Remove Rootkit Malware Detected

Complete Guide To Uninstall Unwanted Software
Rootkit Malware Detected is another deceptive online scam circulated by cyber crime master minds. This kind of scams are created to infect a Windows based computers after which it use to blackmail targeted innocent users and collect illegal revenue from them. Such scams are mostly promoted through deceptive websites that claims a rootkit malware is detected on targeted device, and claims that a tech support team can help the users.
Such kind of hectic pages often appears on screen through some adware or PUPs if installed on computer. Even installing browser’s toolbar or extensions or media players blindly can come bind with hidden additional offers which alters browser or system settings without any prior notice, and this redirects them to vicious online sources, even over the ones promoting Rootkit Malware Detected.
Rootkit Malware Detected based adverts claims that the tech support team will provide the service only after being paid, so the adware just intend you to call provided tech support scam toll free number and avail fake service to resolve those issues which are actually not there on your machine. Thus, in case if you are being shown with Rootkit Malware Detected, you should simply avoid those scary messages, but choosing to identity and terminate possible infectious object on targeted device.
Threat Summary |
| Name: Rootkit Malware Detected |
| Category: Browser hijacker |
|
Features: Alters the user’s browsing experience by changing the default search engine and homepage, displays unwanted ads, and redirects the user to malicious websites. |
| Danger Level: Medium |
|
Symptoms: The unwanted application can cause several adverse effects, such as displaying intrusive pop-up ads and slowing down internet browsing. The threat can manipulate the settings of an internet browser. This manipulation forces users to visit the hijacker’s website and conduct internet searches using their search engine. |
|
Distribution: Browser hijackers or adware such as Rootkit Malware Detected can spread through deceptive pop-up ads, free software installers that are bundled with malware, and fake Flash Player installers. |
|
Removal: To remove the threat, scan your system with powerful SpyHunter anti-malware software |
What is the purpose of Rootkit Malware Detected?

The purpose of adware or browser hijacker is to generate revenue through targeted advertising. It collects user data, such as browsing habits and preferences, to deliver personalized ads. By bombarding users with ads, the unwanted program aims to increase the chances of users clicking on them, leading to potential revenue for its developers.
While adware is primarily an annoyance and can compromise user privacy, it is often a means for companies to monetize free software and services without directly charging users. The primary objective of a browser hijacker is to promote certain websites, generate traffic, and potentially earn revenue through advertising or other means by exploiting the user’s browsing experience without their consent.
How does PUP end up on users’ devices?
Devices can fall victim to browser hijackers or adware through the download of infected files, malevolent email attachments, or visits to compromised websites. These hijacking tools may be bundled within browser extensions or included as part of software packages. Additionally, browser based threats can stem from shareware, freeware, or spyware infections, further expanding their potential sources of origin.
Potentially unwanted programs like Rootkit Malware Detected often find their way onto users’ devices unintentionally, as users can be deceived into unknowingly downloading them. This can occur when users agree to an extra download mentioned in the terms and conditions of software installation. Another tactic involves misleading users with a choice to decline the installation of the browser hijacker software, but the wording deliberately confuses them, resulting in the inadvertent download. Once installed, PUP initiates its malicious actions by manipulating the user’s browser activities through embedded malevolent code.
What are the impacts of Rootkit Malware Detected infection?
Browser hijacking refers to the unauthorized modification of web browser’s settings or behavior by malicious software or websites. It can have various impacts on users and their browsing experience. Here are some common impacts of browser hijacking:
- Altered homepage and search engine: Hijackers often change the default homepage and search engine settings of a browser to redirect users to a different website. This can disrupt the user’s browsing routine and make it challenging to find the desired information.
- Unwanted browser extensions: Browser hijackers or adware may install malicious or unwanted browser extensions without the user’s consent. These extensions can inject ads, track browsing activities, or collect personal information, compromising primacy and security.
- Increased exposure to ads: Hijacked browsers often display an excessive number of pop-up ads, banners ads, or in-text ads. This flood of advertisements not only annoys users but can also slow down browsing speed and consume bandwidth.
- Tracking and data collection: Browser-based infections like Rootkit Malware Detected employ tracking mechanisms to monitor users’ online activities, including websites visited, search queries, and personal information entered on web forms. This information can be used for targeted advertising or sold to third-parties without the user’s consent.
What problems Rootkit Malware Detected can cause?
This undesirable application can cause instability in web browsers by modifying critical settings, introducing incompatible software, or consuming system resources. Users may experience frequent crashes, slow performance, or unresponsiveness while browsing. In more severe cases, browsing hijacking can lead to unauthorized access to online accounts. PUPs may attempt to steal login credentials, financial information, or other sensitive data, putting users at risk of identity theft or fraud.
Furthermore, browser hijacking can be a part of a larger malware infection. In such cases, adware or hijacker may serve as a gateway for other malicious software, such as ransomware, keyloggers, or spyware, further compromising the user’s system and data. Also, browser-based threats with data collection abilities can cause severe problems. They can gather sensitive information such as login credentials, financial data, and personal details, leading to identity theft and fraud. The collected data may also be sold to third parties, compromising user privacy. Additionally, targeted advertising based on the collected information can result in a flood of intrusive and potentially malicious ads.
How can I know if I have an adware or browser hijacker?
If you have an adware or browser hijacker, such as Rootkit Malware Detected installed on your device, you may notice a few clear indications. Users need to exercise caution if they encounter any of the following signs, as it could suggest their system is compromised.
- If users find that their default homepage or preferred search engine has been substituted without their authorization, they should be on high alert.
- If users notice that their search queries are being rerouted to unfamiliar websites, it’s important for them to be cautious and aware of this redirection behavior.
- When users are bombarded with an excessive number of intrusive pop-up ads appearing frequently, they should be cautious and wary of the abundance of unsolicited advertisements.
- If users experience delays in the loading of webpages, where the content takes an unusually long time to appear, it is important for them to remain vigilant and take note of this sluggish performance.
