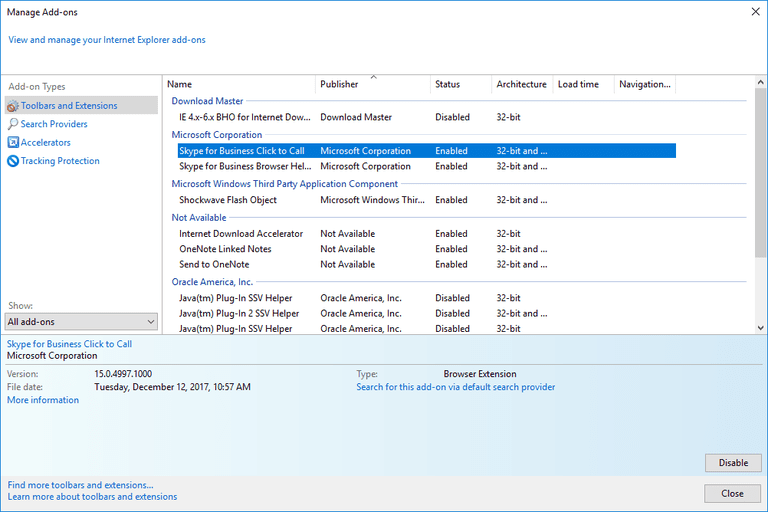
Additional Option
If you still face issues related to browser-hijacker removal, you can reset the Internet Explorer to its default setting.
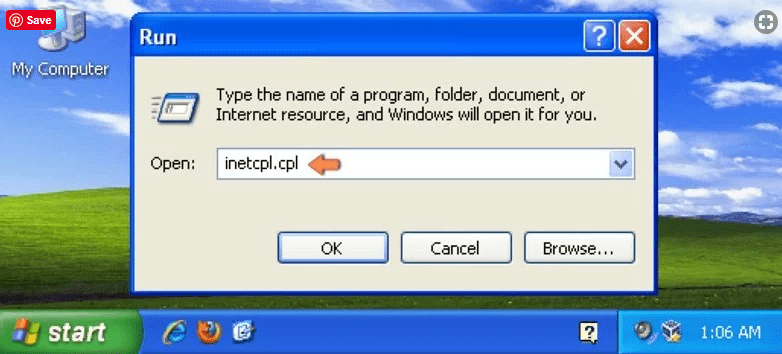
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
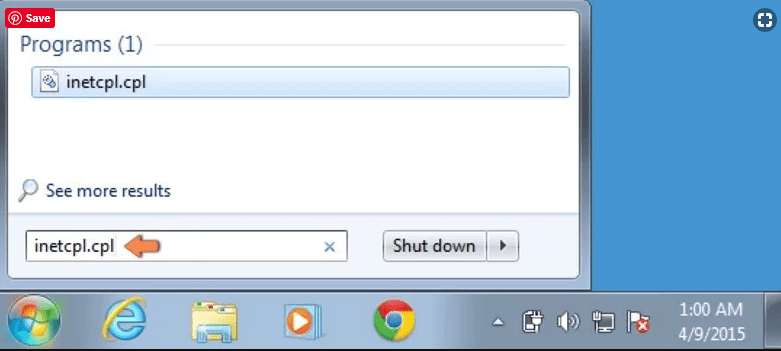
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
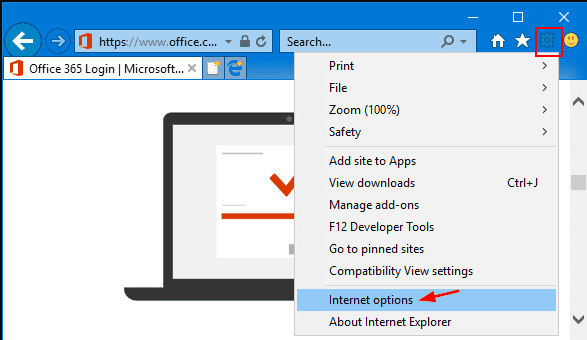
Select the “Advanced” tab in the newly opened window
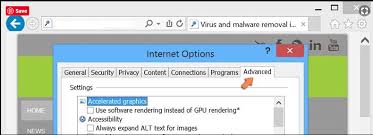
