Alert: Melutix.com Exposed – Avoid Bitcoin Promo Code Scam!
Melutix.com Bitcoin Promo Code Scam Overview
Melutix.com is a fake cryptocurrency trading platform that tricks people through a celebrity-fronted scam on social media. Scammers use deepfake or voice-dubbed videos featuring stars like Cristiano Ronaldo, Elon Musk, Bill Gates, Mark Zuckerberg, and Drake to deceive fans into depositing Bitcoin.
The scammers promise free crypto giveaways with special promo codes, but it’s all a fraud. Melutix.com doesn’t actually exist as a legitimate trading platform; its sole purpose is to steal money from victims who are lured by fake celebrity endorsements and unrealistic bonuses. These videos, shared on platforms like YouTube, TikTok, and Facebook, present viewers with the enticing opportunity to earn free cryptocurrency by participating in what seems like a legitimate promotion.
The scam operates by luring victims into creating accounts on fraudulent cryptocurrency exchange websites. These sites, cleverly designed to mimic the branding of Ronaldo’s companies, promise substantial bonuses in Bitcoin worth around 0.31 BTC for using special promo codes like “CR7” or “TikTok11.” To claim these bonuses, users are instructed to make a small initial deposit of 0.005 BTC and complete ID verification.
However, the reality is far from what it seems. The cryptocurrency platforms promoted in these videos are entirely fake, controlled by scammers whose sole intention is to steal users’ deposits. Despite presenting convincing account dashboards and bonuses, these websites do not facilitate any actual trading or transactions. Once users make a real deposit, they lose access to their accounts, and their funds are irretrievably transferred to the scammers’ wallets.
To make matters worse, the scammers aggressively target vulnerable audiences, including tech enthusiasts, crypto traders, Tesla fans, and space exploration enthusiasts. They invest in video ads and promotion on social media platforms frequented by these groups, amplifying the reach and impact of their fraudulent scheme.
As deepfake technology continues to advance, it is essential to remain vigilant and skeptical of online promotions, especially those involving cryptocurrencies. Here are some practical steps you can take to protect yourself from falling victim to the Melutix.com.
Identifying the Melutix.com Scam
With the growing popularity of cryptocurrency and the allure of celebrities like Cristiano Ronaldo, scammers are finding new ways to exploit people’s interest and admiration. To avoid falling victim to fake giveaway ads, it’s crucial to be vigilant and look out for key signs that can help you identify deceptive promotions.
One red flag to watch out for is a mismatch between the text or voiceover narration and the actual content. Some scams use voiceover narrations about bonuses dubbed over Cristiano Ronaldo’s real interview answers on unrelated topics. If the video and text don’t align, it’s a warning sign.
Another indicator is poor deepfake quality. While some fakes may look realistic, lower quality edits may expose glitches like mismatched skin tones or blurry edges. If the video looks suspiciously edited, it’s best to be cautious.
Be wary of ads directing you to unverified crypto platforms. Before providing any personal information or making deposits, thoroughly research any exchange site mentioned. Many scammers use lookalike domains of real brands to trick unsuspecting victims.
Genuine crypto platforms never ask for deposits before allowing withdrawals. If a platform demands a deposit first, it’s a huge red flag of fraud. Additionally, be skeptical of offers that seem too good to be true, such as promises of free or bonus Bitcoin funds just for signing up. Legitimate platforms don’t give away cryptocurrency in such a manner.
Pay attention to aggressive urgency tactics. Scam promotions often insist that you must act quickly to claim bonus Bitcoin before a deadline expires. This creates pressure to skip proper vetting in the rush, leading to potential scams.
Check for other online mentions. If there’s no media coverage or chatter about Cristiano Ronaldo or any other celebrity making a particular cryptocurrency endorsement, it’s likely a fabrication by scammers. Be cautious of odd social media engagement, such as disabled comments on scam videos and the use of bot accounts or hashtags to create artificial engagement.
Lastly, genuine cryptocurrency promotions always mention the risks involved in the volatile nature of crypto markets. If there’s no mention of risks and the promotion only focuses on free money through bonuses, it’s likely a scam.
To stay safe, verify the authenticity of any viral celebrity cryptocurrency endorsement through the official site or accounts of the celebrity before interacting or providing personal information. If something seems questionable, it’s best to avoid it altogether.
Spotting Scam Websites: Quick Tips
- New Website Domain: Be wary if the website’s domain is recently registered. Scammers often set up shop quickly.
- Picture Perfect Deception: If the product images seem too good to be true, they probably are. Scam sites often swipe photos from elsewhere.
- Lonely Website: If the site doesn’t get many visitors, it’s a red flag. Legit sites usually attract more attention.
- Crazy Discounts: Unrealistically low prices should raise alarms. Scammers use huge discounts to lure you in.
- Social Media Ghosts: If the site is nearly invisible on social media, be cautious. Legitimate businesses usually engage with customers online.
- Silent Customers: Lack of genuine customer feedback is suspicious. Real reviews help build trust; scammers avoid them.
Red Flags of Melutix.com Scam
Melutix.com is waving some serious red flags that scream “scam alert”:
- Spelling and Grammar Mishaps: If you spot lots of spelling and grammar errors on the website, it’s a big hint that the folks behind it might not be professionals.
- Missing Company Details: The absence of any company info, address, contact details, or business registration is a glaring red flag. Legitimate businesses are transparent about who they are.
- No Proof of Payouts: If there’s no evidence that anyone has actually been paid as promised, it’s a clear sign that those big earnings might just be a fairy tale.
- Too-Good-To-Be-True Claims: If the promises sound unrealistically amazing – like earning big bucks for simple tasks – it’s probably a trap. If it seems too good to be true, it usually is.
- Sketchy Redirects: If clicking on links takes you to sketchy, unsecure third-party sites, it’s a major sign of phishing and scamming. Legit sites won’t play these redirection games.
- Requests for Personal/Financial Info: Be wary if the site asks for sensitive data like social security numbers or bank account info. Legitimate platforms don’t need such confidential details.
- High-Pressure Tactics: If the site creates false urgency, claiming you must act immediately to avoid missing out, it’s likely a tactic to pressure you into a scam.
- Only Positive Reviews: If all the reviews seem overly positive and lack any criticism, it’s a warning sign. Legitimate platforms have a mix of feedback, good and bad.
Remember, trust your instincts. If something feels off, it probably is. Steer clear of sites that dangle quick cash as bait to grab your personal info – it’s a classic scam tactic.
Avoiding Melutix.com
Stay one step ahead and avoid falling into the Melutix.com trap with these simple tips:
- Stick to Reputable Platforms: Don’t venture into unfamiliar websites promising easy money. Stick to well-known and reputable platforms.
- Research Before Sharing: Before giving away personal info, research the website thoroughly. Look for reviews and complaints to ensure it’s legit.
- No Upfront Payments: Never pay money upfront for promised rewards. Legitimate opportunities won’t ask for payment in advance.