- Should users notice the sudden appearance of unauthorized toolbars on their internet browser, it is crucial for them to exercise caution and be mindful of these unapproved additions.
Special Offer (For Windows)
Rootkit Malware Detected can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Rootkit Malware Detected has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
Google Chrome (PC)
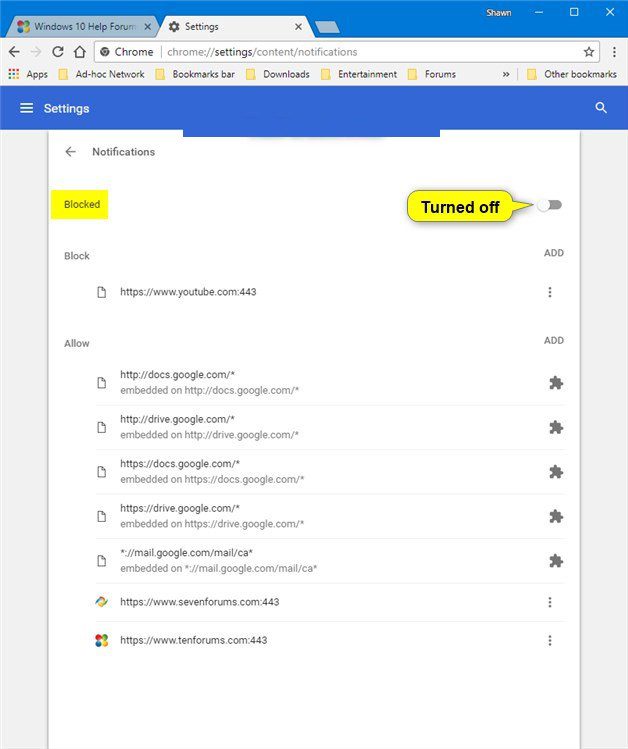
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
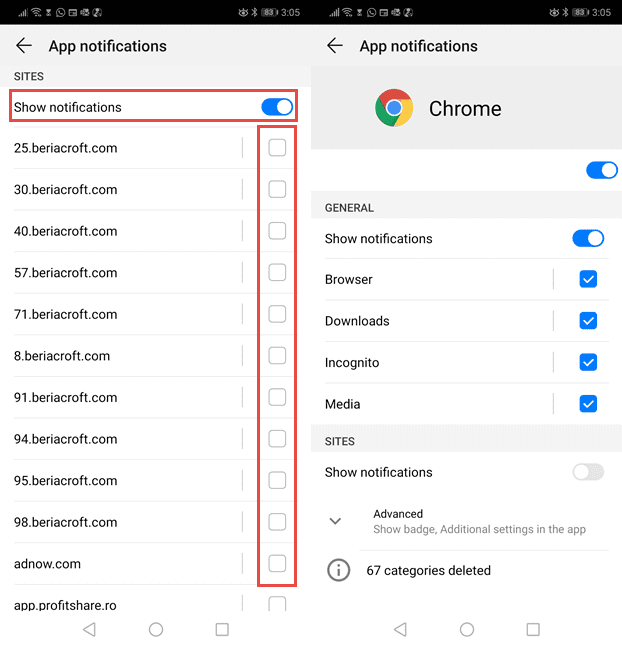
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
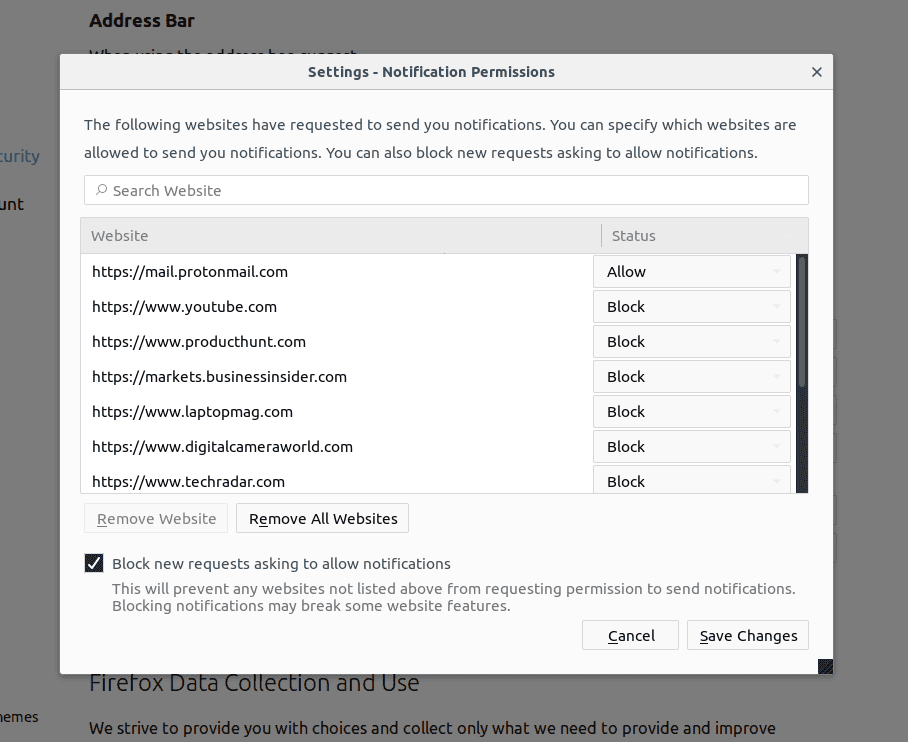
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