Press on “Reset” option
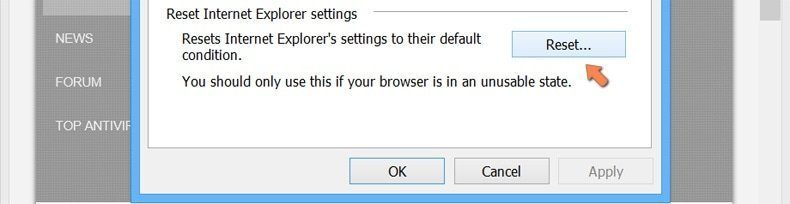
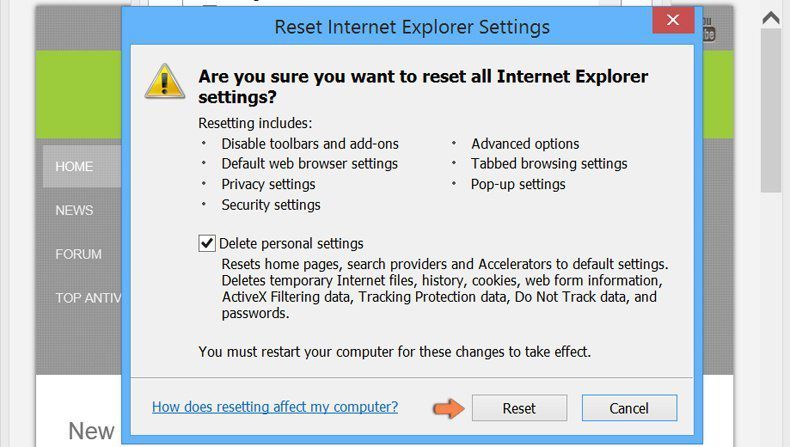
You have to press on the “Reset” button again to confirm that you really want to reset the IE
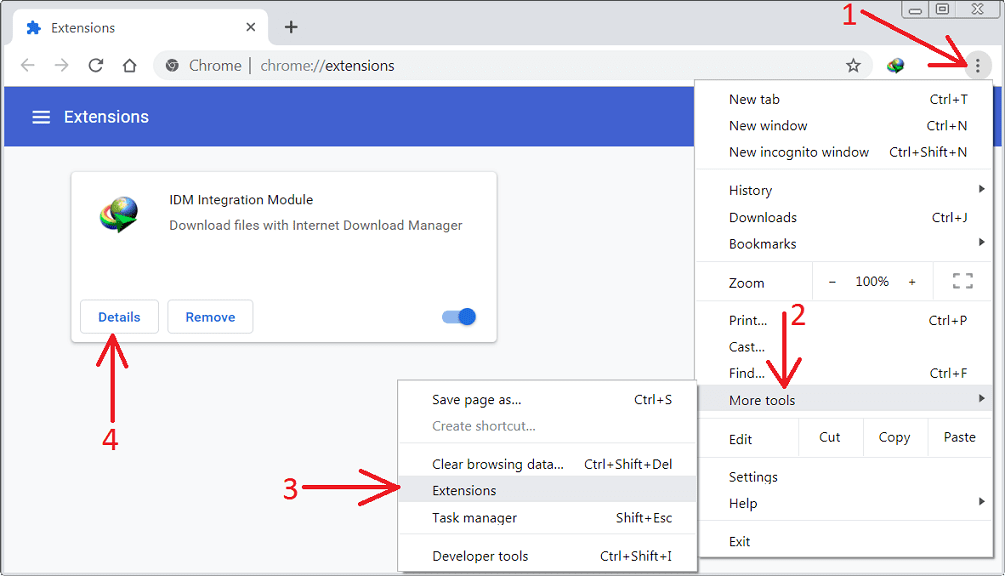
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
Optional Method
If the problems related to browser-hijacker still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
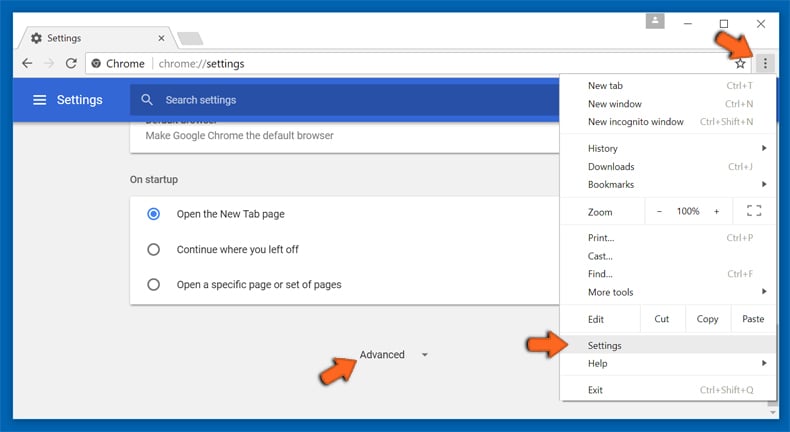
At the bottom, notice the “Reset” option and click on it.