- Beware External Links: Avoid following links to external domains. Stay on the main site you’ve researched to steer clear of phishing traps.
- Spot Errors: Watch out for poor grammar and spelling. Amateurish mistakes can be a sign of scam artists at work.
- Verify Business Addresses: Use Google Maps to verify business addresses. Scams often use fake locations to deceive victims.
- Guard Sensitive Information: Only share sensitive info like SSNs or bank details when absolutely necessary. Legitimate sites won’t ask for these unless essential.
- Prepaid Cards for Online Shopping: Use prepaid cards when shopping online to limit exposure of your real payment cards.
- Ignore False Urgency: Don’t be rushed into decisions with claims of missing out. Scammers use false urgency to pressure victims.
Stay vigilant, take your time, and thoroughly vet any website before sharing personal or payment info. Your best defense is your own caution – protect yourself from these digital wolves in sheep’s clothing!
Things to do if fallen victim to the Melutix.com:
If you have been deceived by the Melutix.com, it is crucial to promptly safeguard yourself and your finances. Follow these steps to mitigate the impact of the scam and protect your assets:
- Notify the Federal Trade Commission (FTC) about the scam by visiting their website at https://reportfraud.ftc.gov/. Additionally, consider lodging a complaint with your state attorney general’s office or local consumer protection agency to ensure appropriate action is taken against the scammers.
- File a report about the scam with the Internet Crime Complaint Center (IC3) through their website at https://www.ic3.gov/. The IC3 is a collaborative effort between the FBI and the National White Collar Crime Center, dedicated to collecting and assessing complaints related to online fraud.
- Submit a report to Facebook, Instagram, or TikTok and mark the ads as misleading or deceptive.
- Reach out to your bank or credit card company without delay and inform them about the fraudulent transaction. Request the cancellation of your card and the issuance of a new one. Explore the possibility of disputing the charge to secure a potential refund.
- Immediately update your passwords and PINs for all your online accounts, particularly if you have used the same credentials on the fraudulent website. This ensures added security and minimizes the risk of unauthorized access.
- Regularly keep an eye on your credit reports and bank statements to detect any signs of suspicious transactions or unauthorized charges.
- If you have concerns about malware infecting your device, conduct a scan using the SpyHunter Anti-Malware software for potential threats.
Threat Summary |
| Name: Melutix.com |
| Category: Scam |
| Features: Aims to deceive users into providing their personal and sensitive information like credit card details, address, phone number, and social security number. |
| Danger Level: Medium |
| Damage: Victims may have severe consequences, such as identity theft, fraud, and other malicious activities. |
|
Symptoms: The unwanted application can cause several adverse effects, such as displaying intrusive pop-up ads and slowing down internet browsing. The threat can manipulate the settings of an internet browser. This manipulation forces users to visit the hijacker’s website and conduct internet searches using their search engine. |
|
Distribution: Browser hijackers or adware such as Melutix.com can spread through deceptive pop-up ads, free software installers that are bundled with malware, and fake Flash Player installers. |
|
Removal: To remove the threat, scan your system with powerful SpyHunter anti-malware software |
What is the purpose of Melutix.com?

The purpose of adware or browser hijacker is to generate revenue through targeted advertising. It collects user data, such as browsing habits and preferences, to deliver personalized ads. By bombarding users with ads, the unwanted program aims to increase the chances of users clicking on them, leading to potential revenue for its developers.
While adware is primarily an annoyance and can compromise user privacy, it is often a means for companies to monetize free software and services without directly charging users. The primary objective of a browser hijacker is to promote certain websites, generate traffic, and potentially earn revenue through advertising or other means by exploiting the user’s browsing experience without their consent.
How does PUP end up on users’ devices?
Devices can fall victim to browser hijackers or adware through the download of infected files, malevolent email attachments, or visits to compromised websites. These hijacking tools may be bundled within browser extensions or included as part of software packages. Additionally, browser based threats can stem from shareware, freeware, or spyware infections, further expanding their potential sources of origin.
Potentially unwanted programs like Melutix.com often find their way onto users’ devices unintentionally, as users can be deceived into unknowingly downloading them. This can occur when users agree to an extra download mentioned in the terms and conditions of software installation. Another tactic involves misleading users with a choice to decline the installation of the browser hijacker software, but the wording deliberately confuses them, resulting in the inadvertent download. Once installed, PUP initiates its malicious actions by manipulating the user’s browser activities through embedded malevolent code.
What are the impacts of Melutix.com infection?
Browser hijacking refers to the unauthorized modification of web browser’s settings or behavior by malicious software or websites. It can have various impacts on users and their browsing experience. Here are some common impacts of browser hijacking:
- Altered homepage and search engine: Hijackers often change the default homepage and search engine settings of a browser to redirect users to a different website. This can disrupt the user’s browsing routine and make it challenging to find the desired information.
- Unwanted browser extensions: Browser hijackers or adware may install malicious or unwanted browser extensions without the user’s consent. These extensions can inject ads, track browsing activities, or collect personal information, compromising primacy and security.
- Increased exposure to ads: Hijacked browsers often display an excessive number of pop-up ads, banners ads, or in-text ads. This flood of advertisements not only annoys users but can also slow down browsing speed and consume bandwidth.
- Tracking and data collection: Browser-based infections like Melutix.com employ tracking mechanisms to monitor users’ online activities, including websites visited, search queries, and personal information entered on web forms. This information can be used for targeted advertising or sold to third-parties without the user’s consent.
What problems Melutix.com can cause?
This undesirable application can cause instability in web browsers by modifying critical settings, introducing incompatible software, or consuming system resources. Users may experience frequent crashes, slow performance, or unresponsiveness while browsing. In more severe cases, browsing hijacking can lead to unauthorized access to online accounts. PUPs may attempt to steal login credentials, financial information, or other sensitive data, putting users at risk of identity theft or fraud.
Furthermore, browser hijacking can be a part of a larger malware infection. In such cases, adware or hijacker may serve as a gateway for other malicious software, such as ransomware, keyloggers, or spyware, further compromising the user’s system and data. Also, browser-based threats with data collection abilities can cause severe problems. They can gather sensitive information such as login credentials, financial data, and personal details, leading to identity theft and fraud. The collected data may also be sold to third parties, compromising user privacy. Additionally, targeted advertising based on the collected information can result in a flood of intrusive and potentially malicious ads.
How can I know if I have an adware or browser hijacker?
If you have an adware or browser hijacker, such as Melutix.com installed on your device, you may notice a few clear indications. Users need to exercise caution if they encounter any of the following signs, as it could suggest their system is compromised.
- If users find that their default homepage or preferred search engine has been substituted without their authorization, they should be on high alert.
- If users notice that their search queries are being rerouted to unfamiliar websites, it’s important for them to be cautious and aware of this redirection behavior.
- When users are bombarded with an excessive number of intrusive pop-up ads appearing frequently, they should be cautious and wary of the abundance of unsolicited advertisements.