Internet Explorer
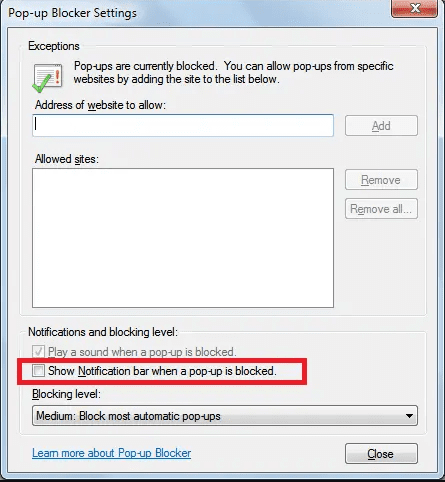
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
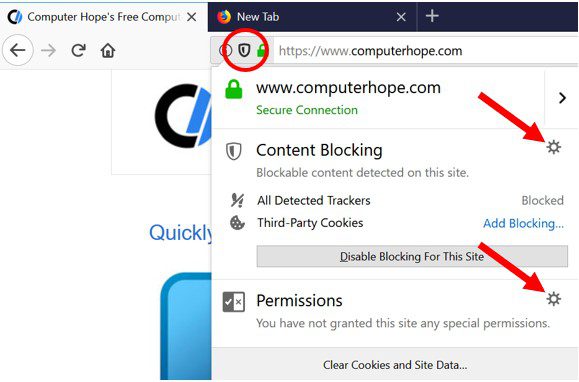
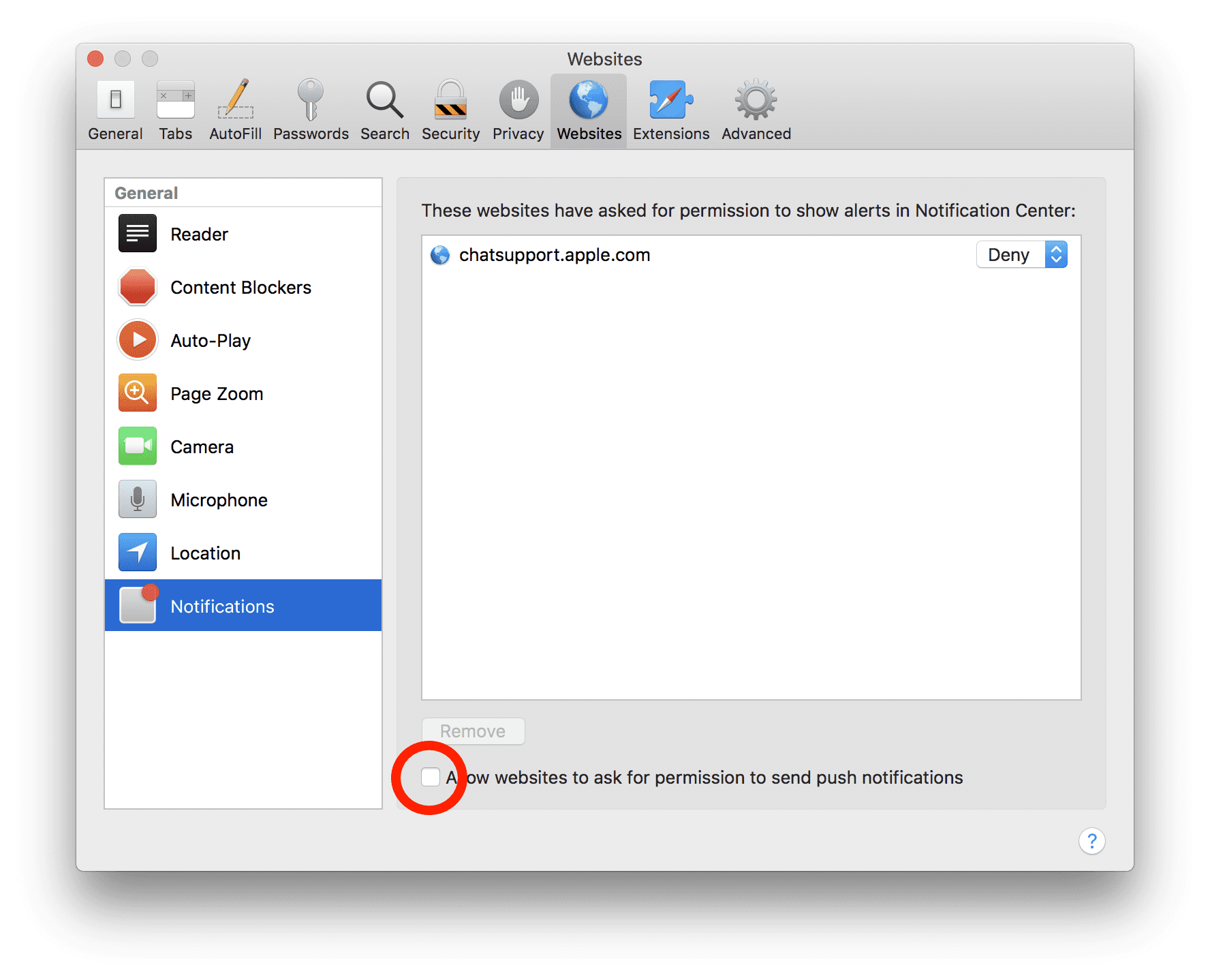
Safari (Mac):
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Rootkit Malware Detected:
Remove the related items of Rootkit Malware Detected using Control-Panel
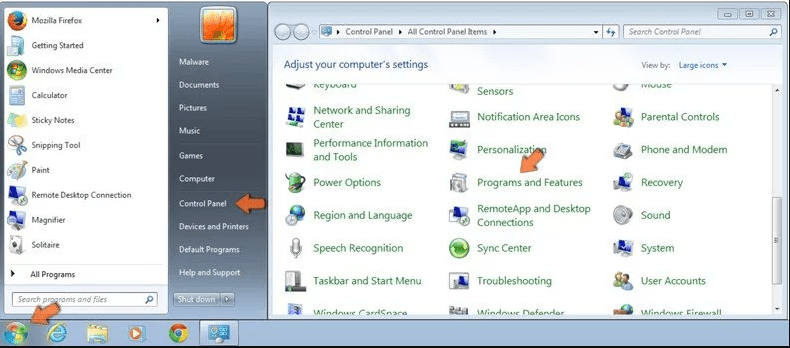
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
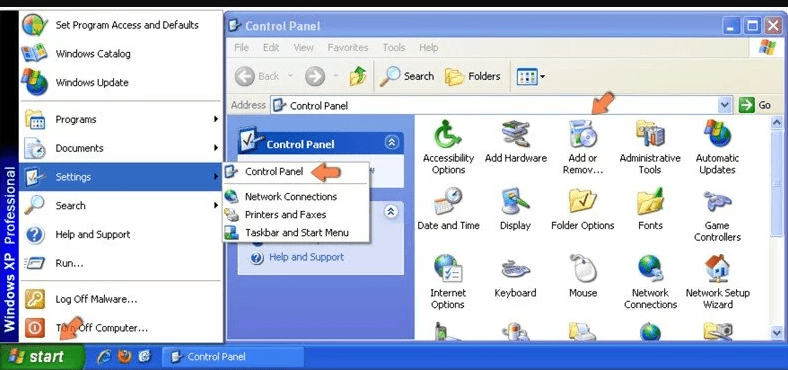
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
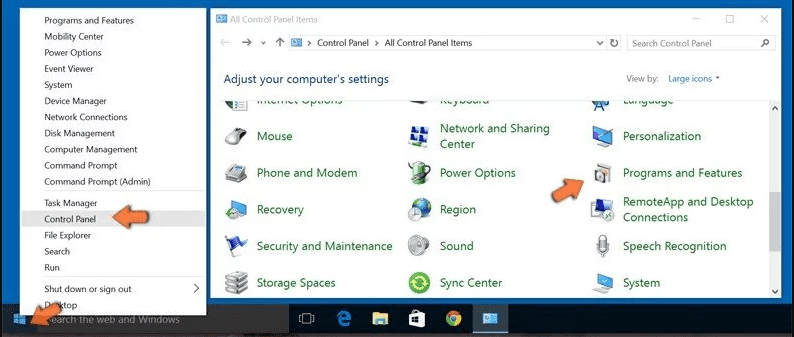
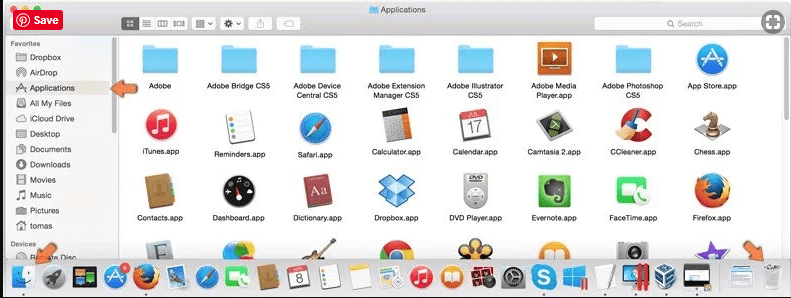