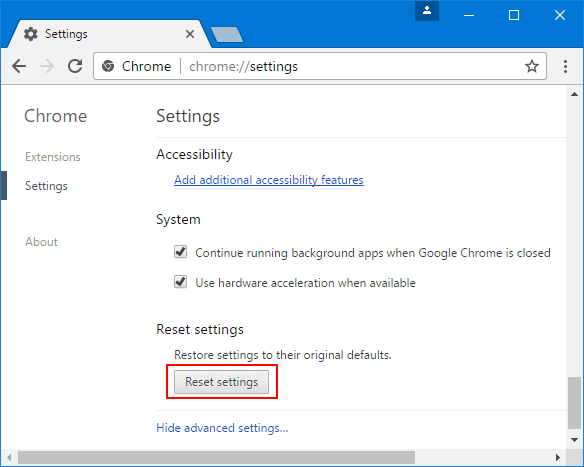
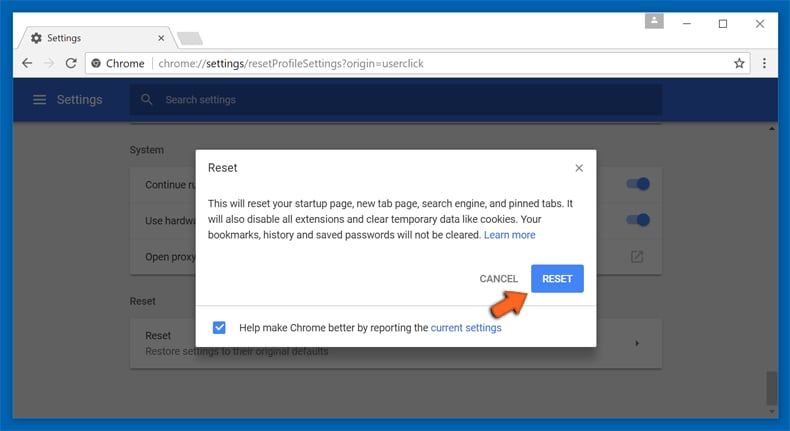
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
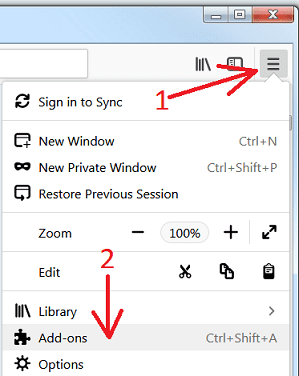
Remove browser-hijacker plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in browser-hijacker removal then you have the option to rese the settings of Mozilla Firefox.
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
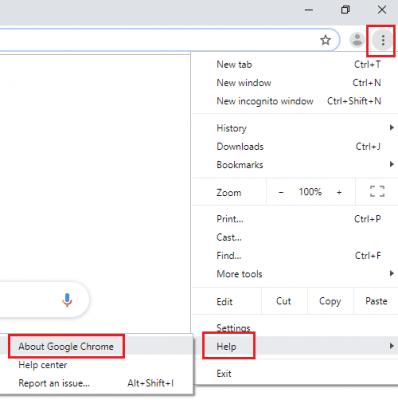
Choose “Troubleshooting Information”
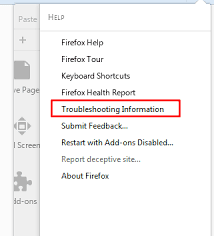