- If users experience delays in the loading of webpages, where the content takes an unusually long time to appear, it is important for them to remain vigilant and take note of this sluggish performance.
- Should users notice the sudden appearance of unauthorized toolbars on their internet browser, it is crucial for them to exercise caution and be mindful of these unapproved additions.
Special Offer (For Windows)
Malware/Spyware/Virus can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter 5 antimalware scanner to check if the program can help you getting rid of this virus.
Special Offer (For Macintosh) If you are a Mac user and Malware/Spyware/Virus has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
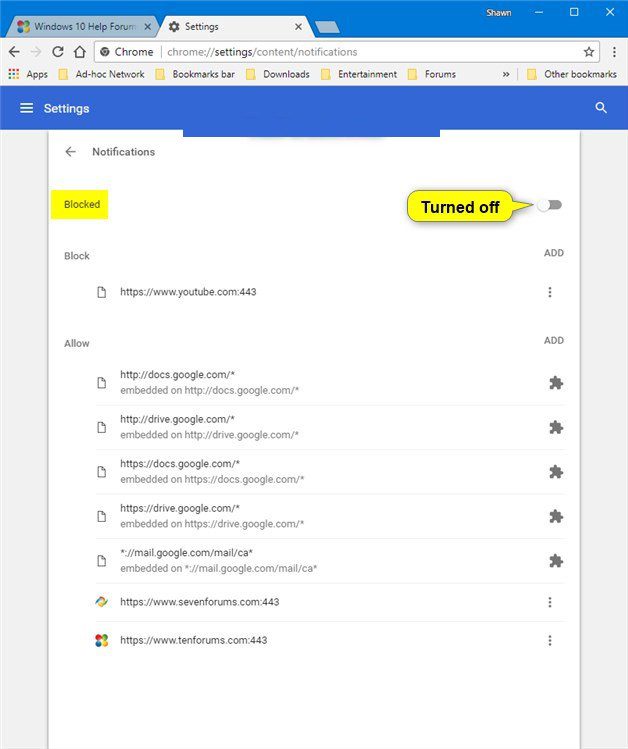
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
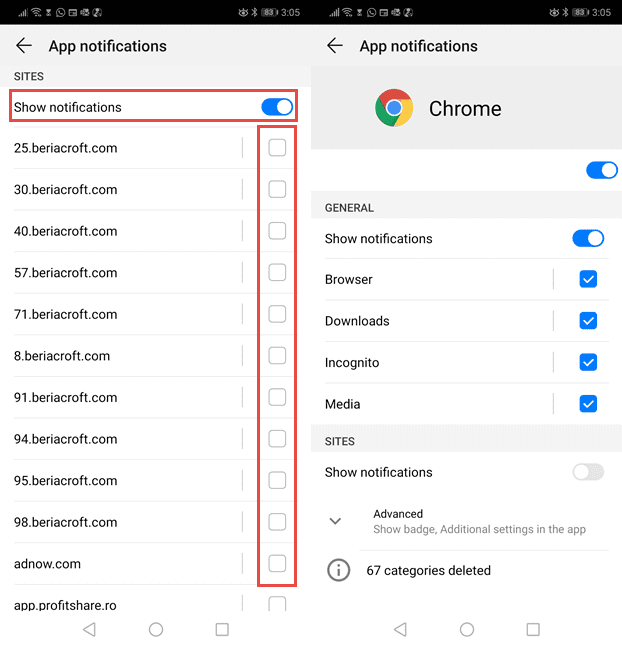
Google Chrome (Android)