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
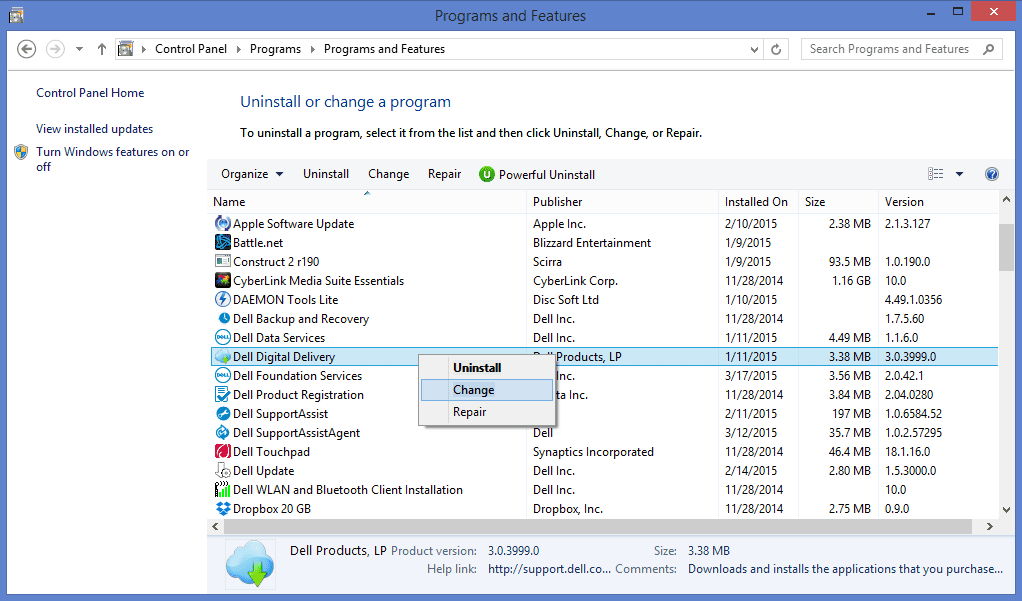
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Rootkit Malware Detected issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Rootkit Malware Detected can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Rootkit Malware Detected has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Rootkit Malware Detected) from Internet Browsers
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
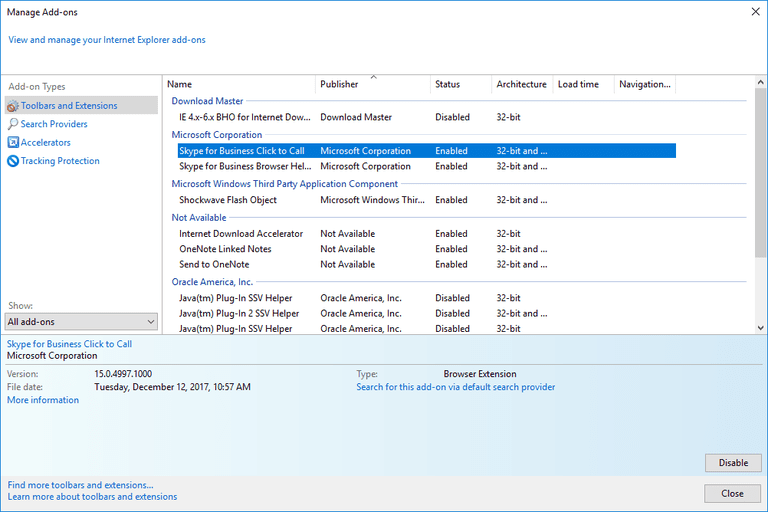
Additional Option
If you still face issues related to Rootkit Malware Detected removal, you can reset the Internet Explorer to its default setting.