In the newly opened pop-up window, click “Refresh Firefox” button
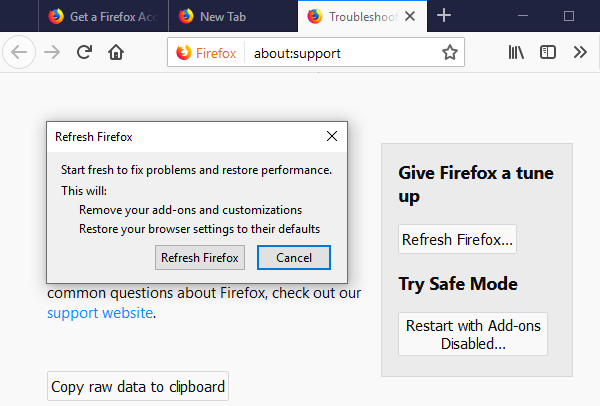
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
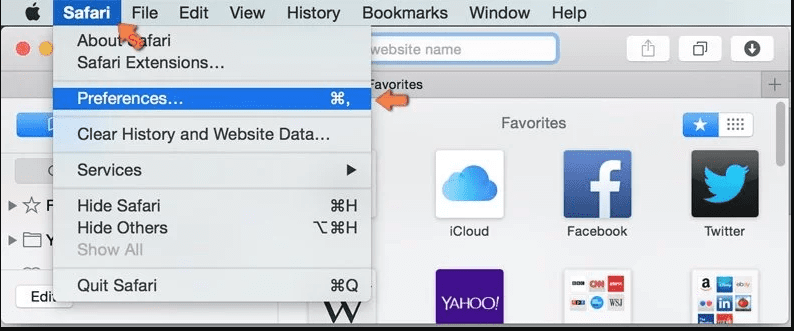
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
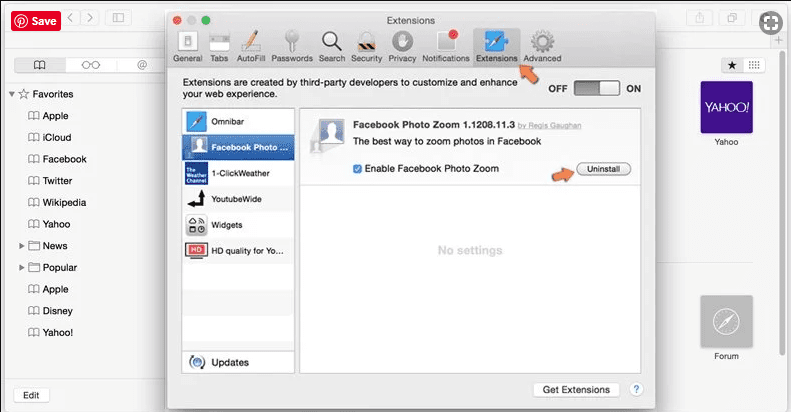
Optional Method
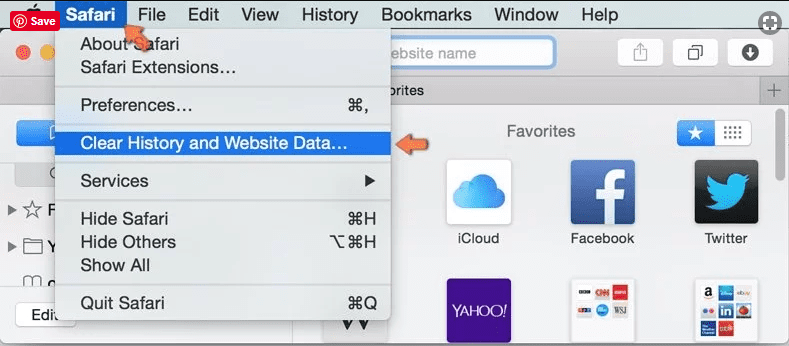
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
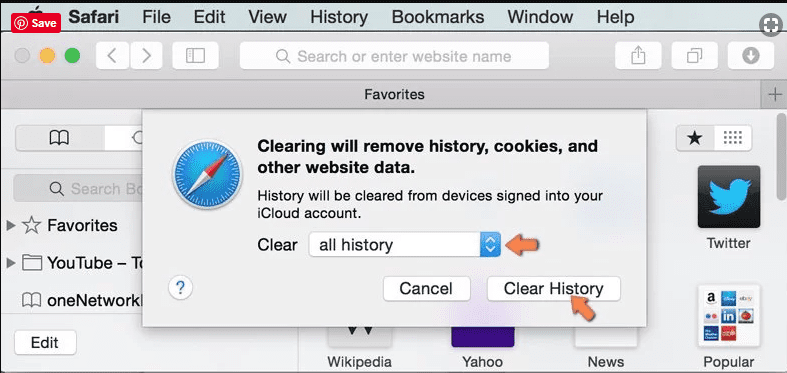
In the newly opened window, select “All History” and then press on “Clear History” option.