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
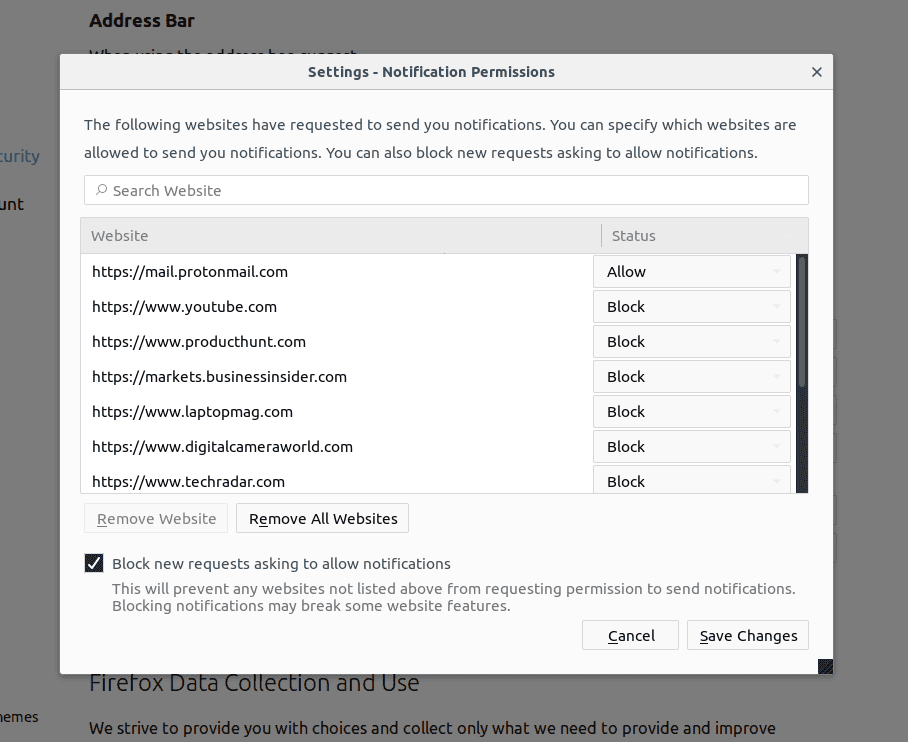
Mozilla Firefox
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
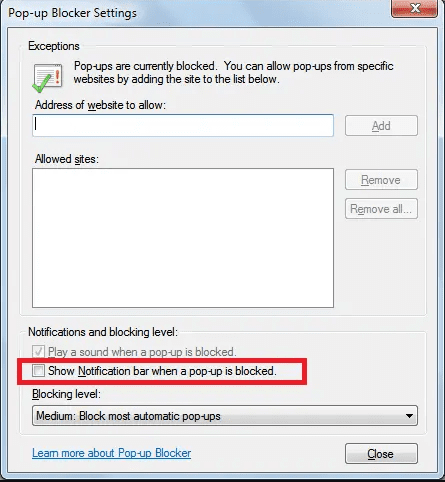
Internet Explorer
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
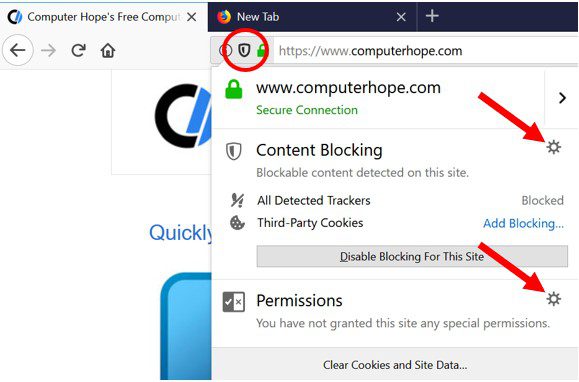
Safari (Mac):
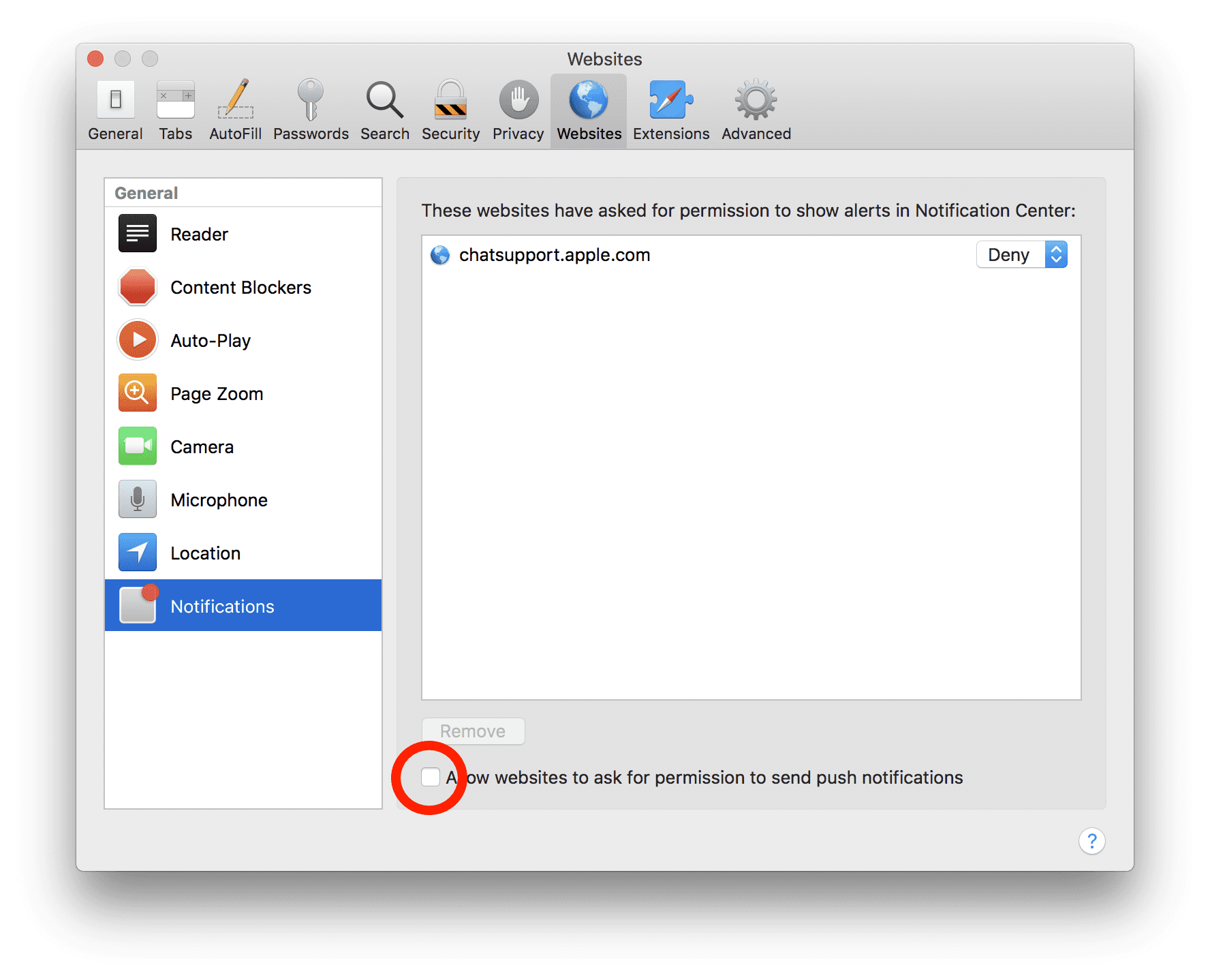
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Melutix.com:
Remove the related items of Melutix.com using Control-Panel
Windows 7 Users
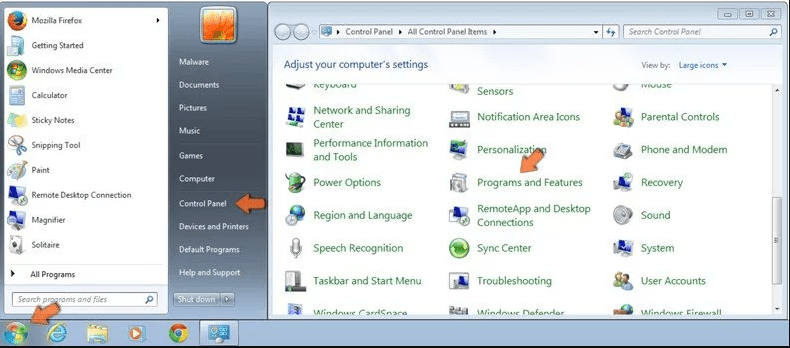
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
Windows XP Users
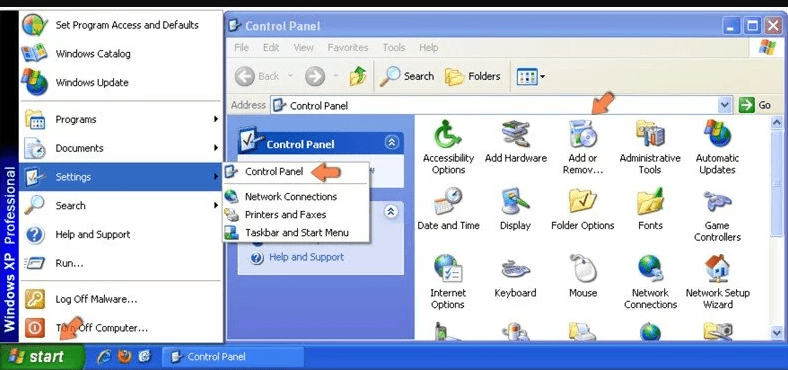
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
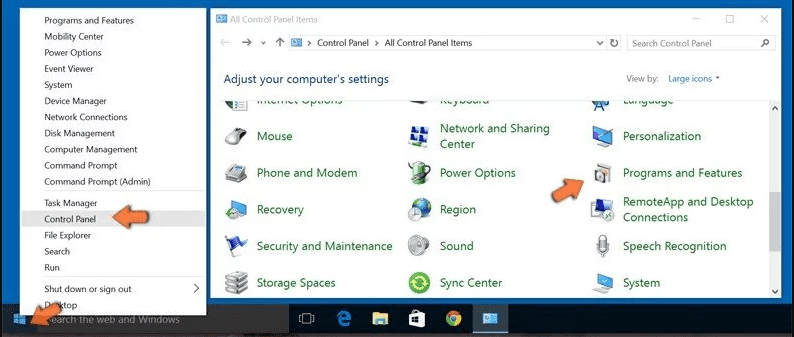
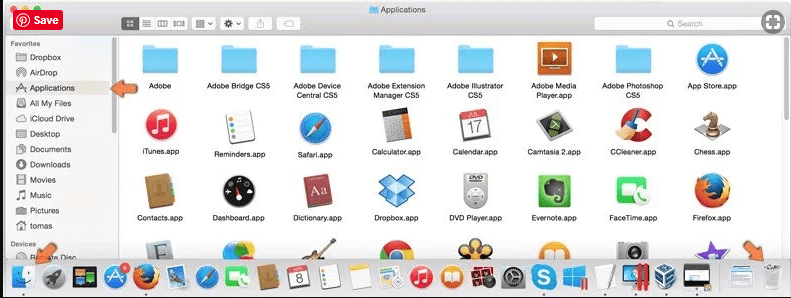
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
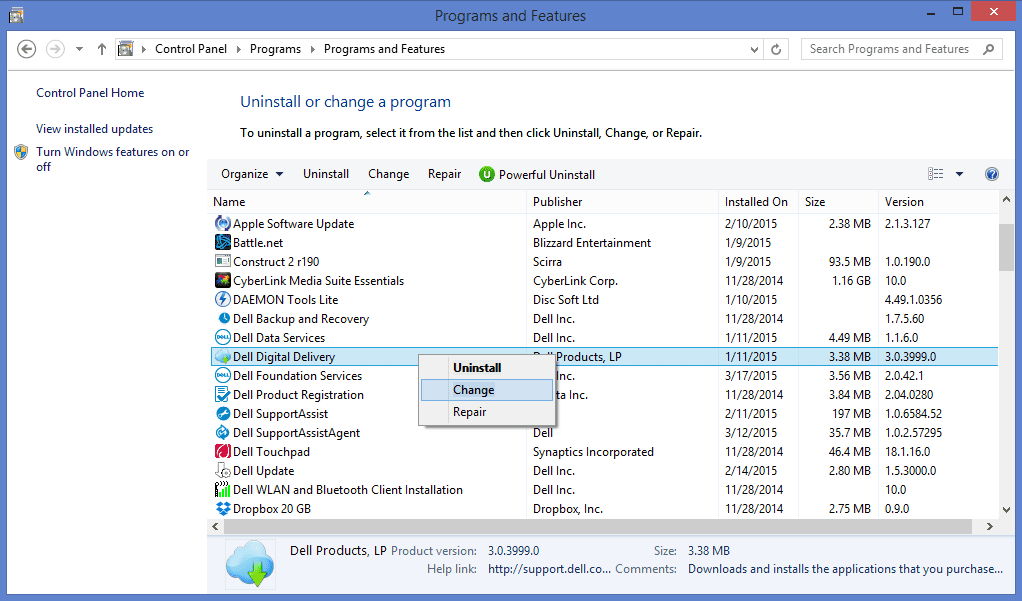