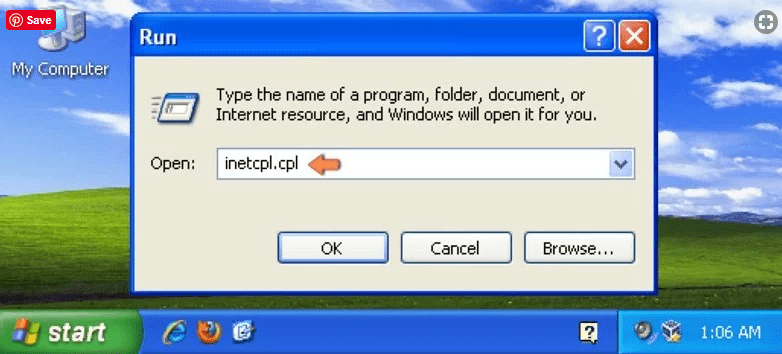
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
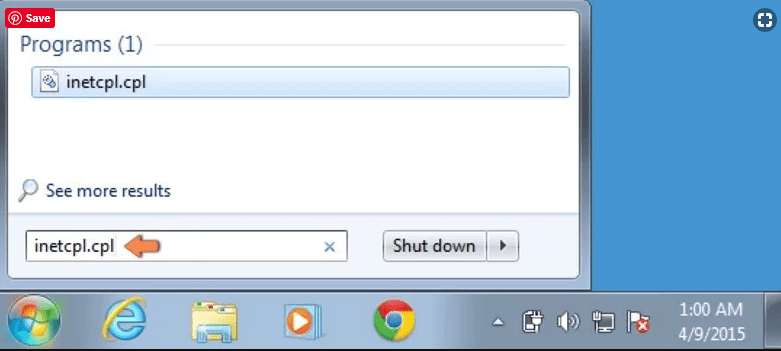
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
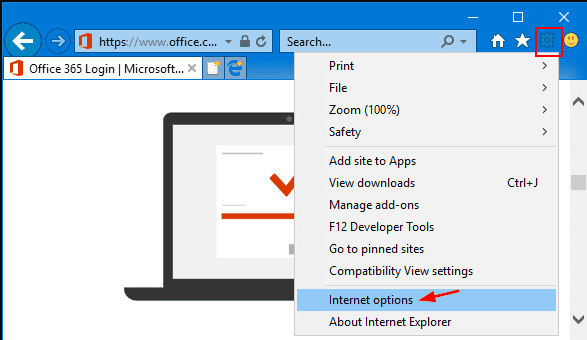
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
Select the “Advanced” tab in the newly opened window
Press on “Reset” option
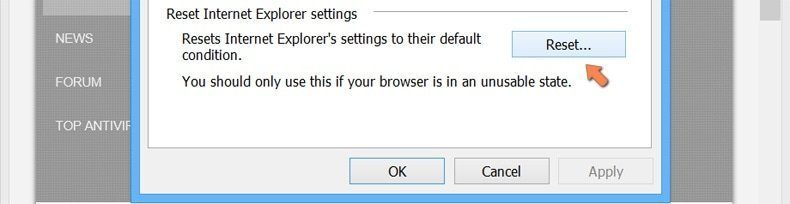
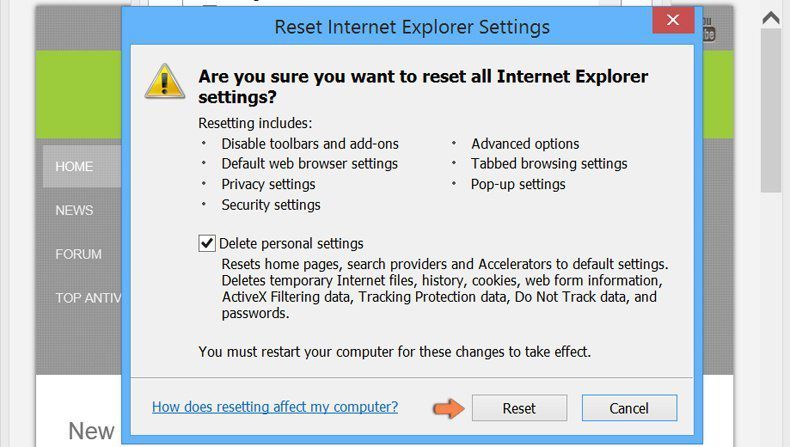
You have to press on the “Reset” button again to confirm that you really want to reset the IE
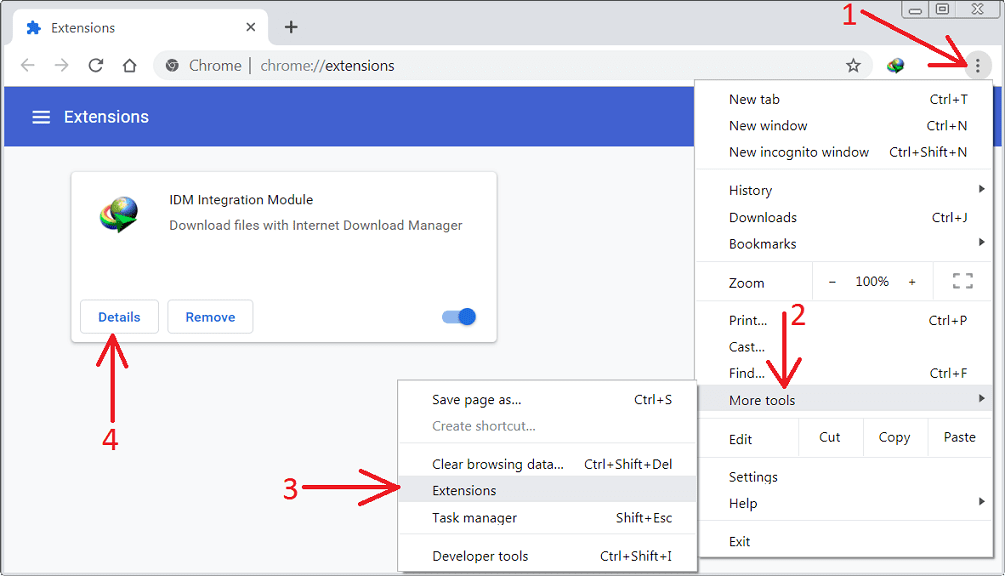
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
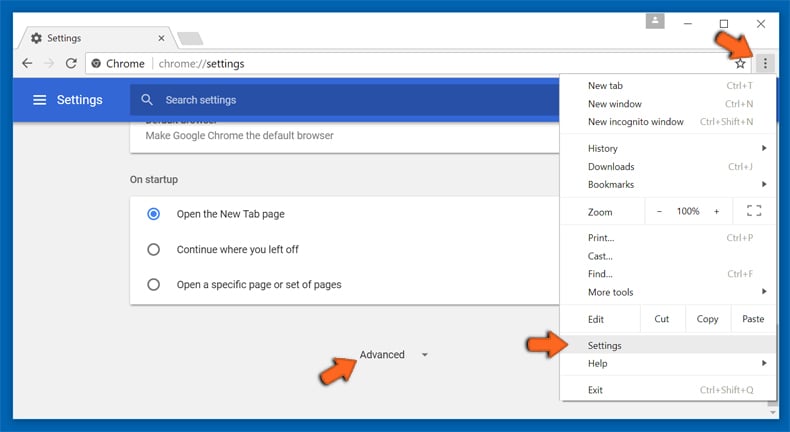
Optional Method
If the problems related to Rootkit Malware Detected still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