Delete browser-hijacker (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
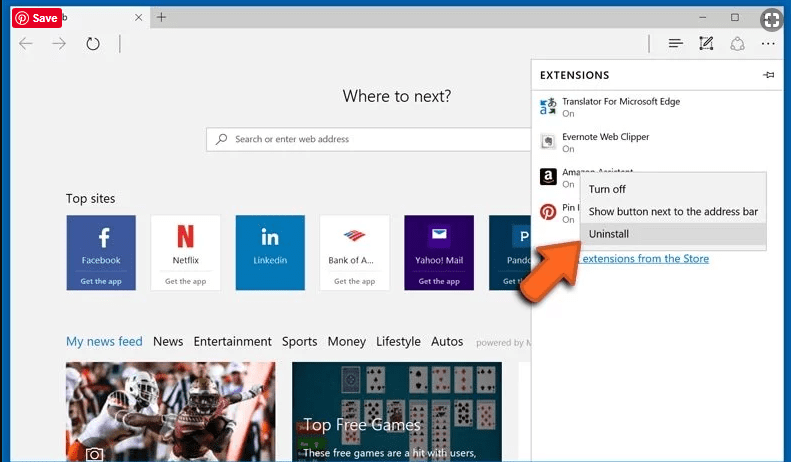
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
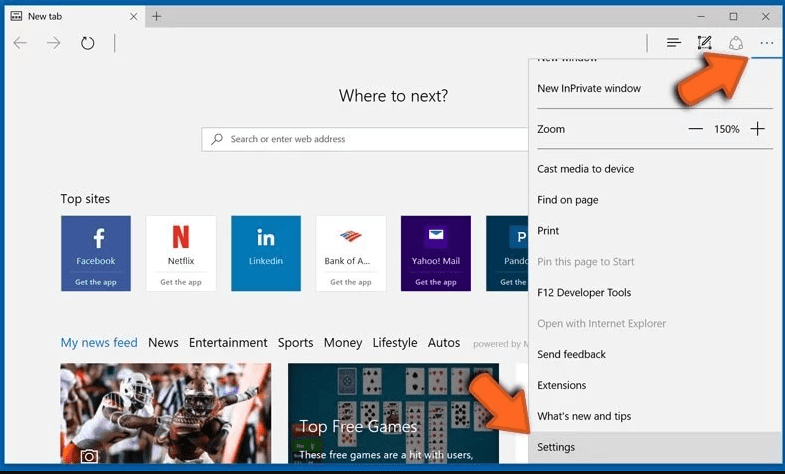
Next steps is to click on “Choose what to clear” button
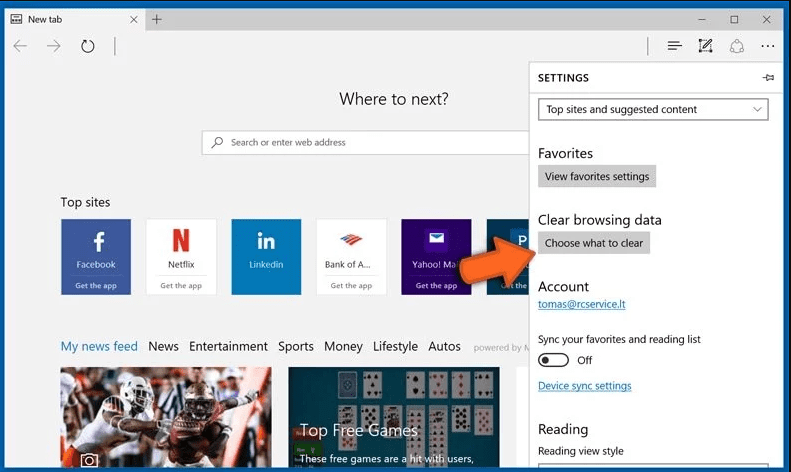
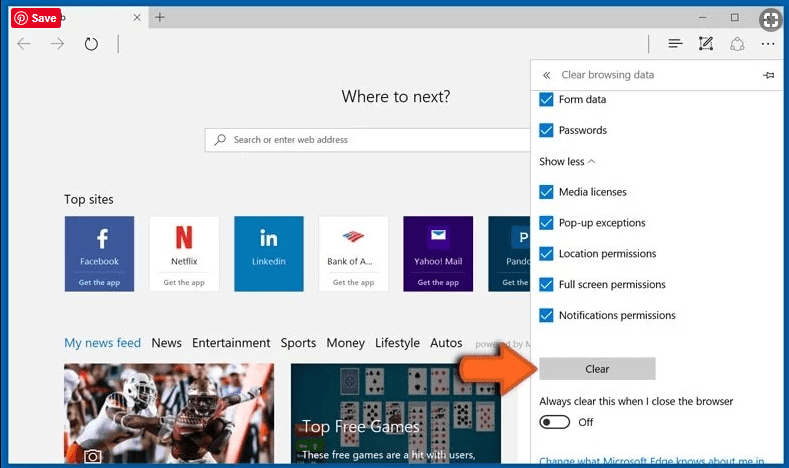
Click on “show more” and then select everything and then press on “Clear” button.