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Melutix.com issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Malware/Spyware/Virus can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter 5 antimalware scanner to check if the program can help you getting rid of this virus.
Special Offer (For Macintosh) If you are a Mac user and Malware/Spyware/Virus has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Melutix.com) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
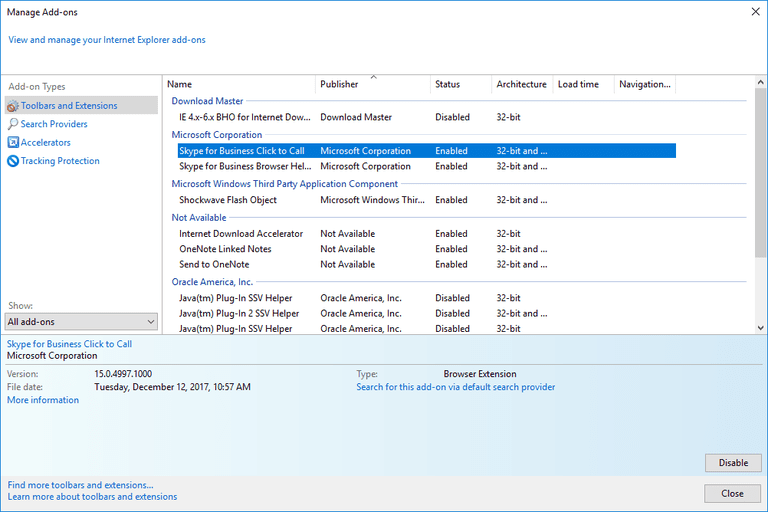
Additional Option
If you still face issues related to Melutix.com removal, you can reset the Internet Explorer to its default setting.
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
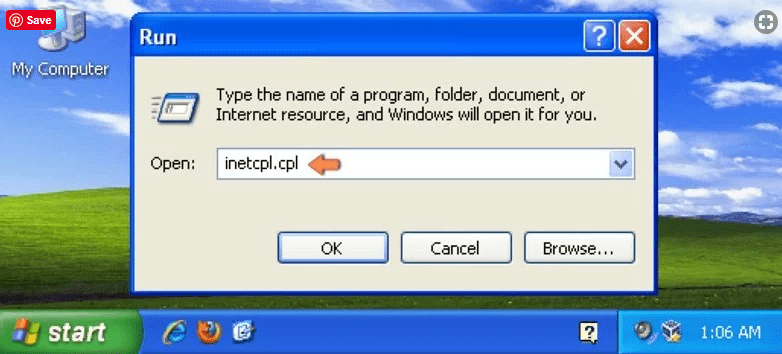
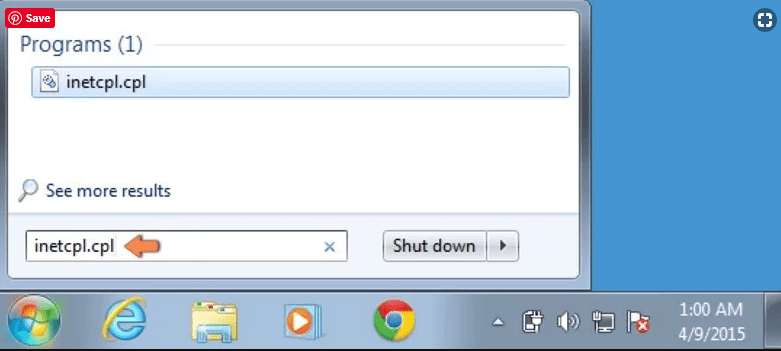
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
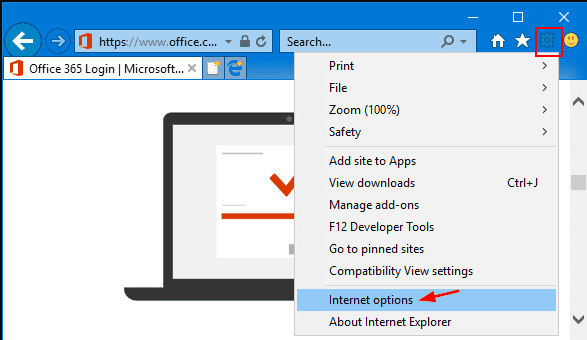