At the bottom, notice the “Reset” option and click on it.
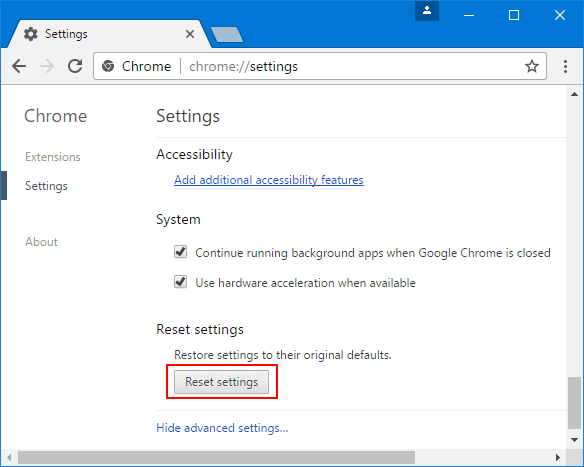
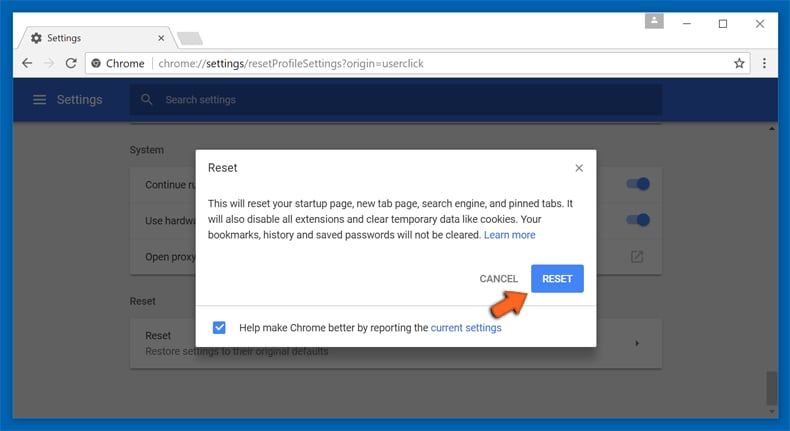
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove Rootkit Malware Detected plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Rootkit Malware Detected removal then you have the option to rese the settings of Mozilla Firefox.
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
Choose “Troubleshooting Information”
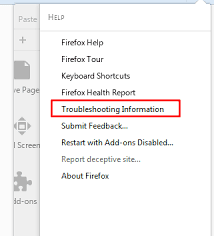
In the newly opened pop-up window, click “Refresh Firefox” button
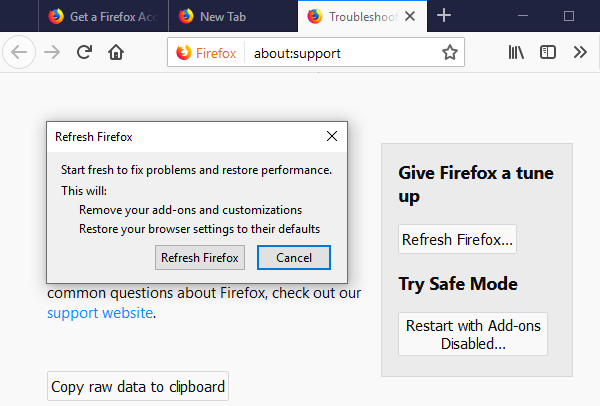
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
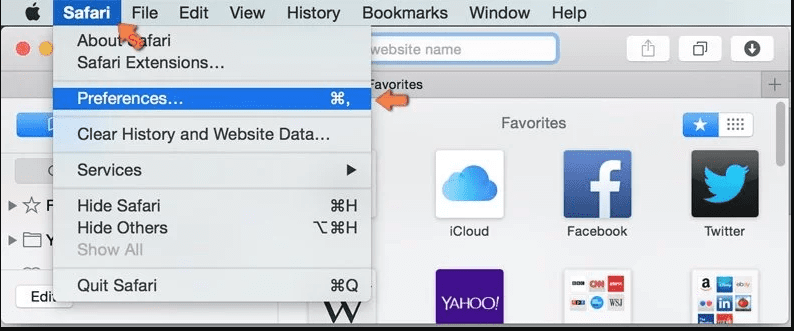
Open the Safari and go to its “Menu” and select “Preferences”.