Recommended online habits you should acquire?
As soon as browser-hijacker infiltrates the PC system, it starts carrying out malicious activities in the background and may lead to a number of unpleasant issues. To avoid getting infected with such browser-based pests, below are some steps you can take:
- Download software from reputable sources: Only download software from reputable websites, such as the official page of the software vendor or well-known download portals. Avoid downloading software from third-party websites or peer-to-peer networks, as these are often sources of bundled adware.
- Pay attention during the installation process: When installing software, pay attention to each step of the installation process. Look for the checkboxes that may indicate the installation of additional software, such as adware or browser extensions. Uncheck these boxes if you don’t want to install the additional software.
- Choose custom installation: During the installation process, choose the custom installation option instead of the default or express installation. This will allow you to select which components to install and to opt-out of installing any bundled adware or other unwanted software.
- Read the End User License Agreement (EULA): Read the EULA carefully before installing any software. Look for clauses that may allow the installation of additional software or adware like browser-hijacker. If EULA contains such clauses, reconsider installing the software.
- Use a reputable web browser: Choose a reputable web browser, such as Google Chrome or Mozilla Firefox, and keep it up-to-date with the latest security patches.
- Install ad-blockers and pop-up blockers: You should use ad-blockers and pop-up blockers to prevent unwanted ads and pop-ups from appearing on your computer screen. Some web browsers have built-in ad-blocker and pop-up blockers, or you can install browser extensions that provide this functionality.
- Be careful when clicking on links: Don’t click on links in emails or on websites unless you are sure they are legitimate. Check the URL and ensure it is spelled correctly and is the correct website. Be wary of shortened URLs or URLs that lead to suspicious or unknown websites.
- Keep your web browser and operating system up-to-date: Regularly install software updates and security patches for your web browser and operating system. This will help to close any security vulnerabilities that adware, hijacker and other malware may exploit.
- Use a reputable antivirus program: A good antivirus program can detect and block infections like browser-hijacker and other malware before they can infect your computer. Make sure you choose a reliable antivirus suite and keep it up-to-date with the latest virus definitions.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your PC system safe and secure.
Conclusion:
To sum up, browser-hijacker can cause significant problems for computer users, including unwanted browser redirects, changes to homepage and search engine settings, and even the installation of additional malware. These infections typically result from downloading and installing software from untrusted sources or clicking on suspicious links. To prevent browser hijackers or adware, it is important to be cautious when downloading and installing software, use reputable antivirus tool, and keep browsers and operating systems updated with the latest security patches.
Related FAQs about browser-hijacker
What are the Symptoms of Browser-hijacker ?
The common symptoms of browser-hijacker infection include changes to the default homepage and search engine, unwanted toolbars and extensions, pop-up ads, and redirects to unfamiliar websites. Additionally, the browser may slow down or crash frequently, and search results may be manipulated or irrelevant to the query.
What Should I do if my PC gets infected with virus like browser-hijacker?
If your computer is infected with this browser-based threat, you should immediately run a virus scan using reputable antivirus software. If the software detects the malware, you should follow the removal instructions provided by it to eliminate the infection and restore your browser settings to default.
How can I protect my password and other personal credentials from browser-hijacker?
To protect your password and other sensitive information from browser-hijacker, you should employ reputable antivirus suite, enable two-factor authentication on all accounts, and use strong and unique passwords for each account. Also, you should avoid clicking on suspicious links or downloading software from untrusted sources.
Why I should trust your research conducted on browser-hijacker?
It’s important to mention that our research is conducted independently and with the assistance of unbiased security experts, who provide us with daily updates on the latest definitions and threats related to malware, adware, and browser hijackers. Moreover, our study on the browser-hijacker threat is supported by VirusTotal.
Special Offer (For Windows)
Browser-hijacker can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and browser-hijacker has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.