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
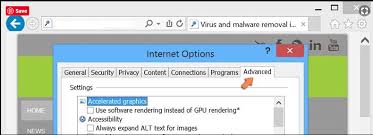
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
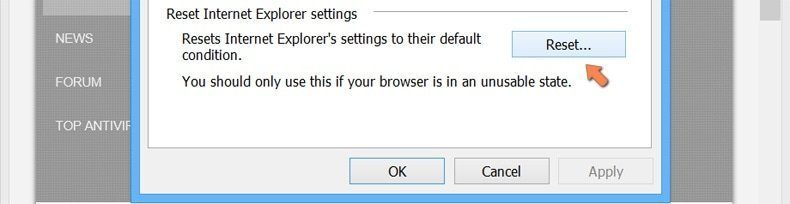
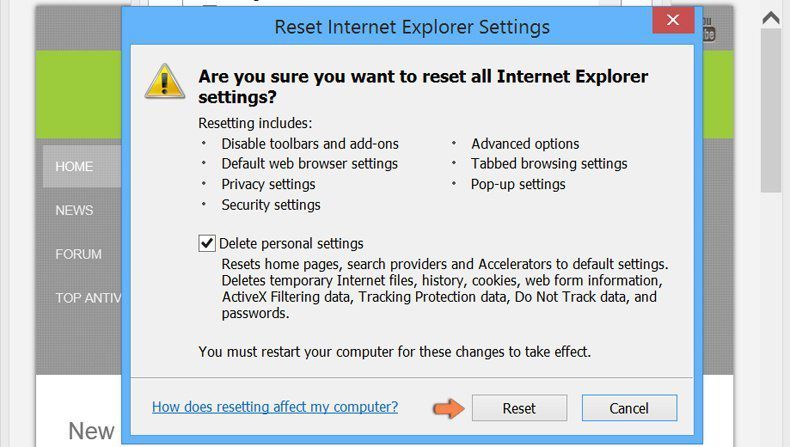
You have to press on the “Reset” button again to confirm that you really want to reset the IE
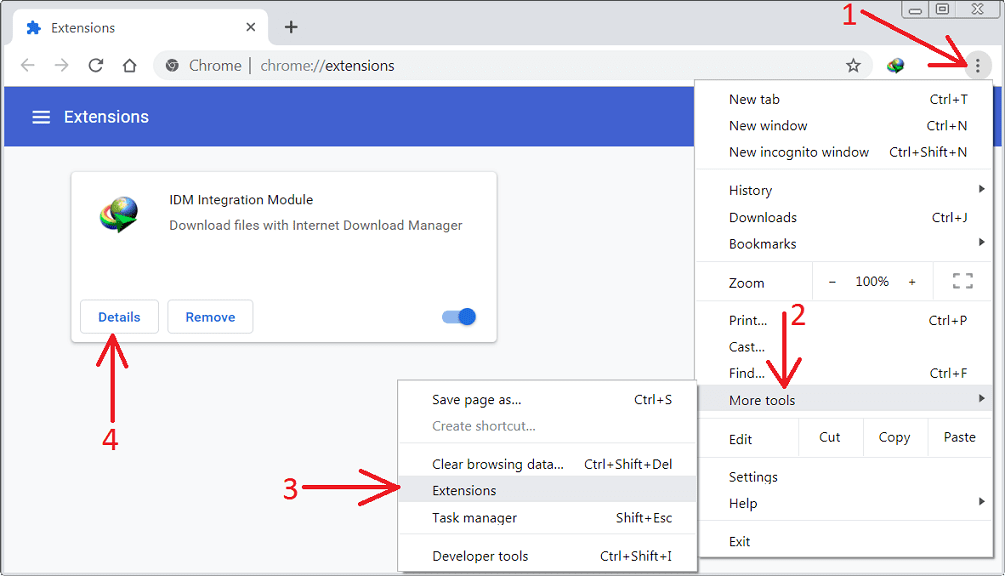
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
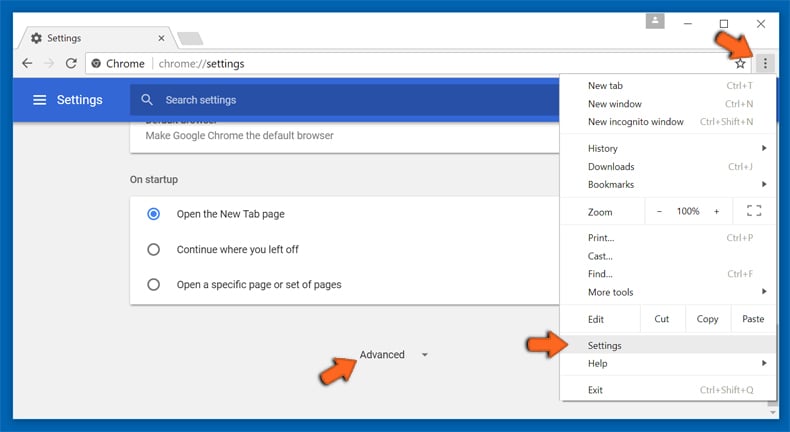
Optional Method
If the problems related to Melutix.com still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
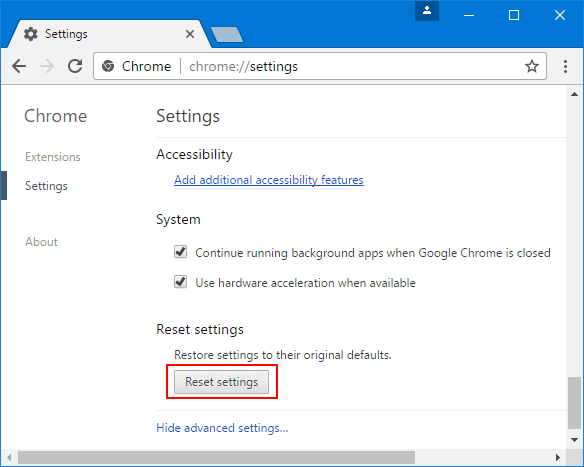
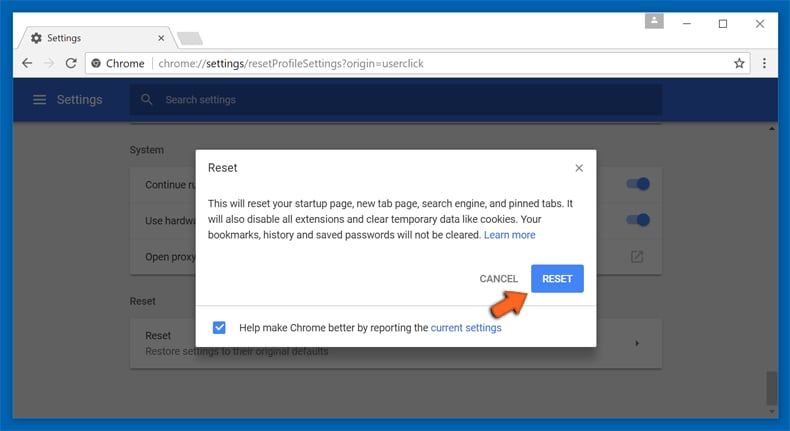
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove Melutix.com plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Melutix.com removal then you have the option to rese the settings of Mozilla Firefox.