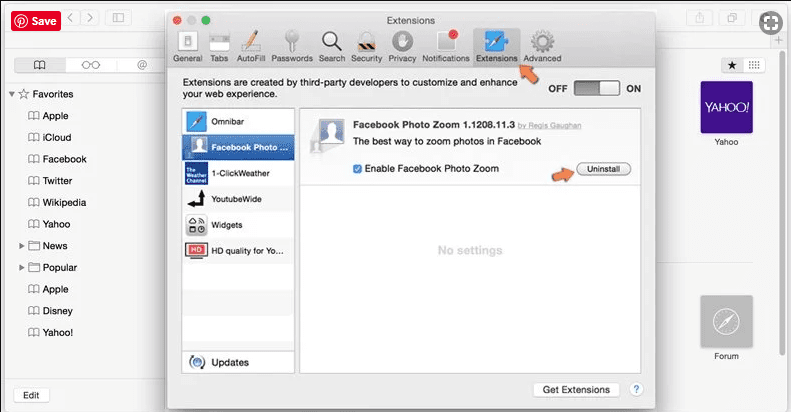
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
Optional Method
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
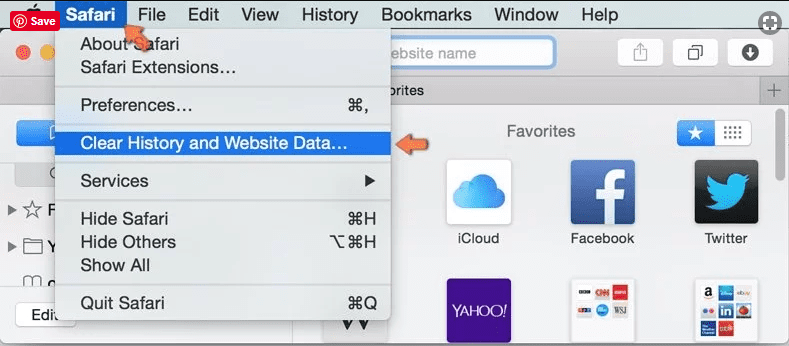
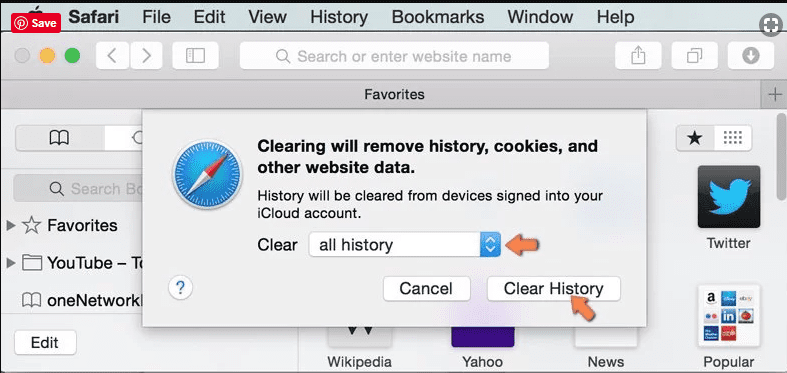
In the newly opened window, select “All History” and then press on “Clear History” option.
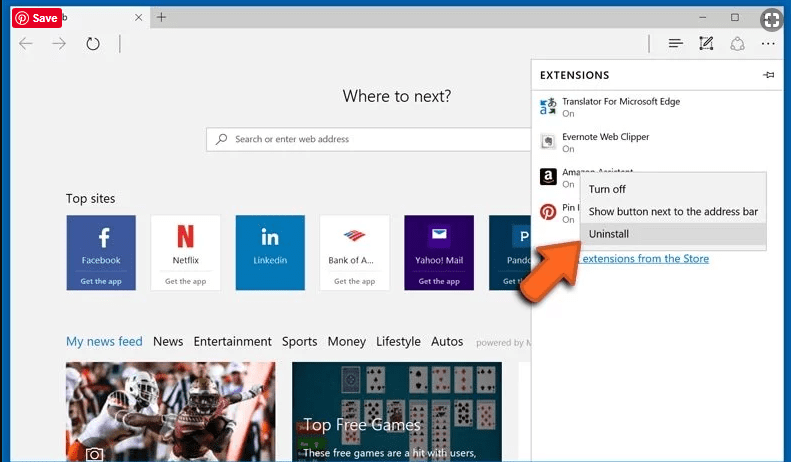
Delete Rootkit Malware Detected (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
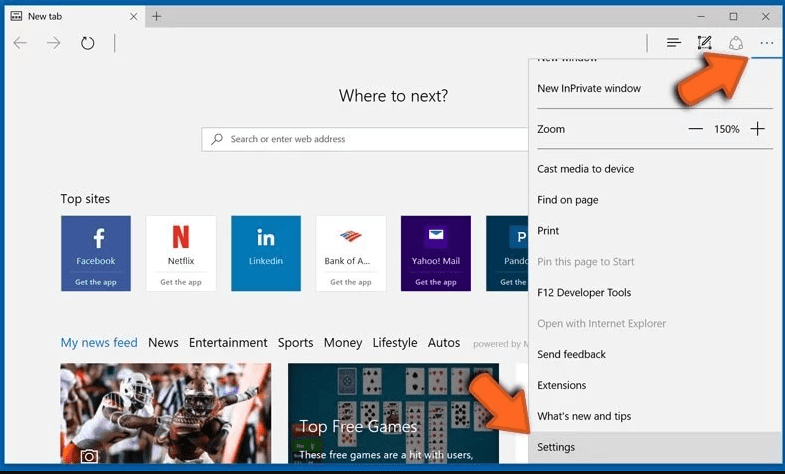
Optional Method
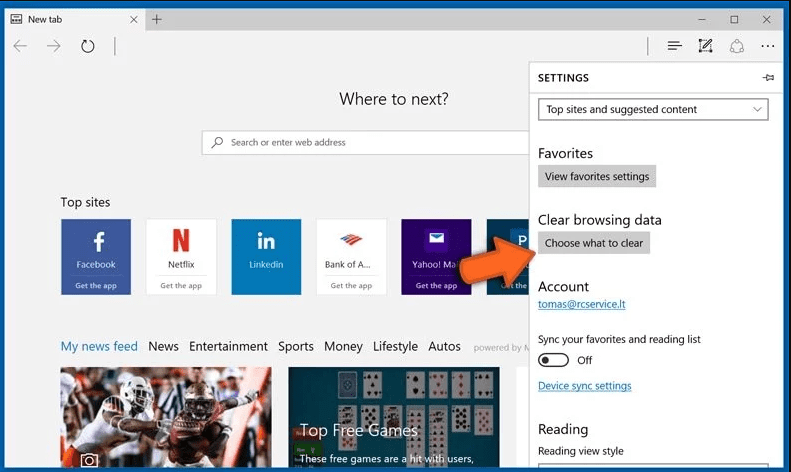
Open the browser (Microsoft Edge) and select “Settings”
Next steps is to click on “Choose what to clear” button
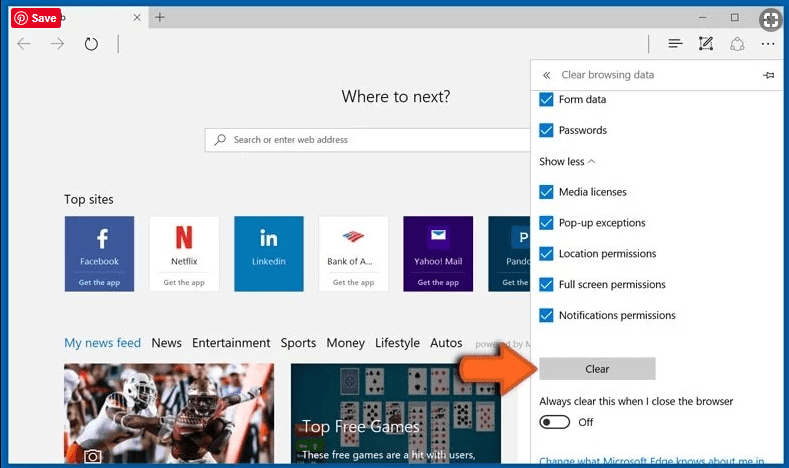
Click on “show more” and then select everything and then press on “Clear” button.
How to prevent Rootkit Malware Detected infection?

There are multiple measures to safeguard against browser hijacking or adware infection:
- Be cautious when downloading software. Browser-based parasite, such as Rootkit Malware Detected often disguises itself as legitimate software, so carefully read all terms, conditions, and end user licensing agreements before downloading any programs.
- Avoid running freeware programs that may unpack software during installation. Prior to installing any software, review the download settings to ensure no unwanted software is included.
- Exercise caution when encountering suspicious links. Refrain from clicking on email links, messages, or pop-up boxes from unfamiliar senders, as they may trigger the download of browser hijackers or adware.
- Keep your operating system (OS) and browser up to date. Regularly applying OS and browser patches is vital to prevent hijacking attacks, as attackers often exploit known vulnerabilities. Updating software closes these potential entry points.
- Utilize antivirus software. Install reliable antivirus software and keep it updated with the latest patches. It offers protection against browser hijacking, notifying users in real-time if downloaded software attempts to modify browser settings. Certain antivirus software empowers users to block such alterations.
By following these steps, you can minimize the risk of potentially unwanted program intrusion and keep your PC system safe and secure.
Conclusion:
To sum up, Rootkit Malware Detected can cause significant problems for computer users, including unwanted browser redirects, changes to homepage and search engine settings, and even the installation of additional malware. These infections typically result from downloading and installing software from untrusted sources or clicking on suspicious links. To prevent browser hijackers or adware, it is important to be cautious when downloading and installing software, use reputable antivirus tool, and keep browsers and operating systems updated with the latest security patches.
Related FAQs about Rootkit Malware Detected
What are the Symptoms of Browser-hijacker (Rootkit Malware Detected)?
The common symptoms of Rootkit Malware Detected infection include changes to the default homepage and search engine, unwanted toolbars and extensions, pop-up ads, and redirects to unfamiliar websites. Additionally, the browser may slow down or crash frequently, and search results may be manipulated or irrelevant to the query.
What Should I do if my PC gets infected with virus like Rootkit Malware Detected?
If your computer is infected with this browser-based threat, you should immediately run a virus scan using reputable antivirus software. If the software detects the malware, you should follow the removal instructions provided by it to eliminate the infection and restore your browser settings to default.
How can I protect my password and other personal credentials from Rootkit Malware Detected?
To protect your password and other sensitive information from Rootkit Malware Detected, you should employ reputable antivirus suite, enable two-factor authentication on all accounts, and use strong and unique passwords for each account. Also, you should avoid clicking on suspicious links or downloading software from untrusted sources.
Why I should trust your research conducted on Rootkit Malware Detected?
It’s important to mention that our research is conducted independently and with the assistance of unbiased security experts, who provide us with daily updates on the latest definitions and threats related to malware, adware, and browser hijackers. Moreover, our study on the Rootkit Malware Detected threat is supported by VirusTotal.
Special Offer (For Windows)
Rootkit Malware Detected can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Rootkit Malware Detected has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.