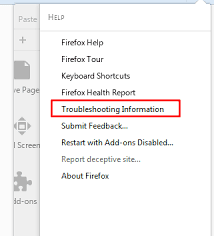
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
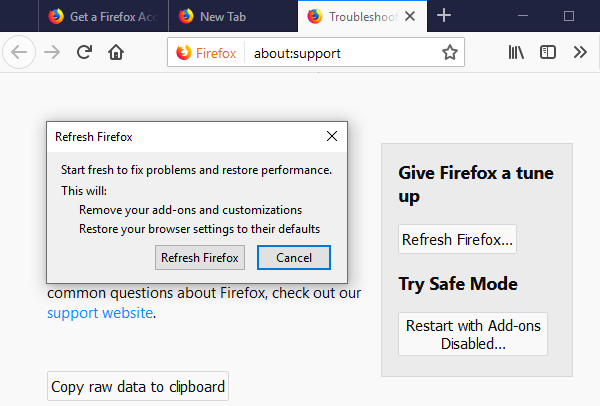
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
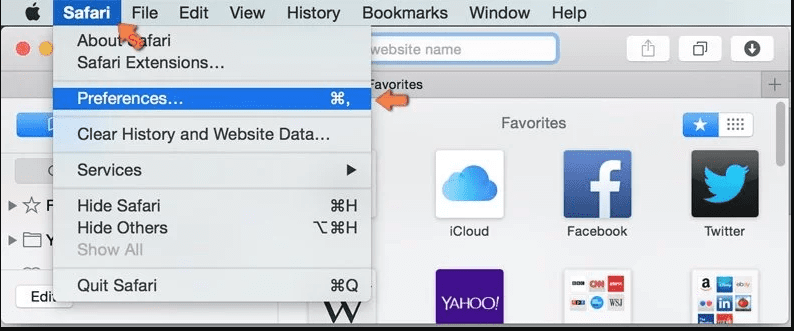
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
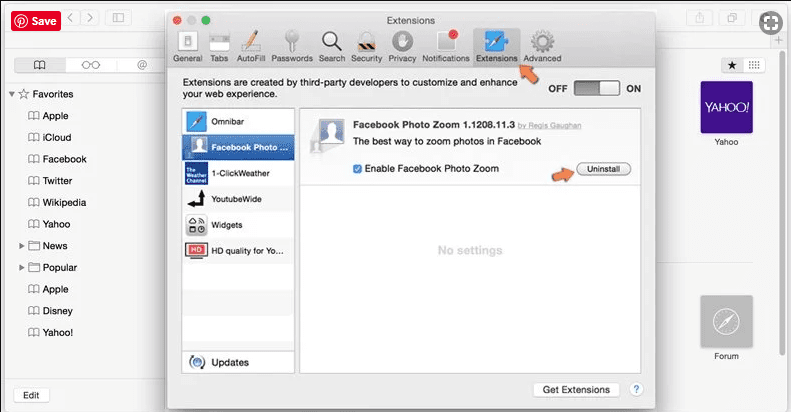
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
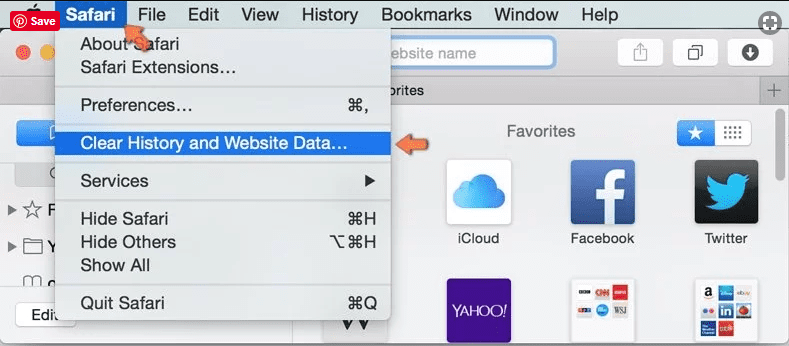
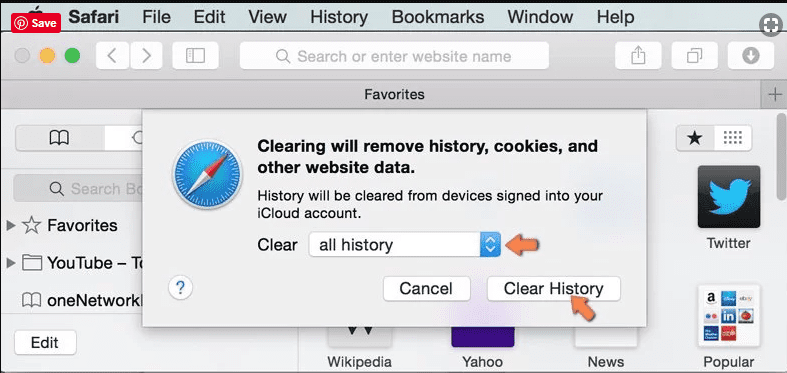
In the newly opened window, select “All History” and then press on “Clear History” option.
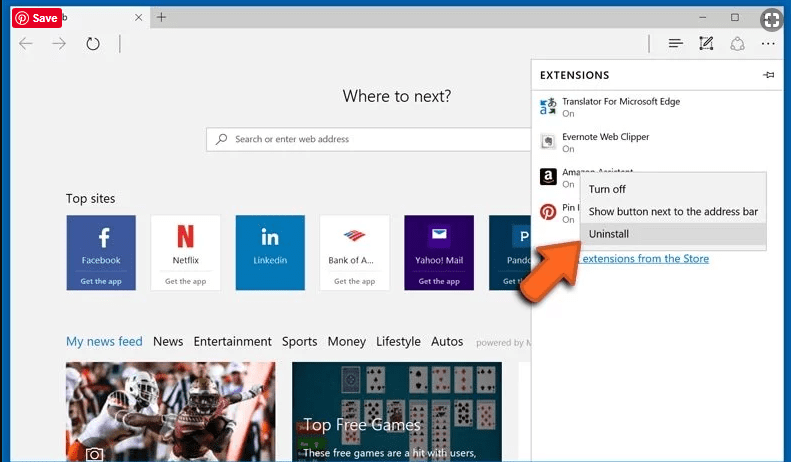
Delete Melutix.com (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
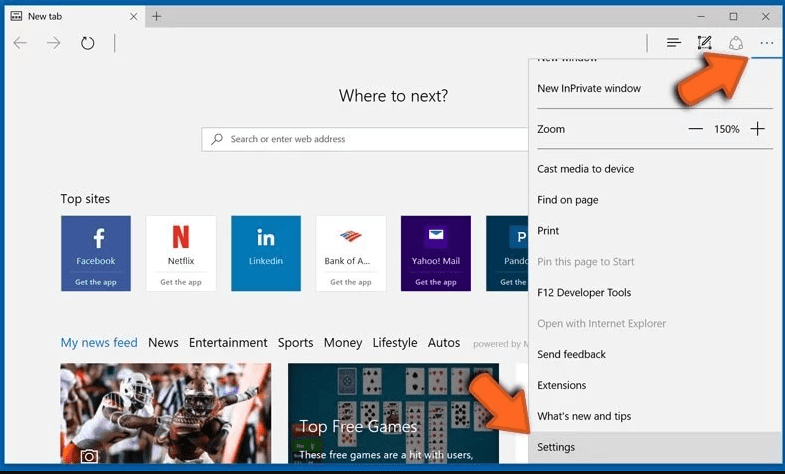
Optional Method
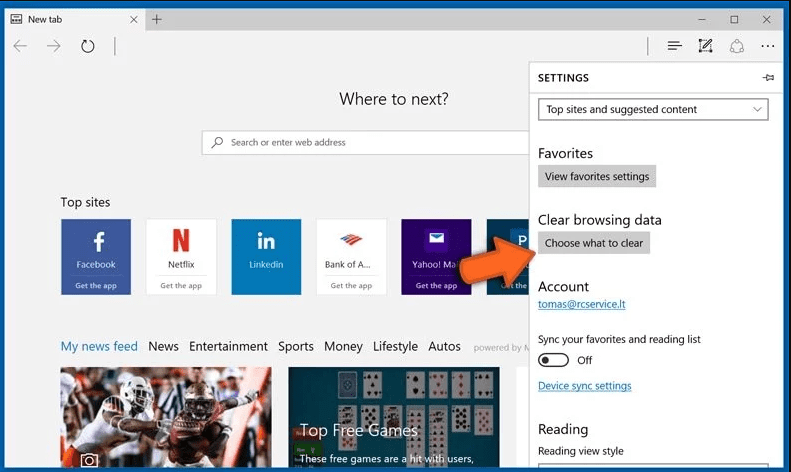
Open the browser (Microsoft Edge) and select “Settings”
Next steps is to click on “Choose what to clear” button
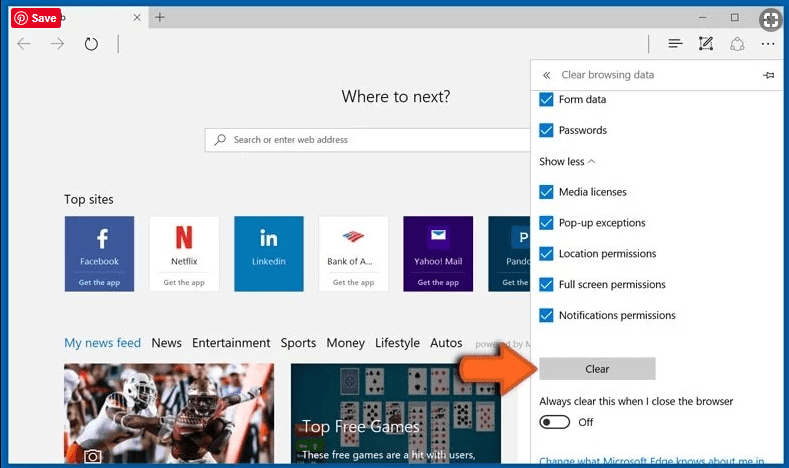
Click on “show more” and then select everything and then press on “Clear” button.
How to prevent Melutix.com infection?

There are multiple measures to safeguard against browser hijacking or adware infection:
- Be cautious when downloading software. Browser-based parasite, such as Melutix.com often disguises itself as legitimate software, so carefully read all terms, conditions, and end user licensing agreements before downloading any programs.
- Avoid running freeware programs that may unpack software during installation. Prior to installing any software, review the download settings to ensure no unwanted software is included.
- Exercise caution when encountering suspicious links. Refrain from clicking on email links, messages, or pop-up boxes from unfamiliar senders, as they may trigger the download of browser hijackers or adware.
- Keep your operating system (OS) and browser up to date. Regularly applying OS and browser patches is vital to prevent hijacking attacks, as attackers often exploit known vulnerabilities. Updating software closes these potential entry points.
- Utilize antivirus software. Install reliable antivirus software and keep it updated with the latest patches. It offers protection against browser hijacking, notifying users in real-time if downloaded software attempts to modify browser settings. Certain antivirus software empowers users to block such alterations.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your PC system safe and secure.
Conclusion:
To sum up, Melutix.com can cause significant problems for computer users, including unwanted browser redirects, changes to homepage and search engine settings, and even the installation of additional malware. These infections typically result from downloading and installing software from untrusted sources or clicking on suspicious links. To prevent browser hijackers or adware, it is important to be cautious when downloading and installing software, use reputable antivirus tool, and keep browsers and operating systems updated with the latest security patches.
Related FAQs about Melutix.com
What are the Symptoms of Browser-hijacker (Melutix.com)?
The common symptoms of Melutix.com infection include changes to the default homepage and search engine, unwanted toolbars and extensions, pop-up ads, and redirects to unfamiliar websites. Additionally, the browser may slow down or crash frequently, and search results may be manipulated or irrelevant to the query.
What Should I do if my PC gets infected with virus like Melutix.com?
If your computer is infected with this browser-based threat, you should immediately run a virus scan using reputable antivirus software. If the software detects the malware, you should follow the removal instructions provided by it to eliminate the infection and restore your browser settings to default.
How can I protect my password and other personal credentials from Melutix.com?
To protect your password and other sensitive information from Melutix.com, you should employ reputable antivirus suite, enable two-factor authentication on all accounts, and use strong and unique passwords for each account. Also, you should avoid clicking on suspicious links or downloading software from untrusted sources.
Why I should trust your research conducted on Melutix.com?
It’s important to mention that our research is conducted independently and with the assistance of unbiased security experts, who provide us with daily updates on the latest definitions and threats related to malware, adware, and browser hijackers. Moreover, our study on the Melutix.com threat is supported by VirusTotal.
Special Offer (For Windows)
Malware/Spyware/Virus can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter 5 antimalware scanner to check if the program can help you getting rid of this virus.
Special Offer (For Macintosh) If you are a Mac user and Malware/Spyware/Virus has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.

